SecureX is Cisco’s free, acronym-defying security platform. (“Is it XDR? Is it SOAR? Does it solve the same problems as a SIEM? As a TIP?” “Yes.”) From the very beginning, one of the pillars of SecureX was the ability to consume and operationalize your local security context alongside global threat intelligence.
Thursday, 29 July 2021
Threat Intelligence in SecureX: Fast, Free, or Easy (pick any three)
Saturday, 29 May 2021
Cisco Secure Firewall insertion using Cisco cAPIC in Azure
In today’s world, enterprises are undergoing a transition to innovate rapidly, keep up with the competition, and increase application agility to meet ever-changing customer demands. To achieve these goals, they often choose the hybrid cloud infrastructure approach, choosing different infrastructure environments to deploy different types of applications. Some applications are best suited for hosting on-premises, whereas others are better suited for hosting in public cloud. Thus, hybrid cloud is the new normal for many organizations. However, in a hybrid cloud environment, the challenge is to maintain a uniform enterprise operational model, comply with corporate security policies, and gain visibility across the hybrid environments.
Read More: 300-710: Securing Networks with Cisco Firepower (SNCF)
Cisco Cloud Application Centric Infrastructure (Cisco Cloud ACI) is a comprehensive solution that provides:
◉ simplified operations
◉ consistent security policy management
◉ visibility across multiple on-premises data centers and public clouds or hybrid cloud environments
◉ unified security policy for the hybrid cloud
◉ extends on-premises layer-7 security to public cloud
In an on-premises Cisco ACI data center, Cisco Application Policy Infrastructure Controller (APIC) is the single point of policy configuration and management for all the Cisco ACI switches deployed in the data center. Cisco ACI multi-site orchestrator (MSO) provides a seamless way to interconnect multiple cisco ACI data centers. MSO is a software solution representing a single point of policy orchestration and visibility across multiple geographically dispersed ACI sites.
Cisco Cloud APIC runs natively on supported public clouds to provide automated connectivity, policy translation, and enhanced visibility of workloads in the public cloud. Cisco Cloud APIC translates all the policies received from MSO and programs them into cloud-native constructs such as VNets (Virtual Network), application security groups, network security groups, outbound rules, inbound rules, etc. This new solution brings a suite of capabilities to extend on-premises data centers into true hybrid cloud architectures, helping drive policy and operational consistency regardless of where your applications reside. Also, it provides a single point of policy orchestration across hybrid environments, operational consistency, and visibility across clouds.
Traditional firewall integration in on-prem Data Centers
Hybrid Cloud
Securing Azure with virtual ASA and FTD solutions
Use case 1: Spoke to Internet (N/S traffic flows)
Use case 2: Spoke to spoke multi-node inter-VPC, intra-region traffic flow enablement
Monday, 8 March 2021
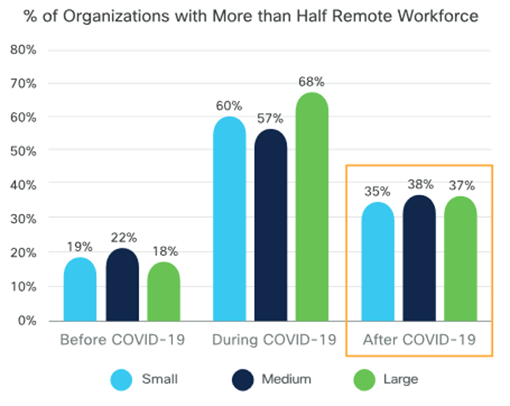
Balancing Safety and Security During a Year of Remote Working
The pandemic brings new security challenges
Cisco technology for secure, remote work
“Cisco security has definitely proven to be the correct choice, because Cisco enables a strong security posture for remote work. When the rapid move to remote work happened, my biggest concern was helping people configure local printers and scanners, not scrambling to secure the enterprise.”
Thursday, 10 September 2020
Introducing Stealthwatch product updates for enhanced network detection and response
Automated Response updates
Release 7.3, introduces automated response capabilities to Stealthwatch, giving you new methods to share and respond to alarms through improvements to the Response Management module, and through SecureX threat response integration enhancements.
