Thursday, 1 December 2022
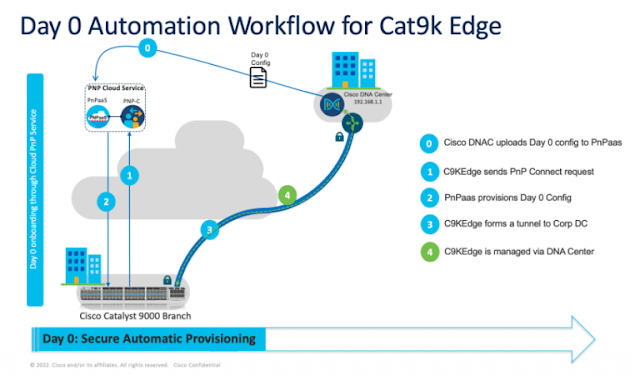
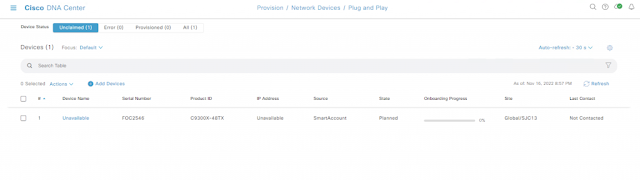
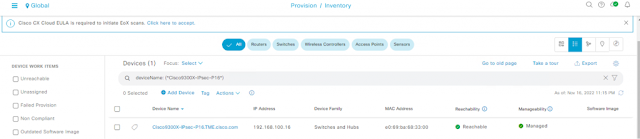
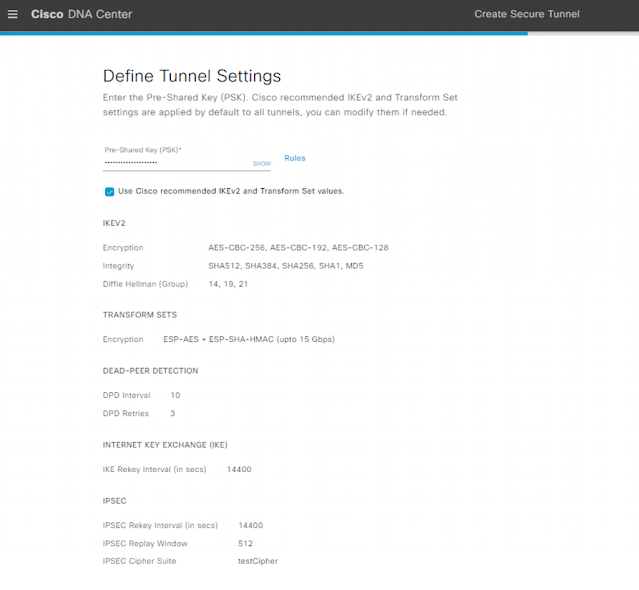
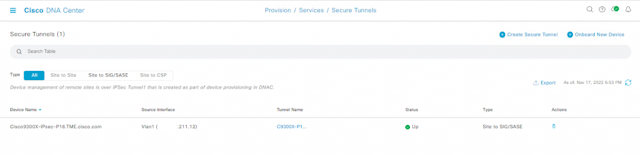
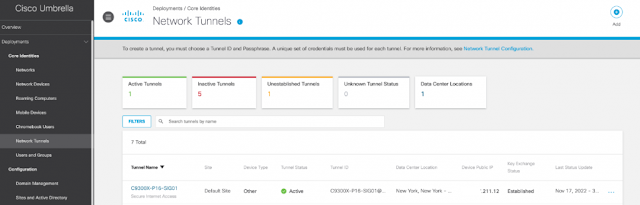
Cisco Catalyst 9300X – IPsec And Cisco Umbrella
Sunday, 13 March 2022
Introducing the new ‘Defending Against Critical Threats’ report
Today, we’re pleased to launch our annual Defending Against Critical Threats report. Inside, we cover the most significant vulnerabilities and incidents of 2021, with expert analysis, insights and predictions from our security and threat intelligence teams across Cisco Talos, Duo Security, Kenna Security, and Cisco Umbrella.
