Thursday, 28 December 2023
Managing API Contracts and OpenAPI Documents at Scale
Saturday, 7 January 2023
We’ve Doubled the Number of Cisco DNA Center Reservable Sandboxes
The Cisco DNA Center sandboxes have always been in high demand. For a while now we have had two always-on and two reservable sandboxes for Cisco DNA Center. With each of these sandboxes requiring at least one Cisco DNA Center appliance and several Catalyst 9000 switches, it’s easy to see why they were some of the most expensive sandboxes we have. (Hence, the limited number.) Expensive not only because of the hardware appliance and physical Catalyst 9000 switches, but also from a rack footprint, power, and cooling perspective.
Fully test all the features of the Cisco DNA Center platform including building SDA fabrics
Taking advantage of some virtualization secret sauce and holiday magic, the sandbox team has done a tremendous job and they have launched 4 Cisco DNA Center reservable sandboxes. Yes, you’ve read that right! We have doubled the number of Cisco DNA Center reservable sandboxes! And all 4 of them are running the latest version of code 2.3.3.5 as of the writing of this blog and have a Cisco ISE server so you can fully test all the features of the Cisco DNA Center platform including building SDA fabrics. There are two CoreOS virtual machines attached to the access switches for traffic generation and client troubleshooting. We’ve also included a CentOS DevBox that provides a developer environment with Python, virtual environment, Ansible and other tools already preinstalled.
Test and develop your applications and integrations
No cost to you
Friday, 28 October 2022
Cisco Announces Open Source Cloud-Native Offerings for Securing Modern Applications
OpenClarity is a trio of projects
Building the Application-First Future
Cisco Leading in Open Source
Join Us at KubeCon in Detroit
Thursday, 13 October 2022
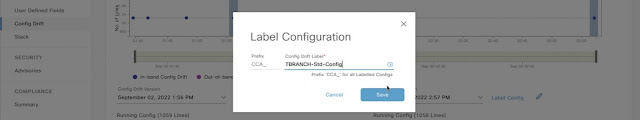
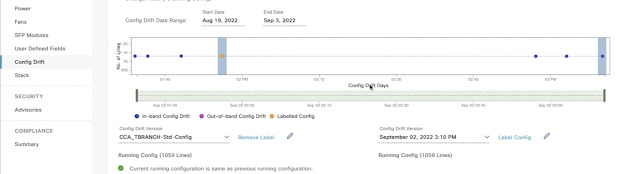
Cisco DNA Center and Device configuration management
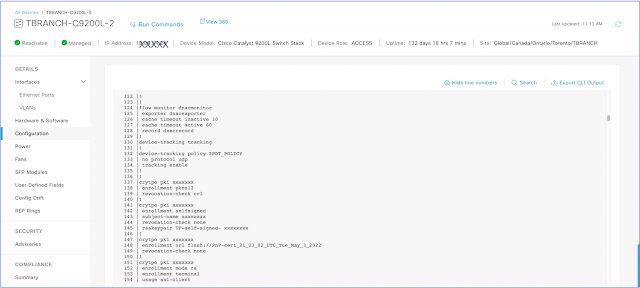
Visualize Configuration in Inventory
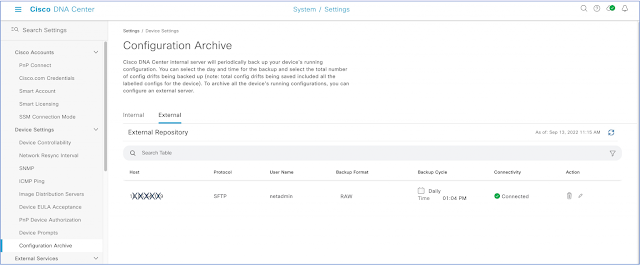
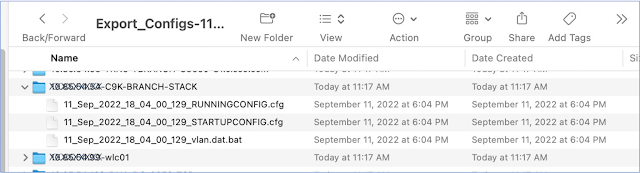
Export the device configuration
APIs to retrieve device configuration
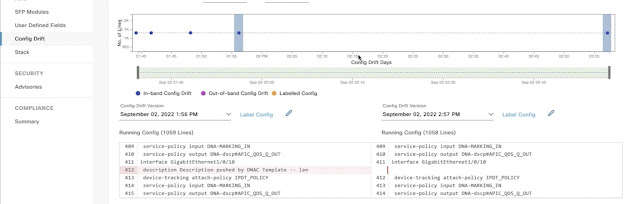
Visualize Configuration Drifts
Saturday, 29 May 2021
Cisco Secure Firewall insertion using Cisco cAPIC in Azure
In today’s world, enterprises are undergoing a transition to innovate rapidly, keep up with the competition, and increase application agility to meet ever-changing customer demands. To achieve these goals, they often choose the hybrid cloud infrastructure approach, choosing different infrastructure environments to deploy different types of applications. Some applications are best suited for hosting on-premises, whereas others are better suited for hosting in public cloud. Thus, hybrid cloud is the new normal for many organizations. However, in a hybrid cloud environment, the challenge is to maintain a uniform enterprise operational model, comply with corporate security policies, and gain visibility across the hybrid environments.
Read More: 300-710: Securing Networks with Cisco Firepower (SNCF)
Cisco Cloud Application Centric Infrastructure (Cisco Cloud ACI) is a comprehensive solution that provides:
◉ simplified operations
◉ consistent security policy management
◉ visibility across multiple on-premises data centers and public clouds or hybrid cloud environments
◉ unified security policy for the hybrid cloud
◉ extends on-premises layer-7 security to public cloud
In an on-premises Cisco ACI data center, Cisco Application Policy Infrastructure Controller (APIC) is the single point of policy configuration and management for all the Cisco ACI switches deployed in the data center. Cisco ACI multi-site orchestrator (MSO) provides a seamless way to interconnect multiple cisco ACI data centers. MSO is a software solution representing a single point of policy orchestration and visibility across multiple geographically dispersed ACI sites.
Cisco Cloud APIC runs natively on supported public clouds to provide automated connectivity, policy translation, and enhanced visibility of workloads in the public cloud. Cisco Cloud APIC translates all the policies received from MSO and programs them into cloud-native constructs such as VNets (Virtual Network), application security groups, network security groups, outbound rules, inbound rules, etc. This new solution brings a suite of capabilities to extend on-premises data centers into true hybrid cloud architectures, helping drive policy and operational consistency regardless of where your applications reside. Also, it provides a single point of policy orchestration across hybrid environments, operational consistency, and visibility across clouds.
Traditional firewall integration in on-prem Data Centers
Hybrid Cloud
Securing Azure with virtual ASA and FTD solutions
Use case 1: Spoke to Internet (N/S traffic flows)
Use case 2: Spoke to spoke multi-node inter-VPC, intra-region traffic flow enablement
Tuesday, 26 September 2017
End-to-end Security Management for the Next-generation Data Center with Cisco ACI and AlgoSec
To address these challenges, we need a solution that supports visibility, agility, automation and extensibility, while not compromising on tight security and compliance requirements.