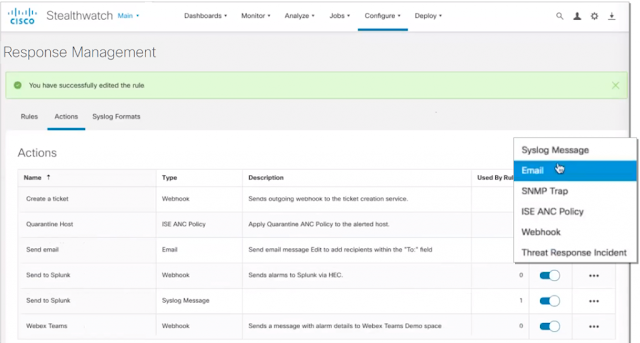
New methods for sharing and responding to alarms
Stealthwatch’s Response Management module has been moved to the web-based UI and modernized to facilitate data-sharing with 3rd party event gathering and ticketing systems. Streamline remediation operations and accelerate containment through numerous new ways to share and respond to alarms through a range of customizable action and rule options. New response actions include:
◉ Webhooks to enhance data-sharing with third-party tools that will provide unparalleled response management flexibility and save time
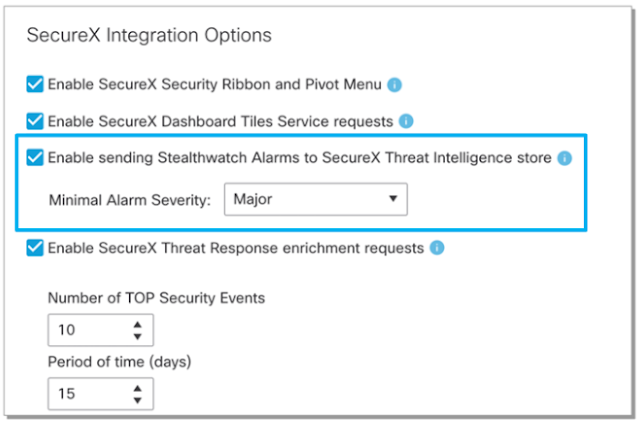
◉ The ability to specify which malware detections to send to SecureX threat response as well as associated response actions to accelerate incident investigation and remediation efforts
◉ The ability to automate limiting a compromised device’s network access when a detection occurs through customizable quarantine policies that leverage Cisco’s Identity Services Engine (ISE) and Adaptive Network Control (ANC)
Enhanced security analytics
Easier management
Sunday, 2 August 2020
The Transformation of Software Testing
A trickier legacy issue to address is that IT buyers have lost trust in existing software development processes to deliver high quality code in dot zero releases. Instead they wait by default for future point deliveries, expecting more acceptable quality before even considering testing a release. Resolving this trust issue is a root driver of the transformation of testing.
We discussed the necessary shift in mindset required to digitize software development by making every person a developer and democratizing the entire process. We also touched on the value of integrating testing developers into the early design and develop stages. In this second post, we will examine in more detail this shift in testing to understand how it transforms the entire development cycle to the benefit of customers as well as developers.
Our goal in the Cisco platform independent group, which provides routing and control plane protocols and DevOps tools to the XE, XR and NX software development teams, is to digitize and transform processes and skillsets to create a hyper-efficient development organization. In particular, we are integrating the development of unit, integration, feature, system, and solution tests into the early stages of the development cycle with real-world use cases based on diverse customer network hardware and software configurations and topologies. How do we capture this detailed customer information? We listen. We share. We communicate.
Bidirectional Communication with Customers Critical in Early Development Stage
We are engaging customers much earlier in the development lifecycle with a goal to build a bidirectional communications channel between Cisco development and customers. First, we listen to understand customer requirements, topologies, and traffic patterns and feed those parameters into our design documents. We request customers’ device configuration files so we can prepare test plans incorporating an appropriate mix of “live in the field” hardware and software environments. We then verify with customer IT teams our design specifications to ensure a mutual understanding of goals. By providing insights into feature functionality and sharing test plans, customers can better prepare for implementation before the final release. Customers can also share their proposed test plans with our teams so that special use cases can be incorporated into our test plans as well.
Cisco customers have been eager to participate in early engagement opportunities to provide real-time feedback on specific feature designs and implementations. A participating customer related to our teams that the recent collaboration with Cisco Engineering “…was fruitful as it ensured that Cisco’s implementation of a specific feature was matching our expectations. Early engagement helps us understand new features so we can create successful design documents as well as train our certification teams. This early collaborative process also helps our team avoid ‘working as designed’ surprises during our testing.”
These collaborations among Cisco development teams and customers result in a reimagining of test design and procedures that permeate the development lifecycle.
Reimagining Testing Throughout Development
As we’ve previously discussed, within our platform-independent teams, everyone is a developer—from solution architects and designers to coders and testers. Each role plays a hand in ensuring the solutions and tools we build meet our customers’ requirements—whether internal teams or external enterprise IT organizations.
