In psychology, the term “cognition” refers to a human function that is involved in gaining knowledge and intelligence. It helps describe how people process information and how the treatment of this information may lead to various decisions and actions. Individuals use cognition every day. Examples as simple as the formation of concepts, reasoning through logic, making judgments, problem-solving, and achieving goals all fall under the purview of this term.
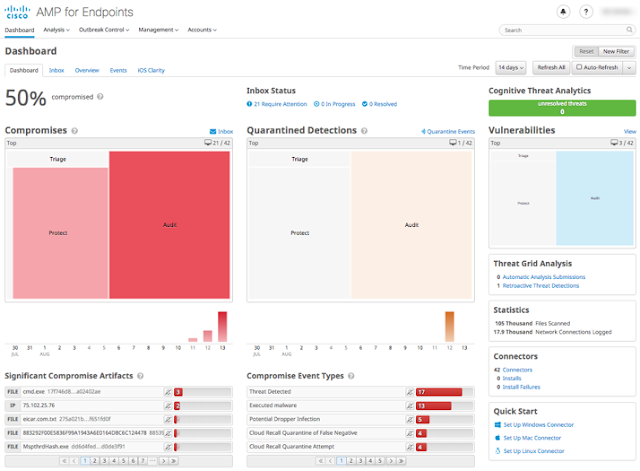
In cybersecurity, applying the principles of cognition helps us turn individual observed threat events into actionable alerts full of rich investigative detail. This process improves over time through continuous learning. The goal is to boost discovery of novel or morphing threats and streamlining of the cybersecurity incident response. The work of the security operations teams can be vastly optimized by delivering prioritized actionable alerts with rich investigative context.
Let’s take a moment to think of the tasks that a security team performs on a day-to-day basis:
◈ Looking through ever-increasing numbers of suspicious events coming from a myriad of security tools.
◈ Conducting initial assessments to determine whether each particular anomaly requires more investigation time or should be ignored.
◈ Triaging and assigning priorities.
All of these actions are based on the processes, technology, and knowledge of any particular security team. This initial decision-making process by itself is crucial. If a mistake is made, a valid security event could be ignored. Or, too much time could be spent to investigate what ends up being a false positive. These challenges, coupled with the limited resources that organizations typically have, as well as complexities associated with attack attribution, may be daunting.
That’s why security teams should embrace automation. At Cisco, we’re committed to helping organizations step up their game through the use of our Cognitive Intelligence. This technology allows correlating telemetry from various sources (Cisco and 3rdparty web proxy logs, Netflow telemetry, SHA256 hash values and file behaviors from AMP and Threat Grid) to produce accurate context-rich threat knowledge specific to a particular organization. This data, combined with the Global Risk Map of domains on the Internet, allows organizations to confidently identify variants of memory-resident malware, polymorphic malware with diversified binaries, and in general any innovative malware, that attempts to avoid detection by an in-line blocking engine.
As a result of automation like this, less time needs to be spent on detailed threat investigations to confirm the presence of a breach, identify the scope and begin triage. And that will in turn dramatically help mitigate the shortage of skilled security personnel by increasing the effectiveness of each analyst.
In cybersecurity, applying the principles of cognition helps us turn individual observed threat events into actionable alerts full of rich investigative detail. This process improves over time through continuous learning. The goal is to boost discovery of novel or morphing threats and streamlining of the cybersecurity incident response. The work of the security operations teams can be vastly optimized by delivering prioritized actionable alerts with rich investigative context.
Enhancing Incident Response
Let’s take a moment to think of the tasks that a security team performs on a day-to-day basis:
◈ Looking through ever-increasing numbers of suspicious events coming from a myriad of security tools.
◈ Conducting initial assessments to determine whether each particular anomaly requires more investigation time or should be ignored.
◈ Triaging and assigning priorities.
All of these actions are based on the processes, technology, and knowledge of any particular security team. This initial decision-making process by itself is crucial. If a mistake is made, a valid security event could be ignored. Or, too much time could be spent to investigate what ends up being a false positive. These challenges, coupled with the limited resources that organizations typically have, as well as complexities associated with attack attribution, may be daunting.
That’s why security teams should embrace automation. At Cisco, we’re committed to helping organizations step up their game through the use of our Cognitive Intelligence. This technology allows correlating telemetry from various sources (Cisco and 3rdparty web proxy logs, Netflow telemetry, SHA256 hash values and file behaviors from AMP and Threat Grid) to produce accurate context-rich threat knowledge specific to a particular organization. This data, combined with the Global Risk Map of domains on the Internet, allows organizations to confidently identify variants of memory-resident malware, polymorphic malware with diversified binaries, and in general any innovative malware, that attempts to avoid detection by an in-line blocking engine.
As a result of automation like this, less time needs to be spent on detailed threat investigations to confirm the presence of a breach, identify the scope and begin triage. And that will in turn dramatically help mitigate the shortage of skilled security personnel by increasing the effectiveness of each analyst.
