Since its initial release, Cisco Application Centric Infrastructure (ACI) has been selected and deployed by many healthcare institutions around the globe. ACI is the foundation for achieving these customer’s next generation application requirements for their complex environments and applications.
In this blog, we will focus on how Cisco ACI is used in production for Electronic Health Records (EHR) systems at large to small healthcare organizations. From discussions with our healthcare customers, some of the key concerns I’ve heard are security, reliability, performance, compliance with regulatory requirements, agility and, most importantly, simple and easy to manage operations. One of the market leading EHR systems is from Epic so we will consider how ACI addresses some of these concerns for Epic systems.
1. Does your platform give you the flexibility to deploy Epic on whichever infrastructure is right for your business? Whether that is a multi-hypervisor-based system, bare-metal, or any option available in the Epic target platform guide?
2. Does your platform give you the resiliency necessary? Do you need high availability across active-active data centers?
3. Does your platform properly secure the Electronic Patient Healthcare Information (ePHI)? Do you have the isolation and layers of security protections that will be required to achieve deployments for next generation applications? Do these implementations start at the client device accessing the EHR system?
The Epic EHR system supports electronic medical and health record data for patients, as well as end to end management of workflows supporting patient care including scheduling, billing, prescription management, record management, clinical unified communications, and more. Epic is a complex application suite, made up of many discrete software components and services. Figure-1 provides a high-level overview of the Epic application suite, mapped into an ACI Application Profile.
In this blog, we will focus on how Cisco ACI is used in production for Electronic Health Records (EHR) systems at large to small healthcare organizations. From discussions with our healthcare customers, some of the key concerns I’ve heard are security, reliability, performance, compliance with regulatory requirements, agility and, most importantly, simple and easy to manage operations. One of the market leading EHR systems is from Epic so we will consider how ACI addresses some of these concerns for Epic systems.
1. Does your platform give you the flexibility to deploy Epic on whichever infrastructure is right for your business? Whether that is a multi-hypervisor-based system, bare-metal, or any option available in the Epic target platform guide?
2. Does your platform give you the resiliency necessary? Do you need high availability across active-active data centers?
3. Does your platform properly secure the Electronic Patient Healthcare Information (ePHI)? Do you have the isolation and layers of security protections that will be required to achieve deployments for next generation applications? Do these implementations start at the client device accessing the EHR system?
The Epic EHR system supports electronic medical and health record data for patients, as well as end to end management of workflows supporting patient care including scheduling, billing, prescription management, record management, clinical unified communications, and more. Epic is a complex application suite, made up of many discrete software components and services. Figure-1 provides a high-level overview of the Epic application suite, mapped into an ACI Application Profile.
Figure 1 ACI Application Profile for Epic
◉ Client access is a grouping of the Thin Client, Willow Client, Thick Client, and Business Continuity Access (BCA) PCs.
◉ Presentation contains the BCA relay, CitrixXenApp and HyperSpace for virtual desktops (VDI), MyChart, and other presentation layer functions and services.
◉ Database contains the Clarity RDBMS, BusinessObjects, and related functions.
◉ CacheDB contains the production Cache database, failover, reporting and disaster recovery (DR) shadow systems.
◉ MultiPurposeServices contains WebBlob servers, FileServices, Network Printers, WinPrintServers, Digital Signing, Kuiper, SQL, SystemPulse for monitoring, and more.
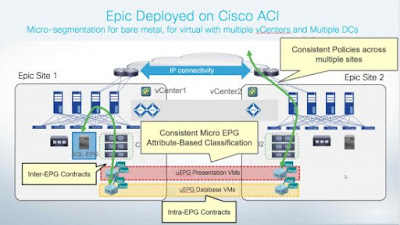
Working together with healthcare customers, Epic deployments on Cisco ACI have included Cache databases and Hyperspace on bare metal servers or virtualized on leading vendors’ hypervisors. Cisco ACI provides a means for consistent segmentation and policy-based automation of the bare metal Unix servers and virtual guests on VMware, Microsoft, or Citrix hypervisors. This simplifies operations for the healthcare IT organization providing a single pane of glass for configuration and troubleshooting across multiple hypervisors and bare-metal server endpoints.
To achieve Epic Honor Roll (Good Maintenance) program requirements, the Epic systems must be deployed on a high availability infrastructure to quickly recover from any downtime during a regional disaster. With this in mind, Epic systems are designed and deployed across multiple fault domains to achieve high availability. ACI simplifies the management of active- active data centers by reducing the complexity of the networking requirements for data center interconnect and by providing centralized, consistent, and flexible automation and control of application and security policies across multiple data centers. An ACI multi-pod deployment provides a common operating framework across separate failure domains in different data centers. The ACI Application Network Profile allows Epic services and server groups to be implemented in separate failure domains, and yet used as a single pool that can be independently operated in the event of a failure.
Figure-2 provides a logical view of the common operational control ACI can provide to simplify management of separate fault domains.
Figure 2 Cisco ACI provides common operational control across multiple pods or data center sites for Epic application resiliency.
In a 2017 research report by the Ponemon Institute, on the cost of a data breach, they talk about the average cost of a data breach at $3.6M and the firms they studied are having larger breaches. So in addition to protecting PHCI, healthcare companies have to concern themselves with ransomware and other threats. Security experts talk about using a layered defense and reducing the attack surface.
Here are a few examples.
1. Security needs to start at the client device. Using Security Group Tags (SGT), we can tag the security group policy associatedwith the client device’s network communications and use ACI or Tetration to do the enforcement in the data center.
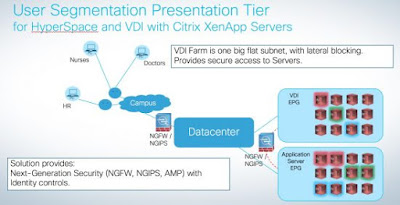
2. If we consider the Epic Hyperspace presentation layer, we can talk about using secure VDI for desktop virtualization so that each virtual workstation is completely isolated from any other client workstation by micro-segmenting the Hyperspace on Citrix XenApp or VMware horizon VDI VMs using Cisco ACI. (See Figure 3)
Figure 3 Epic Presentation Tier with Cisco ACI secure VDI use case
In another example, in the Multipurpose Services tier, Web Blob servers communicate to discrete application servers which have full rein to talk to each other. With micro-segmentation, they can be isolated to further reduce the attack surface.
In recent discussions with Epic customers requiring additional layered data center security policies and looking for ways to further reduce the application attack surfaces, we have presented another option, Cisco Tetration, for their Epic EMR deployments. I will cover this and more in a future blog.
1. Tetration records all network traffic between data center physical and virtualized guests, and provides extremely precise “customized white list” application profiles used to secure the Epic EMR system and all other healthcare applications in customer data centers today (regardless of which networking infrastructure is implemented today).
2. Tetration also provides real time change notification as healthcare applications evolve; the application profiles are automatically updated to provide visibility and policy enforcement for the Epic system and all the other applications sharing the data center infrastructure.





0 comments:
Post a Comment