The traditional castle-and-moat model of cybersecurity is outdated due to the evolving perimeter caused by remote work and fluid data access. Organizations must integrate security at every touchpoint. The proliferation of IoT devices increases entry points for cybercriminals, necessitating a unified approach to endpoint security.
Advanced technologies like AI and quantum computing are transforming cybersecurity, making threats more sophisticated and encryption standards vulnerable. The convergence of technologies, such as networked sensors and big data, expands the attack surface while improving AI capabilities for both attackers and defenders. The increasing sophistication of cyberattacks, as seen in incidents like the SolarWinds hack and Colonial Pipeline attack, highlights the need for proactive, integrated security strategies.
Critical infrastructure vulnerability, regulatory considerations, and the necessity of collaborative security practices underscore the importance of a Unified Security Platform to provide adaptive defenses and foster a security-conscious culture within organizations. The Hybrid Mesh Firewall emerges as a vital component in this landscape, offering the flexibility and comprehensive protection required to meet modern cybersecurity challenges. Before we delve into “What is Hybrid Mesh Firewall”, let us discuss a few customer problems:
Key problem areas for customers
1. Misconfigurations and vulnerability exploitation
One of the most significant issues plaguing organizations is the prevalence of misconfigurations and the exploitation of these vulnerabilities. Despite having multiple security products in place, the risk of human error and the complexity of managing these systems can lead to critical security gaps.
2. Rapid attack execution
The speed at which cyber-attacks can be executed has increased dramatically. This necessitates even faster defense responses, which many traditional security setups struggle to provide. Organizations need solutions that can respond in real-time to threats, minimizing potential damage.
3. Hybrid environments
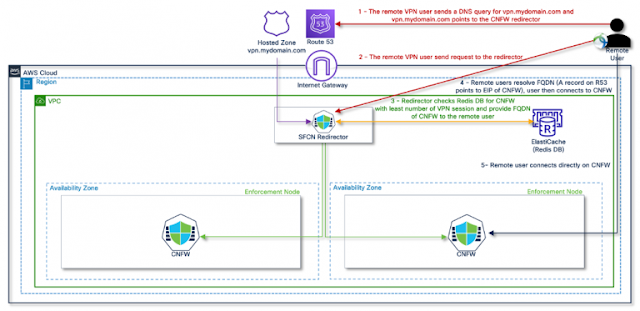
The modern workforce is distributed, with employees working from various locations and using multiple devices. This hybrid environment requires robust protection that is enforced as close to the user or device as possible. The conventional approach of backhauling remote user traffic to a central data center for inspection is no longer viable due to performance, scalability, and availability constraints.
The emergence of SASE has transformed how network and security solutions are designed, providing connectivity and protection for a remote workforce. However, the shift to distributed controls has become inevitable, presenting its own set of challenges. Many customers deploy best-of-breed security products from different vendors, hoping to cover all bases. Unfortunately, this often results in a complex, multi-vendor environment that is difficult to manage.
4. Siloed security management
Managing security across different silos, with multiple teams and solutions, adds to the complexity. Each system must operate effectively within the principles of Zero Trust, but ensuring consistent performance across all products is challenging. Security systems need to work cohesively, but disparate tools rarely interact seamlessly, making it hard to measure and manage risks comprehensively.
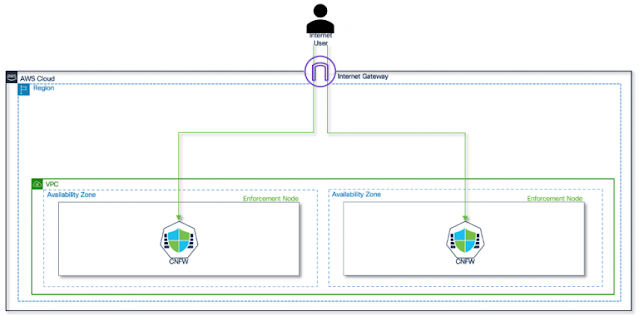
The hybrid mesh firewall solution
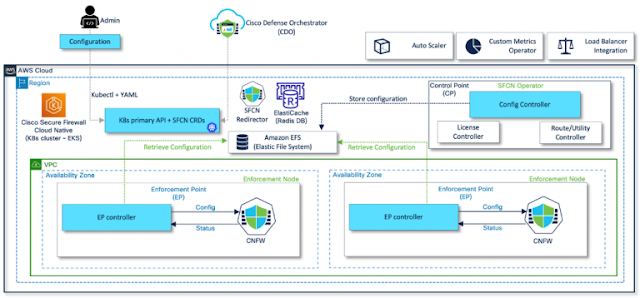
Hybrid mesh firewall platforms enable security policy enforcement between workloads and users across any network, especially in on-premises-first organizations. They offer control and management planes to connect multiple enforcement points and are delivered as a mix of hardware, virtual, cloud-native, and cloud-delivered services, integrating with other technologies to share security context signals.
