Cybersecurity is a top priority for any organization conducting business over the Internet. Protecting your assets encompasses an ever-expanding digital landscape. Any data breach can have a devastating impact on the finances and brand equity of an organization. It’s why cybersecurity is treated as a business risk, rather than merely an IT issue. The importance of security is nothing new, but the global pandemic has made it even more critical.
Rise in Remote Access Authentication
Many of the new security challenges stem from the rapid increase in remote work that occurred almost overnight last year with the global rollout of stay-at-home orders. According to data from Cisco DUO, more organizations across all industries have enabled their employees to work from home, and there’s every indication this could continue for an extended time. Between February and April of 2020, we saw a 60% increase in remote access authentication — a percentage that has held remarkably steady ever since.
For IT Ops, a key challenge was ensuring their business employees could securely access the tools and resources they needed to do their jobs, seamlessly and with no additional friction. At the same time, organizations have had to protect critical information and minimize risk, all while accommodating myriad types of users and devices using unsecured networks. In order to accomplish the above, having visibility and insights into remote work patterns is a must, allowing SecOps and NetOps teams to authenticate and secure enterprise traffic through zero-trust solutions and multi-factor authentication.
Identifying Cyberthreat Patterns
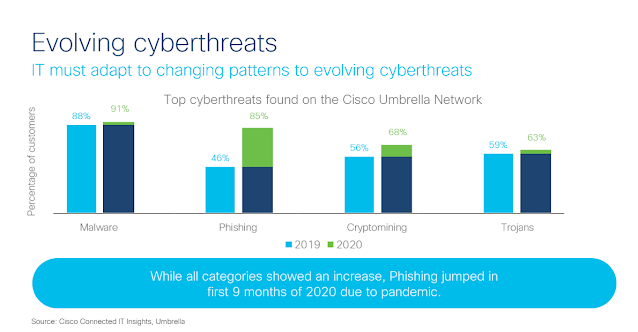
In addition to the expansion of the attack surface due to the shift to remote work, cyber-criminals evolved their attacks to feed on people’s fears around the pandemic. DNS traffic analysis by Cisco Umbrella revealed some startling findings for the first nine months of 2020. For example, among our Umbrella DNS customers:
◉ 91% saw a domain linked to malware
◉ 68% saw a domain linked to cryptomining
◉ 85% saw a domain linked to phishing
◉ 63% saw a domain linked to trojans
In fact, since 2019, trojans and phishing have traded spots in threat ranking. In 2019, trojans were the number two threat at 59%, while phishing was number four with 46% impacted. Over the past year, phishing has risen by nearly 40% in large part due to malicious actors preying on people’s fears about the virus.
If IT teams are to scale and stay ahead of the bad actors in this evolving landscape of cyberthreats, they must be able to proactively monitor and identify malicious traffic and its patterns. It is vastly better to predict and prevent cyberattacks than to try to undo the damage caused by data breaches after the fact.
Threat Targets by Industry
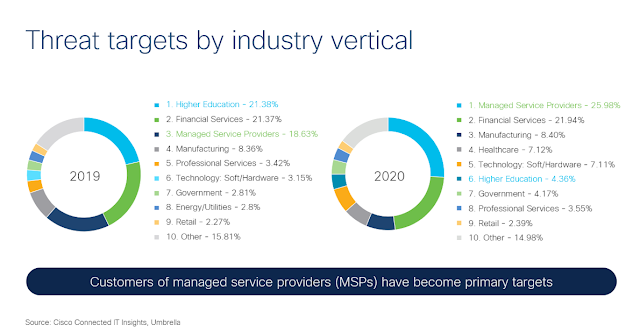
Shifts in the distribution of threat traffic across different business markets since 2019 offer further insight into how to secure your enterprise. In particular, managed service providers (MSPs) have now surpassed financial services as the most impacted markets. In fact, U.S. government agencies have issued recent warnings about the heightened risk of attacks by state actors on MSPs.
Why this jump in MSP threat traffic? MSPs are attractive targets because, unless an MSP has effectively secured its own environment, it is vulnerable to attack by malicious actors who can then hijack remote monitoring management to go after the MSP’s clients. These customers are then at higher risk than the MSP itself. (By contrast, higher education traffic has dropped considerably in the ranking of impacted markets over the past year — from the top spot to the number six spot — most likely due to students being unable to attend classes in person.)
The rise in malware using sophisticated hiding and evasion techniques has made cyber defense teams’ jobs that much harder. In order to secure your data and your enterprise, manual monitoring and intervention is no longer a viable solution. Today’s cyber defenders must have visibility across applications, networks, and devices, along with the ability to leverage machine speed and predictive intelligence to deliver scalable, adaptable protection.
Source: cisco.com







0 comments:
Post a Comment