- Exam Name: Understanding Cisco Cloud Fundamentals
- Exam Number: 210-451 CLDFND
- Exam Price: $300 USD
- Duration: 90 minutes
- Number of Questions: 55-65
- Passing Score: Variable (750-850 / 1000 Approx.)
- Recommended Training:
- Understanding Cisco Cloud Fundamentals (CLDFND)
- Understanding Cisco Cloud Fundamentals (CLDFND) E-Learning
- Exam Registration: PEARSON VUE
- Sample Questions: Cisco 210-451 Sample Questions
- Practice Exam: Cisco Certified Network Associate Cloud Practice Test
Wednesday, 6 November 2019
210-451
210-451 CCNA Cloud
210-451 Online Test
CCNA Cloud Practice Test
CCNA Cloud Study Guide
Cisco CCNA Cloud Certification
Cisco CCNA Cloud Primer
Cisco Certification
Get Quality Preparation with Cisco 210-451: CCNA Cloud (CLDFND) Sample Question
Tuesday, 5 November 2019
The Awesome Power of Webex Collaboration Combinations
Universal Combinations Guaranteed to Make Your Day Great
What is the best part of your morning? We used to hear commercials like Folgers coffee say, “It’s Folgers in your cup”. I think they were on to something big because millions of people around the world have a love affair with coffee and start their day off with coffee and their favorite pairing, from doughnuts, warm baked breads, muffins, scones, croissants and more, people love a great combo. I myself love an extra hot chai tea latte, and a vanilla Tahini bar.
Essential Workplace Combinations to Help You Thrive
At Cisco Webex we believe our collaboration technology paired with your device of choice, brings you many essential combinations to thrive in your professional daily lives. Here are my favorite Webex combinations, that enable me to have a productive workday, every day:
#1 Productive Start
As I start my morning, it is important for me to review my plan for the day and that starts with me checking my Webex Teams application on my mobile device for messages from my team, look to see if I’ve missed any urgent calls and to review meetings upcoming for the day and respond as appropriate. As a corporate executive and global leader, the combination I use most often and essential to my daily routine is with my mobile device and Webex Teams application. I have meetings at varied times of the day, including my commute to and from work, and need to collaborate and connect with my team, anytime anywhere. I love that Webex enhances my daily work routine, simply, and with the velocity I need on the go.
#2 Intuitive Experiences
My second favorite combination might surprise you, it’s not the obvious like chocolate covered strawberries and champagne, which admittedly I do love too, but it’s the intuitive experiences, ease of use and the power of the outcomes my team and I achieve during the day, enabled by AI in Webex Meetings and our Devices. Here are a few magical examples that happen effortlessly when we join AI to our Webex Meetings and Devices.
#3 Join Meetings Seamlessly
When I arrive into the office daily, I’m usually finishing up a call from my mobile office; I walk into my physical office and my Webex Teams Board device, comes alive and has “Hello Aruna” pop up on screen. The invisible proximity pairing technology from my mobile device to my Webex Teams enabled devices, allow my profile to connect, so I can use, my device of choice for the next meeting, whether it’s a one-to-one, with my team or one-to-many, I love the convenience and simplicity of Webex connecting me to others and just working.
#4 Knowing What Matters Most is Now Enabled by AI
Being an executive my meetings are typically back to back and depending on the nature of the call or who I’m meeting with, I love the prompt by my Webex Assistant on my Webex Teams board that says “Hello Aruna, you have a call in five minutes, would you like to join?”, I simply answer “Yes.” and boom I’m in the meeting.
Even more surreal in the meeting is Facial Recognition, I can now see the name tags underneath the faces of the people I’m meeting with. How many times do we join a meeting and think, “Hmm who is that person in the blue shirt?”. Now with virtual tags, I know who is in the meeting and can address them by name when we converse.
#5 People Insights, the X-Factor in Webex Meetings
Another AI feature within Webex Teams I love is People Insights which adds an X-Factor to my meetings. Now before, during, or after a meeting, I can go one step further and hover over a name of a person and view a detailed profile with public information, such as their name, title, education, company and more will pop up, to help me connect on a more human and personalized level.
