Thursday, 9 February 2023
Women Technical Leader Incubation Program (WTLI) in India
Tuesday, 5 July 2022
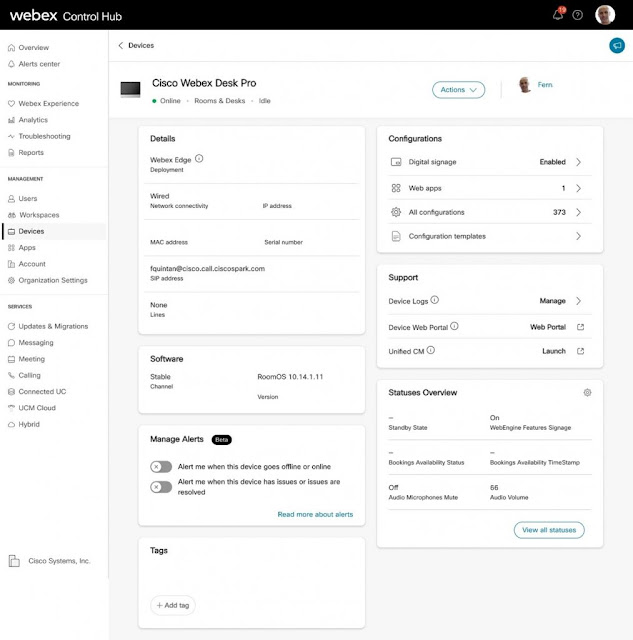
What IT loves about Webex Control Hub
We work from just about anywhere. Coffee shops, airplanes, kitchen tables. The nature of our work is hybrid and when we aren’t in shared spaces with our colleagues, we rely on our collaboration suite to keep us connected. As the collaboration leader for video endpoints across Cisco, my day revolves quite heavily around Webex and delivering consistent collaboration experiences to Webex users.
As we work across the world using collaboration tools both internally and externally, managing that experience is becoming more complex. With earlier tools, learning when, where, and why our collaboration services, devices, or applications faltered was like trying to find a rogue brace in 100,000 lines of code. Shortly after we migrated to our Cisco Collaboration Meeting Rooms Cloud solution, we began working on Webex Control Hub. Ever since, we’ve become smarter about pinpointing those rogue braces.
Control Hub is a centralized collaboration management portal that offers troubleshooting, analytics and compliance capabilities for our collaboration portfolio. We have multiple services, like Webex Meetings, Webex App, Webex Devices, Webex Calling, and with Control Hub, we get to see what’s happening across the board in our environment. In a word, it’s amazing.
Diving into Webex data to troubleshoot
In the past, let’s say Fernando called to escalate a connection issue he had with Webex Meetings. We’d have to wait on Cisco Technical Assistance Center (TAC) to get backend Webex data and send it our way. Then, we’d go down a rabbit hole trying to pinpoint the issue, pulling information from different sources while trying to piece together a picture of what went wrong. Meanwhile Fernando is frustrated he can’t join calls. It’s affecting his work productivity. It’s not great for business.
Today, when Fernando says he has a problem, we find it quickly. Control Hub populates a single dashboard with data from our entire environment, from aspects like users, devices, places, and services. Control Hub visually organizes that data to show me where Fernando is having issues, whether it’s a network issue, or a loose cable on his Cisco Webex Desktop Pro device. It’s a user-friendly interface, and in an instant, I spot when Fernando’s call is disrupted, for how long, what his bandwidth was, his latency – I get the entire picture, not pieces.
Winning with user and device management
Simplified support and APIs
Needles in haystacks are painful and unnecessary
Saturday, 25 June 2022
Our future network: insights and automation
Insights and automation will power our future network. Think of it as a circular process: collect data from network infrastructure. Analyze it for insights. Share those insights with teams to help them improve service. Use the insights to automatically reprogram infrastructure where possible. Repeat. The aim is to quickly adapt to whatever the future brings—including new traffic patterns, new user habits, and new security threats.
Insights
Automation
The Road Ahead
Tuesday, 3 May 2022
The SASE story II: How Cisco IT developed our SASE product amid an evolving industry landscape
As revealed in The SASE story, part I, the SASE model brings value to enterprise IT organizations looking to achieve connectivity and security resilience through a secure, efficient, hybrid architecture. In Part II, we’ll outline the journey we took to develop our Cisco SASE solution.
