Thursday, 4 January 2024
AIOps Drives Exceptional Digital Experience Through Network Assurance
Saturday, 20 May 2023
How Cisco’s SaaS Solutions on AWS Deliver Unbeatable Value to Customers and Partners
Cisco’s SaaS Key Solutions Use cases
Saturday, 7 August 2021
Revolutionizing Customer Engagement and Collaborative Development
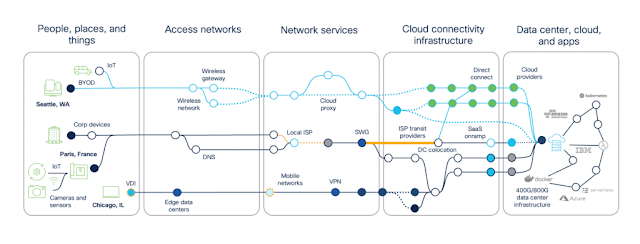
Our customers are looking for ways to simplify management of their Cisco devices and adopt new technologies faster while maintaining strong security across their environment. They are facing challenges in locating the right information necessary for deployment, obtaining access to the right resources, gaining visibility into their assets as well as more automated capabilities to reduce risks, increase uptime, and optimize overall performance.
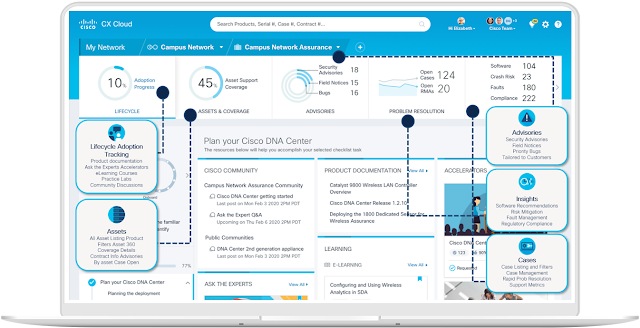
Cisco CX Cloud was built to address these concerns, alongside the Success Tracks suite of service packages. A cloud-based Software as a Service (SaaS) platform, CX Cloud provides customers with unified access to all of their Cisco portfolio in one pane of glass. Users can view their assets, contract coverage and licenses, access insights into the health of their network infrastructure, be alerted to security advisories, detect risks, open support cases in-app, and take advantage of contextual learning to train their IT teams all within CX Cloud.
Realizing the value of IT investments quickly is critically important to delivering results with agility. Our customers have told us that they want to be able to self-service, but at the same time be able to leverage consultative subject matter experts to help navigate more complex infrastructures. For example, one of our customers mentioned that often once a vendor sells something, they are left to figure out how to set it up, how to use it, and how to make it work to meet their needs. Another received a mandate to eliminate all critical security vulnerabilities across their entire infrastructure in a relatively short time frame, which is traditionally neither fast nor easy to accomplish, and weren’t sure where to begin.
In partnership with our customers, the CX Cloud Insights & Innovation Team aligns CX Cloud’s platform capabilities with our customers’ goals, so value is realized faster. We help customers learn how to use the CX Cloud platform and move through every stage of the adoption lifecycle, removing barriers along the way and identifying how to make the platform exactly what our customers need it to be. We have engaged with many customers and have learned from them the many ways CX Cloud helps them every day.
Tuesday, 4 May 2021
8 Reasons why you should pick Cisco Viptela SD-WAN
20 years ago, I used to work as a network engineer for a fast-growing company that had multiple data centers and many remote offices, and I remember all the work required to simply onboard a remote site. Basically, it took months of planning and execution which included ordering circuits, getting connectivity up and spending hours, and sometimes days, deploying complex configurations to secure the connectivity by establishing encrypted tunnels and steering the right traffic across them. Obviously, all this work was manual. At the time I was very proud of the fact that I was able to do such complex configurations that required so many lines of CLI but that was the way things were done.
