We’ve seen a sharp increase in the number of organizations growing their remote workforces over the last decade. In fact, at the start of 2020, the number of remote workers in the U.S. stood at 4.7 million, which represents 3.4% of the population.
The advent of cloud, multi-cloud, and hybrid cloud architectures has made it possible for businesses to rapidly adapt to changing workforces and working styles. However, these changes have also introduced new challenges in managing security operations.
The key reasons for this include:
◉ Workers are accessing organizations’ servers and applications remotely, which opens up new entry points for cyber attacks
◉ Employees are relying increasingly on cloud-hosted services to work and collaborate
◉ Remote workers are being targeted by more and more malware sites
◉ Employees fail to consistently practice good cyber hygiene
As the remote workforce grows and cyber threats stack up, its important organizations have the capability to manage risks and uncertainty to keep critical assets secure. Where risks are known, actions are clear. But with unknown risks, there needs to be a focus on disciplined research and investigation. This helps generate intelligence to develop detailed use cases, providing Security Operations (SecOps) teams with a guide to respond to threats.
By defining known and unknown risk scenarios in your security operations lifecycle, you can meet the demands of remote workers using cloud and network services, while ensuring you remain protected.
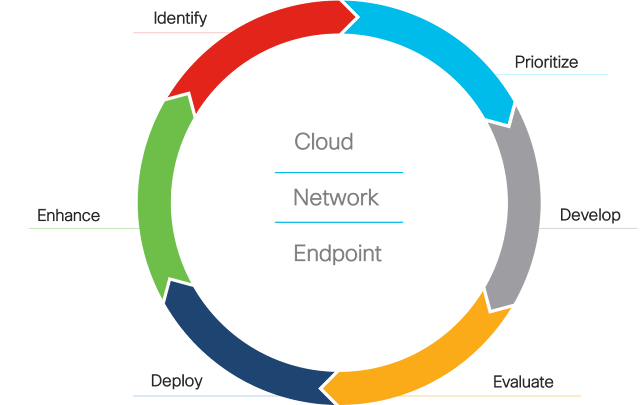
Let’s explore how to establish a six-phase threat detection and response methodology that addresses uncertainty.
Identify
Establishing a clear methodology for security operations teams to follow is a critical element of effective and efficient threat detection and response.
This methodology starts with identifying uses cases. Uses cases are the definition and analysis of an attack method. In addition to the type of attack, use cases include step-by-step detail on how an attack unfolds, e.g. exfiltration of data from an organization or compromised privileged login, as well as possible control points for use in mitigation. Establishing a methodology that SecOps then leverages to identify and create new use cases is crucial to ensuring the organization maintains a strong security posture.
Building a disciplined approach to use case identification and analysis is the foundation of your detection and response process; providing insights on use case relevancy and organizational asset protection effectiveness.
Without these insights you will lack the visibility needed to truly maximize the value of follow on process steps such as developing, evaluating, and enhancing.
Organizations that follow a defined methodology to discover, collect, refine, validate, and apply changes to use cases address a critical weakness in “set it and forget it” programs. These programs assume the security policies and use cases developed at the time of implementing advanced operations tools remain static – an assumption that can create broad gaps in your threat visibility.
Prioritize
Prioritizing use case development is very important given it directly impacts how fast your organization is ready to respond to specific threats. It is often debated which use cases to do first, which are most important, and how to assess the lifecycle for additional use cases. While prioritization could be based on importance, you’re likely to be more effective balancing importance with feasibility (e.g. how complex and risky is the use case to implement) and the speed at which a particular business operates.
Establishing a model to prioritize use cases will help you manage this balance. One approach is to create relative categories. For example:
◉ ‘Control’ based use cases relate to a regulatory objective, such as Payment Card Industry Data Security Standard (PCI DSS)
◉ ‘Threat’ based use cases leverage threat intelligence related to Tactics, Techniques, and Procedures (TTPs)
◉ ‘Data or Asset’ based use cases relate to specific datasets or assets that represent additional risk to the business
Reviewing new use cases in each of these categories with a balance between importance and feasibility provides a great strategy for new use case prioritization.
The advent of cloud, multi-cloud, and hybrid cloud architectures has made it possible for businesses to rapidly adapt to changing workforces and working styles. However, these changes have also introduced new challenges in managing security operations.
The key reasons for this include:
◉ Workers are accessing organizations’ servers and applications remotely, which opens up new entry points for cyber attacks
◉ Employees are relying increasingly on cloud-hosted services to work and collaborate
◉ Remote workers are being targeted by more and more malware sites
◉ Employees fail to consistently practice good cyber hygiene
As the remote workforce grows and cyber threats stack up, its important organizations have the capability to manage risks and uncertainty to keep critical assets secure. Where risks are known, actions are clear. But with unknown risks, there needs to be a focus on disciplined research and investigation. This helps generate intelligence to develop detailed use cases, providing Security Operations (SecOps) teams with a guide to respond to threats.
By defining known and unknown risk scenarios in your security operations lifecycle, you can meet the demands of remote workers using cloud and network services, while ensuring you remain protected.
Let’s explore how to establish a six-phase threat detection and response methodology that addresses uncertainty.
Managing uncertainty with disciplined security operations
Establishing a clear methodology for security operations teams to follow is a critical element of effective and efficient threat detection and response.
This methodology starts with identifying uses cases. Uses cases are the definition and analysis of an attack method. In addition to the type of attack, use cases include step-by-step detail on how an attack unfolds, e.g. exfiltration of data from an organization or compromised privileged login, as well as possible control points for use in mitigation. Establishing a methodology that SecOps then leverages to identify and create new use cases is crucial to ensuring the organization maintains a strong security posture.
Building a disciplined approach to use case identification and analysis is the foundation of your detection and response process; providing insights on use case relevancy and organizational asset protection effectiveness.
Without these insights you will lack the visibility needed to truly maximize the value of follow on process steps such as developing, evaluating, and enhancing.
Organizations that follow a defined methodology to discover, collect, refine, validate, and apply changes to use cases address a critical weakness in “set it and forget it” programs. These programs assume the security policies and use cases developed at the time of implementing advanced operations tools remain static – an assumption that can create broad gaps in your threat visibility.
Prioritize
Prioritizing use case development is very important given it directly impacts how fast your organization is ready to respond to specific threats. It is often debated which use cases to do first, which are most important, and how to assess the lifecycle for additional use cases. While prioritization could be based on importance, you’re likely to be more effective balancing importance with feasibility (e.g. how complex and risky is the use case to implement) and the speed at which a particular business operates.
Establishing a model to prioritize use cases will help you manage this balance. One approach is to create relative categories. For example:
◉ ‘Control’ based use cases relate to a regulatory objective, such as Payment Card Industry Data Security Standard (PCI DSS)
◉ ‘Threat’ based use cases leverage threat intelligence related to Tactics, Techniques, and Procedures (TTPs)
◉ ‘Data or Asset’ based use cases relate to specific datasets or assets that represent additional risk to the business
Reviewing new use cases in each of these categories with a balance between importance and feasibility provides a great strategy for new use case prioritization.




0 comments:
Post a Comment