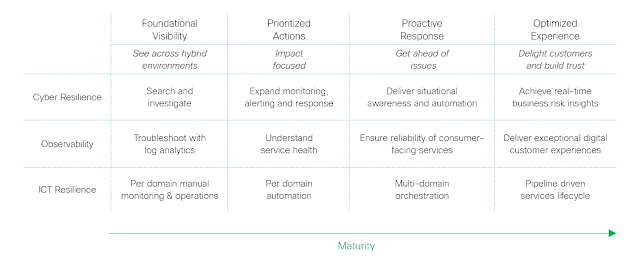
Cisco has been involved with PCI since the outset, having a seat on the board of advisors and helping craft the development of PCI standards through different evolutions. Cisco has consulted extensively with customers to help meet the requirements and provided extensive user friendly documentation on how customers can meet the requirements, both in minimizing the scope of the assessment as well as in ensuring security controls are present. We have released systems that are PCI compliant in control aspects as well as data plane aspects, and have built-in out-of-the box audit capabilities in a number of infrastructure based, and security based, solutions.
The purpose of this blog is to walk into the PCI DSS 4.0 with a focus on architects, leaders, and partners who have to navigate this transition. We will discuss what is new and relevant with PCI DSS 4.0, its goals and changes. We will then explore products and solution that customers are actively using in meeting these requirements, and how our products are evolving to meet the new requirements. This will be targeted to teams who already have been on the PCI journey. We’ll transition to an expansion into PCI DSS in more detail, for teams that are newer to the requirements framework.
One thing that is important to note about the 4.0 update, is it will be a phased rollout. Phase 1 items (13 requirements) had a deadline of March 31, 2024. The second phase is much larger and more time has been given, but it is coming up soon. Phase 2 has 51 technical requirements, and is due May of 2025.
What’s new in PCI DSS 4.0, and what are its goals?
There are many changes in PCI DSS 4.0. these were guided by four overarching goals and themes:
Continue to meet the security needs of the payments industry.
Security is evolving at a rapid clip, the amount of public CVE’s published has doubled in the past 7 years (source: Statista). The evolving attack landscape is pushing security controls, and new types of attack require new standards. Examples of this evolution are new requirements around Multi-Factor authentication, new password requirements, and new e-commerce and phishing controls.
Promote security as a continuous process
Point in time audits are useful but do not speak to the ongoing rigor and operational hygiene needed to ensure the proper level of security controls are in place in a changing security environment. This step is an important step in recognizing the need for continual service improvement vis-a-vis an audit. This means that process will be have additional audit criteria in addition to the application of a security control.
Provide flexibility in maintaining payment security
The standard now allows for risk based customized approaches to solving security challenges which is reflective to both the changing security environment, and the changing financial application environments. If the intent of the security control is able to be met with a novel approach, it can be considered as fulfilling a PCI requirement.
Enhance validation methods and procedures for compliance
“Clear validation and reporting options support transparency and granularity.” (PCI 4.0 at a glance). Clarity in the measurements and reporting is articulated. This is important for a number of factors, you can’t improve what you don’t measure, and if you’re not systematically tracking it in well-defined language, it is cumbersome to reconcile. This focus will make reports such as the attestation report more closely aligned to reports on compliance and self-assessment questionnaires.
How Cisco helps customers meet their PCI Requirements.
Below is a table that briefly summarizes the requirements and technology solutions that customers can leverage to satisfy these requirements. We will go deeper into all of the requirements and the technical solutions to these.
A more detailed look at the requirements and solutions is below:
Requirement 1: Install and Maintain network security control.
This requirement is will ensure that appropriate network security controls are in place to protect the cardholder data environment (CDE) from malicious devices, actors, and connectivity from the rest of the network. For network and security architects, this is a major focus of applying security controls. Quite simply this is all the technology and process to ensure “Network connections between trusted and untrusted networks are controlled.” This includes physical and logical segments, networks, cloud, and compute controls for use cases of dual attached servers.
