Tuesday, 22 August 2023
Why are CEOs Cyber Resilient?
Thursday, 30 March 2023
Failing Forward – What We Learned at Cisco from a “Failed” Digital Orchestration Pilot
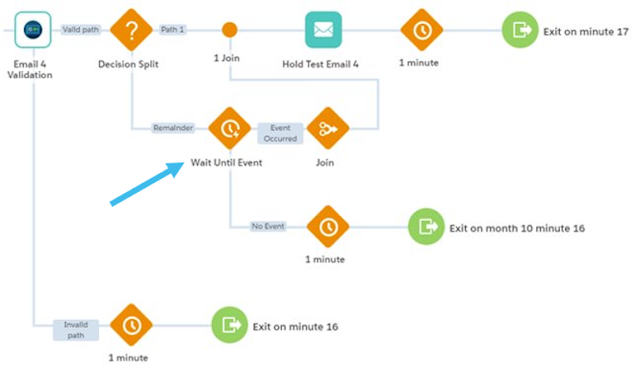
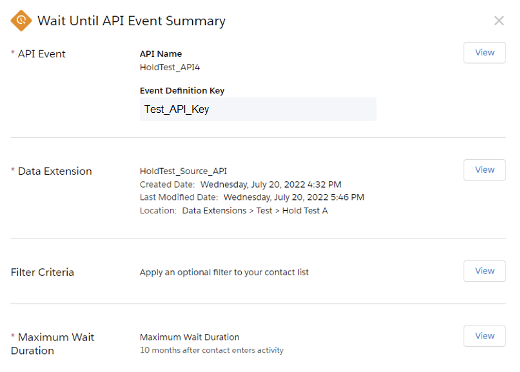
Our Digital Orchestration Goals
Use Case #1: Seamlessly connect prescriptive actions across channels to our sellers, partners, and customers.
Use Case #2: Pause and resume a digital email journey based on triggers from other channels.
Use Case #3: Connect analytics across the multichannel customer journey.
Use Case #4: Easily integrate data science to branch and personalize the customer journey.
Finding Success
Tuesday, 28 February 2023
An Easier Way to Secure Your Endpoints
| Challenge: Expertise | Challenge: Time | Challenge: Evidence |
| “My team can’t be experts on every new threat, or all be experts in threat hunting.” | “I don’t have enough time to go after every new threat, alert, patch and compromised device.” | “We can’t always identify which threats to prioritize or get to the root cause of every attack.” |
Sunday, 20 March 2022
Private 5G Delivered on Your Terms
Connecting everyone and everything
What separates Cisco Private 5G from the rest?
Saturday, 23 January 2021
Cisco’s Role in the Monumental Vaccination Effort
Big challenges require big solutions. But when it comes to technology for coronavirus vaccine access and administration, many of those big solutions already exist.
As you read this, COVID-19 vaccines are being rolled out in different capacities around the world. The troubling news is, getting the vaccines to the public is continuing to present an evolving array of challenges. Limited availability, complex transportation and storage, and phasing are all creating confusion. The good news is that technology is helping to overcome those challenges by building bridges between the government agencies in charge of the vaccination effort, the retail pharmacies and healthcare organizations administering the vaccines, and the communities who need them.
During the past nine months, Cisco has been powering an inclusive recovery through efficient vaccine administration; helping essential organizations stand up the technology and communications needed by medical and healthcare facilities, retail pharmacies, essential government services, and other frontline efforts. And, today, Cisco continues to do its part as a trusted technology partner. We’re helping enable vaccine administration by improving three key functions—communications and access, field operations and administration, and security and application performance.
Communications and access
By providing communications and access solutions—such as Cisco Webex and Webex Contact Center—we’re enabling better patient access and outreach, better care provider and administrative collaboration, and more virtual engagements. We’re also providing a more comprehensive way for government agencies, healthcare facilities, and retail sites to efficiently scale their efforts to address increased volume and equitable access to critical information and services.
Field operations and administration
With field operations and administration solutions—like networking, WiFi analytics, video, collaboration, and cloud-delivered location services and security—we’re helping organizations respond to dynamic community needs, set up field hospitals and mobile clinics, provide equitable access, improve citizen experiences, and simplify equipment monitoring.
Security and application performance
Finally, our innovative security and application performance tools—among them, application monitoring and management, IoT sensors, cameras, and cloud-enabled security—are ensuring the safety, security, privacy, performance, and compliance necessary for organizations to successfully administer vaccines and operate efficiently around the clock.
As you can imagine, vaccine administration systems will likely remain under immense pressure until the millions of people who need vaccinations get them. So, it is vital for government, healthcare, and retail organizations to keep these mission-critical services running as smoothly as technologically possible. That, as it turns out, is our strong suit.
