Imagine juggling multiple remotes for your entertainment system, each controlling a different device and requiring endless button presses to achieve a simple task. This is what managing a complex network security landscape can feel like—a jumble of disparate solutions, each demanding your attention and contributing to confusion.
Today’s IT environment is no stranger to complexity. The rise of hybrid work, multicloud adoption, and more sophisticated cyberthreats have created a security landscape that traditional, siloed solutions simply cannot keep pace with. This leaves organizations vulnerable, jeopardizing the security of their data, applications, and user trust.
This is where convergence comes in. It’s just like having a single, universal remote for your entertainment system.
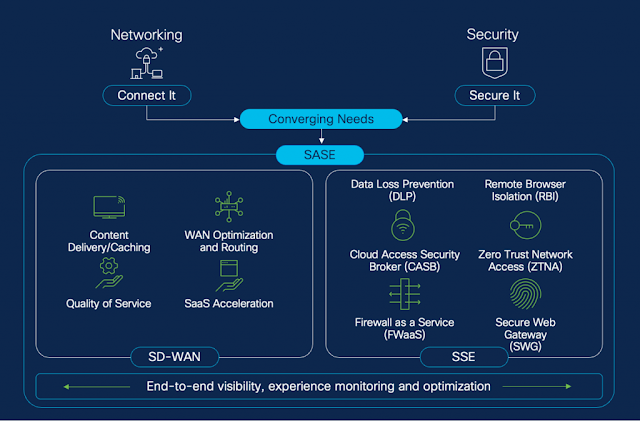
Secure access service edge (SASE) is this “universal remote” for your network security. It offers a converged approach that combines networking and security into a single, cloud-delivered service. By bringing security closer to the user and the cloud edge, organizations can help ensure comprehensive protection regardless of the user’s location or access point.
However, adopting SASE can feel like navigating a maze. Different vendors, complex integrations, and lengthy implementation times can leave you feeling lost. At Cisco, we understand the challenges you face and the need for simplicity. That’s why we’re committed to making your SASE journey simpler and more efficient.
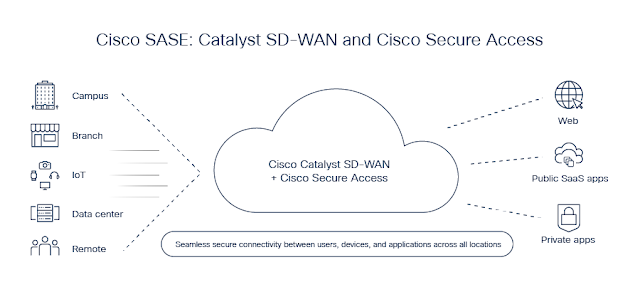
Figure 1: Evolve to full SASE—Catalyst SD-WAN and Secure Access integration
Introducing the integration of Cisco Catalyst SD-WAN and Cisco Secure Access, a cloud-delivered security service edge (SSE) solution. It’s a single, integrated SASE solution that unifies the power of Cisco Catalyst SD-WAN with the robust security of our SSE solution, Cisco Secure Access. This powerful duo forms the foundation of our integrated Cisco SASE solution, offering a simplified path to robust security and streamlined management.
You can think of Catalyst SD-WAN as the intelligent highway, optimizing network traffic flow and ensuring reliable connectivity. Cisco Secure Access, meanwhile, functions as the tollbooth or security checkpoint, allowing only authorized users and devices access. When these two solutions are integrated, they offer a streamlined and efficient approach to SASE, helping to ensure secure and efficient access for your data, applications, and users.
Catalyst SD-WAN and Cisco Secure Access (SSE) combine to transform your network’s performance and security. Through Catalyst SD-WAN’s advanced networking technology, your data is intelligently routed along the most efficient pathways, optimizing cloud application performance and reducing latency by connecting users to the nearest point of presence (PoP). This ensures enhanced redundancy and supports the high bandwidth demands of specialized regional sites, underpinning your network’s scalability and agility.
