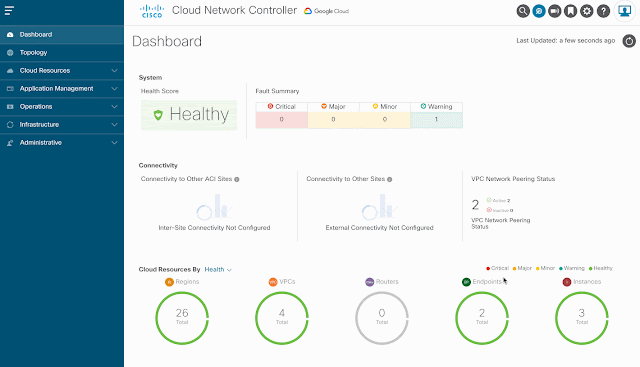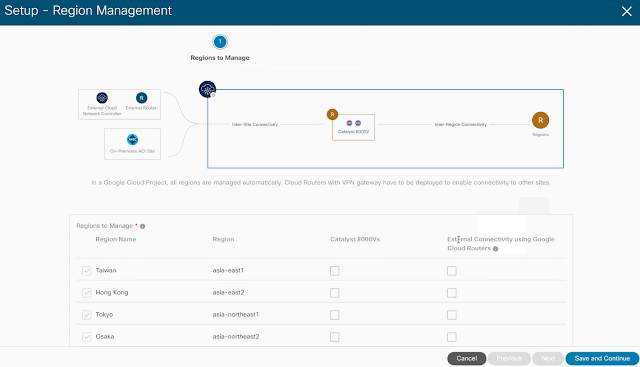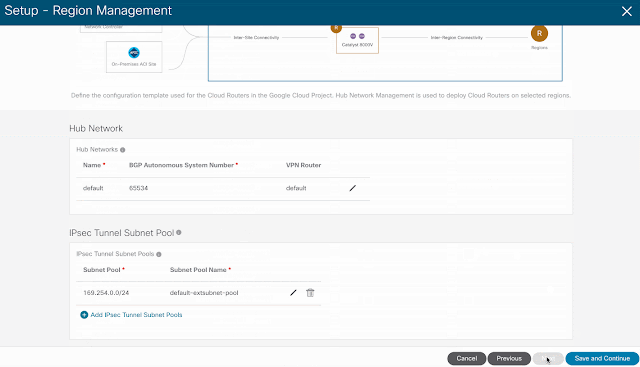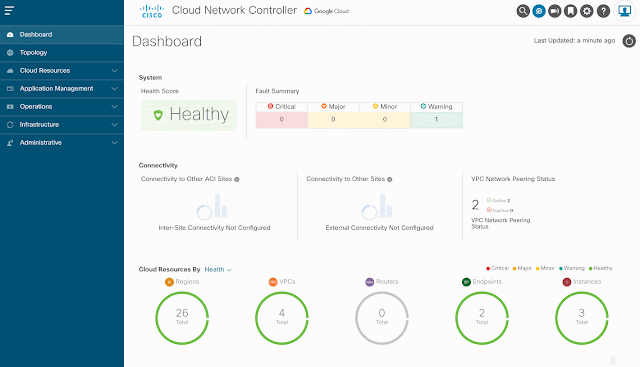
Most of our large customers today have datacenters and leverage multiple clouds to maximize flexibility and agility for meeting their business needs. Traditionally, the security for these environments has rested with different teams, each having their own tools and processes. But as our application and IT environments become more interwoven, the complexity of the environments and the challenge of securing them has massively increased. Siloed tools and teams are now part of the problem, generating new gaps and blind spots. Attackers are growing more sophisticated and taking advantage of these new challenges. In fact, last year, 39% of breaches spanned multiple environments and cost organizations an average of $4.75M per breach globally.
It is time to rethink how organizations approach the hybrid-multicloud security strategy — converging the fabrics between on-premises and cloud network security to foster collaboration across teams and deliver a unified edge security strategy.