Read More: 300-420: Designing Cisco Enterprise Networks (ENSLD)
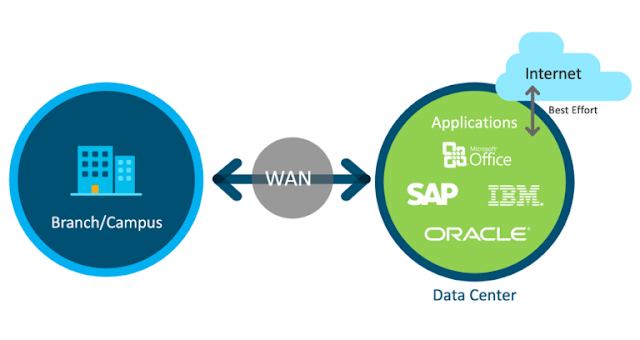
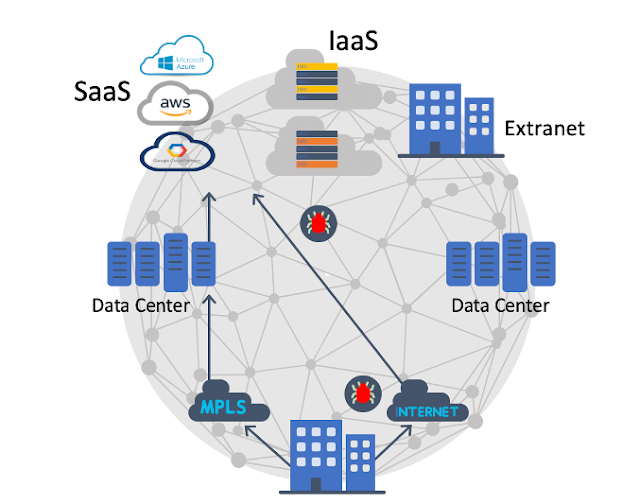
During the decade that followed, we saw a slew of WAN and encryption technologies become available to help with the demand and scale for secure network traffic. MPLS, along with frame Relay, became extremely popular and IPsec-related encryption technologies became the norm. All this was predicated on the fact that most traffic was destined to one clear location and that is the data center that every company had to build to store all its jewels including applications, databases and critical data. The data center also served as the gateway to the internet.
The rise of Cloud Computing
The need for SD-WAN
Why Cisco Viptela?
Saturday, 14 November 2020
Under Analytics
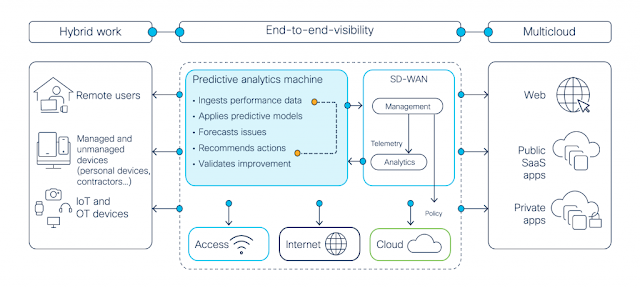
Back when network management was booming in the early 90’s, the whole idea seemed straightforward. System administrators would speak of endpoints on the network as being “under management” or conversely “unmanaged.” There seemed to be a place for everything and looking back now at those times, enterprises seemed so simple compared to today. Maybe simple is not the right term, maybe they just seemed more orderly compared to the modern network landscape.
At some point, hackers showed up and names like “under management” or “unmanaged network elements” made little difference to them. I remember security folks in the early days joking that SNMP (Simple Network Management Protocol) stood for “Security Not My Problem.” An insecure network meant that you had an insecure business! The experienced security architect knows that whether the system is under management, under someone else’s management, or completely unmanaged, if that system is part of the business, it is still their job to secure it. To put it another way, while management of systems can span certain, more specific information systems, security must always be as wide as the business.
I would like to suggest a new term and concept for our vocabulary and that is “under analytics.” I like to think of this as a conceptual means to discuss if areas of your digital business have enough visibility for continuous monitoring of its integrity. Why not just call it “under management?” Well, because more and more these days, you are NOT the one managing that area of the network. It might be the cloud service provider managing it, but it is still your problem if something gets hacked. You could even then speak of observable domains as having certain requirements that satisfy the type of analytics you would like to perform.
There are many types of observational domains to consider so let’s talk about some here. Back in the day, there was just your enterprise network. Then when folks connected to the internet, the concepts of internal and external and even the DMZ networks were referenced as observable network domains. These days, you have to deal with public cloud workloads, Kubernetes clusters, mobile devices, etc. Let’s just say that you can speak of having any amount of observable domains for which you require telemetry that will get you the visibility required to detect the most advanced threat actors in those domains.
For each of these observable domains, there will need to be telemetry. Telemetry is the data that represents changes in that domain that feeds your behavioral analytics outcomes. You could make a list of the competency questions you would want to answer from these analytical outcomes.
◉ Are there any behaviors that suggest my systems have been compromised?