#6 AI Improving the Meetings Experience Through Voice Transcription
My final favorite AI combination is with Webex Meetings and Voice Transcription. During my meetings, my team and I rarely have time to take fast and furious notes to capture all that is going on, take action items and jot down key insights, but meetings just got better because Webex AI now has voice transcription! As a video meeting is taking place, we have a virtual assistant not only transcribing in real time, but can also transcribe in other languages, can take action items and can share out the meeting notes promptly after the call. I hope you are just as excited as we are for this added innovation.
The Awesome Power of Combinations
The way Webex + my mobile device, + offices devices, or + my life, just works, is an incredibly and invaluable collaboration tool, that helps me optimize my day in a magical way, like Rainbows and Unicorns.
When you think of the power of technology combined with the daily rhythm of our lives, we experience so much value no matter where we are in the world. To our British friends the magical relation might be Rugby and a Pint…
…or Tea and Scones.
To our Aussie friends the magical relation may be Meat Pie and Sauce…
…or Board Shorts and Thongs.
More than Design Thinking
These combinations bring a smile to our face, put a joy in our heart, and bring us so much happiness… There is an awesome and unexplainable thing that takes place when two or more people gather with their talents to create and ideate, where thoughts flow and dreams are realized; that’s the power of collaboration and we believe the best collaborations happen on Webex.
Our Brand Campaign The best collaborations happen on Webex
We are very excited to bring to market our new brand campaign, which will be launched in three geographies: US, UK and Australia. Just like coffee and doughnuts makes our mornings and how champagne and strawberries make our twilight hour… Webex, enables the best collaborations to happen when people come together, anywhere, anytime, on any device around the world.


Monday, 4 November 2019
Time to Get Ahead of the Wi-Fi 6 Upgrade Curve
Sometimes technical innovations strike like lightning. In a flash, shiny new tech arrives and is instantly put in the hands of millions of people. Other times innovations seem like the ocean tide. You can see the slow change coming as the waters incrementally rise, but you’re never quite sure at what point high tide arrives and you’re ready to jump in to ride the next wave.
Each generation of Wi-Fi arrives like the tide, slowly building up, not arriving all at once, but unstoppable nevertheless. Cisco has been preparing for Wi-Fi 6 for some time now. The standard is finalized. 802.11ax (aka Wi-Fi 6) certification of radios, access points, and controllers is underway. Manufacturers are busy incorporating Wi-Fi 6 chipsets into their new products.
Just a few generations of networking ago it was still common to have Ethernet cables in every office to connect desktop behemoths to the corporate network. As desktop PCs evolved into lightweight laptops, wireless connectivity quickly followed as the network of choice to take advantage of increasing mobility. The “app generation” came next with the BYOD wave of wireless smart phones and tablets that invaded the corporate network.
As mobility became a top priority, Wi-Fi took off in carpeted corporate spaces. Access points for Wi-Fi 4 (802.11n) and Wi-Fi 5 (802.11ac wave 1 and 2) sprouted from ceilings in every floor, conference room, and common area. In retrospect the move to wireless connectivity happened very quickly in terms of IT refresh cycles driven by a more mobile workforce requiring access to SaaS applications and IP streaming collaboration services, anytime, anywhere.
Now, Wi-Fi 6 devices are already appearing in people’s hands as progressive companies like Apple and Samsung lead with their next generation of phones. New laptops and tablets shipping today are incorporating Wi-Fi 6 as the new default, bringing the ability to run applications that require low latency and fast downloads—and uploads!—to enhance mobile computing. While Wi-Fi 6 devices will readily attach to older -ac or -n access points, the device owners will not notice any change in performance, resulting in a disappointing experience.
In the enterprise, collaboration applications are becoming a must-have platform to tie together the workforce in traditional carpeted spaces, campus meeting areas, and remote and mobile offices. The importance of keeping everyone on the same page as well as providing immediate connections from field to office is making high-definition video and audio streaming a critical capability that depends on quality wireless access anytime, anywhere.
For a satisfactory collaboration experience, the network needs to provide appropriate bandwidth to handle the up and down stream video transmission with low latency for multiple connections for each meeting. Latency management is specifically addressed in Wi-Fi 6 in a couple of ways. Multi-User Multiple Input Multiple Output (MU-MIMO) enables clients and APs to split the available spatial streams among multiple client devices for both up and down transmissions. Combined with Orthogonal Frequency Division Multiple Access (OFDMA), an RF modulation technique, Wi-Fi 6 enables multiple clients to simultaneously receive data during the same transmit opportunity.