Today, we are we’re bringing on-prem and cloud security together into one unified platform through the Cisco Security Cloud to marry the power of Cisco Secure Firewall and Cisco Multicloud Defense. Combined, these solutions provide multi-environment customers with greater visibility and protection across environments, more consistent control to reduce risk, and simplified security policy creation to alleviate complex operations.
This year at RSA Conference 2024, customers can experience where security meets the network with new capabilities between these solutions — as part of our unified security platform.
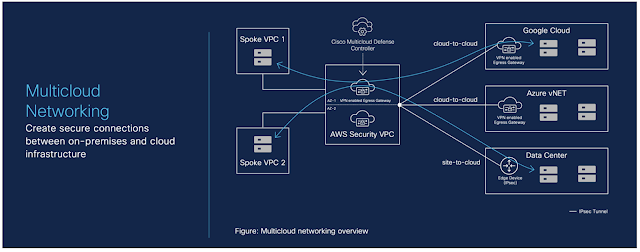
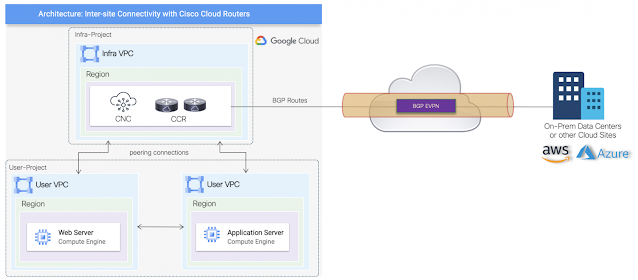
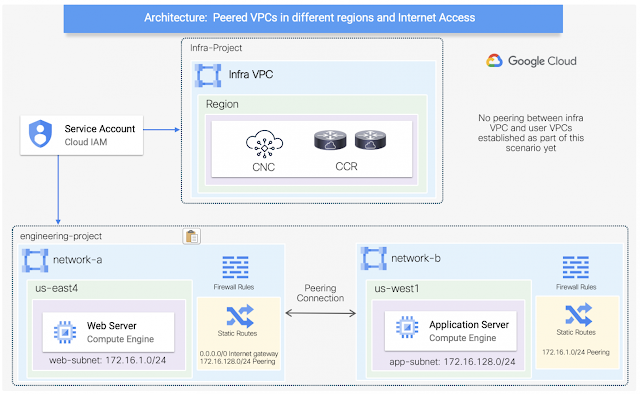
Multicloud networking: Secure connectivity from ground to cloud
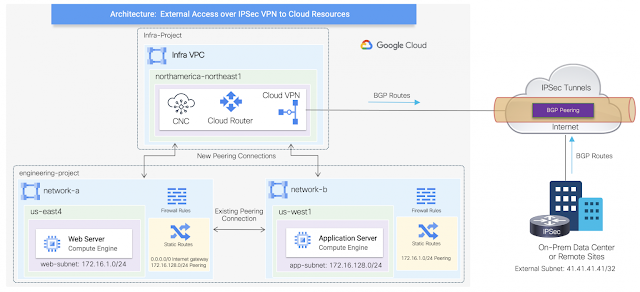
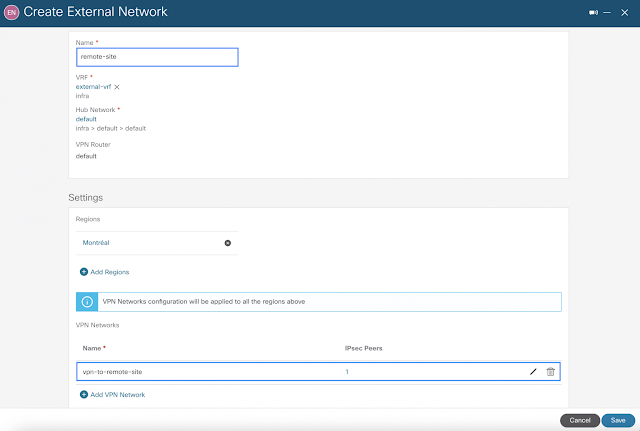
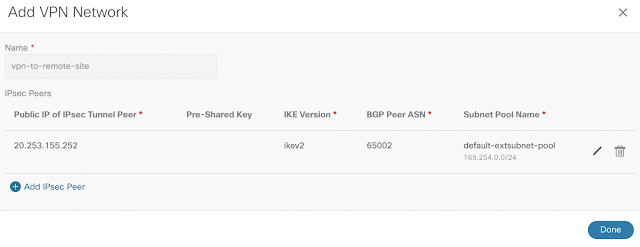
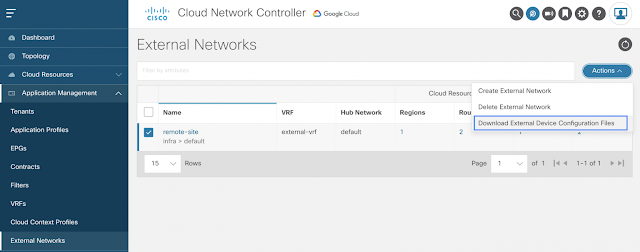
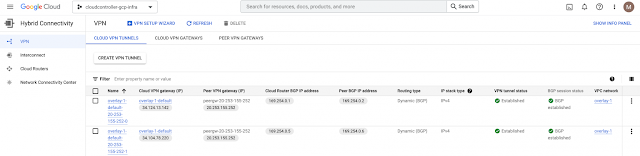
