Why is it so hard to secure your endpoints? The most simplistic reason is because endpoints are in the hands of human beings who can inadvertently click on a link that introduces malware or unwittingly use an unsecure Internet connection which allows threat actors to access a corporate network.
Read More: 700-805: Cisco Renewals Manager (CRM)
Organizations became more prone to breaches over the course of the pandemic because more and more workers were not inside corporate walls (and firewalls) and instead worked from places like a home office or café. With more endpoints outside the confines of the corporate WAN, the attack surface abruptly increased, and with this came greater risk. Working to keep endpoints secure while having to grant access so workers can be productive makes for a difficult balancing act.
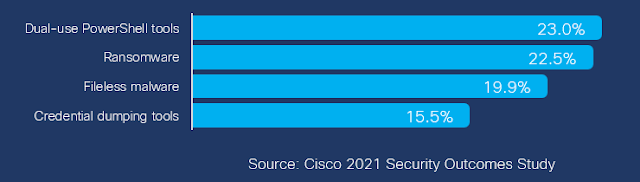
Endpoints are ground zero for organizations of all sizes and across all industry verticals. Cisco examined the nature of security incidents detected by sensors through Indication of Compromise (IOC), detecting suspicious behaviors and analyzing patterns of malicious activity. These are the top four critical severity IOCs we observed:
Without the capability to bring visibility via focused detection, breaches can go undetected for months, until the organization’s critical data have likely already been compromised.
So, if we know endpoints are so often targeted, then why are many organizations having such a problem securing them?
Customers tell us their primary challenges are expertise, time, and evidence:
| Challenge: Expertise | Challenge: Time | Challenge: Evidence |
| “My team can’t be experts on every new threat, or all be experts in threat hunting.” | “I don’t have enough time to go after every new threat, alert, patch and compromised device.” | “We can’t always identify which threats to prioritize or get to the root cause of every attack.” |
These quotes have got to be music to the ears of threat actors. They know, like you do, how hard it can be to find skilled resources to staff your security team. Studies show that most organizations’ internal Security Operations Centers (SOCs) are only able to handle 7 to 8 investigations per day, in part because teams are burdened with frequent, false, and often redundant alerts. This leads to more manual effort for already understaffed teams, making it harder to keep pace with constantly evolving threats and issues. The result? You end up with gaps in security, higher operational costs, and a less efficient and, honestly, burned out team.
But I’m here to tell you it doesn’t have to be like that. Consider our solution offer, Cisco Secure MDR for Endpoint (formerly Cisco Secure Endpoint Pro):
◉ We do the heavy lifting of securing your endpoints: Our dedicated elite team of Cisco security experts performs 24x7x365 endpoint monitoring, detection, and response—so you don’t have to.
◉ We detect and respond to threats in minutes, not hours: Cisco specialists use automation and advanced playbooks, powered by the Cisco SecureX platform, and backed by Talos threat intelligence, to drastically reduce detection and response times.
◉ We investigate every threat and prioritize the most critical ones: We conduct an in-depth investigation of every incident you have and enable you to approve or reject remediation actions based on evidence from our experts.
Cisco Secure MDR for Endpoint can identify and then stop threats, block malware, and contain and remediate even advanced threats that evade frontline defenses. We look at all alert-able threats, investigate and prioritize them, and recommend response actions. We do this around the clock and around the globe, from dedicated, global Cisco SOCs.
By the way, let me tell you a bit more about the incredible Talos threat intelligence standing behind our detection and response capabilities. Talos is a recognized leader in threat intelligence research and proactive and emergency response security services. Their research work includes identifying over 30 billion events per day and then vetting those events with Talos’ 400+ researchers and investigators—benefitting our ability to detect and respond.
We built Secure MDR for Endpoint as a solution, so you don’t have to spend the time and money to build a SOC, develop or acquire the tools to make it work, and then recruit and train the personnel to staff it. Secure MDR for Endpoint takes the time, expense, and complexity out of identifying and responding to threats on endpoints. Our SOC experts use AI and machine learning to separate all the false positive alarms from the real issues that need to be pursued and managed.
Source: cisco.com