Cisco Secure Access serves as a robust cloud-based security shield, embodying the zero-trust approach by thoroughly verifying and continuously monitoring each access attempt, while diligently scanning internet traffic to safeguard your network against the spectrum of emerging cyberthreats.
The integration simplifies the transition to SASE by eliminating the complexities of multivendor environments. A unified management platform offers centralized control and oversight of both networking and security functions, significantly reducing operational complexity and saving IT resources. This comprehensive control enhances decision making, streamlines workflows, and ensures a cohesive security posture across the entire network infrastructure.
Let’s explore how this integrated solution empowers you to address common security challenges.
- Securing branch offices and internet SaaS traffic: Branch offices and roaming users are particularly vulnerable to cyberthreats, especially with the growing adoption of Direct Internet Access (DIA). Our seamless integration extends robust cloud security across your entire SD-WAN fabric, protecting branch offices and users accessing internet and cloud-based applications.
- Empowering zero-trust security: Our solution requires rigorous verification for every access attempt. This continuous monitoring approach ensures only authorized users and devices gain access to critical resources. By leveraging Cisco segmentation and micro-segmentation capabilities, you can effectively isolate critical network segments and resources, significantly reducing the attack surface and hindering unauthorized access.
- Rapid deployment: Through the Cisco automation framework, you can rapidly deploy secure connectivity for hundreds or thousands of branch sites to Cisco Secure Access within minutes. This eliminates the need for complex, time-consuming manual configurations.
- Streamlined customer onboarding: The streamlined purchasing process through the buying tool not only simplifies acquiring licenses but also automatically initiates the creation of tenant spaces tailored for your organization. This pivotal feature represents a significant value-add, seamlessly transitioning customers from the acquisition phase to operational readiness.
The benefits of this integrated SASE solution go beyond just simplifying your security stack, and include:
- Enhanced security: Elevate protection for internet and SaaS traffic at branch offices, while effortlessly steering traffic for additional security. Benefit from a comprehensive suite of security features, including secure web gateway (SWG), Cloud Access Security Broker (CASB), data loss prevention (DLP), zero trust network access (ZTNA), firewall-as-a-service (FWaaS), and IPS.
- Meet converged networking and security needs at scale: Deploy robust SASE architectures on top of your existing Catalyst 8000 series routers for high-throughput branch sites.
- Distributed security enforcement offers tailored security, efficient traffic management, and enhanced protection. It combines on-premises NGFW on the Catalyst 8000 with cloud-based Cisco Secure Access, providing flexibility, scalability, and cost efficiency. This model enables organizations to tailor their security posture to specific needs, offering a robust defense against cyberthreats and empowering them to manage demanding network traffic with strong security measures.
- Operational efficiency: Simplify security implementation with policy-based routing and automated failover, minimizing complexity and ensuring smooth operation.
- Enhanced user experience: Deliver consistent, unwavering security for roaming users, regardless of location, for a more seamless user experience.
- Unparalleled agility: Scale security effortlessly to adapt to your evolving environment, enabling rapid and flexible responses to changing demands.
- Unmatched network visibility and troubleshooting: Combining Cisco Catalyst SD-WAN, ThousandEyes, and Secure Access delivers exceptional network visibility and troubleshooting capabilities. This powerful integration optimizes traffic flow, enhances digital experience assurance by securing user connections, and ensures robust connectivity across your entire network. Gain a comprehensive view of network health, streamline problem resolution, and create a resilient and efficient digital environment.
- Always ahead of threats: Leverage the power of Cisco Talos threat intelligence for real-time insights that identify, correlate, and remediate threats at exceptional speed.
Jumpstart your SASE journey with ease
The integrated power of Cisco Catalyst SD-WAN and Cisco Secure Access unlocks a scalable, secure, and simplified path to SASE. This powerful combination, merging the best of networking and security into a single solution delivers a unified experience for both IT and users. Centralized management of your entire network and security posture streamlines operations and simplifies SASE adoption. Additionally, users enjoy unmatched security with consistent protection across the network, regardless of location.
Source: cisco.com