Wednesday, 6 September 2023
Taming AI Frontiers with Cisco Full-Stack Observability Platform
Saturday, 20 May 2023
How Cisco’s SaaS Solutions on AWS Deliver Unbeatable Value to Customers and Partners
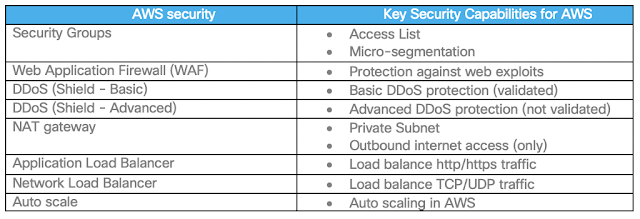
Cisco’s SaaS Key Solutions Use cases
Tuesday, 17 January 2023
Three Best Practices to Enable Partner Success on AWS Marketplace
1. List the right products
2. Align the sales teams around co-selling
3. Invest in developing processes to ensure operational success
Accelerating opportunity and growth
Thursday, 10 November 2022
Cisco Secure Firewall on AWS: Build resilience at scale with stateful firewall clustering
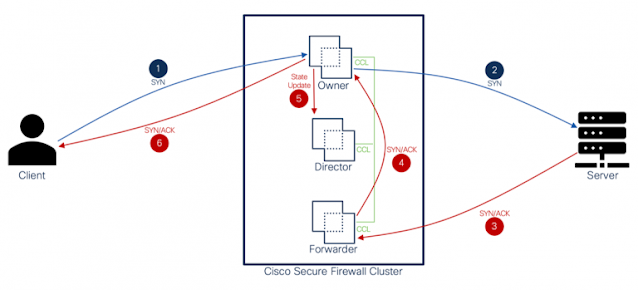
Cisco Secure Firewall clustering overview
Clustering roles and responsibilities
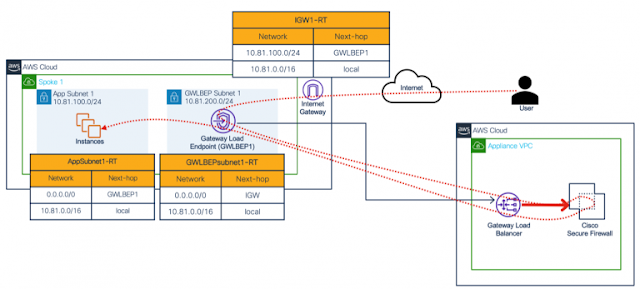
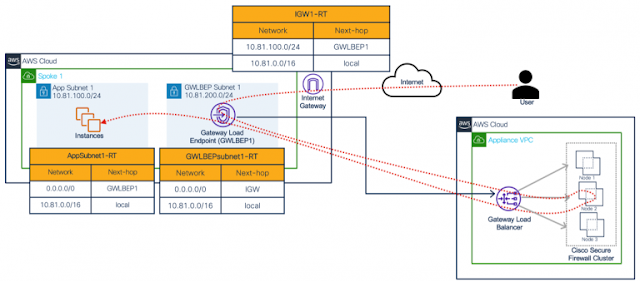
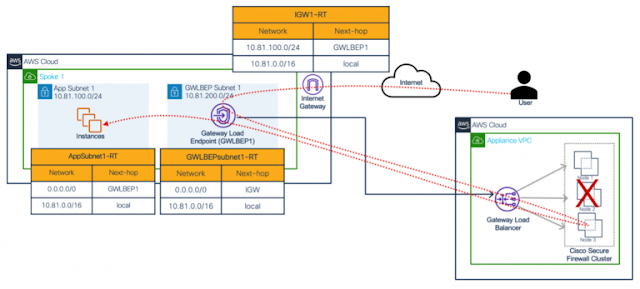
Integration with AWS Gateway Load Balancer (GWLB)
Cisco Secure Firewall clustering in AWS
Thursday, 30 December 2021
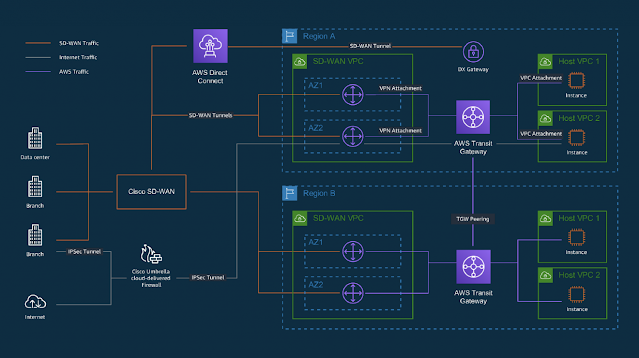
Streamlining Connectivity for a Multi-Region Hybrid World
Multi-region cloud deployments create complexity
The combination of a hybrid cloud migration and the long-term needs of a hybrid workforce are shining a spotlight on the need for consistently secure, high quality access to on-demand compute resources.