CloudPort: The precursor to SASE
Throughout the past decade, IT organizations have witnessed two significant trends: the migration of applications to the Cloud, followed by Hybrid Work. These trends caused IT leaders to think differently about how to better connect users to applications. Many — including Cisco IT — realized that networking and security problems can no longer be solved in isolation. To address this, Cisco IT embarked on a journey to build our own bespoke solution by combining different Cisco networking and security components, delivering SASE-like capabilities in an on-prem platform.
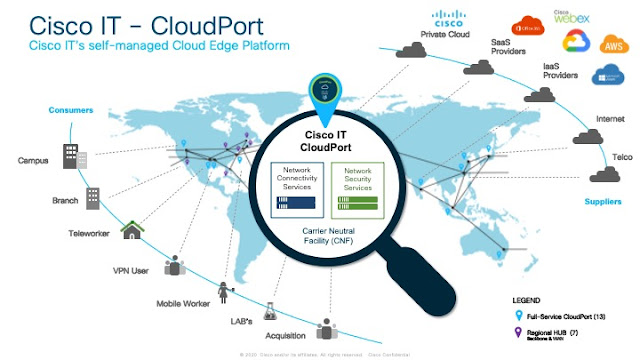
At a Cisco IT offsite in 2013, during a time when workloads were starting to migrate to the cloud, we drafted what is now the CloudPort vision on a hotel bar napkin. The plan was to deploy highly scalable networking and security hardware platforms in colocation facilities worldwide.
Initially, CloudPort was conceived in response to this Hybrid Cloud paradigm shift, providing us with the opportunity to strategically place our network edge directly with major ISPs and Cloud providers. Over time, we realized we could fuse security services directly into this architecture, which allowed us to bring together networking and security into a common platform. This was, effectively, a hardware- and co-lo-based precursor to current cloud-delivered SASE. The crux of this plan was that it allowed us to layer more and more services on top – offering similar capabilities (VPN, Firewall, Zero Trust Network Access, URL filtering, etc.) to what would become known as SASE.
A modernized “SASE” Hub
Adopting Cloud delivered SASE
Tuesday, 15 February 2022
The SASE story: How SASE came to be, and why it has quickly become the default architecture
Secure Access Service Edge (SASE) has quickly become one of the hottest topics related to cloud, networking, and security architectures. As Cisco engineers, we have seen hesitation and confusion among some customers on what SASE really means. We hope to answer most of those questions here.
What is SASE, and how is it related to the Cloud Edge, Zero Trust, and SD-WAN? SASE has positively impacted how we run our IT organization, and how we envision Enterprise IT customers will run theirs. To accurately explain what SASE is, and why SASE came to be, we must look at the evolution of how data is stored and transported within an enterprise.
Our journey started inside the data center
A decade ago, many of us lived in a data Center-centric world, and security was simpler to implement. Here at Cisco, we were moving data inside the four walls of our data centers, and we assumed complete trust. The corporate office, the MPLS circuits between sites, and the Cisco data centers were all within a trusted environment, which enabled us to meet our security and compliance requirements.
Move to hybrid cloud and hybrid work
Arriving at SASE
CloudPort and the evolution of SASE at Cisco
Saturday, 1 January 2022
How Cisco IT is solving multi-cloud management: a single pane of glass
Management of multi-cloud matures
 |
| Figure 1. Multi-cloud strategy adoption |
For enterprise IT organizations, the public cloud has become a staple at delivering software, infrastructure, security, and other capabilities at scale. Companies primarily adopt public cloud services for greater flexibility, faster time-to-market, and to take advantage of best-of-breed solutions while avoiding vendor lock-in. While SaaS platforms are the lion’s share of services consumed (48%), IaaS and PaaS combined make up 51% of public cloud spending (IDG).
When combined with an organization’s private cloud, the collective services available for business units to spin up applications and services rapidly help drive innovation and decrease the time-to-market. It’s no surprise that 74% of enterprises are now taking the best of both worlds and defining hybrid or multi-cloud strategies. In fact, the Boston-based research firm, IDC, has declared 2021 as the year of multi-cloud.