It’s clear that 2021 – and, indeed, the start of 2022 – has been very challenging for security defenders. To bring our Defending Against Critical Threats: Analyzing Key Incident Trends report to life, I sat down with six expert threat hunters and analysts from these teams, and asked them to tell me about their findings on one specific cybersecurity threat, or incident, from the past 12 months. Each expert chose to discuss a topic which tells us a lot about the current priorities of threat actors – below you’ll find a brief summary on some of the key themes we covered.
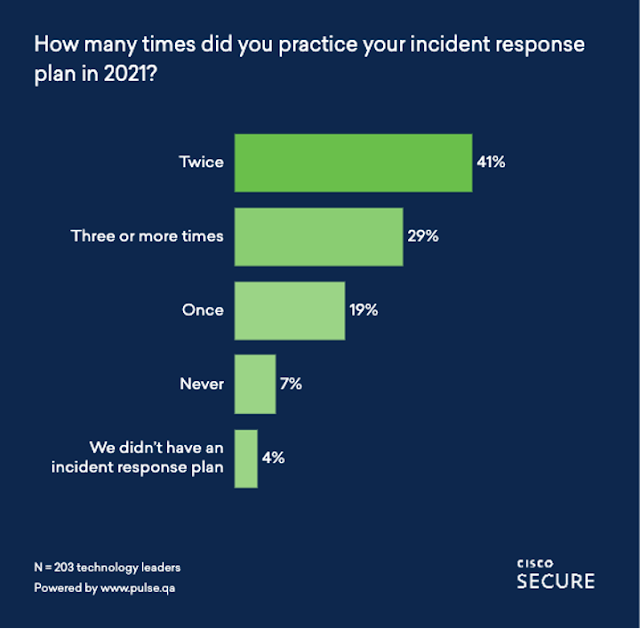
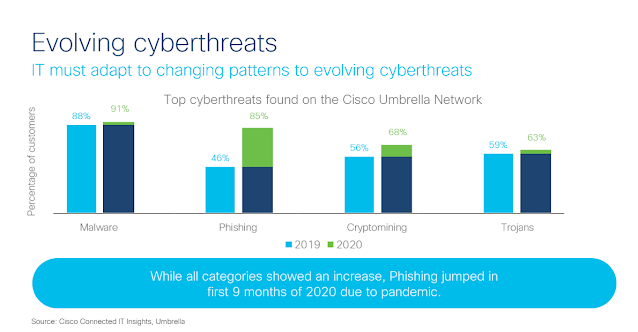
We also conducted a survey among 190+ security and technology leaders via PulseQA to gauge their perspectives on the current threat landscape. We found that 66% of respondents felt that the complexity and volume of cybersecurity attacks had escalated in 2021, whilst 36% felt that attacks had stayed consistent with the previous year.
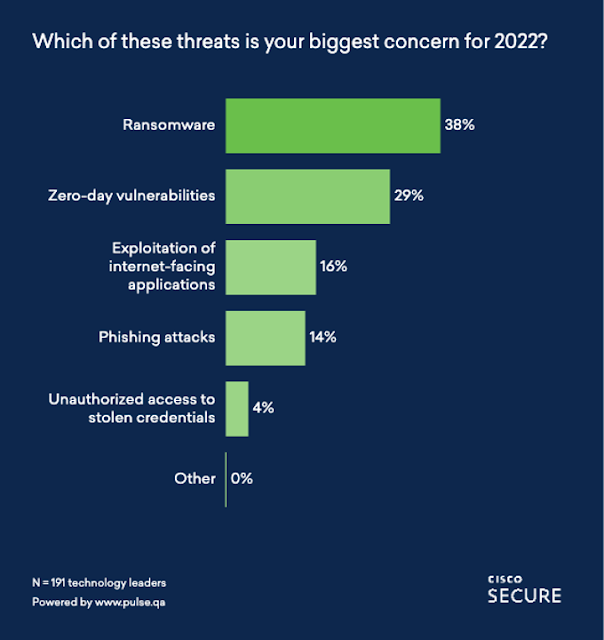
In the survey, we also asked about the top threat concerns security leaders had for 2022. Ransomware came in as the top concern, with 38% of respondents choosing that option. In the report, we discuss the evolution of ransomware and how it has reached a critical level for certain bad actors, provoking a more severe and structured governmental response. You’ll read about this in Matt Olney’s (Talos’ Director of Threat Intelligence and Interdiction) section about the Colonial Pipeline attack.