Cisco helps customers meet this requirement through a number of different technologies. We have traditional controls include Firepower security, network segmentation via ACI, IPS, SD-Wan, and other network segmentation items. Newer technologies such as cloud security, multi cloud defense, hypershield, Panoptica and Cisco Secure Workload are helping meet the virtual requirements. Given the relevance of this control to network security, and the breadth of Cisco products, that list is not exhaustive, and there are a number of other products that can help meet this control that are beyond the scope of this blog.
Requirement 2: Apply secure configurations to all system components.
This requirement is to ensure processes for components are in place to have proper hardening and best practice configurations applied to minimize attack surfaces. This includes ensuring unused services are disabled, passwords have a level of complexity, and best practice hardening is applied to all system components.
This requirement is met with a number of controller based assessments of infrastructure, such as Catalyst center being able to report on configuration drift and best practices not being followed, Meraki, and SDWan as well. Multivendor solutions such as Cisco NSO can also help ensure configuration compliance is maintained. There are also numerous CX advanced services reports that can be run across the infrastructure to ensure Cisco best practices are being followed, with a corresponding report and artifact that can be used.
Requirement 3: Protect stored account data.
This requirement is application and database settings, and there isn’t a direct linkage to infrastructure. Analysis of how account data is stored, what is stored, and where it is stored, as well as cursory encryption for data at rest and the process for managing these, are covered in this requirement.
Requirement 4: Protect cardholder data with strong cryptography during transmission over open, public networks
This requirement is to ensure encryption of the primary account number when transmitted over open and public networks. Ideally this should be encrypted prior to transmission, but the scope applies also to wireless network encryption and authentication protocols as these have been attacked to attempt to enter the cardholder data environment. Ensuring appropriate security of the wireless networks can be done by the Catalyst Center and Meraki in ensuring appropriate settings are enabled.
Requirement 5: Protect all systems and networks from malicious software
Prevention of malware is a critical function for security teams in ensuring the integrity of the financial systems. This requirement focuses on malware and phishing, security and controls, across the breadth of devices that can make up the IT infrastructure.
This requirement is met with a number of Cisco security controls, Email security, Advanced malware protection for networks and for endpoints, NGFW, Cisco Umbrella, secure network analytics, and encrypted traffic analytics are just some of the solutions that must be brought to bear to adequately address this requirement.
Requirement 6: Develop and Maintain secure systems and software
Security vulnerabilities are a clear and present danger to the integrity of the entire payments platform. PCI recognizes the need for having the proper people, process, and technologies to update and maintain systems in an ongoing basis. Having a process for monitoring and applying vendor security patches, and maintaining strong development practices for bespoke software, is critical for protecting cardholder information.
This requirement is met with a number of controller based capabilities to assess and deploy software consistently and at speed, Meraki, Catalyst Center, ACI, Firepower and SD-Wan, all have the ability to monitor and maintain software. In addition, Cisco vulnerability manager is a unique capability to take into account real world metrics of publicly disclosed CVE’s in order to prioritize the most important and impactful patches to apply. Given the breadth of an IT environments software, attempting to do everything at equal priority means you are systematically not addressing the critical risks as quickly as possible. In order to address your priorities you must first prioritize, and Cisco vulnerability manager software helps financials solve this problem.
Requirement 7: Restrict access to cardholder data by business need-to-know
Authorization and application of least privilege access is a best practice, and enforced with this requirement. Applied at the network, application, and data level, access to critical systems must be limited to authorized people and systems based on need to know and according to job responsibilities.