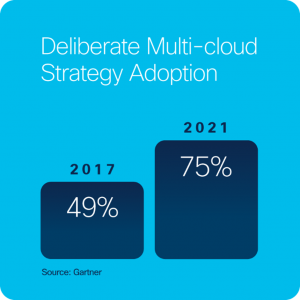
While cloud offerings have matured and consumption continues to increase, one could argue that how we manage multiple private and public cloud services has lagged consumption and is just now beginning to mature. Most IT organizations are experiencing a common set of challenges in how they and their internal customers manage their cloud services, how they can account for and identify owners of cloud services within their company, and a lack of visibility into the usage and costs for these services. In response, enterprises are now adopting a “deliberate” multi-cloud strategy — up from 49% in 2017 to 75% projected for 2021 by Gartner.
Evolving our multi-cloud management strategy
Like most enterprise organizations, Cisco has seen dramatic growth in the use of public cloud-based services over the past decade or more. In parallel, our internal infrastructure offerings continue to evolve in response to customer demand, and technological and feature advancements. Our challenges — which I’m sure we share with many — have included a lack of visibility into all the cloud services consumed (shadow IT), poor budgeting and cost control, inconsistent governance and security, and disparate user experiences.
Read More: 300-735: Automating and Programming Cisco Security Solutions (SAUTO)
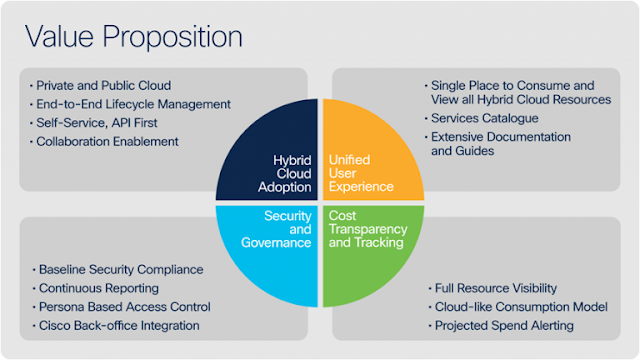
To respond, Cisco IT set out in 2017 to craft a strategy with “single pane of glass” visibility into multi-cloud services. We drafted a blueprint to include a knowledge base about services and how to choose them, methods to ease integration with data- and API-driven capabilities, holistic audit and compliance capabilities with security in mind, and consolidated monitoring and metering capabilities with pay-as-you-go modeling.
“Our goal has been to build a solution that provided a unified experience for all of our customers, regardless of whether they were consuming public or private cloud services,” notes Mayank Jain, Director of Software Engineering at Cisco and a member of the team that has worked on the problem. “We needed a solution that provided the ability for our customers to consume different cloud services and see what it’s costing them over time, all through a single pane of glass.”
Not all clouds are alike
A purpose-built multi-cloud management solution
What’s next?
Sunday, 5 December 2021
Zero Trust framework improves workforce security and productivity, while cutting support costs
Like most companies, Cisco is committed to continually improving security while simultaneously simplifying the user experience.
We’ve learned some important lessons along the way.
There are multiple points where user ID and password credentials can be potentially compromised. For example, employees sometimes chose to ignore best practices by utilizing easy-to-remember passwords such as “123456.” Others would share their Cisco passwords or use them externally for non-business-related applications—essentially utilizing their passwords everywhere.
When we relied only on the password login process, it is estimated that about 80 percent of all hacks were caused by credentials/identity theft. Other points of concern included new-hire onboarding or credentials delivery, password resets on behalf of users, password-related communications, and overall handling or management of password details. All can contribute to potential risks.
Further complicating matters, when most of our workforce went remote in early 2020, it became confusing and taxing for users to know how to access different applications. For example, some apps required a Virtual Private Network (VPN) connection, while others could be accessed directly. Like many other companies, Cisco invested in VPN expansion to support employees working from home, while also rolling out Zero Trust on a limited basis initially (more details below).
As the lines increasingly blurred between work and home life, many remote workers became frustrated at connecting via VPN and enduring the authentication process potentially multiple times a day. It can be tiring for users to keep track of which applications need VPN and which don’t – reducing their productivity. Ultimately, using a VPN when the workforce is almost fully remote can be inefficient, especially when we’re sending data back over the corporate network, only to have it eventually return to the cloud.