◉ Are there any behaviors that suggest some credential has been compromised?
◉ Are there any behaviors to suggest there is a threat actor performing recognizance?
My suggestion is that you begin with these questions and then hold security analytics to them to see if they are competent to answer them daily, weekly, monthly, etc.From there, you can go one step further and start to consider and look into scenarios like the following:
◉ We have a new partner network, is it “under analytics?”
◉ We have a new SaaS service, is it “under analytics?”
◉ This company has a new cloud deployment, do we know if it is “under analytics?”
◉ What part of our digital busines is not “under analytics?”
How well do you know your digital business behavior when it is 100% without compromise? How would you even go about answering this? The truth is, you really do need to get to this level because if you don’t, threat actors will. Even if parts of the business use SaaS products, while parts of the network are using Infrastructure as a Service (IaaS), you can still set the requirements that there must be a sufficient amount of telemetry and analytics that help you understand the answers to these questions above. Your business must always remain “Under analytics” and only then will you be one step ahead of your attackers.
Tuesday, 18 August 2020
Cisco Launches SD-WAN Cloud Interconnect Ecosystem with Megaport
Enterprises can also choose direct cloud interconnects for their site-to-cloud connectivity. However these “mid-mile” interconnects require customers to plan for capacity and global reach upfront, which can lead to underutilization and spiraling cost.
Today we are announcing a collaboration with Megaport, which offers Software-Defined Cloud Interconnects (SDCI). It provides programmable cloud interconnects to bridge enterprise SD-WAN sites to clouds in minutes instead of weeks, with strong performance and high reliability.
This collaboration will offer Cisco’s SD-WAN customers access to Megaport’s global reach. Megaport offers extensive connectivity choices, backed by service-level guarantees for assurance. It includes peering with location data centers, with a global footprint across 23 countries. Megaport connects to more than 200 cloud on-ramps, including leading SaaS services like Office365 and Salesforce, and to the six largest public cloud providers: AWS, Azure, Google, Oracle, IBM and Alibaba. The Megaport ecosystem also connects to 200 network service providers, more than 700 data centers, and 360 IT service providers and aaS providers.
With this new collaboration, Cisco customers can leverage Cisco’s SD-WAN management platform, vManage, to software-define their cloud interconnects to multicloud and SaaS. With this integration, Cisco SD-WAN fabric will act as the overlay, and the Megaport Software Defined Network will act as the underlay.
This collaboration extends Cisco’s SD-WAN leadership, by offering an ecosystem platform for partners, of which Megaport is the first, to bridge Cisco SD-WAN fabric with the carrier-neutral and software-defined cloud interconnect fabrics.
Sunday, 11 August 2019
New Perspectives on Software-Defined WAN
In short, SD-WAN has arrived and organizations are deploying it worldwide. So what can we look forward to as this technology enters its next phase? Let me preview some of the ways we are working to bring even more control, functionality, and flexibility to SD-WAN.
Turning the Internet into a Manageable and Secure WAN
One of the key features of SD-WAN is the ability to use multiple connectivity options simultaneously to always have the most reliable or appropriate connection for application Quality of Experience. Specifically, you can choose among the options available for the location: MPLS, Ethernet, internet, leased lines, DSL, LTE networks, and soon 5G. It’s this flexibility to choose the most cost-effective and best-performing connectivity option available to provide the ideal application experience for each location of a distributed workforce. For example, need to ensure that Office 365 Cloud is performing as needed at branch offices? Instead of relying on an expensive MPLS connection backhauling to headquarters for connections to multicloud applications, use a secure Direct Internet connection to the Microsoft Cloud, which is continuously monitored by SD-WAN to meet performance SLAs.
What’s next? The ability to manage end-to-end connectivity from enterprise to 5G endpoints and back will bring greater levels of control over data traffic and application performance. The key to extending intent-based networking controls from enterprise to 5G cellular endpoints is network slicing in the 5G channels in conjunction with micro-segmentation in the enterprise. 5G slicing enables the carrier to separate traffic into unique partitions, keeping sensitive data separate from normal traffic. The technique enables 5G providers to maintain the necessary service level agreements for low-latency traffic, and create an end-to-end virtual network encompassing compute and storage functions.