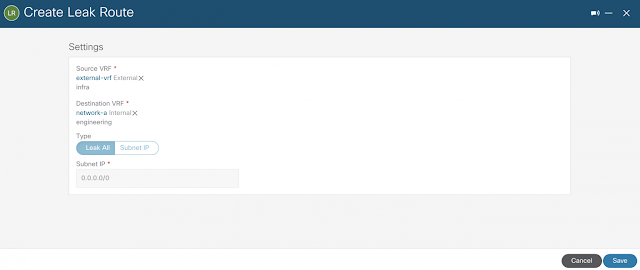
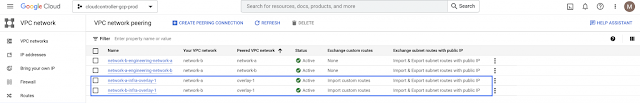
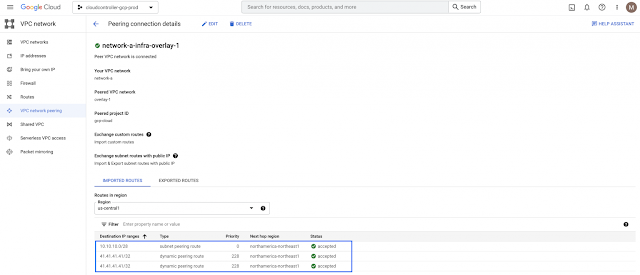
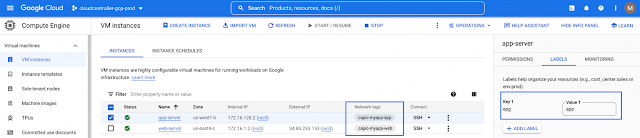
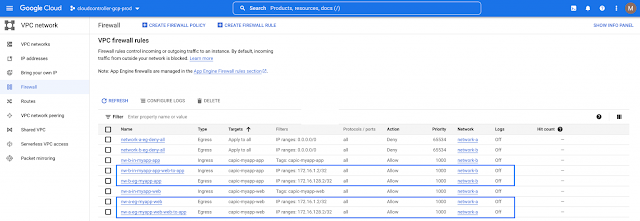
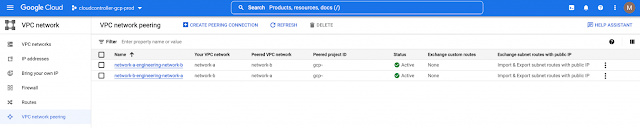
Imagine you have an application on-prem that needs to talk to an application in the cloud, how would you approach this challenge? Traditionally, organizations have had to rely on 3rd party native tools. However, these services can be costly — especially as you scale applications and environments. And as you scale, the complexity increases, reducing visibility and control of critical security functions. Now, by leveraging our unified platform with the Cisco Security Cloud, customers can build these connections in house with secure site-to-cloud and cloud-to-cloud connectivity between applications and environments. With this, organizations will be able to securely scale hybrid cloud operations while reducing cost and maintain visibility and control of their connections and data.
