Tuesday, 2 July 2024
Security Is Essential (Especially in the Cloud)
Monday, 1 April 2024
Mastering CCNP Security 300-740 Exam: An In-Depth Look
In the ever-evolving field of network security, standing out as an IT professional requires not just skill, but validation of that skill. The CCNP Security 300-740 certification emerges as a beacon for those dedicated to mastering Cisco networks' security. This coveted credential is more than a certificate; it's a badge of honor that signifies your prowess in deploying and managing cutting-edge security measures in the cyber world.
Diving Deep into the CCNP Security 300-740 Exam
At the heart of the CCNP Security certification lies the 300-740 exam, a rigorous test that probes your knowledge across various pivotal security domains such as secure network access, content security, and navigating the complexities of cloud security. Crafted meticulously, the 300-740 SCAZT exam ensures that those who pass can shield network infrastructures against the threats of today and tomorrow.
300-740 SCAZT Exam Breakdown:
Duration: 90 minutes
Question Count: Between 55 to 65
Passing Score: Typically falls between 750 and 850 out of 1000
Format: A mix of multiple-choice and simulation-based questions
Validity: 3 years before renewal is required
CCNP Security Exam Preparation Pathways
Official Cisco Resources: Dive into the wealth of knowledge provided through Cisco's own training courses. These not only cover the theoretical aspects but also offer practical lab exercises.
Comprehensive Study Guides: Bolster your preparation with detailed study materials that go in-depth into each 300-740 exam topic.
Practice Makes Perfect: Regular practice exams are invaluable. They pinpoint areas needing improvement and familiarize you with the Cisco SCAZT exam's structure and pacing.
Community Engagement: Connect with peers through forums and study groups. Sharing insights and experiences can provide unique perspectives and study tips.
Best Tips to 300-740 Triumph
Know What's Expected: Thoroughly understanding the 300-740 SCAZT exam objectives can give you a clear roadmap of what to study.
Strategic Study Plan: Allocate your study time wisely, ensuring each topic gets the attention it deserves, with regular reviews.
Real-World Application: There's no substitute for hands-on experience. Create a lab environment to practice real-world security scenarios on Cisco networks.
Stay Informed: The cybersecurity landscape is dynamic. Keep abreast of the latest trends and technologies that could be included in the CCNP Security exam.
Career Advancement Post-Certification
Earning the CCNP Security 300-740 certification can significantly propel your career forward, marking you as a seasoned professional ready to tackle complex security challenges. Career doors that may open include roles as a Network Security Engineer, Security Analyst, Cybersecurity Specialist, or Network Administrator with a security focus.
Benefits of Being CCNP Security Certified:
Industry Credibility: CCNP Security certification is a gold standard in IT, highlighting your expertise in Cisco's security solutions.
Career Growth: It paves the way for advanced roles, showcasing your dedication to professional growth and security mastery.
Skill Enhancement: Preparing for the 300-740 SCAZT exam deepens your understanding of network security, from principles to best practices.
Salary Upside: Certified professionals often enjoy higher salaries and better job prospects.
Global Recognition: Cisco's certifications are acknowledged worldwide, opening international career opportunities.
Considering the Challenges:
Investment Required: Achieving certification comes with its costs, including exam fees and study materials.
Time Management: The extensive study required demands a significant time commitment.
Keeping Pace with Technology: As security technologies evolve, so must your knowledge, necessitating continuous learning.
Exam Rigor: The CCNP Security exam's challenging nature demands a solid grasp of complex concepts and hands-on experience.
Specialization: While highly valuable for those in network security, it might not offer the same benefits for individuals in non-Cisco environments or different IT areas.
Conclusion
The journey towards obtaining the CCNP Security 300-740 certification requires dedication, consistent studying, and practical application. It is a path that not only enhances your professional life but also distinguishes you as an expert in the vital field of network security. By embracing the challenge and making the most of the resources available, you can unlock a new realm of career opportunities and personal growth in the IT security domain.