These enhancements to Wi-Fi 6 enable better Quality of Experience (QoE) for collaboration platforms. As the use of video conferencing increases in an effort to decrease costly—and carbon-footprint heavy—travel, Wi-Fi 6 is ready to take on the extra load.
Upgrading to Wi-Fi 6 is particularly important for organizations with customer-facing applications that depend on public wireless access. Hospitality and retail enterprises want to interface with guests and customers via their mobile device of choice. In a hotel, for example, guests expect the same connectivity performance that they have in their corporate or home network. Superior network performance is a checkbox for repeat business, poor network performance results in a black mark.
In retail, customers want to use their mobile apps to find deals, send photos and videos of merchandise to friends, and use mobile payments. Deep inside a mall with weak LTE coverage, an overloaded Wi-Fi results in customer frustration and lost sales. For expansive indoor spaces, Wi-Fi 6 provides peerless coverage and roaming, fast onboarding, and the capacity to handle hundreds of connections simultaneously.
In the education environment, students visiting prospective campuses will immediately notice if the Wi-Fi coverage meets their expectations for performance. Students expect a flawless wireless experience in lecture halls—where everyone has laptops and mobile devices operating all at once—and demand that classwork files and videos can be instantly downloaded and streamed. In high-density environments like these, Wi-Fi 6 excels at meeting the demand for fast onboarding, stable connectivity, and low latency. Even in an environment with mixed Wi-Fi 5 and 6-capable devices, everyone benefits from the more efficient use of existing bandwidth if the access points are Wi-Fi 6 capable.
In these cases, the Wi-Fi 6 tide is in and it’s time to get your network up to date to keep up with customer, guest, and student expectations and take advantage of the latest innovation in wireless connectivity. To make wireless communications even more seamless, Cisco is in the process of rolling out OpenRoaming, which will make onboarding to wireless networks, that are part of the OpenRoaming Federation, automatic. It will also create a bridge between Wi-Fi and 5G networks to make the transition between the two transparent to the device. I will discuss this more in a future blog post.
Buildings are becoming smarter to increase energy efficiency while adapting the spaces to people and organizational needs. From motion-sensing lights and HVAC systems that adjust office spaces automatically, to built-in conferencing systems and smart whiteboards, IoT devices are permeating office, factory, retail, and healthcare spaces. The cost of adding smart IoT to existing spaces is reduced when many devices can communicate wirelessly instead of threading cables in every nook and cranny.
While the goal is to create a smart environment, many of the individual IoT devices are actually fairly simple, with limited local processing, security settings, and battery power. The wireless network, therefore, must provide security, management tools for visibility into device identities, and granular segmentation to control traffic flows as well as access permissions. The smart building requires an intelligent network to manage and safeguard all the components.
Fortunately, core technology built into Wi-Fi 6 addresses many of the challenges of connecting and managing smart buildings—and ultimately smart cities. With a multitude of sensors, cameras, and all vying for bandwidth, Wi-Fi 6 access points reduce interference using BSS Coloring, which enables devices to identify the closest AP by “color” and tune out all other transmissions from nearby APs and devices. The Target Wake Time capability enables devices to conserve battery power by coordinating sleep cycles with the local AP, so instead of connecting many times a minute, they can be set to wake and transmit less frequently and still maintain a connection when needed. Reduced latency is also an important requirement for IoT applications. Wi-Fi 6 reduces latency and jitter using Orthogonal Frequency Division Multiple Access (OFDMA), which enables many low-bandwidth streams to transmit in parallel.
Monitoring network performance, identifying device types, and securing wired and wireless devices is the function of Cisco Intent-based Networking components Cisco DNA Center, Identity Services Engine, SD-Access, and Assurance. These services running on top of Wi-Fi 6 capabilities create an intelligent wireless fabric to make the smart building a holistic collaboration of sensors, devices, access points, and controllers that are all securely managed from a central portal.
Whether your organization is expanding physically with new buildings, adding employees, moving to more cloud services, or wanting to interface more directly with customers through mobile apps, upgrading to Wi-Fi 6-based infrastructure will immediately provide many benefits and prepare for future growth. Cisco Wi-Fi 6 APs and Controllers will provide not only faster data transfers, but lower latency for much more responsive applications, as well as better performance in high-density environments—all areas that are improved from previous generations of Wi-Fi. Don’t get behind the curve, the time to start your upgrade to Wi-Fi 6 is now.