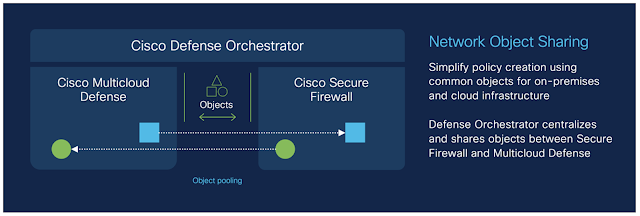
By unifying various firewall architectures, Hybrid Mesh Firewalls ensure consistency and coherence, proactively identifying gaps and suggesting remediations for a holistic approach to network security.
Benefits of hybrid mesh firewalls
- Unified security management: By consolidating various security functions into a single platform, Hybrid Mesh Firewalls simplify management and reduce the likelihood of misconfigurations. Administrators can oversee and configure all aspects of network security from one place, ensuring that no critical security gaps are overlooked.
- Proactive threat identification and remediation: The platform continuously monitors the network for vulnerabilities and misconfigurations, such as when a team managing the Secure Service Edge (SSE) solution inadvertently allows direct access to a risky file-sharing site. In such cases, the firewall promptly alerts the admin and provides a remediation flow, ensuring only low-risk apps access the internet directly while other traffic is securely tunneled. This proactive approach prevents incidents before they occur, safeguarding the network from potential threats like data exfiltration or malware infiltration.
- Real-time response: With the capability to respond in real-time to threats, Hybrid Mesh Firewalls ensure that security measures keep pace with the speed of attacks. This rapid response capability is crucial for minimizing damage and maintaining business continuity.
- Zero trust enforcement: Each component of the security system operates independently but within the overarching principle of Zero Trust. This means that the endpoint protection software on a remote user’s device functions correctly, regardless of the firewall configuration at the data center, and vice versa. Every element of the security infrastructure works to ensure that trust is never assumed and always verified.
Beyond remote work: Securing workloads everywhere
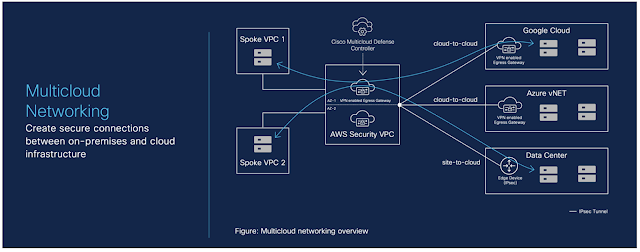
The need for robust security extends beyond the realm of remote work. Modern organizations are leveraging a mix of private and public cloud environments to run their workloads. Whether it’s a private data center, a public cloud provider like AWS or Azure, or even multiple public clouds, the security landscape becomes increasingly complex.
Hybrid Mesh Firewalls are designed to secure workloads regardless of their location. This approach ensures that security policies are consistently applied across all environments, whether on-premises, in a single public cloud, or across multiple cloud providers.
Securing hybrid workloads:
- Consistent policy enforcement: By providing a unified platform, Hybrid Mesh Firewalls ensure that security policies are consistently enforced across all environments. This eliminates the risk of discrepancies that can arise from using different security products in different locations.
- Integrated visibility and control: With integrated visibility into all network traffic, Hybrid Mesh Firewalls allow administrators to monitor and control security policies from a single interface. Centralized management is crucial for identifying and mitigating risks across diverse environments.
- Scalability and flexibility: As organizations grow and their infrastructure evolves, Hybrid Mesh Firewalls offer the scalability and flexibility needed to adapt to new requirements. Whether adding new cloud environments or scaling up existing ones, the firewall platform can grow with the organization.
Conclusion
The need for Hybrid Mesh Firewalls has never been more critical. As organizations navigate the complexities of a distributed workforce, hybrid environments, and the ever-evolving threat landscape, a unified, proactive, and real-time approach to network security is essential. Hybrid Mesh Firewalls offer the consistency, control, and comprehensive protection needed to secure modern hybrid environments effectively. By addressing the key problem areas of misconfigurations, rapid attack execution, and siloed security management, they provide a robust solution that meets the demands of today’s cybersecurity challenges and beyond.
Source: cisco.com