Today, Amazon Web Services (AWS) announced a new capability in Virtual Private Cloud (VPC) networking that is designed to make it easier and more efficient for Cisco Security customers to deploy advanced security controls in the cloud. This new capability is called Amazon VPC Ingress Routing. It allows users to specify routes for traffic flowing between a VPC and the internet or from a VPN connection, such as a private datacenter.
Amazon VPC Ingress Routing is a service that helps customers simplify the integration of network and security appliances within their network topology. With Amazon VPC Ingress Routing, customers can define routing rules at the Internet Gateway (IGW) and Virtual Private Gateway (VGW) to redirect ingress traffic to third-party appliances, before it reaches the final destination. This makes it easier for customers to deploy production-grade applications with the networking and security services they require within their Amazon VPC.
While the remainder of this post focuses on Cisco’s NGFWv and ASAv products, this capability can also be used to deploy a number of other network-based security solutions into the AWS traffic path. This includes services such as the following:
◉ Firewall policy enforcement
◉ Network traffic visibility
◉ Malware detection
◉ URL filtering
◉ Intrusion Prevention
◉ DNS security
The configuration is achieved by creating a custom route table and associating subnet routes with the private Elastic Network Interface (ENI) of the security appliance, and then associating the public ENI with an IGW and VGW. A single firewall instance can protect multiple subnets; however, a separate instance is needed per VPC. Below are some details on the testing we performed as well as sample use cases and configuration guidance.
Cisco NGFWv/ASAv can be deployed in a VPC to protect the following traffic flows:
◉ Traffic Traversing an Internet Gateway (IGW) To/From the Internet
◉ Traffic Traversing a VPN Gateway (VGW) To/From a Remote VPN Peer
◉ Offload NAT from the firewall to AWS network address translation (NAT) gateway or instance
◉ Simplify protection of multi-tier applications spanning subnets and VPCs
◉ The scalable design makes it easy to add new subnets, and more of them
◉ Enables bi-directional, threat-centric protection for traffic bound for private networks and the internet
Enable outbound Internet connectivity and offload NAT function to AWS NAT gateway
In this scenario, the Cisco Firewall (NGFWv or ASAv) is deployed between internal services in the AWS VPC and the internet. The route table for the Internet Gateway (igw-rt) has a specific route for the Inside subnet which directs inbound traffic to the Cisco Firewall for inspection. Prior to this enhancement, the users had to NAT egress traffic on the firewall to bring back the reply packet to the same virtual appliance. This new configuration eliminates the need for an ENI on the firewall and removes the requirement to perform NAT on the firewall, thus improving performance.
Amazon VPC Ingress Routing is a service that helps customers simplify the integration of network and security appliances within their network topology. With Amazon VPC Ingress Routing, customers can define routing rules at the Internet Gateway (IGW) and Virtual Private Gateway (VGW) to redirect ingress traffic to third-party appliances, before it reaches the final destination. This makes it easier for customers to deploy production-grade applications with the networking and security services they require within their Amazon VPC.
While the remainder of this post focuses on Cisco’s NGFWv and ASAv products, this capability can also be used to deploy a number of other network-based security solutions into the AWS traffic path. This includes services such as the following:
◉ Firewall policy enforcement
◉ Network traffic visibility
◉ Malware detection
◉ URL filtering
◉ Intrusion Prevention
◉ DNS security
This is a big win for Cisco customers deploying our security products in AWS, and we are pleased to have been an early adopter and Integration Partner with AWS on this launch.
How to Use Amazon VPC Ingress Routing with Cisco Firewalls
The configuration is achieved by creating a custom route table and associating subnet routes with the private Elastic Network Interface (ENI) of the security appliance, and then associating the public ENI with an IGW and VGW. A single firewall instance can protect multiple subnets; however, a separate instance is needed per VPC. Below are some details on the testing we performed as well as sample use cases and configuration guidance.
Use Cases / Deployment Scenarios
Cisco NGFWv/ASAv can be deployed in a VPC to protect the following traffic flows:
◉ Traffic Traversing an Internet Gateway (IGW) To/From the Internet
◉ Traffic Traversing a VPN Gateway (VGW) To/From a Remote VPN Peer
Benefits of Using Amazon VPC Ingress Routing with Cisco’s NGFWv and ASAv
◉ Offload NAT from the firewall to AWS network address translation (NAT) gateway or instance
◉ Simplify protection of multi-tier applications spanning subnets and VPCs
◉ The scalable design makes it easy to add new subnets, and more of them
◉ Enables bi-directional, threat-centric protection for traffic bound for private networks and the internet
POC Deployment Scenario
Enable outbound Internet connectivity and offload NAT function to AWS NAT gateway
In this scenario, the Cisco Firewall (NGFWv or ASAv) is deployed between internal services in the AWS VPC and the internet. The route table for the Internet Gateway (igw-rt) has a specific route for the Inside subnet which directs inbound traffic to the Cisco Firewall for inspection. Prior to this enhancement, the users had to NAT egress traffic on the firewall to bring back the reply packet to the same virtual appliance. This new configuration eliminates the need for an ENI on the firewall and removes the requirement to perform NAT on the firewall, thus improving performance.
Cisco NGFW/ASA with AWS IGW (routable attached to IGW) and AWS NGW to NAT outbound traffic
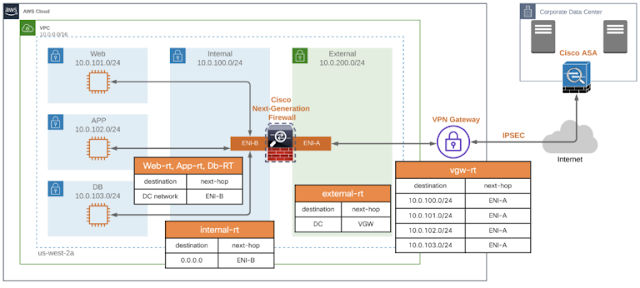
Cisco NGFW/ASA with Multiple Subnets, Three-tier Architecture Using IGW and Amazon VPC Ingress Routing
This topology expands on the previous, demonstrating how multiple subnets can be protected by a single firewall. By utilizing the AWS NAT Gateway service, the number of protected subnets behind a single firewall can be scaled significantly beyond what was previously possible.
As with the previous architecture, the Cisco Firewall is deployed at the edge in routed mode, forwarding outbound traffic to the IGW. Multiple routes are configured in the IGW’s route table to direct the traffic back to the appropriate subnet while the protected subnets forward their traffic to the internal firewall interface via the NAT gateway.
Cisco NGFW/ASA three-tier Architecture with AWS IGW and VPC Ingress Routing
Cisco NGFW/ASA with Multiple Subnets, Three-tier Architecture Using VGW and Amazon VPC Ingress Routing
Cisco Firewalls can also be deployed in an Amazon VPC to inspect traffic flowing through a VPN tunnel. In this case, the Cisco Firewall is deployed at the edge in routed mode, forwarding outbound traffic to the to a VGW. In this example, the local and remote networks are routable; therefore, the NAT gateway can be eliminated, further improving efficiency and reducing cost.
Cisco NGFW/ASA three-tier Architecture with AWS IGW and VPC Ingress Routing
In Addition to Support for Amazon Ingress Routing, we are adding AWS Security Group management to Cisco Defense Orchestrator (CDO). We are also extending the existing ACI policy-based automation for L4-7 services insertion to the AWS cloud by leveraging Amazon VPC ingress routing. These integrations will make deploying L4-7 services in a hybrid cloud as well as Cisco Security at scale in AWS easier than ever.