Requirements for low latency across geographically distributed workloads, resiliency, and compliance with data privacy regulations are driving organizations towards multi-region deployments in the cloud. While this can be done manually by using VPC peering and static routes, management complexity increases with scale and can be error-prone. To make networks streamlined and scalable, organizations need a dynamic and central way to manage their multi-region deployments.
All the hybrids: cloud and work
Saturday, 25 September 2021
Automating AWS with Cisco SecureX
The power of programmability, automation, and orchestration
Automating security operations within the public clouds takes advantage of the plethora of today’s capabilities available and can drive improvements throughout all facets of an organization. Public clouds are built on the power of programmability, automation, and orchestration. Pulling all of these together into a unified mechanism can help deliver robust, elastic, and on-demand services. Services that support the largest of enterprises, or the smallest of organizations or individuals, and everywhere in between.
Providing security AND great customer experience
The success of the major public cloud providers is a testament itself to the power of automation. Let’s face it, Cyber Security isn’t getting any easier, and attackers are only getting more sophisticated. When considering the makeup of today’s organizations, as well as those of the future, a few key points are worth consideration.
Read More: 500-173: Designing the FlexPod Solution (FPDESIGN)
First, the shift to a significantly remote workforce it here to stay. Post-pandemic there will certainly be a significant number of employees returning to the office. However, the flexibility so many have gotten used to, will likely remain a reality and must be accounted for by SecOps teams.
Secondly, physical locations, from manufacturing facilities and office space, to branch coffee shops, not everything has the ability to go virtual and we, as security practitioners, are left with a significant challenge. How do we provide comprehensive security, alongside seamless customer, and top-notch user experience?
Clearly the answer is automation
Customizable automaton and orchestration capabilities
A more effective SecOps team
Sunday, 20 September 2020
Extend secure, automated branch office networking to AWS with Cisco SD-WAN Cloud OnRamp
According to a Cisco study, by 2021, there will be 20 zettabytes of traffic between the DC/branch to the clouds, as companies use popular public cloud platforms like Amazon Web Services (AWS). Meanwhile, “IaaS is forecast to grow 24% year over year, which is the highest growth rate across all market segments,” according to Gartner.
However, while a cloud strategy creates more agility, it also presents challenges for IaaS deployments. Below are three primary concerns cloud users face regularly:
Inconsistent connectivity
Large-scale networks may traverse multiple slow public and/or expensive private connections to get to the cloud deployments, while smaller networks may need to battle out a slow, jittery internet to get to the clouds. In either case, customers will need to find the fastest and most reliable link while confirming a secure transport.
Complexity with governance
No real uniformity exists as to how different platforms handle their governance and compliance. This maze of rules and frameworks can create consistency problems with companies trying to utilize more than one cloud platform, especially with (but not exclusive to) IaaS. Finally, each cloud vendor has its own policy, security and segmentation process. These variances from vendor to vendor add another layer of complexity that must be managed.
Visibility problems
Different cloud platforms also use various protocols for analytics, metrics and insights. This variance can effectively reduce visibility for companies, making it more challenging to optimize usage across the network.
Cisco’s SD-WAN Cloud OnRamp automates and optimizes the enterprise SD-WAN to IaaS and SaaS
Cloud OnRamp is a cloud networking solution and a functionality of Cisco SD-WAN through which enterprises can network their branch sites to workloads deployed in cloud environments. Cloud OnRamp provides seamless, secure and automated networking for IaaS as well as an optimized experience for various SaaS applications.
One proven way to overcome the challenges of a cloud strategy is by implementing a consistent fabric across a company’s entire WAN network using Cisco SD-WAN Cloud OnRamp. Cisco SD-WAN provides a secure WAN architecture that can extend consistent policy enforcement, segmentation and security across both on-premises and cloud networks. Cloud OnRamp simplifies the experience further through the power of automation, using vManage as the single pane of glass management platform to create a SD-WAN transit network in the cloud provider’s environment.
Advantages of Cisco SD-WAN Cloud OnRamp
◉ Greater automation — With Cloud OnRamp, users can expect to automate SD-WAN extension to the cloud in minutes with just a few clicks.
◉ Improved security – Cloud OnRamp reduces security risks by leveraging graular segmentation and streamlined policy enforcement that can control and segment the traffic that flows through the network, guarding against external and internal threats to the data.