Wi-Fi 6 Devices are Populating Enterprise Carpeted Spaces Today
Just a few generations of networking ago it was still common to have Ethernet cables in every office to connect desktop behemoths to the corporate network. As desktop PCs evolved into lightweight laptops, wireless connectivity quickly followed as the network of choice to take advantage of increasing mobility. The “app generation” came next with the BYOD wave of wireless smart phones and tablets that invaded the corporate network.
As mobility became a top priority, Wi-Fi took off in carpeted corporate spaces. Access points for Wi-Fi 4 (802.11n) and Wi-Fi 5 (802.11ac wave 1 and 2) sprouted from ceilings in every floor, conference room, and common area. In retrospect the move to wireless connectivity happened very quickly in terms of IT refresh cycles driven by a more mobile workforce requiring access to SaaS applications and IP streaming collaboration services, anytime, anywhere.
Now, Wi-Fi 6 devices are already appearing in people’s hands as progressive companies like Apple and Samsung lead with their next generation of phones. New laptops and tablets shipping today are incorporating Wi-Fi 6 as the new default, bringing the ability to run applications that require low latency and fast downloads—and uploads!—to enhance mobile computing. While Wi-Fi 6 devices will readily attach to older -ac or -n access points, the device owners will not notice any change in performance, resulting in a disappointing experience.
Collaboration Applications Benefit from Lower Latency, Guaranteed Throughput
In the enterprise, collaboration applications are becoming a must-have platform to tie together the workforce in traditional carpeted spaces, campus meeting areas, and remote and mobile offices. The importance of keeping everyone on the same page as well as providing immediate connections from field to office is making high-definition video and audio streaming a critical capability that depends on quality wireless access anytime, anywhere.
For a satisfactory collaboration experience, the network needs to provide appropriate bandwidth to handle the up and down stream video transmission with low latency for multiple connections for each meeting. Latency management is specifically addressed in Wi-Fi 6 in a couple of ways. Multi-User Multiple Input Multiple Output (MU-MIMO) enables clients and APs to split the available spatial streams among multiple client devices for both up and down transmissions. Combined with Orthogonal Frequency Division Multiple Access (OFDMA), an RF modulation technique, Wi-Fi 6 enables multiple clients to simultaneously receive data during the same transmit opportunity.
These enhancements to Wi-Fi 6 enable better Quality of Experience (QoE) for collaboration platforms. As the use of video conferencing increases in an effort to decrease costly—and carbon-footprint heavy—travel, Wi-Fi 6 is ready to take on the extra load.
Customer Experience Depends on Quality of Wireless Service
Upgrading to Wi-Fi 6 is particularly important for organizations with customer-facing applications that depend on public wireless access. Hospitality and retail enterprises want to interface with guests and customers via their mobile device of choice. In a hotel, for example, guests expect the same connectivity performance that they have in their corporate or home network. Superior network performance is a checkbox for repeat business, poor network performance results in a black mark.
In retail, customers want to use their mobile apps to find deals, send photos and videos of merchandise to friends, and use mobile payments. Deep inside a mall with weak LTE coverage, an overloaded Wi-Fi results in customer frustration and lost sales. For expansive indoor spaces, Wi-Fi 6 provides peerless coverage and roaming, fast onboarding, and the capacity to handle hundreds of connections simultaneously.
In the education environment, students visiting prospective campuses will immediately notice if the Wi-Fi coverage meets their expectations for performance. Students expect a flawless wireless experience in lecture halls—where everyone has laptops and mobile devices operating all at once—and demand that classwork files and videos can be instantly downloaded and streamed. In high-density environments like these, Wi-Fi 6 excels at meeting the demand for fast onboarding, stable connectivity, and low latency. Even in an environment with mixed Wi-Fi 5 and 6-capable devices, everyone benefits from the more efficient use of existing bandwidth if the access points are Wi-Fi 6 capable.
In these cases, the Wi-Fi 6 tide is in and it’s time to get your network up to date to keep up with customer, guest, and student expectations and take advantage of the latest innovation in wireless connectivity. To make wireless communications even more seamless, Cisco is in the process of rolling out OpenRoaming, which will make onboarding to wireless networks, that are part of the OpenRoaming Federation, automatic. It will also create a bridge between Wi-Fi and 5G networks to make the transition between the two transparent to the device. I will discuss this more in a future blog post.