Zero Trust framework delivers secure, uniform user experience
As a result, Cisco decided to move from a traditional, network-based perimeter and VPN model to a Zero Trust model. Zero trust is not a single solution but a framework of solutions that verify a device, establish policy, and continually monitor device behavior. Multi-Factor Authentication is a key element of this approach. We started deploying multi-factor authentication in November 2020 for several applications, then expanded its coverage in 2021 to many additional applications, including Microsoft Office 365.
Our overall goal for Zero Trust and multi-factor authentication is to provide a secure, uniform experience while accessing applications, wherever users or applications are located. From a technical perspective, we had four objectives:
1. Implement an architecture that would allow secure, VPN-free access to some of our most-visited internal and SaaS applications
2. Validate user and device trust on a per-app basis, with an ability to set per-app access policies
3. Improve our authentication experience by reducing the burden on users
4. Build this transition seamlessly, requiring zero user action, and without any outages or distractions
Zero Trust helps us achieve these goals by incorporating user/device trust policies for remotely accessing applications. Users enjoy a “borderless experience” by accessing the network from anywhere, without having to connect through a VPN.
Instead of relying only on user ID and password credentials, Zero Trust adds a layer of protection. It leverages a user-identity certificate that is securely deployed to managed endpoints by our device management suite. This certificate then acts as the first factor of authentication, saving users the step of having to type in their username and password. This also reduces the likelihood that users will save their corporate identity and password in their browser for convenience.
After establishing user trust, the solution validates device trust and health—starting with the assumption that if a device is managed by our corporate device management platforms, then it must have a good baseline security posture. We perform an additional device health check during every authentication transaction to ensure that the device is running the latest software, screen lock, disk encryption, firewall, and anti-virus agent. This real-time check is conducted by the Duo Beyond Device Health app, which continuously operates in the device’s background.
With Zero Trust, when a user tries to log in to an application, our corporate SSO identity engine checks the user and device certificate, does a real-time health assessment of the device, and finally triggers a second-factor notification before allowing user access.
Zero Trust saves time, boosts productivity
Since Zero Trust was implemented, adoption metrics show that it is saving Cisco employees more than 410,000 VPN authentications per month. Based on Cisco IT internal analyses, it takes about 45 seconds for each VPN authentication. This represents 307,500 minutes, or 5,125 hours, saved per month – an annual savings of 61,500 hours. Assuming an average hourly cost per employee of $55, we can value this productivity improvement at $3.4 million per year for Cisco employees. This also represents an optimization of the application information traffic flowing over the company’s core network and offloaded through direct internet access.
Since incorporating controls for device health and trust at the application layer, we’ve substantially improved our ability to react to device risk. For example, we’re conducting approximately 5.76 million device health checks automatically per month. This has allowed us to identify 86,000 devices per month that users have self-remediated. That’s 86,000 potential compromises effortlessly averted.
While there were some concerns about increased support call volume when introducing device health checks for borderless access, only 0.6 percent of users have contacted our help desk for support—which is actually less than the 7 percent rate of help-desk requests for security deployment, password reset, device remediation, and support calls for authentication based on internal benchmark. We feel that the easy-to-follow remediation steps within the Duo Device Health App played a key role in minimizing our support numbers. The deployment had a minimal impact, keeping overall costs low and providing a better user experience.
Subsequently, fewer analysts have been required to provide support, leading to an estimated $500,000 per year savings in helpdesk support costs. In addition to cutting support costs and improving security, the Zero Trust Multi-Factor Authentication framework has improved productivity because users don’t need to waste time logging in to the VPN.
The future of Zero Trust
Sunday, 21 November 2021
Driving down IT OPEX with a Webex bot
Every IT organization strives for excellence by continuously driving down their operating expenses (OPEX) while providing the best-in-class experience to their user base. Several factors affect OPEX, such as increasing IT cases that require more resources to address recurring requests. Having a focused approach to reduce cases can significantly optimize on cost and improve the efficiency of IT Operations teams. One way that Cisco IT is driving down OPEX is by harnessing the power of automation.