Keep in mind, performing in this capacity is nothing new for Cisco. All of the solutions and use cases mentioned above are customer-validated and proven.
As it always has, Cisco provides its customers with solutions that help people and communities access technology, information, advice, and anything else they might require. We were here for our customers before the pandemic. We’re here for them today as we navigate our way through COVID-19 together. And as any trusted partner should, we will be here for our customers tomorrow to take on whatever comes next. That’s why so many leaders around the world, across all levels of government, healthcare, and retail, have trusted and relied on us to stand by them through their ongoing digital transformation efforts.
Tuesday, 10 March 2020
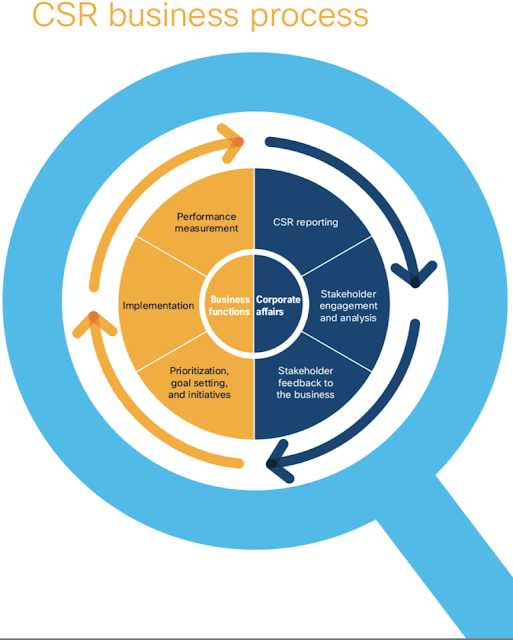
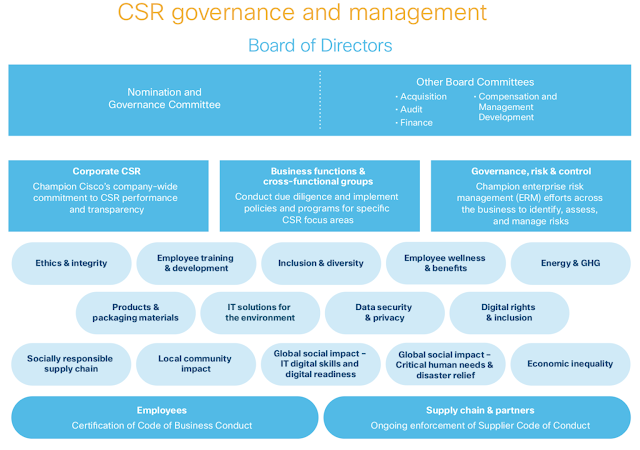
How Cisco manages corporate social responsibility
Corporate social responsibility (CSR) is core to our purpose, our culture, and how we invest. We focus on People, Society, and Planet—issues that align with our business strategy and where we can have the greatest potential for impact. Our success is built on a Conscious Culture, where trustworthiness and ethical conduct are expected and supported among our employees, suppliers, and business partners.
How we manage CSR
Corporate Affairs, as part of the Human Resources organization, champions Cisco’s strategic approach to CSR, including social investment programs and environmental sustainability. The organization also stewards our commitments to CSR performance and transparency. The Corporate Affairs team is responsible for:
◉ Defining and managing our social investment strategy and programs
◉ Driving CSR governance processes
◉ Collaborating with a broad range of stakeholders
◉ Conducting socio-economic research and developing data driven insights
◉ Assessing and monitoring CSR priority issues
◉ Producing our annual CSR Report
◉ Coordinating and ensuring cross-functional ESG alignment
Thursday, 9 January 2020
Bridging the divide: Getting IT and OT to work together for industrial IoT
We often hear customers describe what it is they want out of an IoT deployment: a dashboard with buttons that allows them to see data or analytics of that data to understand what is happening in the operating environment. It’s obvious they have a clear vision of the outcome they want, but they don’t know how to get there. And they can’t — at least, not by themselves. One of the biggest reasons why IoT projects fail is because line of business expectations aren’t managed correctly, or because IT and OT didn’t work together to validate if a solution is feasible with current technology and skill sets.
The IoT tech stack is complex and fragmented. Organizations have to pick the right sensors, select the machines to be connected, choose a connectivity method, and then build the networking, application, and business intelligence layers (often incorporating cloud and multiple applications) on top. To further complicate matters, companies are looking to connect many different (often legacy) machines that have never before been connected. Different protocols must be parsed and cleaned up so that technologies further up the stack can ingest and understand the data.
No single department is capable of navigating all the different technical options and making the best decisions for a seamless, secure IoT deployment. While OT may be able to choose sensors and machines to connect, and IT may be able to build the remainder of the tech stack, these decisions can’t be made in silos. The digitalization of machine data creates a technical convergence, and both sides must work together to make IoT work. IoT is a team sport.
