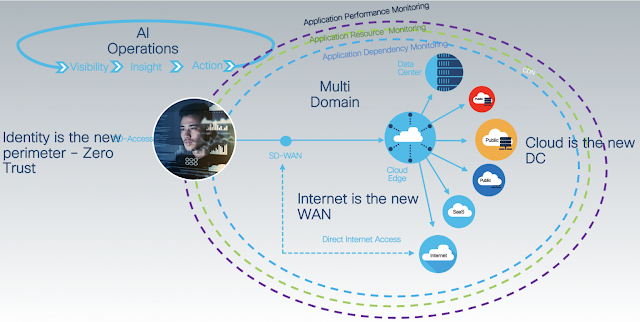
Nearly every day we can read about “ransomware” holding another organization’s data hostage, shutting their operations down, or disrupting their supply chain. Commercial enterprises. Major utilities. Large healthcare providers. Processing facilities. Even small businesses aren’t safe from being the target of these attacks.
The key to preventing your organization from falling prey to ransomware is to keep several steps ahead of hackers. In many cases, the tools you need to protect your data are already available in your network. With the recent introduction of Continuous Trusted Access and the new Cisco Trust Analytics you can now secure your network from several potential attack vectors.
Trust Analytics is part of Cisco SD-Access, Cisco’s best-of-breed Zero Trust solution for the workplace. Trust Analytics detects traffic from endpoints that are exhibiting unusual behavior by pretending to be trusted endpoints using MAC Spoofing, Probe Spoofing, or Man-in-the-Middle techniques.
When anomalies in the network are detected (see Figure 1), Trust Analytics lowers the Trust Score for the endpoint to limit or completely deny access to the network through integration with Cisco Identify Services Engine (ISE). In this blog, we will describe how Trust Analytics can help to secure your network.
Figure 1: When anomalies in the network are detected, Trust Analytics lowers the Trust Score for the endpoint to limit or completely deny access to the network.
Device Spoofing
One tactic used by hackers and ransomware to gain unauthorized access to a network is to take over or spoof the identity of a trusted device. An example of an identity takeover is when someone opens an email and unleashes ransomware that gives control of the device to hackers. The ransomware then moves laterally through the network, infecting as many devices as possible. The spread of ransomware can be very fast, shutting the network down before IT is even aware of the threat.
An alternative to taking over a device is to spoof or steal its identity. In this case, a rogue device pretends to be a trusted device to gain access to the network. Common methods for spoofing endpoints include:
MAC spoofing is a means for stealing the identity of an endpoint. Trusted endpoints are identified either by a secure method like 802.1x authentication or by a simple list of trusted MAC addresses such as with MAC Authentication Bypass (MAB). MAB is useful for authenticating IoT devices that are not capable of 802.1x or that do not have a user. However, MAB leaves an opening for a rogue device to impersonate the MAC address of an authorized endpoint to gain that device’s access and privileges. Often, the hacker will disconnect the authorized endpoint, making the attack easier to carry out and harder to detect.
Probe spoofing involves a rogue device pretending to be a legitimate endpoint of a trusted class like IP phones and video cameras. Often these devices are identified from their traffic profile (i.e., MAC address manufacturer, DHCP options, etc.) By impersonating a trusted class of device, a rogue device may be able to gain privileged network access.
Man-in-the-Middle spoofing is an attack where the rogue device is physically inserted between the endpoint and access point (AP). The endpoint is still able to communicate with the AP but now the rogue device can inspect traffic and inject traffic into the flow.
Zero Trust
When a rogue device successfully spoofs the identity of an endpoint, it is able to exploit the trust the endpoint has been granted. The best defense, then, is to dynamically assess the trustworthiness of each endpoint. This is a key pillar to deploying a “zero trust” network. Certainly, devices must be granted trust so that work can get done. However, because spoofing is a potential threat, the trust for each device must be reevaluated on a continuous basis.

Figure 2: A hacker attempts to spoof the identity of a camera to gain network access. When the hacked camera begins to uncharacteristically reach out into the network, the anti-spoofing engine identifies the activity as an anomaly. The Trust Score for the hacked camera is then dynamically adjusted to prevent the device from communicating with other devices and spreading ransomware.
Figure 2 shows how the trust level of devices can be continuously monitored in a network. In this example, a hacker has taken over or spoofed the identity of a camera. The hacker then attempts to use the network access and privileges granted to the camera to gain further access into the network.
In this case, however, anti-spoofing detection is in place. The camera is part of a trusted class of device with well-known operating characteristics which have been captured in a baseline profile. Through artificial intelligence (AI) and machine learning (ML), the Cisco anti-spoofing AI/ML engine verifies that current operation matches expected behaviors.
A fully trusted device (Trust Score of 10) has full access and privileges. When the hacked camera begins to uncharacteristically reach out into the network, the anti-spoofing engine identifies the activity as outside of the camera’s baseline.
As the device deviates from its baseline, its Trust Score dynamically drops. At a Trust Score of 4 to 7, for example, network access could be limited by dynamically changing the device’s Scalable Group Tag (SGT). This could allow the device to continue to send data but with all privileges revoked until the device can be evaluated or a remediation action taken. In the case of a camera, network access could be limited to providing video tagged with an alert while peer-to-peer traffic is halted to prevent the device from communicating with other devices and spreading ransomware. At a low level (Trust Score of 1 to 3), the device may be denied access altogether until the cause of its rouge behavior can be identified.
The engine also evaluates activity in terms of other factors that can impact the Trust Score, including threat metrics, known spoofing behaviors, vulnerability status, anomalous behavior, and posture metrics. Depending upon the result, the anti-spoofing engine may dynamically adjust the Trust Score for the device.
Anti-spoofing is powerful technology and, as part of Cisco SD-Access, works in conjunction with other Cisco security solutions to better protect your organization. Because anti-spoofing detection is implemented on a device-by-device basis, only the device deviating from its baseline has its Trust Score, network access, and privileges reduced. In addition, deviations are detected as they happen, enabling a Cisco SDA-enabled network to take immediate action to isolate hacked devices and prevent a full ransomware outbreak. This is Cisco’s Continuous Trusted Access.
Already in Your Network
Trust Analytics is yet another powerful tool from Cisco for deploying secure networks. The anti-spoofing capabilities of Trust Analytics are a part of
Cisco Software-Defined Access, a solution with Cisco Digital Network Architecture (Cisco DNA). With these technologies, IT can manage the complete lifecycle for Zero Trust to better protect their network.
One of the best things is that Trust Analytics, through DNA Center, is already in your network. You don’t have to add a new box or start a new subscription to deploy Cisco’s AI/ML spoofing detection and protection. All it takes is enabling the capability under endpoint analytics in DNA Center.
Leverage the full power of your Cisco network to provide better security through
DNA Center.
Source: cisco.com