There are many ways to build out an extended detection and response (XDR) solution; that may be why so many options exist in the marketplace. However, email security is an undeniably critical component in most customer scenarios. Its strengths lie in its ability to enrich incidents, gather actionable telemetry, provide visibility for greater context, and empower quicker response times. This analysis and understanding of data intent — and the subsequent ability to speed remediation — make email security foundational to an effective XDR strategy.
What should be built into your XDR strategy?
◉ Ability to share data rapidly between existing security layers
◉ Greater context and enriched threat investigation and response
◉ Automated security responses
What should an XDR solution provide?
◉ A visual representation of real threats you are investigating
◉ Easy to understand, quick to comprehend results
◉ A seamless way to extend your existing security product
Email administrators use this XDR strategy when investigating threats against end-users in your organization. Using Cisco Secure Email Threat Defense, Cisco bakes this in from the start.
A single email contains many identifiable data dispositions that your email security platform already uses to analyze and act against – IP addresses, URLs, hostnames, and attachments (SHA-256 hash). This data is a gold mine of information used in your XDR platform.
Figure 1: Snapshot of threat techniques in a phishing email
Message tracking shows the verdict of the message and the techniques used to categorize and score the email as a threat. In addition, you’ll see pertinent information such as Sender, Recipient, Attachments, and URLs – the expected data points. Email Threat Defense provides these powerful search capabilities to give you quick access to these message details that empower more informed responses. Remediating threats directly in Cisco XDR and Threat Response streamlines processes and saves valuable time.
Share data between existing security layers
Your XDR strategy needs to deliver this data between security layers. Cisco XDR builds a data correlation map of a message and all related dispositions. Direct results allow further queries and information gathering by giving you a visual, interactive investigation representation.
Figure 2: Example of an XDR investigation starting with a threat message.
IP addresses seen can be added to an inbound policy outside the email platform. Interact with the URL and see judgments, or perhaps sandbox and re-evaluate it in real time. Add the SHA256 to your Secure Endpoint blocklist. These are all now key functionalities of XDR that empower you and your team to make faster, data driven decisions.
Aid and enrich threat investigation and response
Your XDR extensibility should continue with more than just Cisco security products. You can use your existing third-party products for additional intelligence and include extensions to help build your response action.
Figure 3: Extensible options to quarantine and isolate observables
Cisco and Cisco Talos Intelligence Group provide excellent detection and response, rule sets, and a vast intelligence library. In addition, we work closely with partners and additional third-party providers that help to defend against known and emerging threats, new vulnerability discovery, and threat interdiction. Utilizing an external threat feed provider or incorporating your direct private intelligence are vital drivers to XDR collaboration techniques.
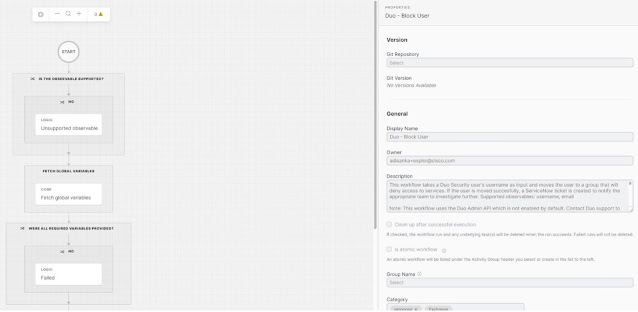
Automate security responses
Cisco XDR rounds out the strategy with orchestration, allowing you to automate responses with various solutions, specifically providing additional detections and actions.
Figure 4: Pre-built orchestrations in XDR, this example blocks user access.
Orchestration allows prebuilt workflows ready to combine the telemetry, security need, and subsequent actions readily available to execute. This automation alleviates the need for redundant or recurring motions that take up your team’s valuable resources and allows them to focus on more strategic initiatives.
Source: cisco.com







0 comments:
Post a Comment