Saturday, 30 September 2023
When it Comes to Compliance Requirements – Topology Matters!
Saturday, 29 July 2023
Provide State-of-the-Art Endpoint Protection as a Managed Service
- Next-gen antivirus protection
- Continuous behaviour monitoring of endpoints (system-level)
- Dynamic file analysis
- Endpoint isolation
- Orbital advanced search
- Threat grid cloud
- Threat hunting mapped to the MITRE ATT&CK framework
Integration with other security technologies and automation
Move from EDR to XDR for increased visibility and improved endpoint protection
Thursday, 22 June 2023
The Value of SOC2 and ISO27001 in Enhancing Customer Trust
Saturday, 10 December 2022
Preparing for 2023 and what lies in store for Endpoint Security
Sunday, 31 July 2022
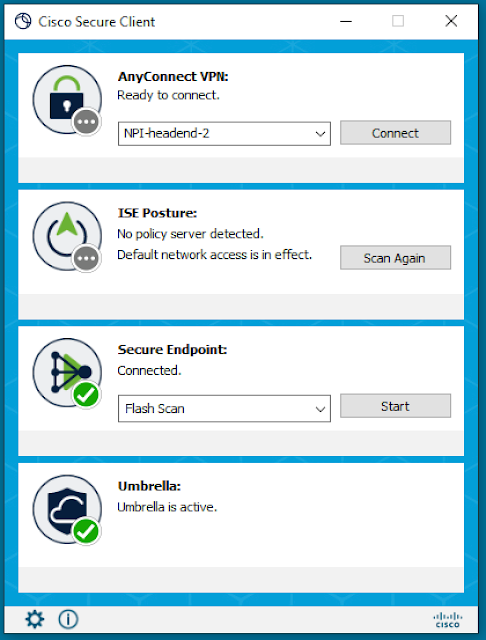
More than a VPN: Announcing Cisco Secure Client (formerly AnyConnect)
We’re excited to announce Cisco Secure Client, formerly AnyConnect, as the new version of one of the most widely deployed security agents. As the unified security agent for Cisco Secure, it addresses common operational use cases applicable to Cisco Secure endpoint agents. Those who install Secure Client’s next-generation software will benefit from a shared user interface for tighter and simplified management of Cisco agents for endpoint security.
Go Beyond Traditional Secure Access
Tuesday, 12 April 2022
Announcing Risk-Based Endpoint Security with Cisco Secure Endpoint and Kenna Security
With a tidal wave of vulnerabilities out there and brand-new vulnerabilities coming out daily, security teams have a lot to handle. Addressing every single vulnerability is nearly impossible and prioritizing them is no easy task either since it’s difficult to effectively focus on the small number of vulnerabilities that matter most to your organization. Moreover, the shift to hybrid work makes it harder to assess and prioritize your vulnerabilities across your endpoints with traditional vulnerability scanners.
Kenna Security maps out the vulnerabilities in your environment and prioritizes the order in which you should address them based on a risk score. We’re excited to announce that after Cisco acquired Kenna Security last year, we have recently launched an integration between Kenna and Cisco Secure Endpoint to add valuable vulnerability context into the endpoint.
With this initial integration, Secure Endpoint customers can now perform risk-based endpoint security. It enables customers to prioritize endpoint protection and enhances threat investigation to accelerate incident response with three main use cases:
1. Scannerless vulnerability visibility: In a hybrid work environment, it’s increasingly difficult for traditional vulnerability scanners to account for all devices being used. Instead of relying on IP address scanning to identify vulnerabilities in an environment, you can now use the existing Secure Endpoint agent to get a complete picture of the vulnerabilities you need to triage.
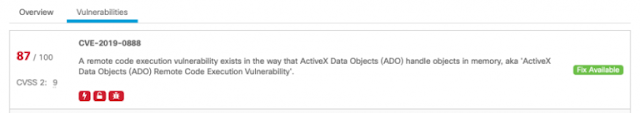
2. Risk-based vulnerability context: During incident response, customers now have an additional data point in the form of a Kenna risk score. For example, if a compromised endpoint has a risk score of 95+, there is a high likelihood that the attack vector relates to a vulnerability that Kenna has identified. This can dramatically speed up incident response by helping the responder focus on the right data.
3.Accurate, actionable risk scores: Organizations often struggle to prioritize the right vulnerabilities since most risk scores such as Common Vulnerability Scoring System (CVSS) are static and lack important context. In contrast, the Kenna Risk Score is dynamic with rich context since it uses advanced data science techniques such as predictive modeling and machine learning to consider real-world threats. This enables you to understand the actual level of risk in your environment and allows you effectively prioritize and remediate the most important vulnerabilities first.
How does the Kenna integration work?