The systems used to meet this requirement are in many cases, shared with requirement 8. With zero trust and context based access controls we include identification in with authorization, using role based access controls and context based access controls. Some of these can be provided via Cisco identity services engine, which has the ability to take into account a number of factors outside of identity (geography, VPN status, time of day), when making an authorization decision. Cisco DUO is also used extensively by financial institutions for context based capabilities for zero trust. For network security enforcement of job roles accessing the cardholder data environment, Cisco firepower and Software Defined access have the capabilities to make context and role based access decisions to help satisfy this requirement. For monitoring the required admin level controls to prevent privilege escalation and usage of root or system level accounts, Cisco Splunk can help teams ensure they are monitoring and able to satisfy these requirements.
Requirement 8: Identify users and authenticate access to system components
Identification of a user is critical to ensuring the authorization components are working. Ensuring a lifecycle for accounts and authentication controls are strictly managed are required. To satisfy this requirement, strong authentication controls must be in place, and teams must ensure Multi-factor authentication is in place for the cardholder data environments. They also must have strong processes around user identification are in place.
Cisco ISE and Cisco Duo can help teams satisfy the security controls around authentication controls and MFA. Coupled with that, Cisco Splunk can help meet the logging and auditing requirements of ensuring this security control is acting as expected.
Requirement 9: Restrict physical access to cardholder data
“Physical access to cardholder data or systems that store, process, or transmit cardholder data should be restricted so that unauthorized individuals cannot access or remove systems or hardcopies containing this data.” (PCI QRG). This affects security and access controls for facilities and systems, for personnel and visitors. It also contains guidance for how to manage media with cardholder data.
Outside the typical remit of traditional Cisco switches and routers, these devices play a supporting role in supporting the infrastructure of cameras and IOT devices used for access controls. Some financials have deployed separate air gapped IOT networks with the cost efficiencies and simplified stack Meraki devices, which simplifies audit and administration of these environments. The legacy proprietary camera networks have been IP enabled, and support wired and wireless, and Meraki MV cameras offer cost affordable ways to scale out physical security controls securely and at speed. For building management systems, Cisco has a suite of IOT devices that support building physical interface capabilities, hardened environmental capabilities, and support for IOT protocols used in building management (BACNET). These can integrate together and log to Cisco Splunk for consolidated logging of physical access across all vendors and all access types.
Requirement 10: Log and monitor all access to system components and cardholder data
Financial institutions must be able to validate the fidelity of their financial transaction systems and all supporting infrastructure. Basic security hygiene includes logging and monitoring of all access to systems. This requirement spells out the best practice processes for how to conduct and manage logging of infrastructure devices that allow for forensic analysis, early detection, alarming, and root cause of issues.
Cisco and Splunk are the world leader in infrastructure log analytics for both infrastructure and security teams. It is deployed at the majority of large financials today to meet these requirements. To compliment this, active synthetic traffic such as Cisco Thousand Eyes and Accedian help financials detect failures in critical security control systems faster to satisfy requirement 10.7.
Requirement 11: Test security of systems and networks regularly
“Vulnerabilities are being discovered continually by malicious individuals and researchers, and being introduced by new software. System components, processes, and bespoke and custom software should be tested frequently to ensure security controls continue to reflect a changing environment.” (PCI QRG)
One of the largest pain points financials face is the management of applying regular security patching across their entire fleet. The rate of CVE’s released has doubled in the past 7 years, and tools like Cisco Vulnerability management is critical prioritizing an infinite security need against a finite amount of resources. Additional Cisco tools that can help satisfy this requirement is: Cisco Secure Network Analytics (11.5), Cisco Advanced Malware protection (11.5), Cisco Catalyst Center (11.2), Cisco Splunk (11.6).
Requirement 12: Support information security with organizational policies and programs
People, process, and technology all need to be addressed for a robust security program that can satisfy PCI requirements. This requirement focuses on the people and process that are instrumental in supporting the secure PCI environment. Items like security awareness training, which can be addressed with Cisco U, are included. Cisco CX has extensive experience consulting with security organizations and can help review and create policies that can help the organization stay secure. Finally, having a Cisco Incident Response program already lined up can help satisfy requirement 12.10 for being able to immediately respond to incidents.