The increase in bandwidth demand and access to engaging online content has led to a rapid expansion of 5G technology deployments. This combination of increased demand from a multitude of user equipment devices (laptops, mobile phones, tablets) and rapid technology deployment has created a diverse threat surface potentially affecting the availability and sustainability of desired low latency outcomes (virtual reality, IoT, online gaming, etc.). One of the newer threats is an attack from rogue or BoT-controlled IoT and user equipment devices designed to flood the network with diverse flows at the access layer, potentially exposing the entire network to a much larger DDoS attack.
With the new Cisco Secure DDoS Edge Protection solution, communication service providers (CSPs) now have an efficient DDoS detection and mitigation solution that can thwart attacks right at the access layer. The solution focuses on 5G deployments, providing an efficient attack detection and mitigation solution for GPRS Tunneling Protocol (GTP) traffic. This will help prevent malicious traffic from penetrating deeper into a CSP network. To achieve the quality of experience (QoE) targets that customers demand in 5G networks, architectures should include the following features:
◉ Remove access level anomalies at the cell site router (CSR) to preserve QoE for users accessing 5G applications
◉ Remediate user equipment anomalies on the ingress port of the CSR to remove overages in backhaul resources like microwave backhaul
◉ Automate both east-west and north-south attack life cycles to remove collateral damage on the network and to preserve application service level agreements for customers
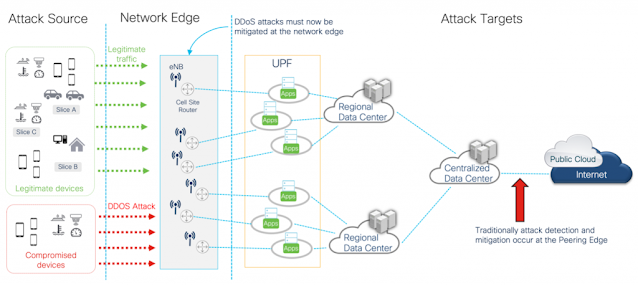
Figure 1. DDoS attack protection at the 5G network edge
The Cisco Secure DDoS Edge Protection solution offers the ability to detect and mitigate the threats as close to the source as possible – the edge. It features a docker container (detector) integrated into
IOS XR and a centralized controller. The system is also air gapped and requires no connectivity outside of the CSP network to operate. The controller performs lifecycle management of the detector, orchestration of detectors across multiple CSRs, and aggregation of telemetry and policy across the network. Having the container integrated into IOS XR allows services to be pushed to the edge to meet availability and QoE requirements for 5G services, while the controller provides a central nervous system for delivering secure outcomes for 5G. Important threats addressed by the Cisco Secure DDoS Edge Protection solution include IoT Botnets, DNS attacks, burst attacks, layer 7 application attacks, attacks inside of GTP tunnels, and reflection and amplification attacks.

Figure 2. Edge protection solution on the Cisco Network Convergence System (NCS) 540
Moving the DDoS attack detection and mitigation agent to the CSR helps speed up the attack response and can lower overall latency. Additionally, efficiency enhancements have been made to the solution in the following ways:
◉ GTP flows are first extracted at the ASIC layer using user-defined filters (UDFs) in IOS XR before they are sampled for NetFlow. This allows more attack bandwidth protection with the same sampling rate.
◉ Tunnel endpoint Identifiers (TEIDs) of GTP flows are extracted and included in the NetFlow data.
◉ Extracted NetFlow data is exported to the detector on the router and formatted using Google Protocol buffers.
Given that the NetFlow data doesn’t need to be exported to a centralized entity and is consumed locally on the router, faster attack detection and mitigation is possible.
Source: cisco.com





0 comments:
Post a Comment