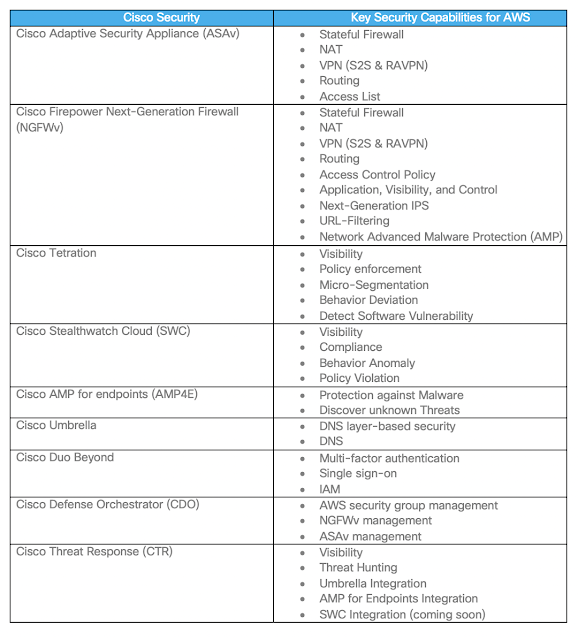
The Cisco Secure Technical Alliance supports the open ecosystem and AWS is a valued technology alliance partner, with integrations across the Cisco Secure portfolio, including SecureX, Secure Firewall, Secure Cloud Analytics, Duo, Umbrella, Web Security Appliance, Secure Workload, Secure Endpoint, Identity Services Engine, and more.
Cisco Secure and AWS Security Lake
We are proud to be a launch partner of AWS Security Lake, which allows customers to build a security data lake from integrated cloud and on-premises data sources as well as from their private applications. With support for the Open Cybersecurity Schema Framework (OCSF) standard, Security Lake reduces the complexity and costs for customers to make their security solutions data accessible to address a variety of security use cases such as threat detection, investigation, and incident response. Security Lake helps organizations aggregate, manage, and derive value from log and event data in the cloud and on-premises to give security teams greater visibility across their organizations.
With Security Lake, customers can use the security and analytics solutions of their choice to simply query that data in place or ingest the OCSF-compliant data to address further use cases. Security Lake helps customers optimize security log data retention by optimizing the partitioning of data to improve performance and reduce costs. Now, analysts and engineers can easily build and use a centralized security data lake to improve the protection of workloads, applications, and data.
Cisco Secure Firewall
Cisco Secure Firewall serves as an organization’s centralized source of security information. It uses advanced threat detection to flag and act on malicious ingress, egress, and east-west traffic while its logging capabilities store information on events, threats, and anomalies. By integrating Secure Firewall with AWS Security Lake, through Secure Firewall Management Center, organizations will be able to store firewall logs in a structured and scalable manner.
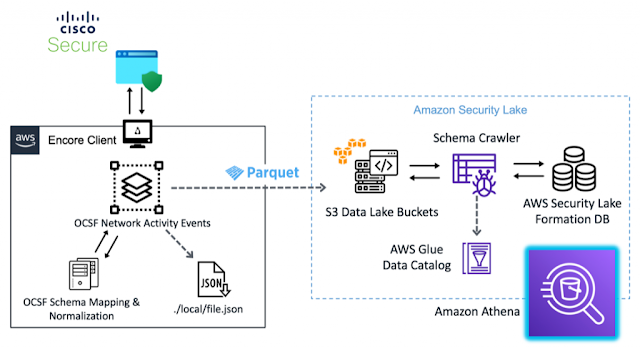
eNcore Client OCSF Implementation
The eNcore client provides a way to tap into message-oriented protocol to stream events and host profile information from the Cisco Secure Firewall Management Center. The eNcore client can request event and host profile data from a Management Center, and intrusion event data only from a managed device. The eNcore application initiates the data stream by submitting request messages, which specify the data to be sent, and then controls the message flow from the Management Center or managed device after streaming begins.
These messages are mapped to OCSF Network Activity events using a series of transformations embedded in the eNcore code base, acting as both author and mapper personas in the OCSF schema workflow. Once validated with an internal OCSF schema the messages are then written to two sources, first a local JSON formatted file in a configurable directory path, and second compressed parquet files partitioned by event hour in the S3 Amazon Security Lake source bucket. The S3 directories contain the formatted log are crawled hourly and the results are stored in an AWS Security Lake database. From there you can get a visual of the schema definitions extracted by the AWS Glue Crawler, identify fieldnames, data types, and other metadata associated with your network activity events. Event logs can also be queried using Amazon Athena to visualize log data.
Get Started
To utilize the eNcore client with AWS Security Lake, first go to the Cisco public GitHub repository for Firepower eNcore, OCSF branch.
Download and run the cloud formation script eNcoreCloudFormation.yaml.
The Cloud Formation script will prompt for additional fields needed in the creation process, they are as follows:
Cidr Block: IP Address range for the provisioned client, defaults to the range shown below
Instance Type: The ec2 instance size, defaults to t2.medium
KeyName A pem key file that will permit access to the instance
AmazonSecurityLakeBucketForCiscoURI: The S3 location of your Data Lake S3 container.
FMC IP: IP or Domain Name of the Cisco Secure Firewall Mangement Portal
After the Cloud Formation setup is complete it can take anywhere from 3-5 minutes to provision resources in your environment, the cloud formation console provides a detailed view of all the resources generated from the cloud formation script as shown below.
Once the ec2 instance for the eNcore client is ready, we need to whitelist the client IP address in our Secure Firewall Server and generate a certificate file for secure endpoint communication.
In the Secure Firewall Dashboard, navigate to Search->eStreamer, to find the allow list of Client IP Addresses that are permitted to receive data, click Add and supply the Client IP Address that was provisioned for our ec2 instance. You will also be asked to supply a password, click Save to create a secure certificate file for your new ec2 instance.
Download the Secure Certificate you just created, and copy it to the /encore directory in your ec2 instance.
Use CloudShell or SSH from your ec2 instance, navigate to the /encore directory and run the command bash encore.sh test
You will be prompted for the certificate password, once that is entered you should see a Successful Communication message as shown below.
Run the command bash encore.sh foreground
This will begin the data relay and ingestion process. We can then navigate to the S3 Amazon Security Lake bucket we configured earlier, to see OCSF compliant logs formatted in gzip parquet files in a time-based directory structure. Additionally, a local representation of logs is available under /encore/data/* that can be used to validate log file creation.
Amazon Security Lake then runs a crawler task every hour to parse and consume the logs files in the target s3 directory, after which we can view the results in Athena Query.
Source: cisco.com