Wired and wireless Enterprise networks are already segmented to channel traffic according to type (sensitive/video/IoT), priority, and latency. Today with 4G LTE, the enterprise segmented traffic destined for a cellular endpoint would move onto the cellular network with few controls over how the data is segmented and managed. The new 5G networks can be sliced to match the security and performance requirements of the segments in the enterprise, thus maintaining the original policies from end-to-end. A security policy, for example, that is established in the enterprise network will follow a person’s device as it transitions from the enterprise to a 5G network slice. Cisco SD-WAN will be able to take full advantage of network slicing in 5G to meet the security and segmentation needs of enterprise networks.
Virtualizing Network Functions for the SD-Branch
Bringing the focus back to ensuring robust branch connectivity, we are enhancing the functions that run on the local edge routers and appliances along with the core SD-WAN software suite. Virtualizing network functions (VNF) increases local performance and minimizes backhaul traffic to corporate data centers DMZs or cloud platforms. Many functions are being virtualized on edge routers and appliances—such as optimization and intelligent caching, application-aware firewalls, intrusion detection, and URL filtering. And, of course, SD-WAN’s full security stack supports compliance, direct internet access, direct cloud access, and guest access.
Virtualizing critical functions and running them at the cloud edge—in the branch office, store, or clinic—improves both the efficiency and cost-effectiveness of distributed computing and a remote workforce. VNFs can also be run on cloud platforms and colocation facilities to spread the functionality over multiple remote locations. For example, by consolidating VNFs on a provider’s IaaS platform—a virtual network hub—IT can reduce management costs while being able to spin up or down new virtual machines as needed to accommodate workloads and connectivity for a group of regional branches. More on this in a future blog post.
Improving Application Quality of Experience with WAN Optimization
WAN optimization techniques have been around since the early days of frame relay and MPLS. The main goal of dedicated optimization appliances was to maximize the throughput on these relatively expensive circuits. As new technologies such as VoIP and video became critical to business, optimizing the circuits to provide the necessary Quality of Service grew in importance. But as direct internet connections became the rule rather than the exception for accessing popular SaaS and cloud apps, a much more granular, flexible, and automated WAN optimization process is required. Thus SD-WAN was designed to meet the new application QoE demands.
There are several optimization methods that Cisco SD-WAN currently employs to improve the QoE for cloud and SaaS applications accessed by the distributed workforce. Currently, Cisco SD-WAN monitors the available links for latency, packet loss, and jitter that affect throughput and performance. By dynamically measuring these characteristics and comparing them with service levels that specific applications require, the SD-WAN can automatically decide which circuits to use for individual applications. VoIP and video are two applications that require specific levels of latency and low jitter to perform correctly. While a SaaS application may be more tolerant of jitter, it still requires a guaranteed level of throughput to provide satisfactory performance. SD-WAN automates the monitoring and selection of appropriate paths to maintain expected QoE for each type of application.
Supplementing these existing performance attributes of SD-WAN are new controls for TCP optimization, forwarding correction, and packet duplication. SD-WAN provides metrics that aid in fine tuning the optimal TCP congestion algorithm to improve application performance. For example, the Cisco SD-WAN TCP optimization engine, a new layer in the Cisco SD-WAN stack, helps maintain superior application performance in high latency networks such as satellite, transcontinental, and other types of circuits prone to high-loss and high-latency.
To better tackle lossy networks, even for non-TCP applications, the Cisco SD-WAN optimization stack includes a Forward Error Correction (FEC) mechanism. FEC improves application experience by using additional parity packets to protect against loss. In situations when the loss percentage is very high, the Cisco SD-WAN optimization stack maintains performance by deploying a Packet Duplication feature. These optimization features help mitigate packet loss over noisy channels, thereby maintaining high application QoE for voice and video in particular. They are being integrated into the Cisco SD-WAN stack in upcoming IOS-XE releases. All three optimization techniques are managed via Cisco vManage and vSmart virtual network functions.
Edge-to-Cloud Protection with Integrated SD-WAN Security Stack
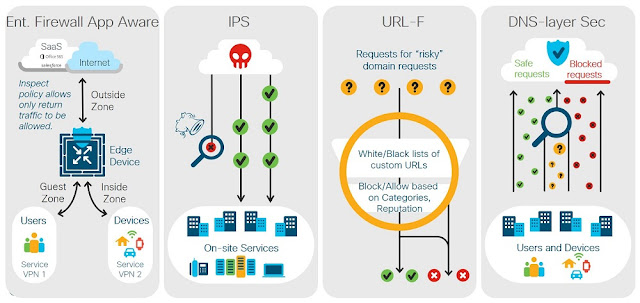
Securing branch to cloud to data center traffic, in all its permutations, is a key strength of SD-WAN. Last year Cisco added a virtualized security stack to provide multiple levels of protection at the cloud edge that includes:
- Application-Aware Enterprise Firewall with the ability to identify, permit, or block over 1400 applications.