◉ Ease of management – Cloud OnRamp provides end-to-end data sharing between cloud and branch and establishes inter-regional visibility across transit data and network telemetry.
Cisco SD-WAN Cloud OnRamp Integration with AWS Transit Gateway
Cisco has partnered with AWS to provide end-to-end solutions for joint customers to create the best possible user experience. Customers benefit from fully automated networking to workloads in AWS Cloud and native integration between Cisco SD-WAN and AWS Transit Gateway and Transit Gateway Network Manager.
Sunday, 3 May 2020
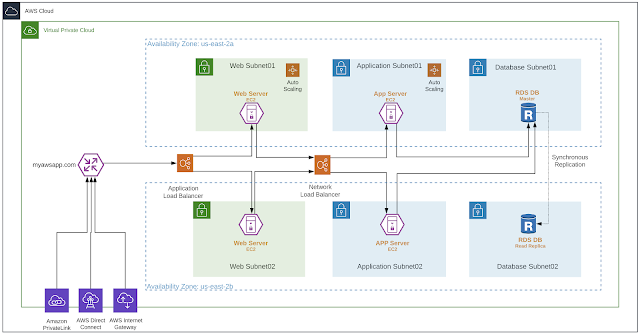
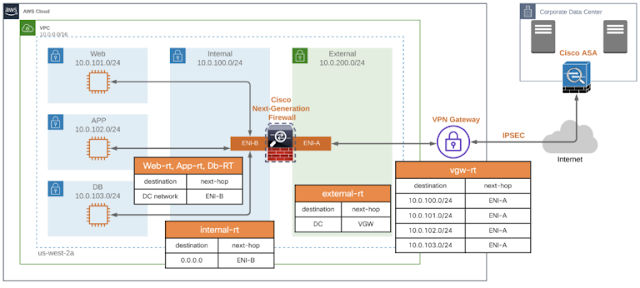
Cisco Secure Cloud Architecture for AWS
AWS recommends three-tier architecture for web applications. These tiers are separated to perform various functions independently. Multilayer architecture for web applications has a presentation layer (web tier), an application layer (app tier), and a database layer (database tier). There is the flexibility to make changes to each tier independent of another tier. The application requires scalability and availability; the three-tier architecture makes scalability and availability for each tier independent.
Tuesday, 7 April 2020
Top 5 features of a Network Traffic Analysis (NTA) tool- Why you need Stealthwatch now more than ever
Research indicates that organizations can’t hire their way out of their cybersecurity woes. CISOs must improve security efficacy, streamline operations and bolster employee productivity, and they must rely on their existing workforce. That’s where Network Traffic Analysis (NTA) tools can provide a cybersecurity quick-win. An effective and modern NTA solution can continuously monitor the network and detect threats that might have bypassed the perimeter or even originated within the business. Top-tier NTA solutions take the weight off of the employees’ shoulders by giving them the tools they need to speed up threat detection and remediation. To help you evaluate an NTA solution effectively, let’s take a look at the top features identified by cybersecurity professionals as part of the research conducted by ESG:
1. Built-in analytics and threat intelligence services
44% of survey respondents said that built-in analytics to help analysts detect suspicious/malicious behavior is one of the most important features. Best-in-class NTA tools have different algorithms and signatures built-in to model behavior and crunch data, allowing for high-fidelity alerts that streamline workloads and accelerate incident response. The same percentage also said that threat intelligence services/integrations to enable comparisons between suspicious behavior and known threats is another top feature. These integrations allow NTA tools to “enrich” network telemetry, making alerts more thorough and actionable.
2. Ability to monitor IoT traffic/devices
Users also need the ability to monitor niche equipment that is unique to their industries. This is especially important in industries that have made aggressive investments in IoT like healthcare, manufacturing and transportation. IoT devices generate telemetry and increase the threat surface like any other connected device, and therefore need to feed into an NTA tool.
3. Ability to monitor all network nodes
37% of respondents stated that alerts for when new network nodes are connected are essential for an NTA tool. This means security professionals want NTA tools to issue alerts when unsanctioned devices connect. This is incredibly important for monitoring and mitigating cyber-risks.
4. Proven integrations with other security technologies
37% also said that one of the most important features is documented and tested integrations with other types of security technologies. These other technologies could be malware sandboxes, network segmentation enforcement technologies and much more. These integrations allow for a closed-loop process that includes network security development, monitoring and enforcement.
5. Public cloud visibility
More than a third of respondents said that the ability to monitor cloud traffic is an essential feature. In order to provide true end-to-end visibility, NTA tools need to be able to tap into VPCs, cloud monitoring logs and APIs across AWS, Azure, GCP, etc.