Smart Buildings and Connected IoT Will Flourish with Wi-Fi 6
Buildings are becoming smarter to increase energy efficiency while adapting the spaces to people and organizational needs. From motion-sensing lights and HVAC systems that adjust office spaces automatically, to built-in conferencing systems and smart whiteboards, IoT devices are permeating office, factory, retail, and healthcare spaces. The cost of adding smart IoT to existing spaces is reduced when many devices can communicate wirelessly instead of threading cables in every nook and cranny.
While the goal is to create a smart environment, many of the individual IoT devices are actually fairly simple, with limited local processing, security settings, and battery power. The wireless network, therefore, must provide security, management tools for visibility into device identities, and granular segmentation to control traffic flows as well as access permissions. The smart building requires an intelligent network to manage and safeguard all the components.
Fortunately, core technology built into Wi-Fi 6 addresses many of the challenges of connecting and managing smart buildings—and ultimately smart cities. With a multitude of sensors, cameras, and all vying for bandwidth, Wi-Fi 6 access points reduce interference using BSS Coloring, which enables devices to identify the closest AP by “color” and tune out all other transmissions from nearby APs and devices. The Target Wake Time capability enables devices to conserve battery power by coordinating sleep cycles with the local AP, so instead of connecting many times a minute, they can be set to wake and transmit less frequently and still maintain a connection when needed. Reduced latency is also an important requirement for IoT applications. Wi-Fi 6 reduces latency and jitter using Orthogonal Frequency Division Multiple Access (OFDMA), which enables many low-bandwidth streams to transmit in parallel.
Monitoring network performance, identifying device types, and securing wired and wireless devices is the function of Cisco Intent-based Networking components Cisco DNA Center, Identity Services Engine, SD-Access, and Assurance. These services running on top of Wi-Fi 6 capabilities create an intelligent wireless fabric to make the smart building a holistic collaboration of sensors, devices, access points, and controllers that are all securely managed from a central portal.
It Really is Time to Take Advantage of Wi-Fi 6
Whether your organization is expanding physically with new buildings, adding employees, moving to more cloud services, or wanting to interface more directly with customers through mobile apps, upgrading to Wi-Fi 6-based infrastructure will immediately provide many benefits and prepare for future growth. Cisco Wi-Fi 6 APs and Controllers will provide not only faster data transfers, but lower latency for much more responsive applications, as well as better performance in high-density environments—all areas that are improved from previous generations of Wi-Fi. Don’t get behind the curve, the time to start your upgrade to Wi-Fi 6 is now.
Sunday, 3 November 2019
Our World in Transition and Our Future Demands
October is Cybersecurity Awareness Month and for me, it’s a time to reflect on where we’ve been and how far we’ve come, study the trends and challenges we face today, and look ahead to the next generation of opportunities facing not only the security community, but society at large.
In my more than 30 years in the security industry, it’s been interesting to see how technology has evolved and changed the world. Security started off as a ‘systems’ conversation. Now, technology touches everyone’s lives, and as a result, cybersecurity affects us all – individuals, businesses, cities, countries, our global community.
During our lifetimes, we’ve shifted from using technology to, in very subtle ways, becoming reliant on it. Whether we realize it or not, these subtleties have made us dependent on technology. The notion of ‘always on’ access to data is highly disruptive to us when we don’t have it. Take maps for example: using a printed map is foreign to us today, and when the maps on our devices don’t work, we’re lost, literally.
When technology is unavailable, in many respects we feel ‘out of the loop’ and behind in knowing what’s going on. There’s a lagging indicator that says, ‘Now that we have access to current information, we always expect this level of connectivity – we depend on it.’ That reliance makes securing the data and the systems that deliver it to us that much more vital.
Since 2017, three major transitions have occurred that illustrate how complicated cybersecurity has become for us all globally. These transitions have caused security professionals to feel the pressure and scrutiny from a number of organizations that have upped their games. They’re having to catch up to a confluence of changes, all occurring at the same time:
1. Technology
Prior to 2017, IT predominantly built and ran an organization’s technology infrastructure, spending on security and hoping it works, relying on best-of-breed products, and managing it all reactively.
