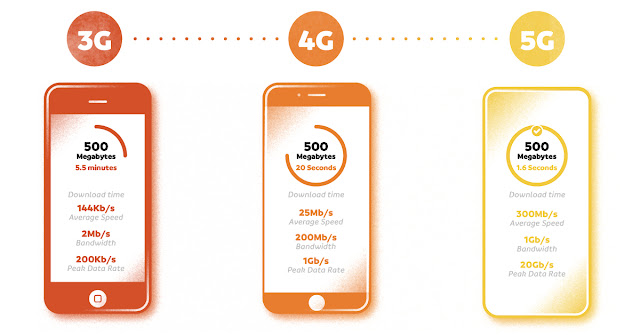
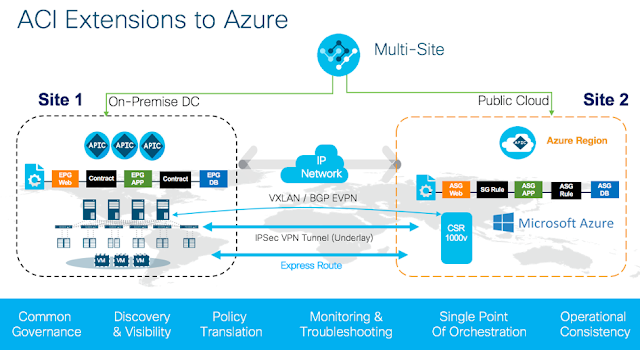
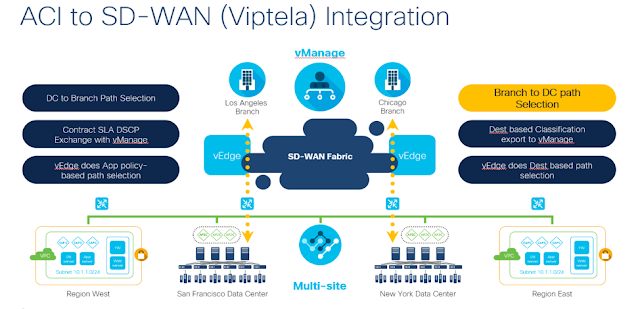
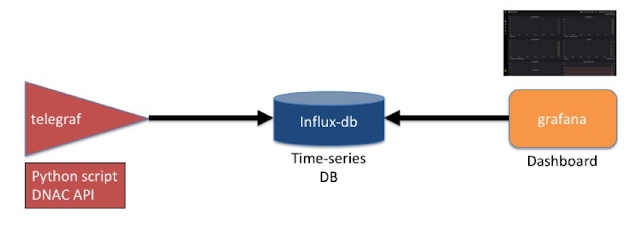
Regardless of whether you’re B2B or B2C, there is a megatrend afoot and the reality is few businesses are ready for it.
Case in point, the recent “Cisco Visual Networking Index: Forecast and Methodology, 2016–2021” states that video will constitute over 80% of internet traffic by the year 2020.
Think about that for a second.
It’s a truly profound movement.
Furthermore, ask yourself two simple questions:
Both questions, when answered honestly, can be incredibly telling.
But fret not—if your business is struggling with video then it’s highly likely all your competitors are feeling the same pains when it comes to this ever-evolving media.
So, let’s say we accept this trend for what it is and we want to truly establish a culture of video within our organizations. What can we do? Who needs to be involved? And how do we get started?
As an owner of a digital sales and marketing agency, IMPACT, I went to my team a few years ago with a simple challenge. I told them:
“Video is changing the world. Our clients aren’t ready for it. They don’t know how to get started and they certainly don’t know what to do to see a true ROI (return on investment) from video. And let me tell you, outsourcing is not the future of video. They need to learn this in-house, and we’re going to teach it to them.”
My statement wasn’t exactly celebrated at first. Fact is, most agencies “do” video for you. Almost none teach you how to do video, as well as integrate it into your sales and marketing process. With the cost of hiring an agency to do video so high, rarely does a company produce enough videos, consistently, to have a major impact on their bottom line.
Over this time of helping clients establish this culture, we’ve seen clearly there are five essential steps to creating a culture of video within your organization. When any of these are skipped, the company rarely reaches its potential. But when followed properly, the results can be astounding. Here they are:
Like anything important in business, getting buy-in to video is a must. But this doesn’t happen by sending out a company memo saying, “We’re going to do video.” No, team members must be taught how buyers are changing, why video isn’t going away, and what that means for sales, marketing, customer service, and more.
Yes, you did read that correctly. Too often video is cast aside as just another marketing activity that cost a lot while producing little fruit. This should absolutely NOT be the case. But if you approach your entire video strategy with a sales focus, then that will guide you not only on the types of videos that you should produce, but you will now see immediate results from the work you produce.
Trying to figure out what your video editorial calendar and priorities are supposed to be? Start with your sales team. Specifically, brainstorm the most common questions they answer on every sales call. If you’re really listening to what your customers are asking, then your video content will resonate, which is why everything from the cost of your products/services to what makes your company truly different needs to be shown, and not just stated, on video. By so doing, you’ll find your prospects are more educated, informed, and certainly further down the buyer’s funnel.
