In this blog, you will learn how to configure IPsec and Cisco Umbrella tunnels on a Catalyst 9300X by onboarding it with the Plug and Play (PNP) Cloud Service and Cisco DNA Center.
This capability is supported with Cisco DNA Center 2.3.4. The switch will need IOS-XE 17.8.1 for onboarding and an Advantage license. The IPsec feature on the switch requires an HSEC K9. Please refer to Part 1 of this series to understand at least three use cases that can leverage IPsec on a Catalyst switch.
PnP Cloud Service (Onboarding C9300X with IPsec)
The onboarding section below assumes that the switch only has direct internet and requires a secure connection back to Cisco DNA Center for management. Traditionally a switch has access to a local PnP Server but with this lean branch deployment with just the 9300X connectivity back to a PnP server is highly unlikely.
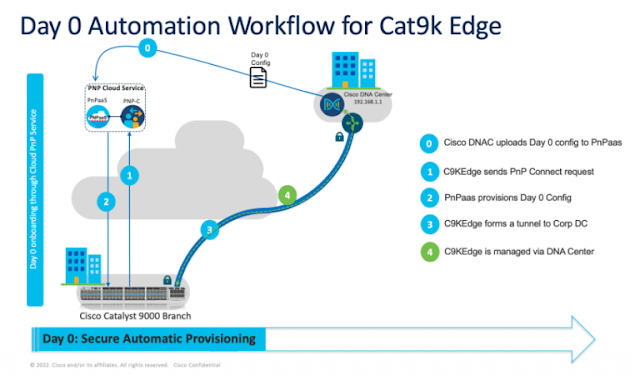
Figure 1. Day 0 Automation Workflow for onboarding Catalyst 9300X
Cisco has augmented the PNP Connect with Plug and Play as a Service (PnPaaS). This enhancement allows Cisco DNA Center to send the Day 0 switch configuration file to the PnP Cloud Service. Once the switch sends its PnP request to devicehelper.cisco.com, the PnP Cloud Service responds with the configuration file. This allows the switch to establish the IPsec tunnel and for Cisco DNA Center to manage the newly onboarded switch.
Figure 2. Onboard Catalyst 9300X Device using PnP Cloud
So, how do you create the Day 0 configuration file? Easy, it’s pretty straightforward. Just go to Cisco DNA Center Provision –> Services –> Secure Tunnels and click on Onboard New Device. The form will ask for a Site and a Virtual Account where the switch is associated. Once this information is confirmed, the form can be completed with the following: the switch serial number, a management IP (resulting in a loopback address on the switch), the IP address of the Head-End (or remote side), an IPsec pre-shared key, the HSEC token, and a switch hostname. If the switch already has the HSEC token pre-installed from manufacturing at the time of purchase (it requires a selection in CCW), then the HSEC token entry does not need to be filled in. To look at the configuration file prior to its implementation, select the Day-0 Configuration Preview tab.
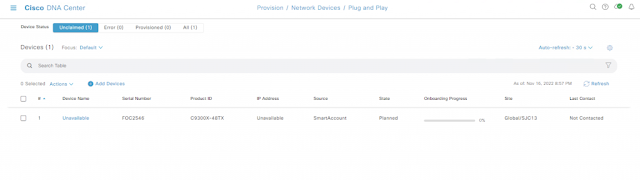
Figure 3. Cisco DNA Center Plug and Play Status
After selecting the Onboard Device option, the onboarding status of the switch can be verified under Provision –> Network Devices –> Plug and Play. Initially, the switch will appear as Unclaimed, and the state as Planned. When the process completes (please be patient, it will take several minutes) the switch appears under Provisioned and the state as Provisioned.
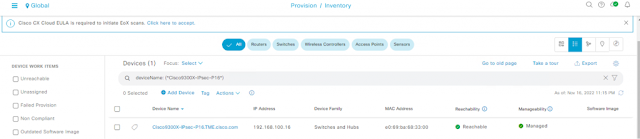
Figure 4. Cisco Catalyst 9300X with IPsec in Inventory
After the switch is onboarded, it can be managed over the IPsec tunnel using the loopback by selecting Provision –> Network Devices –> Inventory.
Cisco Umbrella – Creating Secure Tunnels
Now that the switch is under Cisco DNA Center management, additional IPsec tunnels can be configured to connect to a Secure Internet Gateway (SIG). In this case, it will be to Cisco Umbrella, but it can also be to a third party like Zscaler. In order to automate both sides of the tunnel the switch and Cisco Umbrella there is a prerequisite to integrate Cisco Umbrella and Cisco DNA Center using API Keys (System –> Settings –> External Services). This topic is not covered here. Cisco DNA Center will only automate the switch portion when the API integration is not established.
