Automated Response updates
Release 7.3, introduces automated response capabilities to Stealthwatch, giving you new methods to share and respond to alarms through improvements to the Response Management module, and through SecureX threat response integration enhancements.
New methods for sharing and responding to alarms
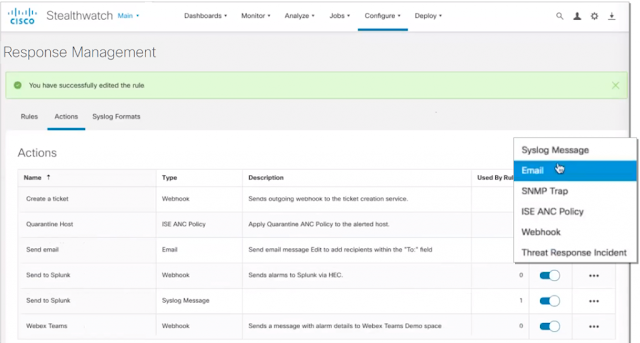
Stealthwatch’s Response Management module has been moved to the web-based UI and modernized to facilitate data-sharing with 3rd party event gathering and ticketing systems. Streamline remediation operations and accelerate containment through numerous new ways to share and respond to alarms through a range of customizable action and rule options. New response actions include:
◉ Webhooks to enhance data-sharing with third-party tools that will provide unparalleled response management flexibility and save time
◉ The ability to specify which malware detections to send to SecureX threat response as well as associated response actions to accelerate incident investigation and remediation efforts
◉ The ability to automate limiting a compromised device’s network access when a detection occurs through customizable quarantine policies that leverage Cisco’s Identity Services Engine (ISE) and Adaptive Network Control (ANC)
Figure 1. Modernized Response Management module with new response action options
SecureX threat response integration enhancements
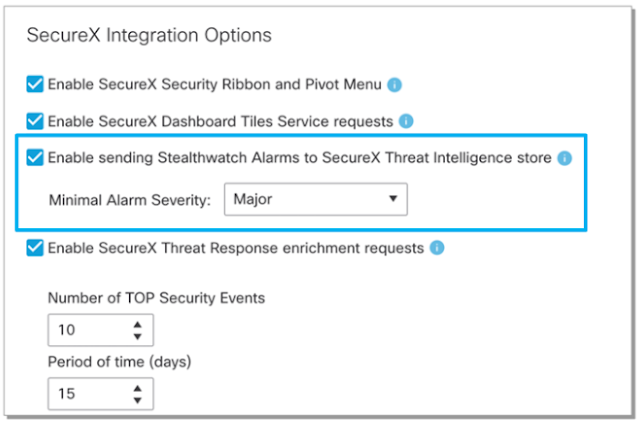
Get granular and be specific with flexible rule configurations that provide the ability to:
◉ Define which alarms from Stealthwatch are shared with SecureX threat response
◉ Base shared alarms off multiple parameters, such as alarm severity, alarm type, and host group
◉ Share alarms from mission critical services with the ability to define incident confidence levels, how target objects are formed, and rule conditions based off targets created for internal or external hosts
Figure 2. Customize which alarms are sent to SecureX threat response by severity
SecureX platform integration enhancements
Cisco’s SecureX platform unifies visibility, centralizes alerts, and enables automation across your entire security infrastructure on a single dashboard. Maximize operational efficiency, eliminate repetitive tasks, simplify business processes, and reduce human errors by:
1. Automating responses with pre-built workflows through SecureX’s orchestration capabilities
2. Creating playbooks with all your integrated security tools through SecureX’s intuitive interface
Figure 3. SecureX’s pre-built workflows and customizable playbooks
Enhanced security analytics
As threats continue to evolve, so do the analytical capabilities of Stealthwatch to deliver fast and high-fidelity threat detections. The cloud-based machine learning engine (Cognitive Intelligence) has been updated to include:
◉ New confirmed detections
◉ New machine learning classifiers for anomalous TLS fingerprint, URL superforest, and content spoofing detections
◉ Smart alert fusion in the new user interface (currently available in beta)
◉ New Stealthwatch use cases including Remote Access Trojan and Emotet malware detections
Figure 4. An example of the new content spoofing detector classifier in action.
Figure 5. Stealthwatch’s new GUI with smart alert fusion.
Easier management
Web UI improvements
Don’t let the setup process slow you down! Optimize installation with web UI enhancements that reduce deployment time and support full configuration of (both?) the appliance and vital services before the first reboot to save time.
Flow Sensor versatility and visibility enhancements
Get visibility into more places than ever before through ERSPAN (Encapsulated Remote Switch Port Analyzer) support now added to Flow Sensors. Benefits include:
◉ Visibility improvements through the ability to see within VMware’s NSX-T data centers to facilitate Flow Sensor deployment and network configuration
◉ Removed requirement of direct physical connectivity
◉ ACI traffic monitoring from Spine and Leaf nodes







0 comments:
Post a Comment