Without question, the biggest difference between the companies that are doing GREAT things with video, versus the ones that are not, comes down to their willingness (and faith) to hire an in-house videographer. You may be thinking to yourself, “Our business could never do that. And how would we even keep this type of person busy?” Well, once you start focusing in on the questions your customers are asking, you’ll quickly see there are likely hundreds of videos for you to produce. In fact, at my agency we’ve seen over and over again that when companies produce 100 videos or more a year (assuming they are focused on the right types of videos), their business, brand, and bottom-line explode.
100 videos? Yes, you read that correctly. Which is also why it’s so much more financially sound to hire someone in-house in lieu of outsourcing. And if you’re wondering, the average compensation we see for a videographer in the marketplace is between 40-60k—way less than the compensation of a typical agency but definitively more fruitful over the course of time.
Few things can shorten a sales cycle as well as a powerfully produced video that focuses in on the typical questions and concerns that a buyer has. This being said, most sales people don’t naturally understand how to integrate video content into the sales process. For this reason, it’s imperative you take the time to teach such skills as using 1-to-1 video in email, what types of content to use before and after sales calls, and even how to effectively communicate on camera.
So there you have it. Five proven steps to creating a culture of video within your organization.
Remember, the key starting point here is the acceptance that this critical medium isn’t going away. It’s the rising tide, and each and every one of us can either lose business (and buyer trust) because of an unwillingness to embrace it, or we can accept that buyers have changed and we therefore must “show it.”
Think about that for a second.
It’s a truly profound movement.
Furthermore, ask yourself two simple questions:
How much of our company website is video right now?
How often do we integrate video into our sales process?
Both questions, when answered honestly, can be incredibly telling.
But fret not—if your business is struggling with video then it’s highly likely all your competitors are feeling the same pains when it comes to this ever-evolving media.
So, let’s say we accept this trend for what it is and we want to truly establish a culture of video within our organizations. What can we do? Who needs to be involved? And how do we get started?
As an owner of a digital sales and marketing agency, IMPACT, I went to my team a few years ago with a simple challenge. I told them:
“Video is changing the world. Our clients aren’t ready for it. They don’t know how to get started and they certainly don’t know what to do to see a true ROI (return on investment) from video. And let me tell you, outsourcing is not the future of video. They need to learn this in-house, and we’re going to teach it to them.”
My statement wasn’t exactly celebrated at first. Fact is, most agencies “do” video for you. Almost none teach you how to do video, as well as integrate it into your sales and marketing process. With the cost of hiring an agency to do video so high, rarely does a company produce enough videos, consistently, to have a major impact on their bottom line.
Over this time of helping clients establish this culture, we’ve seen clearly there are five essential steps to creating a culture of video within your organization. When any of these are skipped, the company rarely reaches its potential. But when followed properly, the results can be astounding. Here they are:
5 Steps to Creating a Culture of Video In-House and Getting Dramatic Results:
1. Everyone Must Understand the What, How, and Why of Video
Like anything important in business, getting buy-in to video is a must. But this doesn’t happen by sending out a company memo saying, “We’re going to do video.” No, team members must be taught how buyers are changing, why video isn’t going away, and what that means for sales, marketing, customer service, and more.
2. See Video, Primarily, is a SALES Tool
Yes, you did read that correctly. Too often video is cast aside as just another marketing activity that cost a lot while producing little fruit. This should absolutely NOT be the case. But if you approach your entire video strategy with a sales focus, then that will guide you not only on the types of videos that you should produce, but you will now see immediate results from the work you produce.
3. Obsess Over Answering Customer’s Questions with Video
Trying to figure out what your video editorial calendar and priorities are supposed to be? Start with your sales team. Specifically, brainstorm the most common questions they answer on every sales call. If you’re really listening to what your customers are asking, then your video content will resonate, which is why everything from the cost of your products/services to what makes your company truly different needs to be shown, and not just stated, on video. By so doing, you’ll find your prospects are more educated, informed, and certainly further down the buyer’s funnel.
4. Hire an In-House Videographer
Without question, the biggest difference between the companies that are doing GREAT things with video, versus the ones that are not, comes down to their willingness (and faith) to hire an in-house videographer. You may be thinking to yourself, “Our business could never do that. And how would we even keep this type of person busy?” Well, once you start focusing in on the questions your customers are asking, you’ll quickly see there are likely hundreds of videos for you to produce. In fact, at my agency we’ve seen over and over again that when companies produce 100 videos or more a year (assuming they are focused on the right types of videos), their business, brand, and bottom-line explode.
5. Teach Your Sales Team How to Use Video in the Sales Process
Few things can shorten a sales cycle as well as a powerfully produced video that focuses in on the typical questions and concerns that a buyer has. This being said, most sales people don’t naturally understand how to integrate video content into the sales process. For this reason, it’s imperative you take the time to teach such skills as using 1-to-1 video in email, what types of content to use before and after sales calls, and even how to effectively communicate on camera.
So there you have it. Five proven steps to creating a culture of video within your organization.
Remember, the key starting point here is the acceptance that this critical medium isn’t going away. It’s the rising tide, and each and every one of us can either lose business (and buyer trust) because of an unwillingness to embrace it, or we can accept that buyers have changed and we therefore must “show it.”