We all needed cybersecurity, but how could we net the best results – the greatest level of efficacy – from the solutions we purchased? Exactly how much value are we getting when spending on a solution? Is it all integrated as a best strategy or are we simply buying technology from the leading brand name or best advertised?
Today, leading IT teams build, buy and run security, use a ‘best-of-integrated’ architecture approach and emphasize visibility, controls, measures and proactive approaches to security that drive efficacy and value.
2. Laws, Regulations, and Customer Requirements
This transition shows the increasing influence that laws, regulations and customer requirements have on a technology or service provider to its clients, and in turn, to their customers, citizens, colleagues, families and friends.
The formalization of laws and regulations – from the EU-NIS Directive to GDPR to the Australian Government Protective Security Policy Framework to the California Consumer Privacy Act, to name a few – have driven greater scrutiny and reform. It’s accelerated substantially in a short period of time, from ‘do-it-yourself’ disharmonious regulations and rule, to a set of country, inter-country and international use standards.
Now corporate and government leaders across the international community are being held accountable. This transition from varying self-rule and self-regulation to accountability, breach reporting and disclosure highlights the implications of mishandling data and privacy through significant fines and executive firings.
In many respects, it’s been a long time coming. What’s interesting is that now that it’s here, it’s caught many off-guard – and it’s by no means slowing down.
3. Internal Oversight
When I started in InfoSec, security was mainly an engineering or computer science discipline. The security team was often avoided so that they couldn’t suppress innovation because of security concerns. The business was self-governing with inconsistent levels of oversight.
Today, internal reporting to and oversight by executive leadership, the CEO, the board of directors and shareholders are becoming standard practice to ensure proper governance. In part, it is a response to the regulatory landscape and the need for higher levels of accountability and oversight from within. It’s also based on the criticality of technology moving from something we use to something we rely on to deliver a service.
All three of these transitions came to the fore in a very short period of time to know how to effectively react, govern and solve for it. By the way, we’re all going through this and determining our own strategies to face the challenges, net the value they deliver, and understand how to be safe and secure in and around it all.
Our Future Demands
Today, there are about 4 billion internet users globally – all told about 10X of what it was in 2000. We’re in a world where everything is being connected and generating data. This will have significant impact on the next few years in particular and even more substantially into the future.
By next year, there will be about 200 billion devices ‘on air,’ which includes cars, telemetry in cities, sensors and a multitude of other connected devices. Two-hundred billion is almost an ephemeral number, but it’s not to be underestimated because the number of vendors creating IoT-connected technology is growing probably 3-4X every year than the prior year. That’s a trend that I don’t see slowing down any time soon.
By 2021, cybercrime is estimated to be a $6 trillion industry – a very profitable industry, though I don’t recommend it as a career choice. It does illustrate the depth and breadth of the challenge – that it’s an international and global issue that we all have to work together to solve because it’s something that we all face.
Raising the Bar for a More Secure Future
Governments and businesses globally are raising the bar to meet the challenge around product assurance, cloud assurance, IoT, lawful intercept, data protection, privacy and the like. Some 30-odd countries are writing or revising their cybersecurity strategies and each can have profound implications on how data is shared and how systems are built.
So, during Cybersecurity Awareness Month, consider what you can do to make the world more safe and secure, and take action. What can you do as individuals? How are you protecting yourself online and helping your business, colleagues, friends and family to do the same? Each individual act, when taken together, can move us all to a more secure future.
We’re not looking for headlines that show ‘good’ or ‘bad.’ We need trend lines that show that what we’re doing collectively is moving us all towards lower risk. As long as the trend line is going in the right direction, we’re doing what we need to do – and we must all do our part.
For governments, companies and individuals alike, Cisco’s Cybersecurity Awareness Month site offers events, activities and educational content, and ways to get involved. The Cisco Trust Center also offers resources to help you with security, data protection and privacy. Both feature links to security reports, videos, threat intelligence, thought leadership and more that will keep you informed.
From Use to Reliance
During our lifetimes, we’ve shifted from using technology to, in very subtle ways, becoming reliant on it. Whether we realize it or not, these subtleties have made us dependent on technology. The notion of ‘always on’ access to data is highly disruptive to us when we don’t have it. Take maps for example: using a printed map is foreign to us today, and when the maps on our devices don’t work, we’re lost, literally.
