I have not been inside an office building for 12 months. A sentence I did not imagine writing anytime soon. Last February, everything changed. And when we pause to reflect, we have to consider that, of the many dramatic impacts to our lives, to society, and the world, in the realm of the professional, one of the most impactful changes has been the fact that many of us no longer commute to an office to perform our jobs.
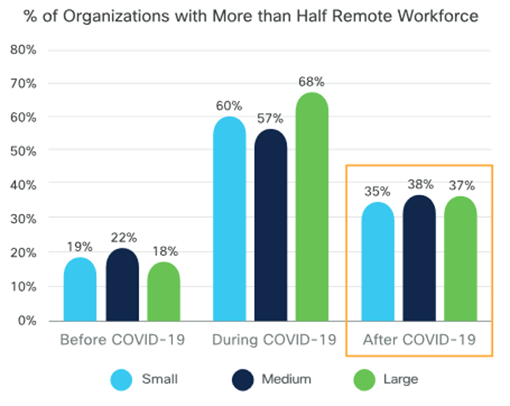
It’s been a year, give or take, since organizations had to provision extraordinary numbers of employees to work remotely as a result of the pandemic. Some companies may consider reopening traditional offices again, but the new work-from-home paradigm has many people contemplating a hybrid model (remote-first seems to be a popular option). In a recent Cisco study, not only were many people currently working remotely, but a substantial percentage of organizations also said that more than half of their employees would still work remotely once pandemic restrictions are lifted.
Source: Cisco Future of Secure Remote Work Report
The pandemic brings new security challenges
In security, we lament about how new initiatives are often instituted with threat protection as an afterthought. This is somewhat true as well of this rush to remote working, especially for companies that had not previously entertained the concept of remote work.
Security cannot remain a secondary thought, and it was quickly understood that remote working led to new security challenges. The concept of “Bring Your Own Device” was in full bloom – maybe “Use Your Own Device” is more accurate given that no one has been bringing anything anywhere.
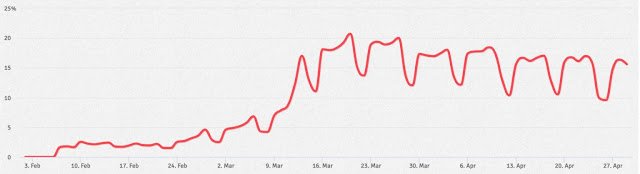
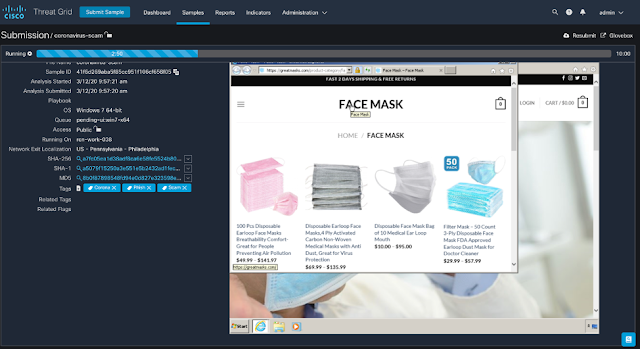
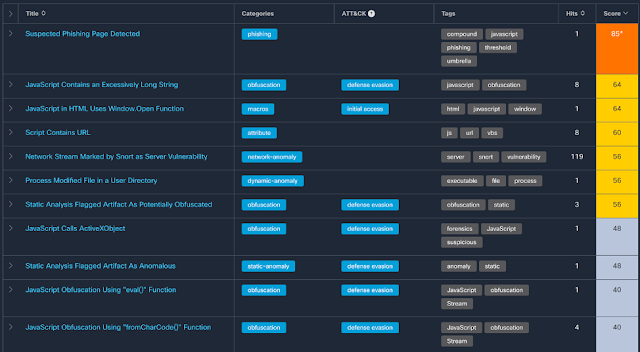
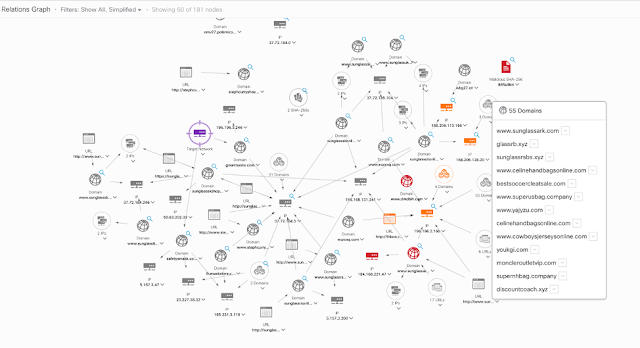
While we were working to secure this new environment, there was a dark side brewing; the world of cybercrime saw an opportunity to capitalize on the haste to preserve life, and we saw a rise in cyberattacks. In one analysis by Cisco Talos, pandemic-themed phishing scams emerged over the course of just a few months.