Figure 5. Cisco Umbrella IPsec Tunnel Creation in Cisco DNA Center
In order to add the Cisco Umbrella tunnels, go to Cisco DNA Center Provision –> Services –> Secure Tunnels but this time click on Create Secure Tunnel. The form will require the following information: Site, Device, number of Cisco Umbrella tunnels (up to 4), Tunnel Name, and Tunnel Source Interface. In addition, a selection of the Cisco Umbrella data center location can be made, otherwise, the selection will be made based on the switch site location. If you have more than one tunnel, either the same data center or a different location can be selected.
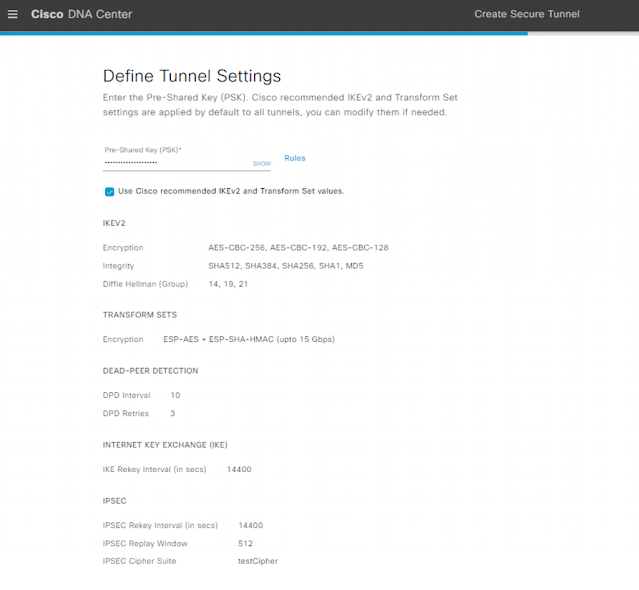
Figure 6. Cisco Umbrella IPsec Pre-Shared Key in Cisco DNA Center
The next screen will ask for the Cisco Umbrella Tunnel Pre-Shared Key and the option to change the default IKEv2 and Transform Set values. The default values are for best practice and should not be changed unless it is for interoperability or other security reasons.
Figure 7. Handling Site Traffic using ECMP or PBR
In the next screen, traffic can be handled either by sending all traffic to Cisco Umbrella using Equal-Cost Multi-Path (ECMP) load balancing when using multiple tunnels or traffic can be steered using Policy-Based Routing (PBR). Handling the traffic in this manner should help with most use cases. Subsequently, there will be a summary screen and a selection to create the tunnel(s).
Figure 8. Cisco DNA Center and Cisco Umbrella Tunnel Confirmation
After the switch and Cisco Umbrella have been provisioned, the status of the tunnels can be verified under Cisco DNA Center Provision –> Services –> Secure Tunnels.
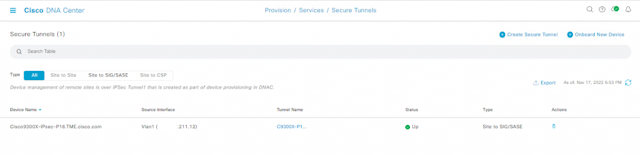
Figure 9. C9300X IPsec Tunnels Cisco DNA Center and Cisco Umbrella
The IPsec tunnel information to both Cisco DNA Center and Cisco Umbrella can be verified via the CLI as well. Tunnel1 is the tunnel to Cisco DNA Center and Tunnel2 is the tunnel to Cisco Umbrella.
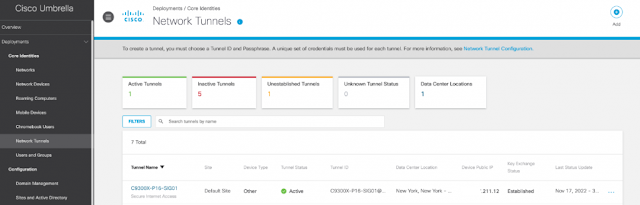
Figure 10. Cisco Umbrella UI IPsec tunnel to C9300X
Alternatively, Cisco Umbrella can also display the IPsec tunnel established to the Catalyst 9300X.
Source: cisco.com








0 comments:
Post a Comment