Here’s what we cover in the new Defending Against Critical Threats:
Tuesday, 21 September 2021
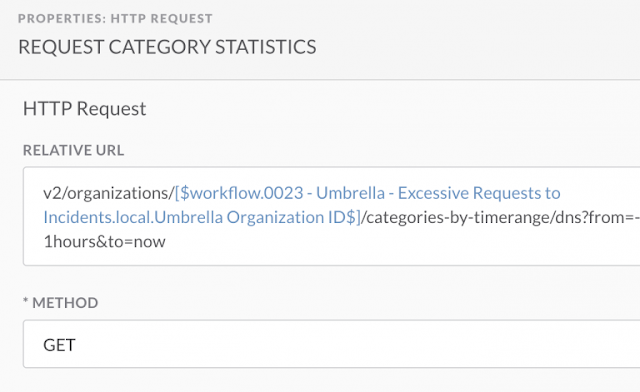
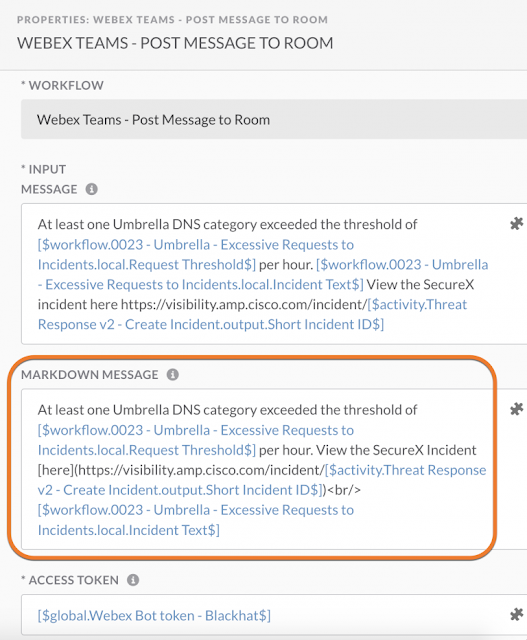
Building a Custom SecureX Orchestration Workflow for Umbrella
Improving efficiency for the Cisco team in the Black Hat USA NOC
As a proud partner of the Black Hat USA NOC, Cisco deployed multiple technologies along with the other Black Hat NOC partners to build a stable and secure network for the conference. We used Cisco Secure Malware Analytics to analyze files and monitor any potential PII leaks. We also used Meraki SM to manage over 300 iPads used around the venue for registration, as well as sales lead generation. Last but not least, we used Umbrella to add DNS level visibility, threat intelligence and protection to the entire network.
Read More: 300-620: Implementing Cisco Application Centric Infrastructure (DCACI)
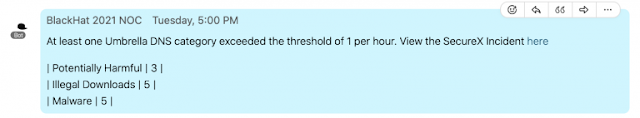
Lets go over an example scenario which many customers may find themselves in. While we were in the Black Hat USA NOC, we were constantly keeping our eyes on the Umbrella security activity report, in order to recognize, investigate and work with other teams to respond to the threats.
