Why network segmentation matters in the enterprise of today
Network Segmentation easily gets lost in a conversation as it is a heavily used term in the industry. Everyone claims to support it when in reality most vendors support the bare minimum to simply claim compliance in an RFP (Request for Proposal) or RFI (Request for Information).
Network segmentation is a critical requirement to address the growing scale, complexity and security demands of today’s campus and branch networks. That’s because segmentation allows customers to protect their data. Segmentation divides an infrastructure into individual components and builds connection points between the relevant components based on the understanding of applications, users, consumers, and devices
The days of managing secure networks with VLANs and ACLs are ways of the old. Customers require a campus infrastructure capable to support a software defined approach for network segmentation. Networks today need to be purpose built for commencing the journey of intent-based networking. Network segmentation is a key pillar supporting the foundation of Cisco’s powerful Software-Defined Access (SD-Access) architecture.
Raising the stakes with multi-level network segmentation
Traditionally, when a customer was required to isolate a given network, VLANS and ACLs (Access Control Lists) were configured to achieve network separation. A simple use case to enforce policies for users, devices, and things were challenging to implement and complex to manage as new users and devices were added to the network. Cisco has addressed these challenges and raised the stakes for network segmentation offering a new approach to multi-level segmentation for the enterprise campus.
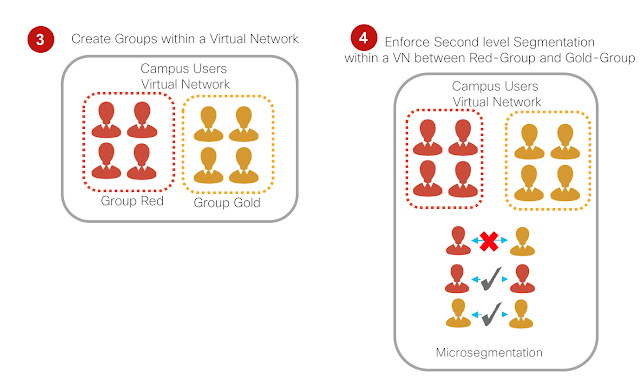
So, what is multi-level segmentation? As it’s called, Multi-level segmentation provides two-levels of segmentation using layer 3 virtual networks (VNs) and scalable group tags (SGTs).
Comparing vendors
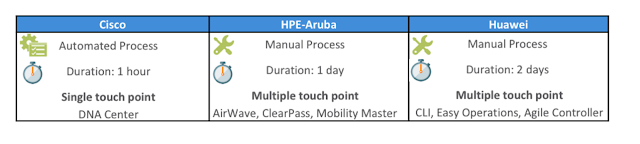
Comparing the segmentation capabilities of Cisco, Aruba and Huawei, several key takeaways can be learned from the independent Miercom report. In the Miercom comparison the bottom line is there is a clear benefit with the automated, single touch point approach of Cisco compared to the manual – multi-touch point approaches of HPE-Aruba and Huawei.
Aruba
Aruba’s segmentation offering is highly dependent on its mobility controller. With only a small amount of traffic, Aruba’s Mobility controller was exposed as a choke point.
Regardless of how many access layer switches and network uplinks are added, the limitation is still present until an additional Aruba Mobility controller can be purchased and added to the network. The network administrator using the Aruba architecture will constantly need to monitor the load of the segmentation service. This is because the mobility controller responsible for wireless association/ termination will become unresponsive when the data plane performance is reached.
Aruba positions their Dynamic Segmentation for Unified Policy for wired and wireless. Aruba launched this back in 2014 and are still positioning this architecture as Next-Gen. The flaws then are still present now.
Is the Aruba solution line-rate? Can it be proved via independent test reports? Can they change policy between users, whatever their respective VLAN is?
Huawei
Huawei’s Free Mobility was basic segmentation at best. Several touchpoints and dashboards are required to get the basics to work. It’s definitely not easy to use, and requires many repetitive steps to create groups and create policy.
Huawei presents its Free Mobility solution to its customers for segmentation using group-based policy. Free Mobility is an add-on to its policy server the Agile Controller 1.0. Huawei does not offer a simple way to offer policy-based automation. In all cases Huawei requires multiple touch points and manual based configurations via CLI and countless clicks on their Agile Controller for policy.
The 3rd party test vendor configured Huawei’s Free Mobility solution to discover that it was not as easy as expected.
Multiple steps are required to create a security group – 12 to be exact. To create a single policy between a configured pair of security groups takes 16 steps.
The key takeaway was Huawei’s inability to provide an easy to use offering for multi-level segmentation.
At best, the segmentation was basic and the network administrator was left to log back into the additional devices to enable port isolation for east-west segmentation.
As you can imagine traditionally there are many touch points when trying to configure various levels of segmentation.
Cisco
With Cisco Digital Network Architecture (DNA) Center, the creation of virtual networks and management of scalable groups is possible and can be done via a single unified dashboard. Cisco DNA Center and SD-Access outshines and outperforms the competition. Cisco SD-Access is built using a campus fabric with built-in mechanisms to support two levels of segmentation. Other network vendors can only offer segmentation based on simple network separation.
The Cisco Catalyst Family embeds VNs and SGTs in its hardware using the Cisco UADP (Unified Access Data Plane) ASIC. This facilitates building a robust foundation based on a powerful hardware that allows customers to enable a network segmentation service without a compromise on performance. Other network vendors use older architectures which are bottleneck designs with limited data plane performance of only 10Gbps.
Our 3rd party tests, compare and assess the network segmentation offerings of each networking vendor. It can be seen from the report, with the other vendors customers will continue down the path of configuring named VLANs and mapping out the size of the subnet per VLAN preparing for deployment. Customers using either vendor will be required to configure a VLAN for wired employees, a VLAN for wireless employees, a VLAN for wired guests, a VLAN for wireless guests, etc.
As stated, those are ways of the past …however this is how the competition will design a campus network. They don’t offer a controller based network to provide automation and the ability to deliver true software defined networking.
Cisco SD-Access not only profiles users, devices, and things but also onboards clients to a fabric. It provides customers with capabilities to move devices in a virtual network (macro segmentation) and provide flexibility to support role-based groups (micro segmentation) and control communication based on network contracts.
With Cisco’s DNA Center, the policy application allows customers to create VNs and groups using the “drag and drop” method. Once configured, network connectivity and access were tested to verify segmentation.
Segmentation doesn’t stop in the campus
Cisco also supports the ability to keep the policy intact from the Campus User to the Data Center application with SGT to EPG (endpoint group) mapping. Cisco is the only vendor capable to offer Intent-Based Networking across the Campus and Data Center.






0 comments:
Post a Comment