When technology is unavailable, in many respects we feel ‘out of the loop’ and behind in knowing what’s going on. There’s a lagging indicator that says, ‘Now that we have access to current information, we always expect this level of connectivity – we depend on it.’ That reliance makes securing the data and the systems that deliver it to us that much more vital.
A Confluence of Change – All in Three Years
Since 2017, three major transitions have occurred that illustrate how complicated cybersecurity has become for us all globally. These transitions have caused security professionals to feel the pressure and scrutiny from a number of organizations that have upped their games. They’re having to catch up to a confluence of changes, all occurring at the same time:
1. Technology
Prior to 2017, IT predominantly built and ran an organization’s technology infrastructure, spending on security and hoping it works, relying on best-of-breed products, and managing it all reactively.
We all needed cybersecurity, but how could we net the best results – the greatest level of efficacy – from the solutions we purchased? Exactly how much value are we getting when spending on a solution? Is it all integrated as a best strategy or are we simply buying technology from the leading brand name or best advertised?
Today, leading IT teams build, buy and run security, use a ‘best-of-integrated’ architecture approach and emphasize visibility, controls, measures and proactive approaches to security that drive efficacy and value.
2. Laws, Regulations, and Customer Requirements
This transition shows the increasing influence that laws, regulations and customer requirements have on a technology or service provider to its clients, and in turn, to their customers, citizens, colleagues, families and friends.
The formalization of laws and regulations – from the EU-NIS Directive to GDPR to the Australian Government Protective Security Policy Framework to the California Consumer Privacy Act, to name a few – have driven greater scrutiny and reform. It’s accelerated substantially in a short period of time, from ‘do-it-yourself’ disharmonious regulations and rule, to a set of country, inter-country and international use standards.
In many respects, it’s been a long time coming. What’s interesting is that now that it’s here, it’s caught many off-guard – and it’s by no means slowing down.
3. Internal Oversight
When I started in InfoSec, security was mainly an engineering or computer science discipline. The security team was often avoided so that they couldn’t suppress innovation because of security concerns. The business was self-governing with inconsistent levels of oversight.
Today, internal reporting to and oversight by executive leadership, the CEO, the board of directors and shareholders are becoming standard practice to ensure proper governance. In part, it is a response to the regulatory landscape and the need for higher levels of accountability and oversight from within. It’s also based on the criticality of technology moving from something we use to something we rely on to deliver a service.
All three of these transitions came to the fore in a very short period of time to know how to effectively react, govern and solve for it. By the way, we’re all going through this and determining our own strategies to face the challenges, net the value they deliver, and understand how to be safe and secure in and around it all.
Our Future Demands
Today, there are about 4 billion internet users globally – all told about 10X of what it was in 2000. We’re in a world where everything is being connected and generating data. This will have significant impact on the next few years in particular and even more substantially into the future.
By next year, there will be about 200 billion devices ‘on air,’ which includes cars, telemetry in cities, sensors and a multitude of other connected devices. Two-hundred billion is almost an ephemeral number, but it’s not to be underestimated because the number of vendors creating IoT-connected technology is growing probably 3-4X every year than the prior year. That’s a trend that I don’t see slowing down any time soon.
By 2021, cybercrime is estimated to be a $6 trillion industry – a very profitable industry, though I don’t recommend it as a career choice. It does illustrate the depth and breadth of the challenge – that it’s an international and global issue that we all have to work together to solve because it’s something that we all face.
Raising the Bar for a More Secure Future
Governments and businesses globally are raising the bar to meet the challenge around product assurance, cloud assurance, IoT, lawful intercept, data protection, privacy and the like. Some 30-odd countries are writing or revising their cybersecurity strategies and each can have profound implications on how data is shared and how systems are built.
So, during Cybersecurity Awareness Month, consider what you can do to make the world more safe and secure, and take action. What can you do as individuals? How are you protecting yourself online and helping your business, colleagues, friends and family to do the same? Each individual act, when taken together, can move us all to a more secure future.
We’re not looking for headlines that show ‘good’ or ‘bad.’ We need trend lines that show that what we’re doing collectively is moving us all towards lower risk. As long as the trend line is going in the right direction, we’re doing what we need to do – and we must all do our part.
For governments, companies and individuals alike, Cisco’s Cybersecurity Awareness Month site offers events, activities and educational content, and ways to get involved. The Cisco Trust Center also offers resources to help you with security, data protection and privacy. Both feature links to security reports, videos, threat intelligence, thought leadership and more that will keep you informed.
