This week, I’m attending Cisco Live in Amsterdam! Together with my team, we’re excited to exchange insights and network with our customers and industry leaders. Our focus is to interact with customers firsthand, grasp their preferences, and highlight how our latest portfolio upgrades cater to their requirements.
Up to this point in the event, numerous customers have emphasized that cybersecurity in industrial settings is a primary concern, alongside the introduction of the new NIS2 regulations. Our team is present to assist customers in navigating and adhering to these latest regulations, ensuring a seamless transition as we adjust to new mandates. Let me share some insights into NIS2 and outline our investments aimed at aiding customers.
Cisco helps customers comply with NIS2 regulations to reduce cyber risk with enhanced cybersecurity capabilities
The European Union created Network and Information Security (NIS2) to update and strengthen the existing NIS1 framework, addressing emerging cybersecurity threats and evolving technological landscapes more effectively. The intent is to enhance cybersecurity resilience and coordination across critical sectors and digital service providers. It will impact more than 350,000 organizations and will extend to non-European companies that are part of the EU supply chain. This directive will be enforced as of October 18, 2024.
To comply with NIS2 requirements, customers need a good understanding of their security posture to implement cyber risk management best practices and zero-trust security policies. Meeting these requirements requires our customers to control risks from their supply chain (machine builders, control system vendors, contractors, hardware service providers, etc.) as well as risks from connected assets that now need access to external applications and cloud services. This translates into a problem of scale for our customers due to the diverse ecosystem of supply chain vendors, and tens of thousands of assets in their environments.
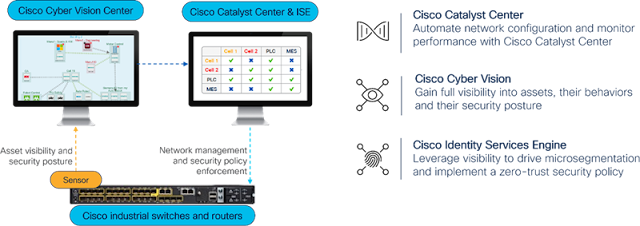
Cisco has comprehensive capabilities and a market-leading industrial networking portfolio, which helps our customers address these challenges. Our portfolio complies with ISA/IEC 62443 security standards so that customers can trust their supply chain.
The Industrial IoT team has been investing in enhancements to industrial security solutions, Cisco Cyber Vision and Secure Equipment Access, to help customers reduce cyber risk and drive compliance with NIS2 cybersecurity regulations as they securely connect assets in their critical infrastructure.
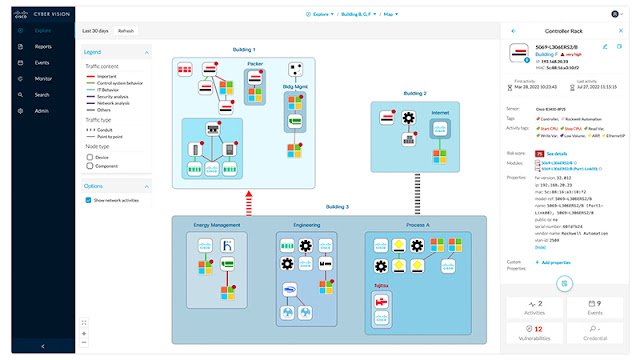
First, we have enhancements to Cisco Cyber Vision with new reports and risk scores from Cisco Vulnerability management. Cyber Vision software, deployed on the industrial network, builds a detailed inventory of all connected assets and their security posture. This will help customers monitor and manage cyber risks of their OT assets. The new report engine helps industrial organizations drive compliance and governance by sharing OT Security Posture insights with all stakeholders.
“With Cyber Vision, we now have the visibility into our mission-critical OT networks as a first step to mitigate vulnerabilities and improve our security posture. Cyber Vision found more than 20 instances of malware in our substations and identified features and protocols that don’t need to be active.”