One key method of transforming testing efficiency and completeness is to integrate developers into the process who have in-depth experience with customer implementations, configurations, and troubleshooting. They participate upfront in the design stage to ensure that new features will work in real-world brownfield as well as greenfield environments. This change makes it possible to evolve from thinking primarily in terms of individual features that are designed, developed, and tested in isolation, to a customer-oriented solution approach. While each feature is coded with specific functionality by design, each must also be implemented as part of a complete networking ecosystem. Applying this philosophy not only helps identify unintended feature interactions, but also moves defect discovery to much earlier in the development cycle, in effect flattening the curve of found defects throughout the development cycle—a primary goal of testing transformation.
New features are not the only testing points to emphasize during the design phase. Since the main “users” of networking software are highly-trained technical professionals, serviceability is key to keeping them productive. For example, interfaces providing data such as telemetry and error codes, as well as CLI formats, are designed from the technical users’ point of view. In design documents, we consider how to expose sufficient debug information to enable faster problem resolutions, but without overwhelming technicians with irrelevant details. Here we are applying machine reasoning to assist in triaging issues. Ease of configuration of network devices and Day 2 management are also critical considerations for testing usability and serviceability. Training and automated checklists ensure that developers are abiding by serviceability guidelines and applying serviceability measurement to code during development.
New software releases are also scrutinized to minimize any unexpected changes in default behaviors. From release to release, behavior testing ensures that:
◉ Software doesn’t consume more memory or processing capacity than in a previous release unless a new feature requires it and is thoroughly documented to prepare the customer.
◉ New releases are backward compatible with supported hardware and software.
◉ Scale and performance do not degrade but stay consistent or improve.
Ultimately our goal in reimagining testing is to build a lasting bridge to quality to ensure our customers have trust in each and every release. While we have always performed intensive feature testing to validate functionality, integration, scalability, and usability, we are emphasizing a significant focus on solution level testing to ensure high levels of performance, interoperability, reliability, security, and conformance. Combined, these layers of testing will provide greater assurance that releases will perform as expected in a multitude of customer environments. We are building this bridge to quality with a unified development infrastructure for testing.
Unified Development Infrastructure Increases Automation and Consistency
Software in the process of being coded is often tested in virtual testbeds that can be quickly modified. This usually works fine for unit and integration testing. However, the further along the development cycle, the more complex the testing and interactions with the environment. Virtualized testing may not uncover all the issues that will be discovered in real-world configurations.
To address this gap, we are building flexible testbeds based on real hardware—routers, switches, servers, access points and software—that mimic real network deployments and operations. Since testbeds are based on a common infrastructure and environment, they enable reuse, code sharing, and complimentary software testing. Unifying topologies and infrastructure in development and testing improves efficiency by uncovering issues earlier in the cycle.
Transformation of Software Testing Benefits Developers and Customers
Reimagining and transforming the development testing cycle is paying off at Cisco in multiple ways. Internally, new tools for automating testing processes are making work more efficient and more engaging for developers at every stage of the software cycle. As we involve customer teams earlier in the development cycles, they are regaining trust in software release readiness and are willing to deploy new solutions sooner after release with more confidence.
Thursday, 4 June 2020
Umbrella with SecureX built-in: Coordinated Protection
An attack typically includes at least some of the following steps:
◉ reconnaissance activities to find attractive targets
◉ scanning for weaknesses that present a good entry point
◉ stealing credentials
◉ gaining access and privileges within the environment
◉ accessing and exfiltrating data
◉ hiding past actions and ongoing presence
This whole process is sometime called the “attack lifecycle” or “kill chain” and a successful attack requires a coordinated effort throughout the process. The steps above involve many different elements across the IT infrastructure including email, networks, authentication, endpoints, SaaS instances, multiple databases and applications. The attacker has the ability to plan in advance and use multiple tactics along the way to get to the next step.
Security teams have been busy over the past couple of decades as well. They have been building a robust security practice consisting of tools and processes to track activities, provide alerts and help with the investigation of incidents. This environment was built over time and new tools were added as different attack methods were developed. However, at the same time, the number of users, applications, infrastructure types, and devices has increased in quantity and diversity. Networks have become decentralized as more applications and data have moved to the cloud. In most instances, the security environment now includes over 25 separate tools spanning on-prem and cloud deployments. Under these conditions, it’s difficult to coordinate all of the activities necessary to block threats and quickly identify and stop active attacks.
As a consequence, organizations are struggling to get the visibility they need across their IT environment and to maintain their expected level of effectiveness. They are spending too much time integrating separate products and trying to share data and not enough time quickly responding to business, infrastructure, and attacker changes. The time has come for a more coordinated security approach that reduces the number of separate security tools and simplifies the process of protecting a modern IT environment.
