I was recently able to grab some time with a Cisco customer to hear about their experience with Cisco Stealthwatch Cloud, a SaaS-based Network Detection and Response (NDR) solution. Aspire Technology Partners, a Managed Security Service Provider, explained their use of the product for one of its customers that was in a dangerous situation involving some slippery malware floating around in the network. As I worked on this case study, I couldn’t help but think of one thing in particular…The North Carolina State Fair.
I am a relatively new North Carolina resident. Prior to working from home, I was no stranger to the commute up I-40 to building 9 of Cisco’s RTP campus. As I found my way around my new home state, I kept hearing that the NC State Fair is a rite of passage for new residents. I decided to check it out. What an experience that was. I got to see a monster truck show, a lot of farm animals and the world’s largest pumpkin. I also ate more fried food on a stick than my heart could handle. We also got to play whack-a-mole, a game that requires you to smash each mole as they poke their heads out of the machine with a mallet. As you progress, you earn points for each successful ‘whack’. Unfortunately, you can never really win since they never stop popping up.
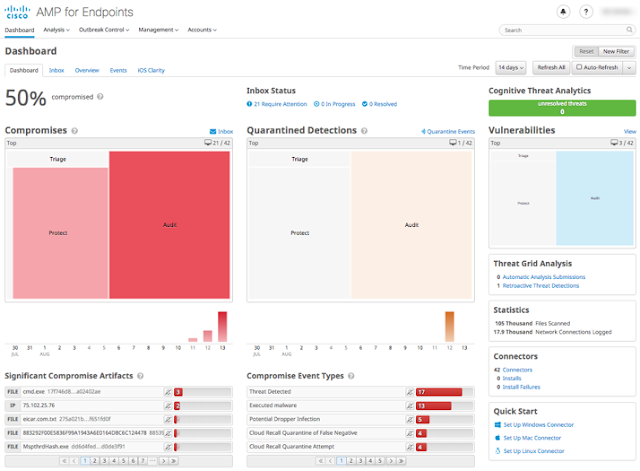
Without an NDR tool like Stealthwatch Cloud in place, the modern Security Operations Center (SOC) is effectively doing the same thing. Their endpoint and perimeter solutions, while critical to network safety, are playing whack-a-mole: stomping on malware and isolating devices as they become infected while still knowing that the network is still at risk. Without east-west monitoring and visibility into encrypted traffic, businesses are susceptible to subsequent attacks once malware has established a foothold on the network. If your security team can’t identify how threats are accessing the network, malware could stay hidden for months…or even years.
Aspire Technology Partners was working with a customer who deployed an Incident Response (IR) team to contain a threat, believed to be ransomware, that was surfacing all over their network. The Aspire SOC team decided to deploy Stealthwatch Cloud to track the malware through east-west traffic monitoring. Here are a few reasons why Stealthwatch Cloud was critical to not only detecting the threat, but also stopping it dead in its tracks:
Stealthwatch Cloud deploys almost instantly
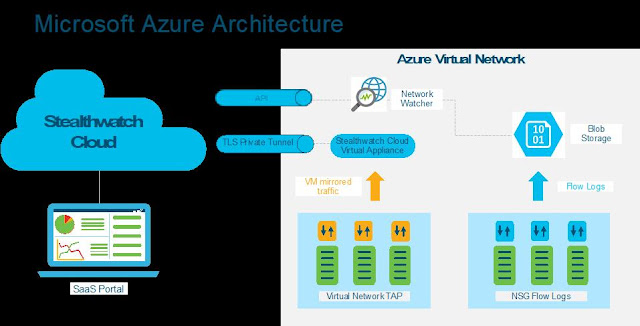
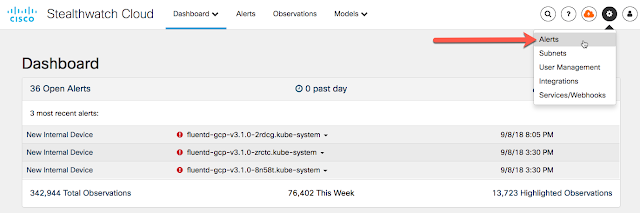
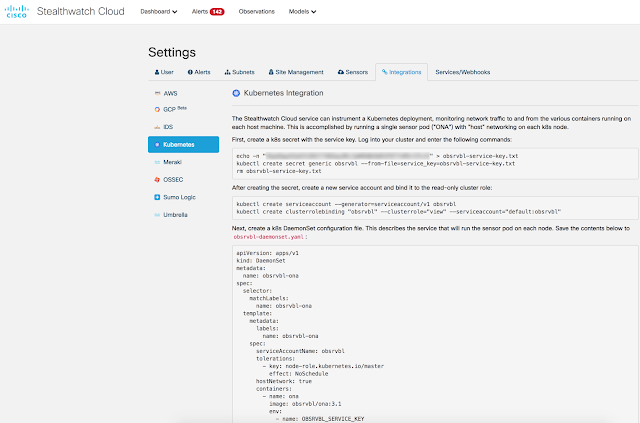
The Aspire SOC team deployed Stealthwatch Cloud on the customer’s private network in just 2 hours. This allowed the team to immediately start digging through east-west flows to hunt down the threat.