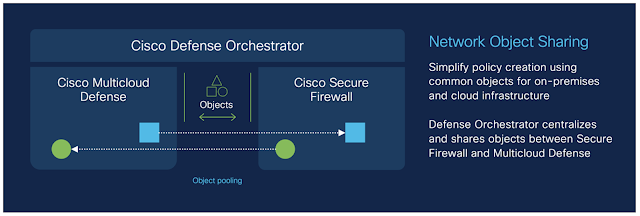
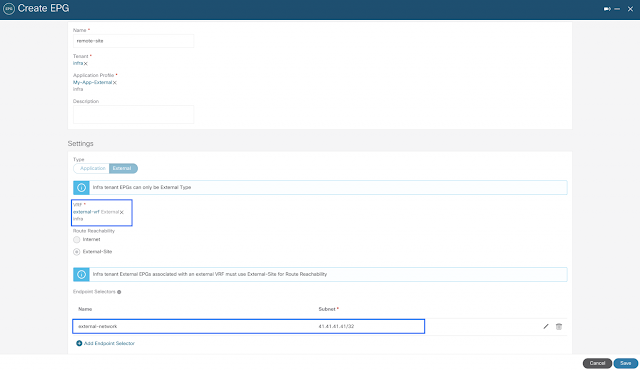
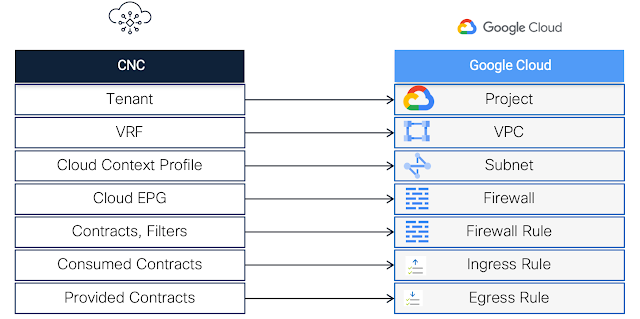
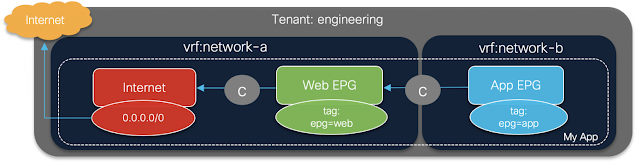
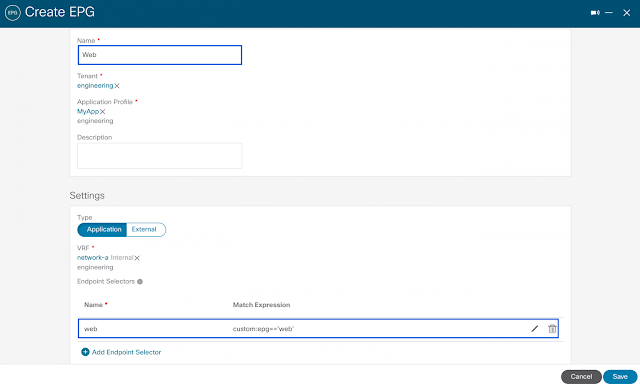
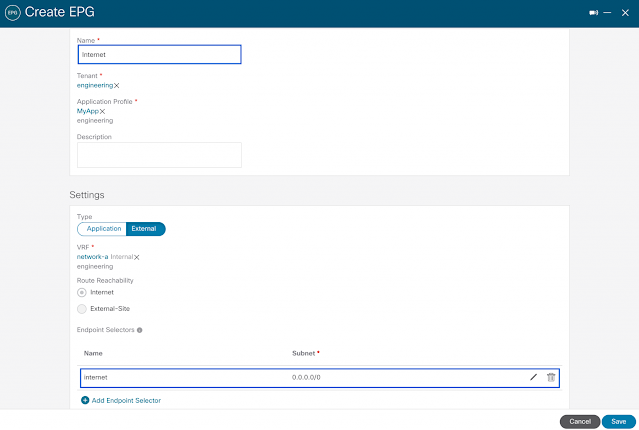
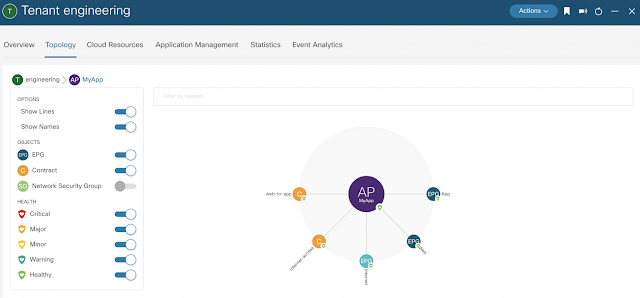
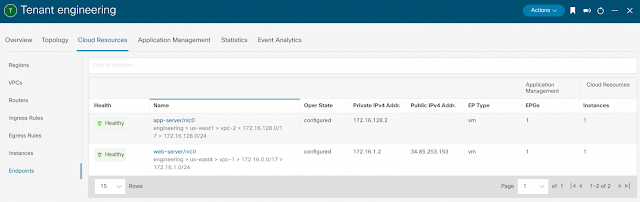
New network object sharing further simplifies policy creation across multi-environments
In many cases today, organizations are building, deploying, and managing policies in silos. This disparate method strains teams — creating laborious, redundant steps in the policy building process, leads to increased risk of human error and cues the dreaded swivel chair scenario — hopping between numerous tools and platforms to build policies.
At Cisco Live EMEA, we announced general availability of network object sharing for static objects. Today at RSA Conference, we’re reducing multi-environment complexity even further with the ability to now share dynamic objects using our unified management fabric. This gives organizations a single location to pool objects, simplifying policy building and management across environments. Baked into