- Intrusion Protection System (IPS) using Snort, the most widely deployed IPS engine in the world, to deliver real-time network defense against malware intrusions.
- URL-Filtering with advanced reporting on over 80 URL categories, providing IT with greater visibility and reducing risk with usage policies customized to an organization’s unique needs.
- DNS/web-layer security with integrated connections to Cisco Umbrella to prevent enterprise branch users, guests and mobile users from accessing inappropriate internet content and known malicious sites that might contain malware and other security risks.
Coming soon to a Cisco edge router near you is Cisco Advanced Malware Protection (AMP) Threat Grid operating as a virtual network function (VNF). The additional AMP-focused layer includes a context-aware knowledgebase of known malware infectious agents. Cisco AMP Threat Grid identifies and alerts IT staff of discovered infections, and provides information on the malware method of attack, a measure of the threat it poses, and how to defend against it. Operating at the branch edge, with the SD-WAN VNF security stack, AMP Threat Grid provides a layer of malware protection, examining all incoming and outgoing traffic, ensuring that malware originating from direct internet connections can’t infect branch devices. Similarly, malware originating from the branch can’t hide in traffic outbound to the enterprise network or cloud applications.
Threat insights exposed with AMP Threat Grid are viewable through the Cisco vManage Portal where administrators can also initiate protective actions such as segmenting infected devices from the rest of the network. The vManage Portal gives network admins a view across the entire WAN, displaying all suspected infections, malware type, and paths of infection through the network. To augment security threat intelligence, the VNF instances of AMP Threat Grid working at the local edges are continuously connected to both AMP Cloud and Threat Grid Cloud, both managed by Cisco Talos Security.
AMP Cloud and Threat Grid Cloud collect malware and suspicious file data from Cisco installations around the world, maintaining a Malicious File Hash catalogue of suspected infections and keeping the information up to date on all Cisco routers as well as third-party security tools via an open API. For example, API integration of AMP Cloud and Threat Grid Cloud with application-aware, threat-focused firewalls provides rapid identification of suspected malware files with automated sandboxing of unknown files in the Threat Grid Cloud for additional analysis.
SD-WAN Continues to Improve Branch Connectivity, Application QoE, and Security
Cisco SD-WAN is foundational for a new software-defined network architecture. As organizations become more distributed, the workforce needs new ways to connect edge to cloud, data center to branch, while ensuring a high Quality of Experience for cloud and SaaS applications wherever they are needed. Cisco is at the forefront of this new wave of distributed connectivity, continuously refining our SD-WAN software and security stack to meet the needs of the digital enterprise.
Saturday, 4 May 2019
Accelerate Your Journey to AWS With a Cisco Cloud Ready Network
While pre-application migration planning and application readiness is a key area of focus, many organizations have also realized that network readiness is also critical in accelerating and ensuring a successful cloud adoption journey. Legacy network architectures lack the simplicity, adaptability, automation and most of all application-awareness needed to deliver the best user experience. A Cloud Ready Network needs to enable a secure and optimized connectivity to cloud services from the branch/remote-offices.
Cisco next-gen SDWAN is one of the pillars of the Cloud Ready Network that can accelerate organizations adoption of cloud.
Cloud Ready WAN
To guarantee optimal end users experience an organization requires seamless connectivity between branch office locations, applications, and workloads hosted in the cloud. Many WAN solutions are ill-equipped for this task because they are generally rigid, complex to configure, and expensive to maintain. IoT adoption, a dramatic increase of the number of network devices, and the sophistication of security threats further compounds this challenge.
Cisco SDWAN on Amazon Web Services (AWS) is an overlay WAN architecture that is designed to address heterogeneous WAN connectivity and distributed users by building a scalable WAN infrastructure that reduces data transport costs and operational expenses. Cisco SDWAN for AWS helps with the following two major use cases:
Cloud Onramp for SaaS – Improving SaaS performance with SDWAN on AWS
Enterprises with the legacy WAN architecture, find it challenging to ensure a quality end user experience with their SaaS adoption. Often times a suboptimal path with increased latency is chosen to connect a user to the SaaS application in the cloud resulting in a degraded end user experience. A cloud ready network via SDWAN solves the problem by creating multiple Internet exit points and dynamically steering around bandwidth and latency issues in real-time, resulting is an optimal SaaS user experience at branches.