Saturday, 20 May 2023
How Cisco’s SaaS Solutions on AWS Deliver Unbeatable Value to Customers and Partners
Cisco’s SaaS Key Solutions Use cases
Sunday, 22 January 2023
Launch Your Cybersecurity Career with Cisco CyberOps Certifications | Part 1
Cisco CyberOps Certification Evolution
Cisco SOC Tier 1 Analyst Learning Path
SOC Analyst Job Outlook
Thursday, 3 November 2022
Be on Guard This Spooking Spanning Tree Season
It was a dark and stormy night…
Enough of the trick already, Hank… where’s the treat?
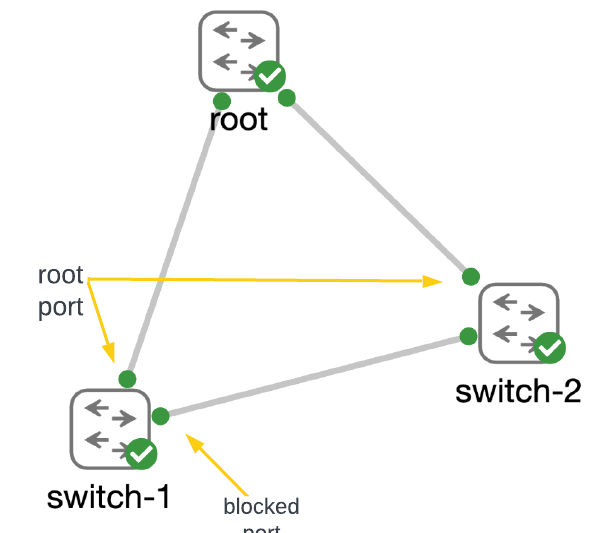
You are NOT root: Preventing unexpected root bridges with root guard
Identifying the root bridge for the network
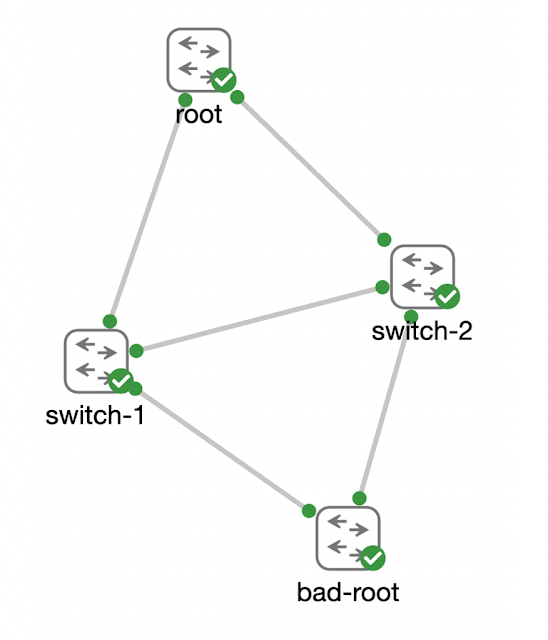
Stopping a new root on the block… err, network
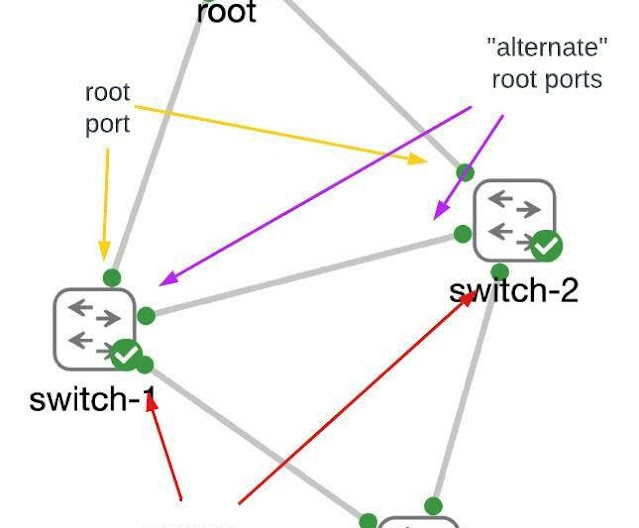
Bringing out the Guard… root guard, that is
Take the scare out of spooky spanning tree with knowledge
Sunday, 22 May 2022
How Cisco DNA Assurance Proves It’s ‘Not a Network Issue’
When something in your house breaks, it’s your problem. When something in your network breaks, it’s everyone’s problem. At least, that’s how it can feel when the sudden influx of support tickets, angry phone calls, and so on start rolling in. They quickly remind you that those numbers behind the traffic visualizations are more than numbers alone. They represent individuals. That includes individuals who don’t notice how the infrastructure supports them until suddenly… it’s not.
