While hybrid work is not a new concept, it continues to evolve as we gather more information about employee work preferences and customers’ workplace and real estate goals. At Cisco, we leverage the insights gained from our own hybrid work environments, including our offices and collaboration centers, to shape our approach. In this blog, we will focus on two of our Hybrid Work building pillars—supporting hybrid work and digitizing real estate—and how data plays a vital role in optimizing workspaces. The remaining pillars, corporate sustainability and employee health and wellness, will be covered in our next blog.
Support Hybrid Work: Designing Spaces that Matter
Even as employees return to the office post-pandemic, companies are reconfiguring their real estate portfolios to align with their return-to-work strategies. Cisco has been proactive in reimagining the workplace by investing in collaborative hubs and, in some cases, downsizing office spaces to prioritize other areas.
Toronto & Chicago
Our hybrid work journey began with the design of an innovation center in Toronto, aimed at inspiring innovation and investment in Digital Transformation. This office, although constructed before the pandemic, marks some of our first steps in creating smart and collaborative workspaces. By leveraging a single converged network powered by Power over Ethernet (PoE) technology, we connected people, processes, and data, enhancing productivity and optimizing energy usage. Over time, we made adjustments to the space based on insights gathered, including downsizing the overall floorplate. Today, the Toronto office serves as a studio to educate people on the hybrid work journey.
In Chicago, our office layout was designed to accommodate a pre-pandemic work environment, with employees spending more time in the office. The majority of the layout was dedicated to “me” spaces (70%), such as personal offices and individual workstations, while the remaining portion focused on “we” spaces (30%) to foster collaboration. This office serves as a showcase for Cisco’s technology and collaboration devices, furthering our hybrid work journey.
Penn1 & Atlanta
Throughout each these projects and our work -from-home experiment during the pandemic, we collected significant data to inform our future space designs. A 2021 Cisco Employee Survey revealed that 81% of our employees preferred to work outside the office for 3 to 5 days per week, with office visits primarily driven by learning and collaboration needs.
Armed with these valuable insights, we incorporated these findings into our subsequent major office transformations, including PENN1 in NYC and our latest office in Atlanta. In these locations, we purposefully designed specific spaces such as hot desks, huddle rooms, and collaboration areas to align with the identified trends and utilization patterns of our offices. Each of these offices were meticulously configured with layouts and technology to enhance productivity and collect valuable data for ongoing support of hybrid work. At both, Penn1 and Atlanta, our commitment to hybrid work is evident in the deliberate reduction of space to meet workforce capacity, utilization of collaboration technology, video-enabled environments, prioritization of collaboration spaces over individual workstations, and the elimination of personal offices.
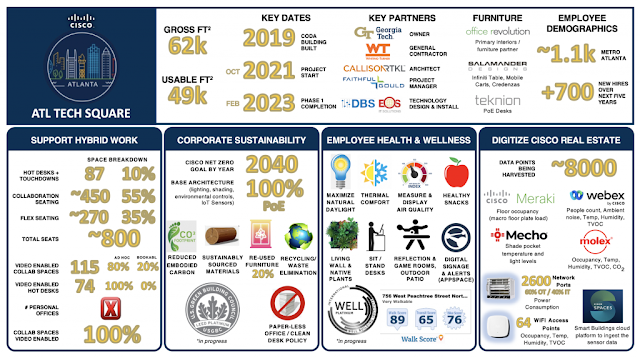
The PENN1 office follows a 30% “me” space to 70% “we” space ratio, which is the opposite of what our pre-pandemic offices were designed for. With the development of our latest office in Atlanta, the ratio of “me” to “we” spaces is now 10% to 90%. This clear shift reflects our data and observations on how people now utilize office space. Hybrid work means going to the office to collaborate with others, rather than focusing on individual tasks. The choices we made in our office designs demonstrate our dedication to creating environments where teams can thrive, engage in meaningful learning, collaborate seamlessly, and drive innovation.
Digitize Cisco Real Estate: Leveraging Data for Smarter Workspaces
Building on the previous section, we now explore how data and analytics have shaped Cisco’s decision-making process in creating
workspaces that promote collaboration, learning, and productivity. By harnessing insights from various sources, we have been able to optimize the physical environment to align with employee needs and preferences. Here are a few examples of how data and analytics have guided our hybrid work approach.
Cisco Video End Points
Analyzing data from Cisco Video End Points revealed that the average meeting size consisted of 3.7 in-person participants and 2.5 remote participants. Armed with this information, we intentionally designed small collaboration rooms, quiet spaces, and huddle rooms that cater to smaller groups. This approach fosters frequent and effective collaboration within a more intimate setting.
Cisco Spaces
Cisco Spaces is the core of our Hybrid Work strategy, acting as the foundation that brings everything together. It transforms flat floor plans into dynamic and interactive 3D maps, helping us to better understand and strategize for space utilization. We continuously collect data around the clock from our collaboration devices, networking devices, and third-party devices, enabling us to gain valuable insights in real time. This data empowers us to make informed decisions across the many areas of space design, safety, sustainability, and employee health and wellness. Whether it’s reimagining the layout of a room or helping facilities know what rooms to clean based on occupancy, this data provides us with the insights drive an impactful and informed hybrid work practice.
By utilizing data from Cisco Spaces, we identified a popular room layout at Penn1—a semi-open space with a high-top bar, low-profile seating, and limited power outlets. This configuration unexpectedly became a preferred spot for employees, encouraging focused collaboration and reducing distractions. Analyzing room utilization data through Cisco Spaces allowed us to recognize the demand for such spaces, leading us to implement similar designs in our latest office in Atlanta.
Employee Data
Industry standards revealed that employees typically visit the office to learn, collaborate, and socialize. This knowledge greatly influenced our space design, resulting in dedicated areas at Penn1 and Atlanta that cater to these functions. From large, connected rooms for training and workshops to smaller breakout rooms for collaboration, our spaces are purposefully designed to support these activities based on employee data.
By leveraging the power of data and analytics, Cisco has made informed decisions about space utilization, room design, and meeting configurations. This optimization not only enhances the physical environment but also ensures that our spaces align with the needs and preferences of our employees, facilitating a seamless transition into the hybrid work model.
You Can Be Next: Translating Data into Action
Now that we have discussed how data informs our approach to hybrid work, you may be wondering how to begin implementing your data-driven strategy. At Cisco, we recognize that smart buildings and hybrid work environments require a network of trusted partners to design, build, implement, and iterate — partners just like you. To get started on developing a data-first approach to hybrid work, consider the following options as your next steps:
1. Schedule a tour: Visit our new offices in Atlanta or PENN1 in NYC to witness firsthand the data-driven approach we have adopted and how it can benefit your customers. If you are an existing partner, reach out to your Product Marketing Manager (PMM) today.
2. Virtual tour: If an in-person visit is not possible, take a
virtual tour of PENN1 to preview the capabilities of our smart building approach.
Together, let’s leverage data to create actionable insights and shape the future of hybrid work. By creating workspaces that employees want to return to, buildings that provide the necessary data to adapt to changing needs, and environments that foster sustainability and innovation, we can deliver the experience that both customers and employees desire.
Remember, the future of work is hybrid, and data is the key to unlocking its full potential. Together, we can create workspaces that inspire productivity, collaboration, and success. Let’s embrace the power of data and embark on this exciting journey toward a more connected, smart, and flexible work environment.
Source: cisco.com