To achieve this the SDWAN fabric continuously measures the performance of designated SaaS applications through all permissible paths from a branch including direct internet access. For each path, the fabric computes a quality-of-experience (vQoE) score that gives network administrators visibility into application performance. The fabric also makes real-time decisions to choose the best-performing path per application per VPN between the end users at a remote branch and the cloud SaaS application and automatically fails over in case of performance degradation.
Wednesday, 20 February 2019
Practicing Responsible SSL Inspection in an SD-WAN Environment
Looking at an SD-WAN fabric, WAN aggregation may seem outdated as headquarters and core locations no longer need to serve as fortified gateways to the internet. Despite these architectural changes, core locations can excel as aggregation points for more challenging security operations, such as Transport Layer Security (TLS) decryption, often called by its more common name, Secure Socket Layer (SSL) inspection.
Security remains a top concern across the WAN. Enterprises want to detect the latest malware threats, yet the latest research shows that 70% of malware attacks are estimated to be hidden in encrypted TLStraffic that network and security teams cannot see. With encrypted internet traffic increasing, SSL inspection has been promoted a solution for finding hidden malware, but this is misleading for a number of reasons.
To Decrypt or Not
Though some SD-WAN vendors may tout their SSL inspection capabilities—such as hardware acceleration or off-loading—as evidence of product superiority, indiscriminate decryption across the WAN is not a sound practice. Decrypting sensitive traffic can violate privacy and data laws, and establishing whitelist policies to avoid violations is time-consuming and, at best, educated guesswork. Furthermore, many enterprise teams do not have the compute resources for wholesale SSL inspection, forcing them to suffer performance degradation as traffic enters the WAN.
Cisco addressed this challenge by developing a proprietary process known as Encrypted Traffic Analytics(ETA). With ETA enabled, Cisco SD-WAN platforms, such as the Integrated and Aggregated Services Routers (ISR and ASR), as well as the Enterprise Network Compute System (ENCS) hosting virtual devices, are able to categorize malicious traffic without performing decryption. Enabling ETA allows your SD-WAN fabric more precise network policies, where any traffic flagged as questionable can then be backhauled to core locations for responsible decryption.
This is a unique process we call SSL Aggregation.
Reasons to adopt SSL Aggregation
While Cisco SD-WAN enables industry-leading, zero-touch branch security capabilities, such as stateful firewalling, URL filtering, DNS monitoring, and Snort IPS, it is recommended to backhaul any traffic ETA flags as questionable to core locations for three main reasons:
◈ Greater physical space at core locations allows for more robust security layering, including products that are different from, or go beyond, what’s available through SD-WAN. A next-generation firewall (NGFW) with SSL Inspection, next-generation anti-virus (NGAV) that can detect fileless malware, or SIEM technology can help to remediate and log vulnerabilities after the malicious traffic is decrypted for inspection.
◈ Many enterprises manage thousands of branch office locations in their SD-WAN fabric. Even if SSL inspection capabilities exist at branch and remote office locations, the complexity of such data could overwhelm network and security teams. By consolidating malicious data flows into fewer ingress points, security management is simplified.
◈ Metadata created in conjunction with ETA can alert to zero-day threats that evade threat intelligence. Sending the flagged traffic to secure core locations is the safest practice when aiming to retain and utilizing data.
Given their superiority as secure hubs to isolate and examine malicious traffic, core locations make effective aggregation points for practicing responsible SSL inspection in an SD-WAN environment. Architecting this process is simple with Cisco.
Architecting SSL Aggregation
◈ At the Branch: Deploying a 1000 or 4000 Series Integrated Services Router (ISR 1000; ISR 4000), or a 5000 Series Enterprise Network Compute System (ENCS 5000) will allow your branch locations to feed key telemetry data into Stealthwatch, enabling ETA across the SD-WAN fabric.
◈ Core/Colo/Campus/HQ: Because these core locations will receive high volumes of aggregated traffic, deploying 1000 Series Aggregated Services Router (ASR 1000) is recommended to handle increased flows. A Cisco Firepower Threat Defense (FTD) Next-Generation Firewall (NGFW) can decrypt the malicious traffic at the core and detect the threat.