the Cisco Security Cloud platform, this capability empowers organizations to easily share objects between Secure Firewall and Multicloud Defense, reducing complexity, removing duplicative processes, and stopping the pain of maintaining yet another case of siloed operations across separate solutions.
As we continue to innovate across the Cisco Security Cloud, synergies across the network security portfolio will continue to grow. The launch of these shared capabilities between Cisco Secure Firewall and Cisco Multicloud Defense is a significant step towards converging the fabrics of best-in-class data center and cloud security to protect customers from ground to cloud.
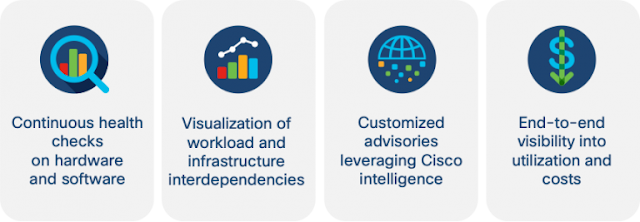
Looking to get started? Understand your risk by signing up for our free Cloud Visibility and Risk Report. Powered by Cisco Defense Orchestrator and Cisco Multicloud Defense, our solutions run alongside your clouds to help you understand your risk with pervasive visibility into assets and connections — our experts then provide you with actionable security insights and recommendations to better protect your infrastructure.
Source: cisco.com