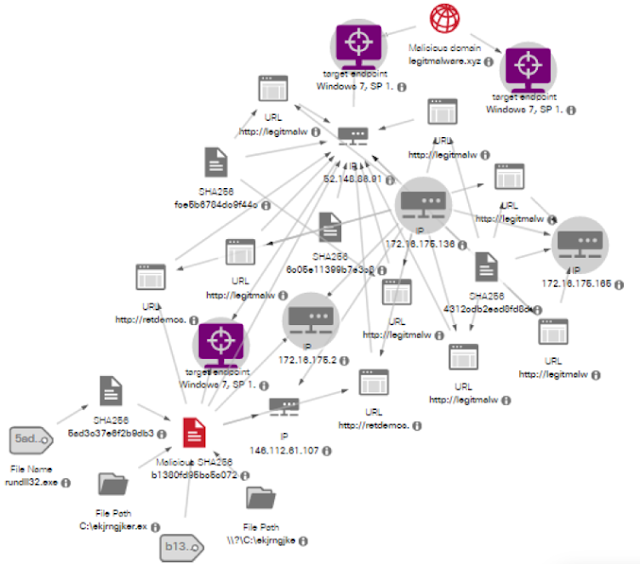
Example of a Confirmed Threat Campaign
In a sense, Cognitive Intelligence algorithms mimic the threat hunting process for observed suspicious events. It identifies combinations of features that are indicative of malware activity, in a similar fashion that an incident responder would do, starting with relatively strong indicators from one dataset and pivoting through the other datasets at its disposal. The pivot point may lead to more evidence, such as behavioral anomalies that help reinforce the infection hypothesis. Alternatively, the breach presumption may fade away and can either be terminated very quickly or re-started when new data becomes available. These algorithms are similar to incident response playbooks used by Cisco CSIRT and other incident response teams, but operate on a much larger scale.
What’s New in 2018: Probabilistic Threat Propagation
One of the example algorithms that we call Probabilistic Threat Propagation (PTP) is designed to scale up the number of retrospectively convicted malware samples (threat actor weapon), as well as the number of malicious domains (threat actor infrastructure) across the Cisco AMP, Threat Grid, and Cognitive knowledge bases.
Probabilistic Threat Propagation in a Nutshell
PTP algorithm monitors network communications from individual hashes to hosts on the Internet and constructs a graph based on the observed connections. The goal is to accurately identify polymorphic malware families and yet unknown malicious domains, based on the partial knowledge of some of the already convicted hashes and domains. The key here is that malware authors often reuse the same command-and-control (C2) infrastructure. Hence the C2 domains often remain the same across polymorphic malware variants. At the same time, these domains are usually not accessed for benign purposes.
For example, if an unknown file connects to a confirmed malicious domain, there’s a certain probability that this sample is malicious. Likewise, if a malicious file establishes a connection to an unknown domain, there’s a probability for this domain to be harmful. To confirm such assumptions, Cisco leverages statistical data surrounding the domain to determine how frequently it’s accessed, by which files and so on.
Graph built by Probabilistic Threat Propagation Algorithm
The capability that we have introduced helps security analysts track and detect new versions of malware, including polymorphic and memory-resident malware, given the fact that C2 infrastructure remains intact. Similarly, this method is capable of tracking migrations of attacker’s C2 infrastructure, given the knowledge of malicious binaries which belong to the same malicious family. Cognitive Intelligence helps leverage specific telemetry from a stack of security products (file hashes from AMP, file behaviours from Threat Grid, anomalous traffic statistics and threat campaigns from Cognitive). That allows Cisco to model threat actor behaviors across both the endpoint and the network to be able to better protect its customers.
Probabilistic Threat Propagation algorithm also provides additional sensitivity to file-less malware (that doesn’t have file footprint on the disk of the system) and process injections. Such infections can be detected when a legitimate process or a business application starts communicating with domains associated with C2 infrastructure, that other malicious binaries predominantly contacted.
The beauty of this capability is that it runs offline in the Cisco cloud infrastructure, and therefore does not require any additional computational resources from customers’ endpoints or infrastructure. It simply works to provide better protection and the increased count of retrospective detections for novel variants of known malware.
Measuring Results
This blog entry wouldn’t be complete if we didn’t speak about the initial results, that just this single algorithm delivers. From a single malicious binary, Probabilistic Threat Propagation algorithm is able to identify tens if not hundreds of additional binaries that are a part of the same threat family and that also get convicted as a part of this analysis. Similarly, with this new mechanism of tackling polymorphism, we will generally be able to identify tens of additional infected hosts affected by a polymorphic variant of a particular threat. That is especially rewarding when it comes to measuring the positive impact on Cisco customers.
Scaling threat detection efficacy with Probabilistic Threat Propagation
Cisco AMP for Endpoints and other AMP-enabled integrations (AMP for Email Security, AMP for WSA, AMP for Networks, AMP for Umbrella) leverage AMP cloud intelligence to provide improved threat detection capabilities boosted by the PTP algorithm.