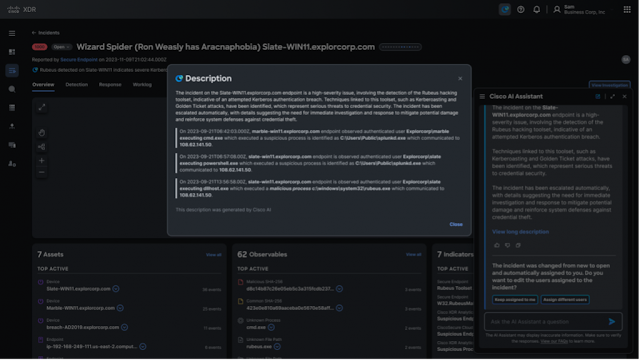
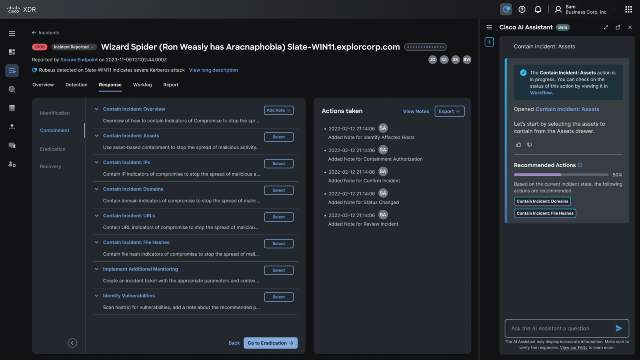
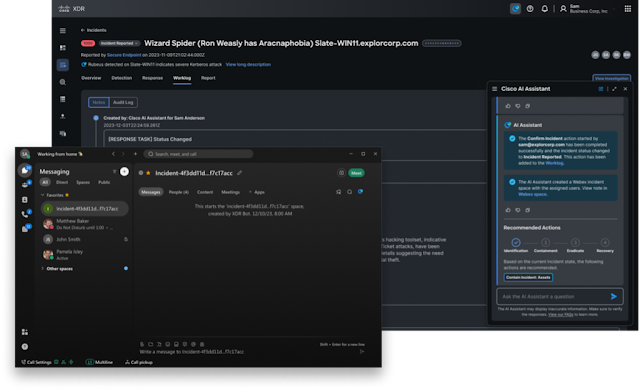
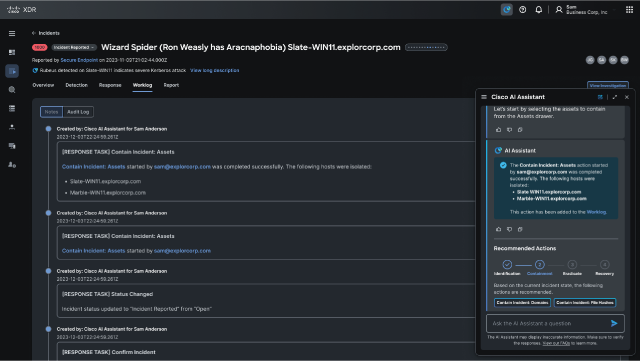
In the intricate dance between cyber attackers and defenders, understanding adversary behavior is the difference between keeping up with sophisticated attacks or falling behind the evolving threat landscape. For security teams, this often feels like trying to navigate a maze blindfolded since adversaries typically have greater insights into defender strategies than defenders have into adversarial attacks. This lack of visibility can lead to reactive cybersecurity with ineffective security operations, poor incident response, and a weak security posture.
However, there’s another approach to cybersecurity that empowers security teams to strengthen their security operations and proactively protect their environments.
Move from Reactive to Proactive Security
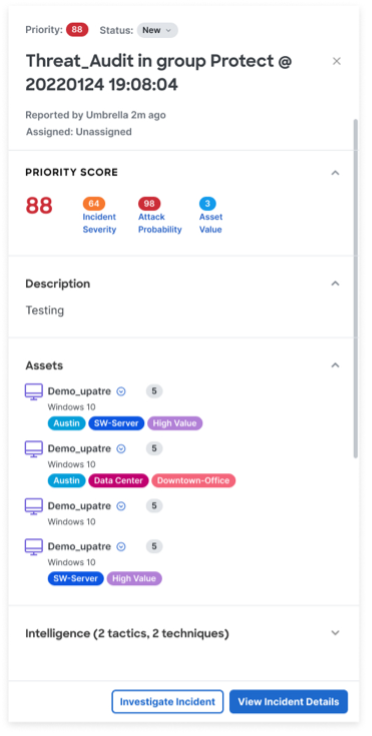
Enter MITRE ATT&CK coverage mapping – a groundbreaking capability coming soon to Cisco XDR that enables security teams to turn their reactive operations into a holistic cybersecurity strategy by taking a proactive approach to threats. MITRE ATT&CK coverage mapping uses an interactive heatmap to connect adversary behaviors to detections from Cisco XDR and other integrated security solutions (see Figure 1).
Figure 1: MITRE ATT&CK Coverage Map Dashboard
This helps visualize how your security tools cover every attacker tactic, technique, and procedure (TTP) from the MITRE ATT&CK framework to give you a comprehensive understanding of threats across your entire security environment. You can use the automated MITRE ATT&CK coverage map to strengthen your security operations by enhancing threat detection, identifying and closing gaps in your defenses, and improving incident response.
The MITRE ATT&CK coverage map enhances detection of sophisticated threats across your environment. Understanding the tactics and techniques used by adversaries allows you to improve your security by taking stronger preventative measures. Moreover, it simplifies analysis of potential threats while fostering a proactive cybersecurity mindset that helps your security teams increase alignment with attacker motives and methods. It helps you prioritize incidents based on the impact and relevance of specific adversary behaviors.
Visualizing and mapping attacker TTPs also helps your security teams expose gaps in threat detection. They can use the MITRE ATT&CK coverage map to gain complete visibility into how your current security tools cover the full spectrum of threats. This allows your analysts to spot holes in your security infrastructure and prioritize resources across the most critical gaps. Furthermore, identifying weaknesses in your defenses enables you to deploy new security tools to close coverage gaps and strengthen your overall security posture.
Finally, MITRE ATT&CK coverage mapping improves incident response with a standardized language for your security operations. The MITRE ATT&CK framework provides a common language that makes it easier for security teams to communicate and collaborate on incidents. When combined with a heatmap of product coverage, you can streamline the incident analysis process while reducing the burden on your security team to identify patterns across alerts. This speeds detection and investigation to reduce both mean time to detection (MTTD) and mean time to response (MTTR) for your security operations.
Bolster Your Defenses
MITRE ATT&CK coverage mapping in Cisco XDR provides comprehensive visibility into adversary TTPs, giving you a quick and complete understanding of attackers. These actionable insights empower your analysts to hunt for threats with targeted hypotheses based on MITRE ATT&CK techniques for a proactive approach to security. Your analysts can also use these insights to strengthen your overall security posture and enhance your defenses by identifying, prioritizing, and closing gaps across your security stack.
In the ever-changing world of cybersecurity, staying ahead of adversaries is imperative. With MITRE ATT&CK coverage mapping in Cisco XDR, you can enable proactive security operations, bolster your defenses, and navigate the cyber threat landscape with greater confidence.
Source: cisco.com