Let’s make a distinction between frame and packet before moving forward as these terms are often used rather loosely. The term frame refers to the bits and bytes that include the layer 2 header and trailer along with the data encapsulated by the header and trailer. The term packet is used to describe the layer 3 header and data without the layer 2 header or trailer.
The switch maintains an address table called MAC address table in order to efficiently switch frames between interfaces. When the switch receives a frame, it associates the MAC address of the sending device with the switch port on which it was received. In this way, a switch dynamically builds an address table by using the source MAC address of the frames received.
As a practice, try issuing command ipconfig /all on Windows CLI and show mac address-table on Cisco switch CLI to get warmed up for later examples. The command show mac address-table, not surprisingly, is used to display the MAC address table of a switch we just talked about, as shown below:
SW1#show mac address-table
Mac Address Table
——————————————-
Vlan Mac Address Type Ports
—- ———– ——– —–
All 0100.0ccc.cccc STATIC CPU
All 0100.0ccc.cccd STATIC CPU
All 0180.c200.0000 STATIC CPU
All 0180.c200.0001 STATIC CPU
All 0180.c200.0002 STATIC CPU
All 0180.c200.0003 STATIC CPU
All 0180.c200.0004 STATIC CPU
All 0180.c200.0005 STATIC CPU
All 0180.c200.0006 STATIC CPU
All 0180.c200.0007 STATIC CPU
All 0180.c200.0008 STATIC CPU
All 0180.c200.0009 STATIC CPU
All 0180.c200.000a STATIC CPU
All 0180.c200.000b STATIC CPU
All 0180.c200.000c STATIC CPU
All 0180.c200.000d STATIC CPU
All 0180.c200.000e STATIC CPU
All 0180.c200.000f STATIC CPU
All 0180.c200.0010 STATIC CPU
All ffff.ffff.ffff STATIC CPU
1 000e.8316.f50d DYNAMIC Fa0/16
1 0013.195a.0bca DYNAMIC Fa0/16
1 0013.197e.4f88 DYNAMIC Fa0/16
1 0019.2fa7.b28d DYNAMIC Fa0/13
1 0019.2fa7.b28e DYNAMIC Fa0/14
1 0019.2fa7.b28f DYNAMIC Fa0/15
1 0025.84ba.7a22 DYNAMIC Fa0/16
Total Mac Addresses for this criterion: 27
In the above output, you should be able to identify various dynamically learned MAC addresses and the switch ports those MAC addresses are associated with. Each dynamically learned MAC address is associated with one and only one switch port. However, there may be more than one MAC addresses associated with the same switch port which means multiple devices are reachable off the same switch port. There are two possible scenarios in which multiple MAC addresses may be associated with the same switch port. In one case, the switch port may be connected to another switch which in turn has multiple devices connected to it. In the second case, multiple devices may be directly connected to the same switch port through a hub.
How Switches Work
The basic logic used by switches when forwarding frames is the key to understanding many enhanced switching concepts and is worth a quick review here. The forwarding logic differs based on the type of destination MAC address and on whether the destination address has been added to the MAC address table of the switch.
Known Unicast
The switch already has an entry in its MAC address table for the destination MAC address in the frame so it knows exactly which interface leads to the destination of the frame. The switch forwards frame out the single interface associated with the destination MAC address in the frame.
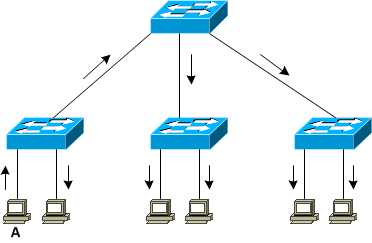
Figure 7-1 describes how known unicasts are propagated in a switched network. Host A sends a frame destined to host B which is forwarded by the intermediate switches to its final destination following the direction of the arrows.
Figure 7-1 Known Unicast Propagation
Unknown Unicast
The switch has no entry in its MAC address table for the destination MAC address in the frame. The switch sends a copy of the frame out all interfaces, other than the interface on which the frame was received. The idea here is that the frame would ultimately reach all hosts and the host having the same MAC address as the destination address of the frame would accept it while all other hosts would reject the frame.
Figure 7-2 describes how unknown unicasts are propagated in a switched network. Host A yet again sends a frame destined to host B but this time intermediate switches do not yet have an entry for the MAC address of host B in their MAC address tables. Pay careful attention to the direction of arrows and note that the frame sent by host A is received by all hosts in the switched network including hosts connected to other switches. Only host A whose MAC address matches the destination MAC address of the frame would accept that frame while all other devices would reject it. It is not difficult to understand that a lot of bandwidth is wasted here because the frame is sent to every host on the switched network. The negative impact would be more significant in a larger switched network with several switches and possibly hundreds of host.
Figure 7-2 Unknown Unicast Propagation
Broadcast
The switch sends a copy of the frame out all interfaces, except the interface on which the frame was received, identically to unknown unicasts. This switch behavior is also called frame flooding.
Figure 7-3 describes how broadcasts are propagated in a switched network. Host A sends a broadcast frame with the broadcast destination MAC address of FFFF.FFFF.FFFF and the frame is propagated to all hosts in the network even those connected to other switches.
Figure 7-3 Broadcast Propagation
Multicast
The switch floods frame identically to unknown unicasts and broadcasts, unless certain multicast optimizations are configured.
There are some problems with the way switches forward different types of frames by default, especially in larger switched networks. First, there is no isolation between hosts and any host can communicate with any other host totally unchecked. This is not a very desirable situation for you as a network administrator as there is no security from malicious software or users. Second, a broadcast sent by any host would reach every other host on the network which is neither bandwidth efficient nor secure. A malfunctioning Network Interface Card (NIC) or a piece of malicious software on a host can generate excessive broadcasts consuming all the bandwidth available and starving legitimate applications. These problems can be greatly alleviated by using virtual LANs or VLANs.






0 comments:
Post a Comment