In an ever-evolving digital landscape, cybersecurity has become the cornerstone of organizational success. With the proliferation of sophisticated cyber threats, businesses must adopt a multi-layered approach to ensure the integrity of their digital assets and safeguard their sensitive information. Two leading players in this space, Cisco’s Duo Security and Cisco Identity Intelligence, have emerged as champions in Identity Threat Detection & Response. In this blog post, we will explore how Cisco Identity Intelligence seamlessly complements Cisco’s Duo Security to provide a comprehensive and robust cybersecurity strategy.
The Power of Identity Threat Detection & Response
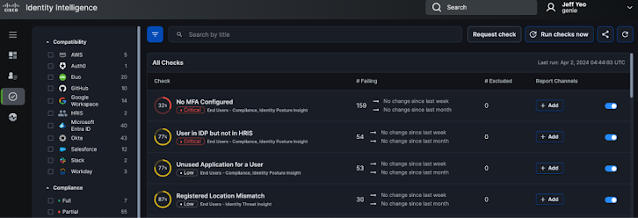
Identity Threat Detection & Response (ITDR) has become a vital aspect of modern cybersecurity. It focuses on identifying anomalies in user behavior, detecting potential unauthorized access, and responding to security incidents promptly. Cisco’s Duo Security has established itself as a prominent solution in this domain, offering a range of features such as multi-factor authentication (MFA) and access controls that protect against unauthorized access.
Cisco Identity Intelligence: Elevating Cybersecurity Preparedness
Cisco Identity Intelligence brings an additional layer of protection to the table with its advanced capabilities in anomaly detection and behavioral analytics. This innovative technology analyzes user behavior patterns, device interactions, and network activities to identify even the subtlest deviations from normal behavior. This is particularly crucial in today’s threat landscape, where attackers are becoming increasingly adept at mimicking legitimate user actions.
How Cisco Identity Intelligence Complements Cisco’s Duo Security
1. Enhanced Anomaly Detection: While Cisco’s Duo Security provides robust MFA and access controls, Cisco Identity Intelligence takes it a step further by analyzing user activities in real time. By establishing a baseline of normal behavior, Cisco Identity Intelligence can swiftly identify any unusual actions, potentially preventing unauthorized access even after initial authentication.
2. Behavioral Analytics: Cisco Identity Intelligence’s AI-driven behavioral analytics can identify complex attack patterns that may go unnoticed by traditional security measures. By correlating data across multiple dimensions, Cisco Identity Intelligence helps security teams detect identity-related threats that could lead to data breaches or system compromise.
3. Holistic Threat Response: When integrated with Cisco’s Duo Security, Cisco Identity Intelligence enables a comprehensive threat response strategy. The combined capabilities of these two solutions allow organizations to not only prevent unauthorized access but also respond proactively to emerging threats, minimizing potential damage.
4. Adaptive Security: Cisco Identity Intelligence’s adaptive security approach means that it continuously learns from new data and adjusts its understanding of what constitutes normal behavior. This adaptability ensures that evolving attack techniques are promptly recognized and mitigated.
5. Reduced False Positives: Cisco Identity Intelligence’s sophisticated engine minimizes false positives by understanding context and user intent. This helps security teams focus their efforts on genuine threats, reducing alert fatigue and streamlining incident response.
Conclusion
As the cyber threat landscape continues to evolve, the collaboration between leading cybersecurity solutions becomes imperative. Cisco’s Duo Security and Cisco Identity Intelligence collectively fortify an organization’s defense by combining multi-factor authentication, access controls, AI-driven anomaly detection, and behavioral analytics. This synergy creates a robust shield against identity-related threats and provides a holistic approach to cybersecurity.
Remember, in today’s digital age, a comprehensive cybersecurity strategy is not a luxury but a necessity. By embracing the combined power of Cisco’s Duo Security and Cisco Identity Intelligence, organizations can confidently navigate the complex realm of cyber threats and safeguard their digital assets with unwavering resolve.
Source: cisco.com






0 comments:
Post a Comment