Cisco Umbrella with SecureX can make your security processes more efficient by blocking more threats early in the attack process and simplifying the investigation and remediation steps. Umbrella handles over 200 billion internet requests per day and uses fine-tuned models to detect and block millions of threats. This “first-layer” of defense is critical because it minimizes the volume of malicious activity that makes its way deeper into your environment. By doing this, Umbrella reduces the stress on your downstream security tools and your scarce security talent. Umbrella includes DNS Security, a secure web gateway, cloud-delivered firewall, and cloud access security broker (CASB) functionality. But no one solution is going to stop all threats or provide the quickly adapting environment described above. You need to aggregate data from multiple security resources to get a coordinated view of what’s going on in your environment but can’t sink all your operating expenses into simply establishing and maintaining the integrations themselves.
That’s where Cisco SecureX comes in. Cisco SecureX connects the breadth of Cisco’s integrated security portfolio – including Umbrella– and your other security tools for a consistent experience that unifies visibility, enables automation, and strengthens your security across network, endpoints, cloud, and applications. Let’s explore some of the capabilities of SecureX, the Cisco security platform and discuss what they mean in the context of strengthening breach defense.
◉ Visibility: Our SecureX platform provides visibility with one consolidated view of your entire security environment. The SecureX dashboard can be customized to view operational metrics alongside your threat activity feed and the latest threat intelligence. This allows you to save time that was otherwise spent switching consoles. With the Secure threat response feature, you can accelerate threat investigation and take corrective action in under two clicks.
◉ Automation: You can increase the efficiency and precision of your existing security workflows via automation to advance your security maturity and stay ahead of an ever-changing threat landscape. SecureX pre-built, customizable playbooks enable you to automate workflows for phishing and threat hunting use cases. SecureX automation allows you to build your own workflows including collaboration and approval workflow elements to more effectively operate as a team. It enables your teams to share context between SecOps, ITOps, and NetOps to harmonize security policies and drive stronger outcomes.
◉ Integration: With SecureX, you can advance your security maturity by connecting your existing security infrastructure via out-of-the-box interoperability with third party solutions. In addition to the solution-level integrations we’ve already made available; new, broad, platform-level integrations have also been and continue to be developed. In short, you’re getting more functionality out of the box so that you can multiply your use cases and realize stronger outcomes.
The SecureX platform is included with Cisco security solutions to advance the value of your investment. It connects Cisco’s integrated security portfolio, your other security tools and existing security infrastructure with out-of-the-box interoperability for a consistent experience that unifies visibility, enables automation, and strengthens your security across network, endpoints, cloud, and applications.
Friday, 30 August 2019
Secure and Compliant Collaboration with Webex Teams
Easy, Secure Collaboration
In today’s modern and digital workplaces, teamwork transcends organizational and functional boundaries. Effective, secure, and compliant collaboration with your stakeholders, partners and customers is paramount to improving productivity.
Compliance, administration security controls and policies vary greatly across organizations and industry verticals. For any modern collaboration platform, it’s critical to have the flexibility to facilitate communications with external participants outside of the user’s organization – coupled with security controls that minimize friction for users. Webex Teams has a rich set of features spanning compliance, administrative controls and visibility – giving you a secure collaboration experience.
Webex Teams is the easiest messaging platform to set up for cross company collaboration
By default, Webex Teams is an open platform allowing users to communicate with others both inside and outside the organization – while still maintaining end to end encryption and control.
Compliance
Organizations need to comply with internal and external rules and regulations. Companies in regulated industries have to meet regulatory mandates in addition to their own compliance and data loss prevention policies. Cisco Webex Teams allows organizations to ensure compliance around data loss prevention through integration with leading CASB solutions like Cisco Cloudlock. These integrations allow visibility into all user generated content with immediate detection and remediation of user actions and posts that violate your compliance policies.
In addition, Cisco Webex Teams also supports “legal hold” to help organizations with data retention requirements to support legal investigations for compliance. During a litigation proceeding, organizations may be required to preserve data for a period that may be longer than their normal retention policy. In this case, legal hold can be enabled to ensure that relevant information is not purged, but instead retained until the litigation or investigation is complete.
Control
Under certain circumstances and regulatory environments, it may be necessary to block communication with external users who belong to a different organization. Administrators can enforce this policy and block external communications easily with native controls built in Webex Teams. When configured appropriately, users in the organization will no longer be able to message users outside their organization. We are enhancing this capability to allow limited communication to users only in approved domains via a Whitelist created and maintained by admins.