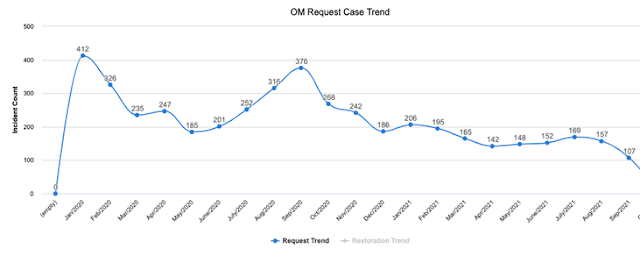
By the end of September 2020, the number of service request cases to Management & Finance IT’s (M&F IT) Order Management (OM) Automation team in Cisco had been cut by half and operational costs reduced by one-third. The solution: a self-help Webex bot called ‘OM-BOT’ that the OM Automation team created to assist with service request cases.
OM-BOT helps users answer queries without requiring any IT teams’ intervention. Below are some benefits of implementing OM-BOT:
◉ Avoided 140 IT cases per month
◉ Improved Mean Time to Resolution (MTTR): cases get created in the correct queue, reducing the time it takes to resolve cases
◉ Improved case routing: OM-BOT links user to the correct team to solve their cases
◉ Enhanced user experience: we meet with users weekly to discuss feedback, most of it positive
From January 2020 to September 2020, we, the OM IT Support Team, were receiving an average of 285 cases per month (see Figure 1). However, in the last six months, we’ve seen an average of 145 cases per month — a reduction of about 48.5 percent, most of which can be attributed to the usage of OM-BOT.
Why did we build OM-BOT?
How did we build OM-BOT?
Did we face any challenges?
What is the roadmap ahead for the bot?
Tuesday, 26 October 2021
Plug & Play (PnP) enables faster onboarding of new offices
Most IT engineers can agree that device provisioning for new offices is tedious, time-consuming, and error-prone. Fortunately, our Cisco IT Customer Zero team—which tries out the latest Cisco solutions and integrations to prove value and share experiences—has discovered that it doesn’t need to be that way.
By leveraging the Plug & Play (PnP) capability in Cisco DNA Center, we’ve managed to slash provisioning time by over 50%, while improving the engineer/user experience, reducing configuration issues, and enhancing security.
Prior to PnP, provisioning new offices was tedious and error-prone
Before PnP, our process was manual and slow, with a high risk of producing errors. In the weeks before we set up a switch, engineers had to scour a 501-page playbook to find the right configuration for the device model and office size. They would then travel to the office and paste in the appropriate code snippets via the command-line interface (CLI).
During this process, engineers could easily type an incorrect character or miss a line/s of code. These types of mistakes were responsible for the vast majority of Day-1 problems. The process also required engineers to remain for Day-1 support.
PnP provides the ability to automate onboarding, eliminating errors and saving time
Today, Cisco DNA Center’s PnP capability allows us to onboard new sites much faster by automating the onboarding of devices and the configuration of underlay routing (Figure 1). Switches automatically connect to Cisco DNA Center and retrieve the correct template, based on their serial number and tags. Engineers no longer have to engage in the time-consuming activity of searching through the playbook for the right configuration. PnP also reduces the need to type command-line instructions and cut-and-paste blocks of code. We are now able to standardize our configuration with the use of templates and version control. Instead of using Microsoft Word or Excel spreadsheets, we can create templates that are used across multiple devices with the concept of variables allowing us to be adaptable to each device using templates and tags, saving time and ensuring compliance. Finally, with PnP, engineers no longer need to go on-site for Day-1 support.
Tuesday, 7 September 2021
How the network team’s bold steps + agile mindset launched a cloud-ready backbone
In 2014, we realized our world in network engineering was changing rapidly. Like many IT organizations, we saw a shift to the internet and cloud services in our network traffic. Over that year alone, we observed a 200% increase in peak internet and cloud traffic. That’s when we knew our network needed to change to accommodate the evolution of conducting business at Cisco.
Our network was designed and evolved with the bulk of our enterprise traffic originating from and destined for resources within Cisco’s “four walls.” The growing demand for traffic to cloud providers and SaaS services meant a quick pivot was necessary. As a result, our initial step was to build Cisco IT CloudPorts in strategic carrier-neutral facilities, which allowed us to quickly secure connections between the Cisco enterprise and the outside world.
Our CloudPort hubs provide high availability and flexibility to turn up new connectivity quickly, but our private backbone connecting the CloudPorts needed enhancement. With more and more business reliance on public cloud and SaaS workloads, the resiliency and performance required for CloudPort connections grew. We needed the capability to quickly respond to network issues and use our backbone to route traffic from one region to another.