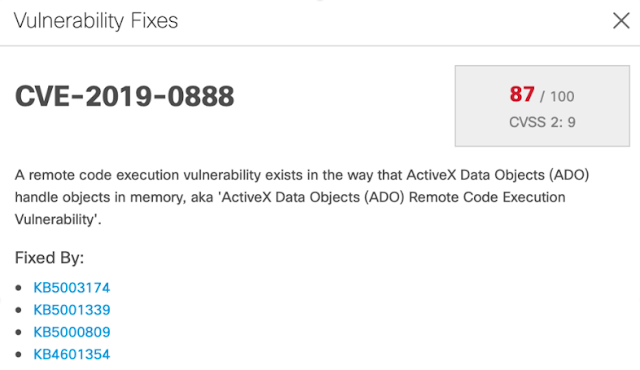
The Kenna integration brings Kenna Risk Scores directly into your Secure Endpoint console. As an example of this integration, the computer in the screenshot below (Figure 1) has been assigned a Kenna Risk Score of 100.
Who can access the Kenna integration?
Tuesday, 5 April 2022
Intelligent alert management
The challenge
In cyber security, we all know what alert fatigue is, and we know there is no silver bullet to get out of it. In our previous incarnation, our product was guilty as well. Who wants to go through 20,000 alerts one by one? And this was just from one product.
Building a detection engine
Alert Fusion
Threats
Assets
Reactive system
Wrap-up
Sunday, 13 March 2022
Introducing the new ‘Defending Against Critical Threats’ report
Today, we’re pleased to launch our annual Defending Against Critical Threats report. Inside, we cover the most significant vulnerabilities and incidents of 2021, with expert analysis, insights and predictions from our security and threat intelligence teams across Cisco Talos, Duo Security, Kenna Security, and Cisco Umbrella.
It’s clear that 2021 – and, indeed, the start of 2022 – has been very challenging for security defenders. To bring our Defending Against Critical Threats: Analyzing Key Incident Trends report to life, I sat down with six expert threat hunters and analysts from these teams, and asked them to tell me about their findings on one specific cybersecurity threat, or incident, from the past 12 months. Each expert chose to discuss a topic which tells us a lot about the current priorities of threat actors – below you’ll find a brief summary on some of the key themes we covered.
We also conducted a survey among 190+ security and technology leaders via PulseQA to gauge their perspectives on the current threat landscape. We found that 66% of respondents felt that the complexity and volume of cybersecurity attacks had escalated in 2021, whilst 36% felt that attacks had stayed consistent with the previous year.
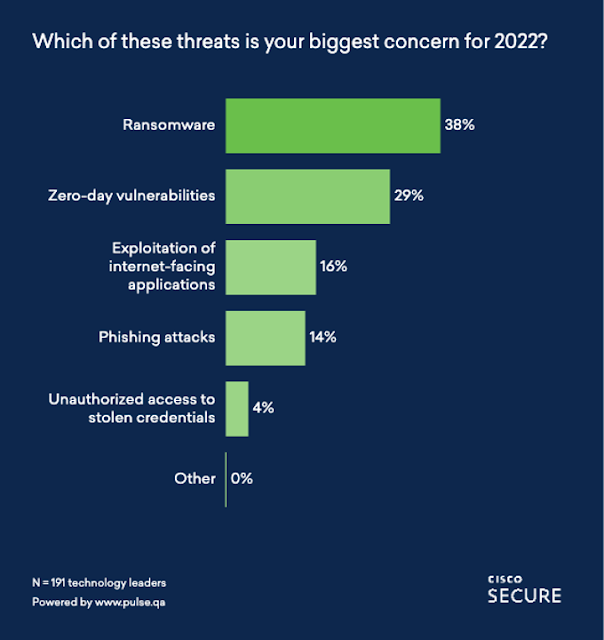
In the survey, we also asked about the top threat concerns security leaders had for 2022. Ransomware came in as the top concern, with 38% of respondents choosing that option. In the report, we discuss the evolution of ransomware and how it has reached a critical level for certain bad actors, provoking a more severe and structured governmental response. You’ll read about this in Matt Olney’s (Talos’ Director of Threat Intelligence and Interdiction) section about the Colonial Pipeline attack.
Here’s what we cover in the new Defending Against Critical Threats:
Saturday, 4 December 2021
Relevant and Extended Detection with SecureX
Al Huger spoke about Cisco’s vision of Extended Detection and Response (XDR); specifically covering the breadth of definitions in the industry and clarifying Cisco’s definition of XDR:
“A unified security incident detection and response platform that automatically collects and correlates data from multiple proprietary security components.”
He also detailed the way Cisco’s approach to XDR is founded upon our cloud-native platform SecureX. In this blog series I’m going to expand on that XDR definition and explore how extended detection and other XDR outcomes can be achieved today leveraging the SecureX platform and integrated products.