The adage that “time is money” applies here, and maybe better than anywhere else. Because when users on the network cannot do what they came to do, the value of their halted actions can add up quickly. That means reaction can’t be the first strategy for preserving a network. Instead, proactive measures that prevent problems (ha, alliteration) become first-order priorities.
That’s where Cisco DNA Center and Assurance comes in, and along with it, Leveraging Cisco Intent-Based Networking DNA Assurance (DNAAS) v2.0, the DNAAS course.
Let’s Start with Intent
This will come as no surprise to anyone, but networks are built for a purpose. From a top-down perspective, the network provides the infrastructure necessary to support business intent. Cisco DNA Center allows network admins and operators to make sure that the business intent is translated into network design and functionality. This ensures that the network is actually accomplishing what is needed. Cisco DNA Center has a load of tools, configs, and templates to make the network functional.
What is Cisco DNA Assurance?
Cisco DNA Assurance is the tool that keeps the network live. With it, we can use analytics, machine learning, and AI to understand the health of the intent-based network. DNA Assurance can identify problems before they manifest into critical issues. DNA Assurance allows us to gauge the overall health of the network across clients, devices, and applications and establish an idea of overall health. From there, we can troubleshoot and identify consistent issues compared to the baseline health of the network — before those issues have a significant impact. We don’t have to wait for an outage to act. (Or react.)
We’re no longer stuck in this red-light or green-light situation, where the network is either working or it’s not. When the light goes from green to yellow, we can start saying, “Hey, why is that happening? Let’s get to the root cause and fix it.”
Obviously, this was all-important before the big shift to hybrid work environments, but it’s even more critical now. When you have a problem, you can’t just walk down the hall to the IT guy, you’re sort of stranded on an island, hoping someone else can figure out what’s wrong. And on the other hand, when you’re the person tasked with fixing those problems, you want to know what’s going on as quickly as possible.
One customer I worked with installed Cisco DNA Assurance to ‘prove the innocence of the network.’ He felt that being able to quickly identify the network problem, especially if it was not necessarily a network issue, helped to get fixes done more quickly and efficiently. DNA Assurance helped to rule out the network or ‘prove it was innocent’ and allow him to narrow his troubleshooting focus.
Another benefit of DNA Assurance is that it’s built on Cisco’s expertise. 30+ years of experience with troubleshooting networks and devices have gone into developing Assurance. Its technology doesn’t just give you an overview of the network, it lets you know where things are going wrong and helps you discover solutions.
About the DNAAS course
Leveraging Cisco Intent-Based Networking DNA Assurance (DNAAS) v2.0 is the technology training course we developed to teach users about Cisco DNA Assurance. The course is designed to give a clear understanding of what DNA Assurance can do and to build a deep knowledge of the capabilities of the technology. It’s meant to give new users a firm handle on the technology while increasing the expertise of existing users and empowering them to further optimize their implementation of DNA Assurance.
One of the things we wanted to do was highlight some of the areas that users may not have touched on before. We give them a chance to experience those things and potentially roll them into tangible solutions on their own network. It’s all meant to be immediately actionable. Users can take this course and instantly turn back around and do something with the knowledge.
Labs are one of the ways that we’ve focused on bringing more of the experience to users who are taking the course. New users are going to interact with a real DNA Center instance, and experienced users are going to have the chance to see new configurations. We build out the fundamental skills necessary to use DNA Assurance, rather than focusing on strict use cases.
We treated it like learning to drive a car. We could teach you all the specifics about one highly specialized vehicle, or we could give you the foundational skills necessary to drive anything and allow you to work towards your specific needs.