– Emerson Cardoso, Chief Information Security Officer, CPFL Energia
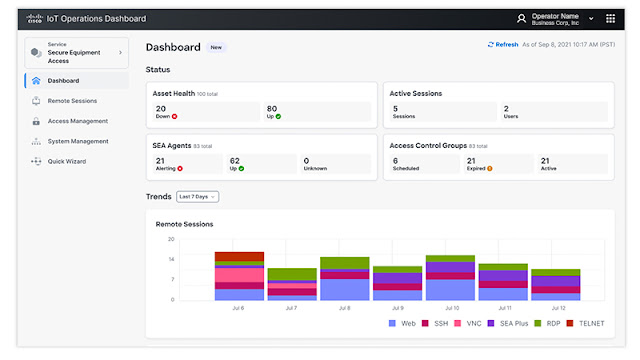
External users need to connect to OT assets for maintenance and troubleshooting. Operational teams can use Cisco Secure Equipment Access to remotely deploy, configure, and troubleshoot assets and applications connected to Cisco industrial routers and switches. Secure Equipment Access solution adopts a ZTNA architecture that enforces strong security controls to grant remote users access only to specific resources at specific times. Another exciting announcement is the new Secure Equipment Access dashboard that helps administrators to monitor and audit remote access activities and trends for compliance. The dashboard works to enable advanced users and partners to automate remote access workflows with a new set of APIs for easy integration with other software solutions.
“As the NIS2 cybersecurity regulation is implemented across Europe, our industrial customers need to better control remote access to their operational networks. Cisco Secure Equipment Access simplifies the enforcement of zero-trust network access policies within an OT environment. By embedding this capability into the industrial network, Cisco makes it easy for customers to deploy OT cybersecurity at scale.”
– Damiano Di Mauro, OT Networking Solutions Team Leader, Lutech (Cisco partner)
In our journey to help customers with Cyber Vision capabilities, we are very excited to see our partner Orange launching ‘Secure Industrial LAN’ managed service for industrial organizations. They are combining the Cisco Industrial IoT networking portfolio with Cisco Cyber Vision for OT security and skilled resources from Orange Cyberdefense and Orange Business worldwide. This service can be delivered to multinational customers with production sites across the globe with a single offer.
“As industries are accelerating the digitization of their operations, they need help to manage and secure industrial networks anywhere they are on the globe. By combining Cisco’s leading industrial networking and OT security portfolio with Orange Business’ and Orange Cyberdefense’s IT and OT expertise with human resources worldwide, our Secure Industrial LAN offer is the ideal solution for industrial organizations to scale their operations, improve resilience, and meet ever-growing cybersecurity regulations.”
– Emmanuel Routier, VP Smart Industries, Orange Business (Cisco partner)
The excitement of new enhancements doesn’t just stop there. Because different industries and use cases require different network technologies and capabilities for connectivity, we are continuing to expand our industrial networking portfolio to ensure customer success for a variety of deployment scenarios and locations. Therefore, we are also announcing:
- Catalyst IW9167E is now available for hazardous environments (Class 1, Div 2), so that customers in locations such as oil & gas, chemical, and pharmaceutical can deploy Wi-Fi or Cisco Ultra Reliable Wireless Backhaul (Cisco URWB).
- The Catalyst IW9165 series now also supports Wi-Fi 6/6E as well as Cisco URWB. With different form factors, we are enabling customers to deploy in more locations such as inside a cabinet in manufacturing, and roadways intersections.
- The 5G PIM now supports both public and private standalone on Catalyst Industrial Rugged Routers (IR1100, IR1800, IR8300) for roadways (cameras and sensors at intersections), public safety (ambulances, police cars), utilities, and other mission critical industrial settings.
If you are at Cisco Live Amsterdam, come and find the Cisco Industrial IoT Team at the World of Solutions to experience live demos and a coffee machine powered by Catalyst Center and Secure Equipment Access. Innovation and a cup of coffee come together to fuel digitization and connectivity for the whole week. I look forward to seeing you there!
Source: cisco.com