Stealthwatch Cloud detects threats behaviorally
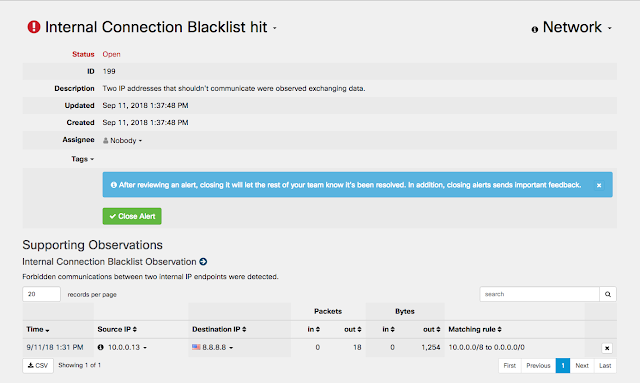
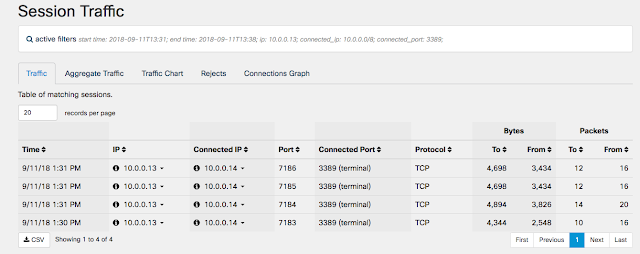
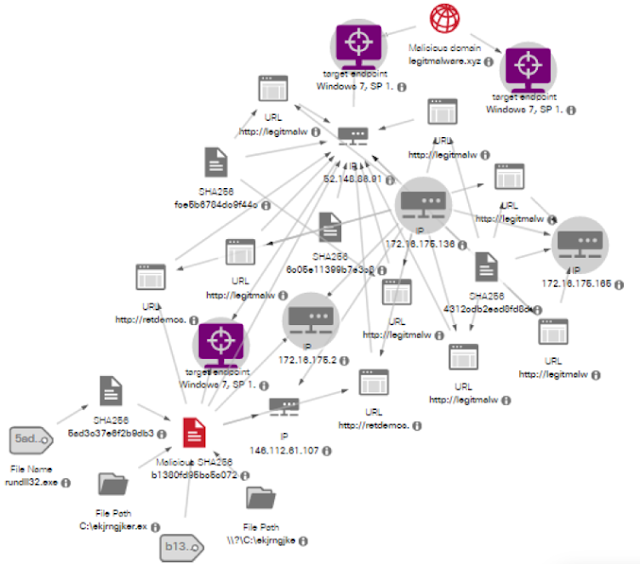
Stealthwatch Cloud uses the network itself as a sensor, and offers both automated threat detection and the ability to search manually for threats. The team needed to identify the foothold of the attacker, and with comprehensive visibility provided by Stealthwatch Cloud, was able to discover that the malware found its way into the network via a vulnerable 3rd party device. No endpoint or agent-based solution could have figured this out.
Built-in remediation methods enable quick response to threats
Stealthwatch Cloud offers a wealth of integrations with 3rd party and Cisco solutions that allow users to go one step further and communicate across their organization, pivot into other tools to carry on an investigation and much more. Alerts come alongside their supporting observations that contain bits of context that users can leverage as they continue to investigate. A simple firewall rule blocked out this malware for good.
So, stop playing whack-a-mole, unless you’re at the fair. Even with proper agent-based and perimeter protection, your network may still be at risk. You can fill that gap and gain comprehensive visibility on-prem or in the cloud with Stealthwatch Cloud.