Thursday, 12 August 2021
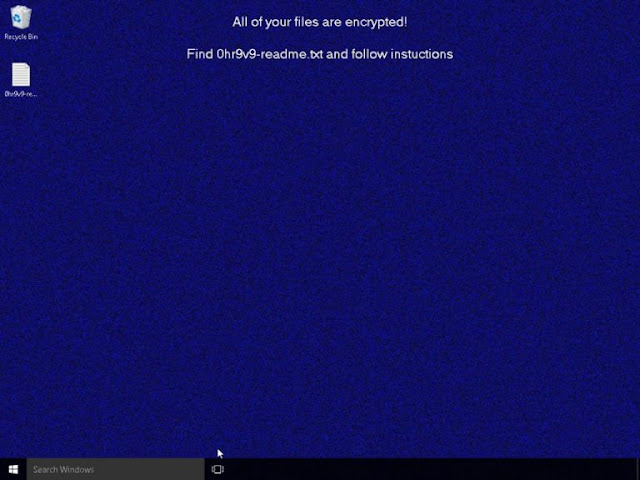
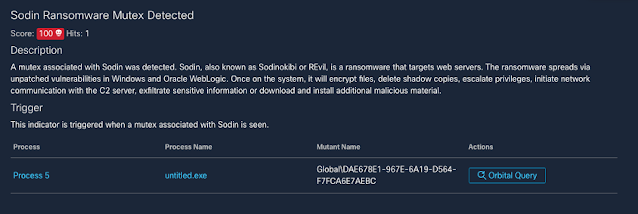
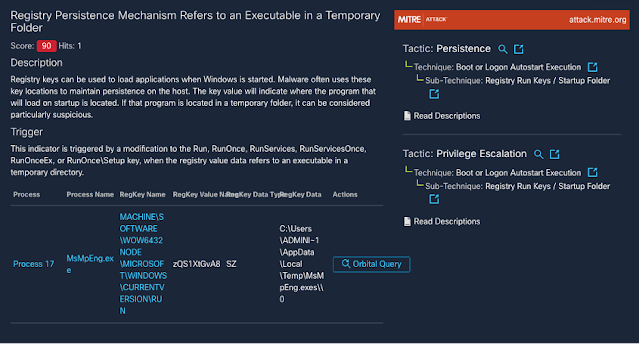
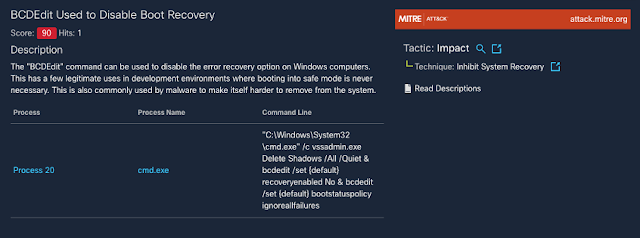
Threat Protection: The REvil Ransomware
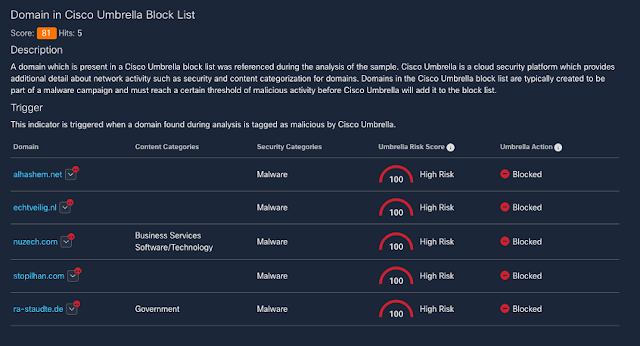
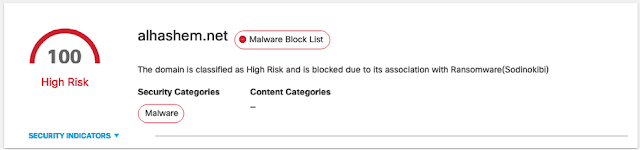
The REvil ransomware family has been in the news due to its involvement in high-profile incidents, such as the JBS cyberattack and the Kaseya supply chain attack. Yet this threat carries a much more storied history, with varying functionality from one campaign to the next.
The threat actors behind REvil attacks operate under a ransomware-as-a-service model. In this type of setup, affiliates work alongside the REvil developers, using a variety of methods to compromise networks and distribute the ransomware. These affiliates then split the ransom with the threat actors who develop REvil.
We looked at REvil, also known as Sodinokibi or Sodin, earlier in the year in a Threat Trends blog on DNS Security. In it we talked about how REvil/Sodinokibi compromised far more endpoints than Ryuk, but had far less DNS communication. However, when revisiting these metrics, we noticed that this changed in the beginning of 2021.
Wednesday, 9 June 2021
Under Pressure to Secure Your Enterprise? Predict More to Prevent More
Cybersecurity is a top priority for any organization conducting business over the Internet. Protecting your assets encompasses an ever-expanding digital landscape. Any data breach can have a devastating impact on the finances and brand equity of an organization. It’s why cybersecurity is treated as a business risk, rather than merely an IT issue. The importance of security is nothing new, but the global pandemic has made it even more critical.