The phrase “Extended Detection” conjures up an image of multiple data elements, perhaps many of them otherwise considered low fidelity signals, all merged into a single, high-fidelity alert. This extended detection is so wonderful that an analyst can immediately access the business relevance, the risk, the root cause and the appropriate response actions; perhaps this alert is so explainable that all this can be done automatically at machine-scale. Before we get to this state of nirvana, let’s take a step back and look at the phrase “Extended Detection” and that end state. It all begins with a detection.
But is it important?
That question – “but is it important” – stems from a more fundamental one: what does this alert mean to me? In our security operations centres today, we can have a number of products that generate detections, observations, sightings, etc. that feed into our operational processes. On their own these alerts indicate something potentially of interest in the space of that security tool. For example, an Endpoint Detection and Response product such as Cisco Secure Endpoint makes the observation of a malicious file seen on a host or a Network Detection and Response product such as Cisco Secure Network Analytics makes an observation of a host downloading a suspiciously high amount of data. These alerts tell us that something happened but not what it means in the context of the environment that it fired —your environment — creating that original question: “but is it important?”
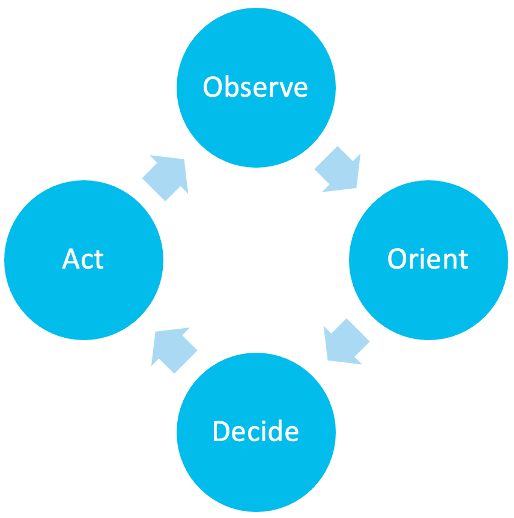
In my experience “importance” is in the eye of the beholder. What can be considered a false positive in one environment is that high-fidelity, actionable pure-gold event in another: with the only difference being the environment the alert fired in. If we revisit the notion of the OODA (Observe, Orient, Decide, Act) loop for a moment, this is the second step of Orientation, bringing into account the environment variables that when held against the initial observation accelerate the decision and action phases.
Risk-Based Extended Detection with SecureX
Thursday, 12 August 2021
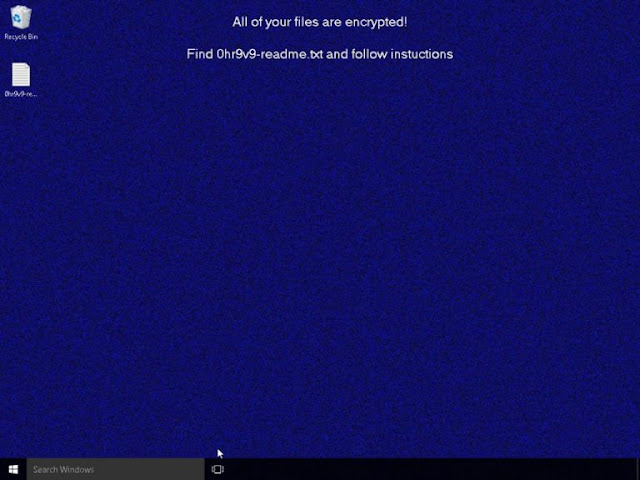
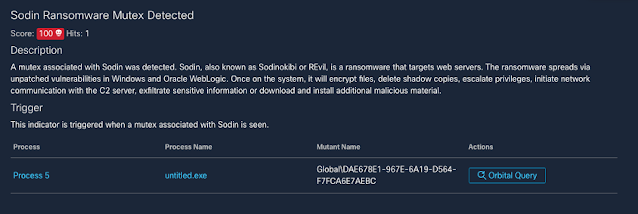
Threat Protection: The REvil Ransomware
The REvil ransomware family has been in the news due to its involvement in high-profile incidents, such as the JBS cyberattack and the Kaseya supply chain attack. Yet this threat carries a much more storied history, with varying functionality from one campaign to the next.
The threat actors behind REvil attacks operate under a ransomware-as-a-service model. In this type of setup, affiliates work alongside the REvil developers, using a variety of methods to compromise networks and distribute the ransomware. These affiliates then split the ransom with the threat actors who develop REvil.
We looked at REvil, also known as Sodinokibi or Sodin, earlier in the year in a Threat Trends blog on DNS Security. In it we talked about how REvil/Sodinokibi compromised far more endpoints than Ryuk, but had far less DNS communication. However, when revisiting these metrics, we noticed that this changed in the beginning of 2021.