Percent of observed emails tracked by Talos containing pandemic themes
Source: Cisco, “Defending Against Critical Threats, A 12 Month Roundup”
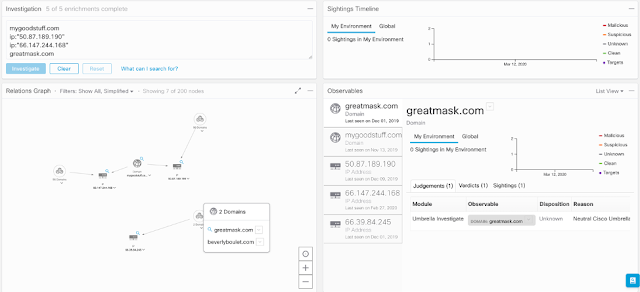
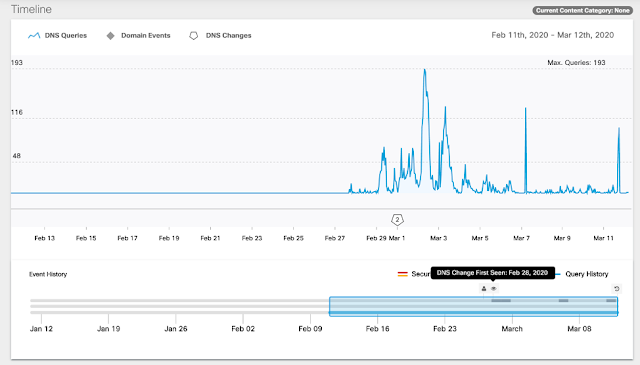
While the pandemic raged on, and cybercrime targeted our fears, there was no slowdown in the everyday threats that carried on with broader targets, as shown in this timeline from a recent Cisco report.
Source: Cisco, “Defending Against Critical Threats, A 12 Month Roundup”
Cisco technology for secure, remote work
At the start of the pandemic, Cisco quickly took action to help our customers securely provision for remote workers. Some of the offerings included extended free licenses and expanded usage counts for Cisco Webex, as well as several technologies for securing remote access and endpoints.
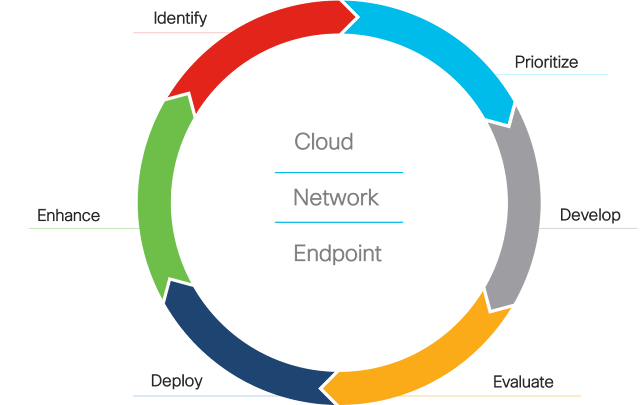
We all know that the pandemic will not last forever, but as mentioned previously, remote work is a viable way to run many businesses. What are some of the best ways to protect your company’s workforce? Cisco has developed the Secure Remote Worker solution, which incorporates many security components needed to embrace this new work setting.
With Cisco, New Castle Hotels and Resorts was able to secure its remote workforce within hours. According to Alan Zaccario, Vice President of IT and Cybersecurity for New Castle:
“Cisco security has definitely proven to be the correct choice, because Cisco enables a strong security posture for remote work. When the rapid move to remote work happened, my biggest concern was helping people configure local printers and scanners, not scrambling to secure the enterprise.”
One thing that we can all agree on is that sitting alone in your room, working remotely, can be a lonely undertaking. That’s why collaboration tools are key to not only keeping the business on track, but also keeping us connected. However, collaboration can sometimes add more complexity, and that is why we have enhanced our Cisco Secure Remote Worker offering by coupling security with collaboration tools that make remote work more secure.
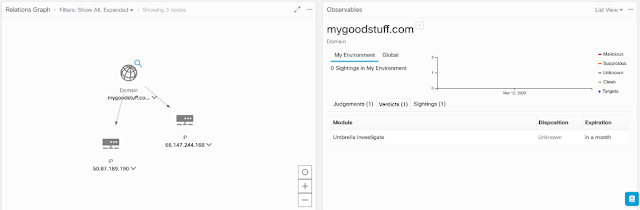
Finally, the Cisco SecureX platform brings all of our security technology (plus third-party technologies) together to protect users and devices wherever they are. SecureX is built into every Cisco product. It is a cloud-native platform that connects our integrated security portfolio and customers’ security infrastructure to provide simplicity, visibility, and efficiency.
SecureX delivers a unified view of customers’ environments, so they no longer have to jump between multiple dashboards to investigate and remediate threats. It also gives customers the ability to automate common workflows across security products from Cisco and third parties to handle tasks such as threat hunting and identifying device vulnerabilities.
“We really can’t afford a misfire with our security spend,” added Zaccario of New Castle. “We understand the Cisco security integrations, and how Cisco’s platform approach protects our investment.”
The tragedies of the pandemic have taught us many important lessons. From a technology perspective, as we all scrambled to create a fully remote workforce, it is nice to know that the capabilities to do so securely have kept pace with the need to protect the health of our most valuable assets, our co-workers.
Source: cisco.com