Rise in Remote Access Authentication
Many of the new security challenges stem from the rapid increase in remote work that occurred almost overnight last year with the global rollout of stay-at-home orders. According to data from Cisco DUO, more organizations across all industries have enabled their employees to work from home, and there’s every indication this could continue for an extended time. Between February and April of 2020, we saw a 60% increase in remote access authentication — a percentage that has held remarkably steady ever since.
For IT Ops, a key challenge was ensuring their business employees could securely access the tools and resources they needed to do their jobs, seamlessly and with no additional friction. At the same time, organizations have had to protect critical information and minimize risk, all while accommodating myriad types of users and devices using unsecured networks. In order to accomplish the above, having visibility and insights into remote work patterns is a must, allowing SecOps and NetOps teams to authenticate and secure enterprise traffic through zero-trust solutions and multi-factor authentication.
Identifying Cyberthreat Patterns
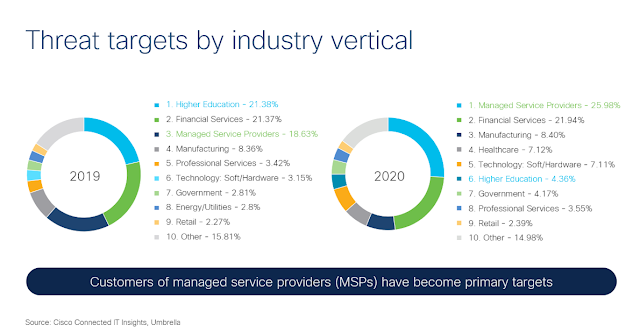
Threat Targets by Industry
Thursday, 25 March 2021
Threat Trends: DNS Security, Part 2
Part 2: Industry trends
In our Threat Trends blog series, we attempt to provide insight into the prevalent trends on the threat landscape. Our goal in giving you the latest info on these trends is that you’ll be better prepared to allocate security resources to where they’re needed most.
Knowing the larger trends can help in this pursuit, particularly when it comes to the most common threat types. This is what we covered in part one of this Threat Trends release on DNS Security, using data from Cisco Umbrella, our cloud-native security service.
However, different industries sometimes have different levels of exposure to certain threat types. For example, those in the financial services industry may see more activity around information stealers; others in manufacturing may be more likely to encounter ransomware.
This is what we’re going to cover in part two. We’ll focus on specific industries, looking at two things: the top threat categories they face, and the categories that they’re more likely to encounter when compared to other industries. In this way, you’ll be better armed knowing which threats you’re more likely to encounter within your industry.
As in part one, we’ll be looking at data covering the calendar year of 2020. This time we’ll be comparing yearly totals of DNS traffic to malicious sites, by industry. While we do this, we’ll occasionally drill down to the monthly level, or look at endpoint data, to highlight items of interest. All of this gives us a window into the categories of threats that generate the most traffic for various organizations.
So, without further ado, and in no particular order, here are the industry trends:
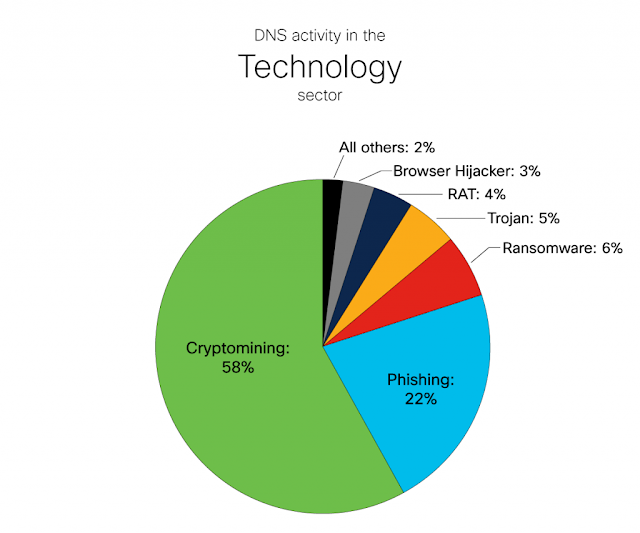
Technology
The vast majority of DNS traffic in the Technology sector—the sector involving the development and/or distribution of technological goods and services—can be attributed to two categories: cryptomining and phishing. These two categories alone accounted for 70 percent of the traffic for organizations in this sector.