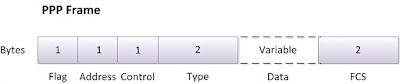
The standard version of HDLC does not have a protocol field to identify the Layer 3 protocol encapsulated by HDLC. But the PPP standard does define a protocol field to identify the type of packet inside the frame. This field allows packets from many different Layer 3 protocols to pass over a single link. However, in practice only packets for the two versions of IP (IPv4 and IPv6) are encountered. Figure 12-5 shows a PPP frame which is identical to the HDLC frame presented in Figure 12-5 earlier in the chapter.
Figure 12-5 PPP Framing
PPP is a varsatile protocol and supports both synchronous and asynchronous links. The protocol Type filed in the header allows multiple Layer 3 protocols to be carried over the same PPP link. PPP also supports authentication and two mechanisms are available for this purpose: Password Authentication Porotocol (PAP) and Challenge Handshake Authentication Protocol (CHAP). PPP has control protocols for each higher-layer protocol supported by PPP, allowing easier integration and support for those protocols.
PPP Components
Even though PPP framing is pretty similar to HDLC, PPP defines a set of Layer 2 control protocols that perform various link control functions. These control protocols of PPP are separated into two caregories:
◈ Link Control Protocol (LCP): It has several functions related to the data link itself ignoring the Layer 3 protocol encapsulated by PPP.
◈ Network Control Protocol (NCP): There is one protocol of this caregory for each network layer protocol. Each protocol performs functions specific to its related Layer 3 protocol.
Key Concept: PPP has two components: LCP that is responsible establishing, configuring, maintaining, and terminating the connection, and NCP which is specific to the Layer 3 protocol encapsulated by PPP.
The Link Control Protocol (LCP) implements all those control functions that work regardless of the Layer 3 protocol encapsulated by PPP. All functions specific to a Layer 3 protocol are performed by the Network Control Protocol (NCP) specific to the related protocl, such as IP Control Protocol (IPCP) for the Internet Protocol (IP). PPP uses a single instance of LCP for a PPP link while one NCP instance is used for each Layer 3 protocol defined on the link. For example, a PPP link that uses IPv4, IPv6, and Cisco Discovery Protocol (CDP) will use one instance of LCP plus IPCP for IPv4, IPv6CP for IPv6, and CDPCP for CDP.
Table 12-2 Functions of Link Control Protocol (LCP)
| LCP Feature | Function | Description |
| Magic number | Detection of looped link | Disables the router interface if a looped link is detected so that rerouting takes place over a working route. |
| Link-quality monitoring (LQM) | Error detection | Disables a router interface that exceeds certain error percentage threshold, andallows rerouting over better routes. |
| PAP and CHAP | Authentication | Exchanges names and passwords so that each device can verify the identity of the device at the other end of the link. |
| Multilink PPP | Bundling multiple links | Multiple parallel PPP links are bundled together to expand available bandwidth by load balancing traffic over those links. |
Authentication
In the field of networking, authentication is a mechanism used to verify the identity of another device. This identity verification is needed to confirm that the other device is legitimate and not some one only appearing to be an authentic device in order to cause damage or steal information. For example, if R1 and R2 are to form a serial link using PPP, R1 may want R2 to somewhow prove that it really is R2. This scenario is where R1 is authenticating R2, or in other words, asking R2 to prove its identity.
PPP is used over both synchronous leased lines and asynchronous dial lines, and configuration of authentication remains the same for both cases. PPP defines two authentication protocols: Password Authentication Protocol (PAP) and Channel Handshake Authentication Protocol (CHAP). Both protocols involve exchanges of messages between the two PPP speaking devices, but there are differences in detail. With PAP, the device to be authenticated starts the message exchange by sending a clear text pasword, claiming to be legitimate. The device at the other end of PPP link compares the password with its own password and if the password is correct, sends back an acknowledgement. The authentication process is one way and one or both devices can authenticate each other separately. PAP is simple in operation as well as configuration but it is insecure because the password is sent in clear text and can be sniffed.
Channel Handshake Authentication Protocol (CHAP) is a much more secure option than PAP and the password is never sent in clear text with CHAP. CHAP verifies the identity of the PPP peer by means of a three-way handshake. The general steps performed are:
1. After Link Control Protocol (LCP) phase is complete and CHAP is negotiated between the two devices, the authenticator sends a challenge message to the PPP peer.
2. The peer responds with a calculated through a one-way hash function of Message Digest 5 (MD5).
3. The authenticator calculates its own hash value and compares the received response agains it. If the values match, the authentication is considered successful. Otherwise connection is terminated.
CHAP is a one-way authentication method, which means it involves an authenticator authenticating its peer. In practice, both peers are configured to authenticate each other and two separate three-way handshakes take place.
PAP is much less secure because PAP sends both the hostname and passowrd in clear text inside a message. These values can be easily read if someone places a tracing tool in the circuit to sniff data. CHAP uses a one-way hash algortithm, known as MD5, with input to the algortithm being a password that is used locally to compute the hash and never crosses the link and a shared random number.
PPP Phases: LCP, Authentication, and NCP
LCP negotiation is a PPP phase in which parameters are negotiated for establishing, configuring, and testing the data-link connection. During LCP negotiation, the two routers agree whether to use PAP or CHAP for authentication or whether to use authentication at all or not. The LCP negotiation also uses a parameter called MagicNumber, which is used to determine if the link is looped back. A random text string is sent across the link and, if the same value is received back, the router knows that the lin if looped. An LCP state of open means that LCP was successfully completed, while an LCP state of closed indicates an LCP failure.
The authentication phase is optional as PPP authentication is not mandatory. The authentication protocol agreed upon in the LCP negotiation (PAP or CHAP) is used to perform authentication in this phase.
The mandatory NCP phase is used to establish and configure different network-layer protocols. The most common network layer protocol is the Internet Protocol (IP). You know that there is a specific NCP for each network layer protocol supported and the one for IP is IP Control Protocol (IPCP). The two routers exchange IPCP messages to negotiate options specific to the network layer protocol, that is, IP. IPCP negotiation can be used for IP address assignment to the peer.




0 comments:
Post a Comment