Overall, students are going to expand their practical knowledge of DNA Assurance and gain actionable skills they can immediately use. DNAAS is an excellent entry into the technology for new users and an equally excellent learning opportunity for experienced users. It helps build important skills that help users to get the most out of the technology and keep their networks running smoothly.
Source: cisco.com
Saturday, 30 April 2022
ChatOps: How to Build Your First Webex Bot
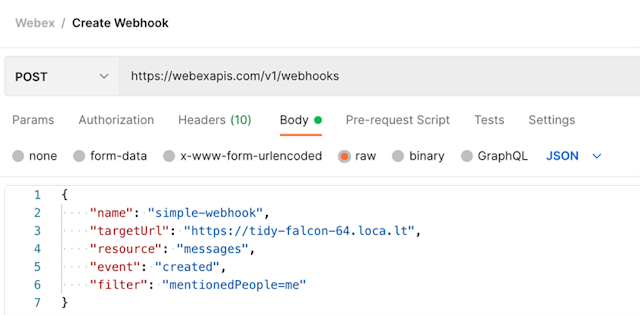
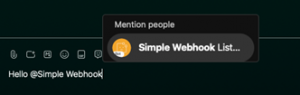
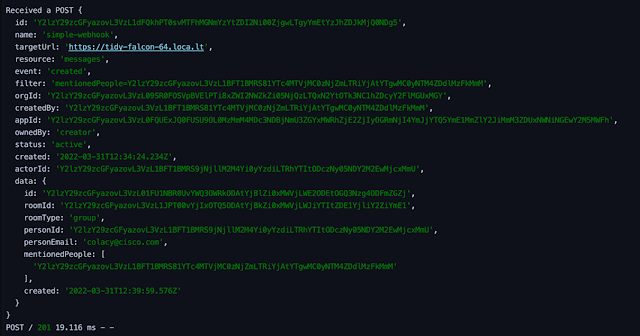
In this post, you’ll learn how to create a Webex bot, register a Webhook in Webex, and configure your bot to listen to Webhook – all with plenty of code examples. Check back for more as we build new use cases that leverage different aspects of automation using chat-driven interfaces.
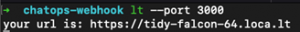
In the DevOps world, we’re always looking for new ways to drive automation around communication. When we deploy new code, scale our deployments, or manage our feature flags – we want our teams to know about it. The Webex API makes it easy to build announcement flows triggered by successful events in our infrastructure. However, if we can trigger those events from Webex as well, then we’ve entered the world of ChatOps.
More Info: 300-835: Automating Cisco Collaboration Solutions (CLAUTO)
ChatOps is the use of chat clients like Webex Teams, chatbots, and real-time communication tools to facilitate how software development and operation tasks are communicated and executed. Using Webex APIs, we can build bots that allow us to enter commands that manage our infrastructure, trigger approval workflows, deploy code, and much more.
Security Disclaimer
Security is a top concern here at Cisco. In normal application development, security should always be built into the initial steps of getting code up and running. Today, we’re going to keep it simple and focus on the basics. Then, we’ll cover how to authenticate and authorize Webhook requests. We’ll hold off on security until the next blog post in our ChatOps series, once we’ve proven an end-to-end connection.
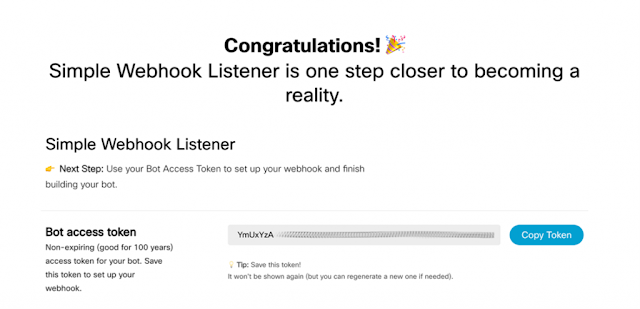
How to create a Webex bot
First, let’s create a Webex bot using the Webex Developer UI.