Cisco Stealthwatch
Stealthwatch aligns well with the most important NTA attributes cited by the surveyed cybersecurity professionals. For example, Stealthwatch:
◉ Features multiple types of built-in analytics. Its behavioral modeling and multi-layered machine learning algorithms can detect hidden threats- even those hiding in encrypted traffic.
◉ Provides comprehensive visibility. In addition to monitoring on-premises environments, Stealthwatch also offers agentless visibility into the public cloud. It can also detect when a new network node connects, monitor traffic from IoT devices and more. Nothing slips through the cracks with Stealthwatch.
◉ Backed by Cisco Talos threat intelligence. Threat intelligence is one of the most important features of an NTA tool. Stealthwatch ties its multi-layered analytics with global threat intelligence from Talos, the largest non-governmental threat intelligence organization in the world, and can take immediate action when activity is associated with a known threat, no matter the origin.
Saturday, 7 December 2019
Configuring Cisco Security with Amazon VPC Ingress Routing
Amazon VPC Ingress Routing is a service that helps customers simplify the integration of network and security appliances within their network topology. With Amazon VPC Ingress Routing, customers can define routing rules at the Internet Gateway (IGW) and Virtual Private Gateway (VGW) to redirect ingress traffic to third-party appliances, before it reaches the final destination. This makes it easier for customers to deploy production-grade applications with the networking and security services they require within their Amazon VPC.
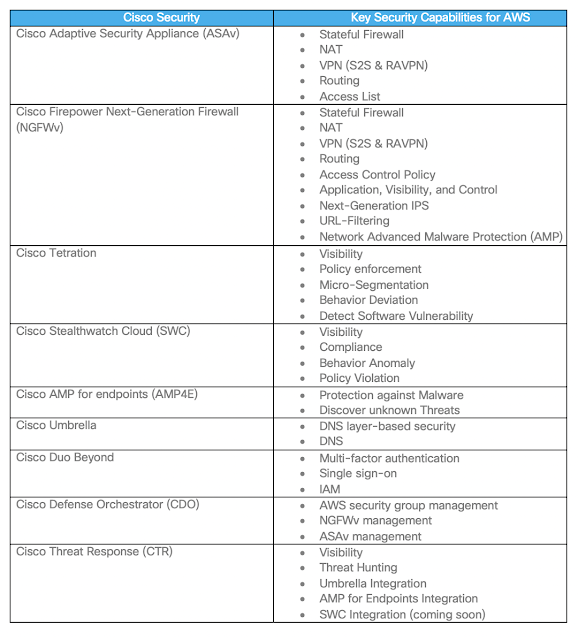
While the remainder of this post focuses on Cisco’s NGFWv and ASAv products, this capability can also be used to deploy a number of other network-based security solutions into the AWS traffic path. This includes services such as the following:
◉ Firewall policy enforcement
◉ Network traffic visibility
◉ Malware detection
◉ URL filtering
◉ Intrusion Prevention
◉ DNS security
How to Use Amazon VPC Ingress Routing with Cisco Firewalls
The configuration is achieved by creating a custom route table and associating subnet routes with the private Elastic Network Interface (ENI) of the security appliance, and then associating the public ENI with an IGW and VGW. A single firewall instance can protect multiple subnets; however, a separate instance is needed per VPC. Below are some details on the testing we performed as well as sample use cases and configuration guidance.
Use Cases / Deployment Scenarios
Cisco NGFWv/ASAv can be deployed in a VPC to protect the following traffic flows:
◉ Traffic Traversing an Internet Gateway (IGW) To/From the Internet
◉ Traffic Traversing a VPN Gateway (VGW) To/From a Remote VPN Peer
Benefits of Using Amazon VPC Ingress Routing with Cisco’s NGFWv and ASAv
◉ Offload NAT from the firewall to AWS network address translation (NAT) gateway or instance
◉ Simplify protection of multi-tier applications spanning subnets and VPCs
◉ The scalable design makes it easy to add new subnets, and more of them
◉ Enables bi-directional, threat-centric protection for traffic bound for private networks and the internet
POC Deployment Scenario
Enable outbound Internet connectivity and offload NAT function to AWS NAT gateway
In this scenario, the Cisco Firewall (NGFWv or ASAv) is deployed between internal services in the AWS VPC and the internet. The route table for the Internet Gateway (igw-rt) has a specific route for the Inside subnet which directs inbound traffic to the Cisco Firewall for inspection. Prior to this enhancement, the users had to NAT egress traffic on the firewall to bring back the reply packet to the same virtual appliance. This new configuration eliminates the need for an ENI on the firewall and removes the requirement to perform NAT on the firewall, thus improving performance.