When the right people come together to solve a business problem with IoT, it becomes much easier to build a successful solution. Four primary groups or individuals include:
The line of business:
Representatives from lines of business can articulate the business need. These people are experts in higher level business strategy, sales, marketing, how to go to market, etc. For the line of business, IoT is a means to an end to achieve a business objective. These people can envision the dashboard and contribute to process and organizational design. While they may or may not own the budget, the line of business defines and creates the demand for a business improvement.
IT department:
The IT department is responsible for the enterprise IT infrastructure. The department’s main concerns are security, scalability, and manageability. They work in a fast, dynamic environment. IT is always under pressure to get things done—and to do more with less. When it comes to an IoT deployment, the IT department is concerned with the tech stack from the network out to the edge.
OT department:
The OT department is generally responsible for the equipment on the shop floor. They are concerned about quality, uptime and maintenance of machinery that is typically two to three decades old. Often times, the machines produce data that doesn’t go anywhere. There’s a human/machine interface where operator receives data and makes decisions. The OT department plays a key role in connecting machinery on the shop floor for an IoT deployment.
Procurement:
Procurement is responsible for finding products and services at the best cost. Sometimes this means breaking up solutions and buying components piecemeal. It’s best to bring procurement on board sooner than later so that they understand that the broad spectrum of components in an IoT deployment come from one ecosystem of integration. If a solution is broken up into bits and pieces, none of the solution providers will feel motivated to deliver the best possible service.
Even with these parties at the decision-making table, there are likely to be gray areas. Organizations often have to experiment or partner with a provider for technology that they don’t have the skills to work with internally. Of course, it’s important to get the right skills at the right time for the right cost.
At Cisco, we work hard to pull together the key technologies and partners required to deliver seamless, secure solutions that span the manufacturing floor to the cloud. Our partner ecosystem consists of large systems integrators, service providers, OT partners, distributors, and a variety of others. We span and bring together both the IT and OT worlds to create harmony and cohesion across our customer’s organization, our Cisco partner ecosystem and through the solution itself via Cisco Validated designs to ensure a successful IoT initiative.
Saturday, 12 October 2019
Cisco DNA Center Real Time Event Notifications into Webex Teams!
Find out about network issues before your users do!
Cisco DNA center has a powerful issue correlation engine for enterprise wired and wireless networks. Taking real time feeds of network telemetry it is able to identify issues and provide context for resolution. The next question is what to do with the events? Some customers would like to send them to an email system, where as others would like to create a message in an instant messaging system.
Fortunately, there is a webhook based notification that can be used to process and handle issue notifications. This blog post provides a simple python script to send a notification to a Webex Teams room, or email server. Version 1.3.1 of Cisco DNA Center provides native email integration, so I will focus on the Webex Teams integration.
Getting Started
As with all of my examples, the sample code is posted on github.
The first step is to download the code and create a python virtual environment (the virtual environment is optional). You need to change directory into the WebHookServer directory.
git clone https://github.com/CiscoDevNet/DNAC-Platform
python3 -mvenv env3
source env3/bin/activate
cd DNAC-Platform/WebHookServer
The next step is to install the required python libraries
pip install -r requirements.txt
You will also need to edit the configuration file config/dummy_spark_config.py and add a Webex Teams roomId and provide a valid Webex Teams token. To get a token and find the API call to discover the roomID go to developer.webex.com .
AUTH="Bearer XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX"
# alerts room
ROOMID="XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX"
You need to run the server and it will listen on port 9000. This can be changed if required.
./server.py
Testing out the issue notifications
The next challenge is to generate an issue. Fortunately, I have provided a sample script to generate some “dummy” issues.
The client directory contains some “fake issues” that can be sent to the server for testing.
If you run the client.py program will no arguments, a list of valid issues is provided.
./client.py
Run with --event and a valid example.
Valid Examples:ap_down_eg, ap_flap_eg, border_dhcp_eg, device_unreachable_eg, swim_eg, new_flap_eg
The schema for issues changed between 1.3.0 and 1.3.1. There are examples for both old and new versions. New versions has prefix “new.” The new_flap_eg is an example of a new issue. I am going to send the new format example.
$ ./client.py --event new_flap_eg
Sending:new_flap_eg
200
The server will display the JSON payload, as well as sending it to the Webex Teams room.
Cisco DNAC configuration
Wednesday, 1 August 2018
5 Reasons Cloud UC and BroadSoft Are Top of Mind
I’d like to highlight five key reasons why I think our overview resonated so well.
1. Customer cloud UC perceptions have changed
We recently conducted a survey with over 1,000 IT decision makers from seven countries. In it, we learned that cloud UC is a key priority of their digital transformation strategies. 74% of respondents said they will choose a cloud provider in the next 24 months.