Saturday, 2 November 2019
How To Get Good Score in Cisco 300-135: CCNP Routing and Switching (TSHOOT) Certification Exam in Short Time
- Exam Name: Troubleshooting and Maintaining Cisco IP Networks
- Exam Number: 300-135 TSHOOT
- Exam Price: $300 USD
- Duration: 120 minutes
- Number of Questions: 15-25
- Passing Score: Variable (750-850 / 1000 Approx.)
- Exam Registration: PEARSON VUE
- Sample Questions: Cisco 300-135 Sample Questions
- Practice Exam: Cisco Certified Network Professional Routing and Switching Practice Test
- Recommended Training:
Artificial Intelligence: Leveraging Data from Edge to Cloud
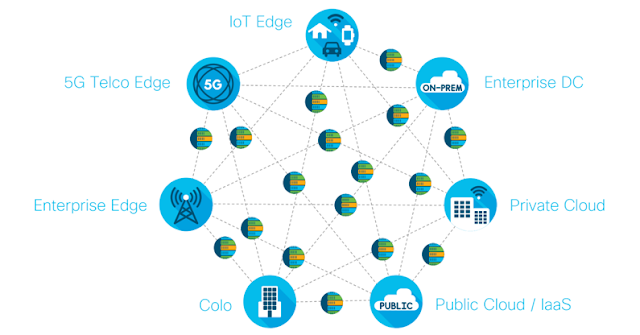
Artificial Intelligence (AI) will transform every industry, including government, by enhancing organizational effectiveness and speed of operation. But AI will also change the nature and pace of threats organizations will face. If we’re to achieve the full promise of AI and transform data into intelligence and action, we must lead with an insight driven approach to everything we do. In addition, we must take advantage of cognitive capabilities wherever possible. All while leveraging the full potential of data across private, hybrid and multicloud environments – from the edge to the cloud.
Artificial intelligence delivers insights when and where they are needed
To gain a competitive advantage, organizations need to start with a solid foundation, one that takes advantage of the best infrastructure options. This should include embedded analytics capabilities across edge, datacenter, and cloud environments. It should also include the capability to deliver insights when and where they are needed. And do so while incorporating continuous intelligence through real-time context. To unlock the strategic value of your data, you must have the ability to:
◒ Process and analyze data from distributed data sources
◒ Stream real-time data from edge devices
◒ Have the ability to store, analyze, apply AI/ML and deliver insight back to the edge devices to make intelligent decisions.
Artificial intelligence and cloud-scale architecture
At Cisco, we’ve been working on a cloud-scale architecture that brings together big data, compute farm, and storage tiers. They work together as a single entity yet scale independently to address IT and operational needs. Through this approach, we have created an architecture that enables:
◒ Extremely fast data ingest and data engineering done at the data lake
◒ An AI compute farm that allows for different types of AI frameworks and compute types (GPU, CPU) to work on this data for further analytics
◒ Gradual retirement of data that has been worked on to a storage dense system with a lower $/TB, providing a better TCO (storage tiering)
◒ To seamlessly scale the architecture to thousands of nodes with a single pane of glass management using Cisco Application Centric Infrastructure (ACI).
Cisco Data Intelligence Platform caters to this evolving architecture, bringing together a fully scalable infrastructure with centralized management, plus a fully supported software stack (in partnership with industry leaders in the space) to each of these three independently scalable components of the architecture, including data lake, GPU and object storage.
As you think about how to leverage artificial intelligence, ask yourself three key questions:
1. Are you architecting to enable your organization to drive value from data across environments?
2. Is your team ready to manage data spread across multiple clouds?
3. Will you be leveraging the full potential of your data?
Thursday, 31 October 2019
Remote Access Trojans
You’re working for a high-profile technology company, close to releasing a market-changing product to the public. It’s a highly contested space, with many competitors, both domestic and international. There’s also a lot of buzz in the media and online speculation on the scope and impact your new product will have. And it goes without question that customers are keen to know more about the upcoming game-changer.
Your goal is to keep the secrets under wraps until the public announcement. Unfortunately, your surprise is about to be spoiled. It happens sometimes, as much as we work to prevent it—from accidental embargo slips to insider leaks. But in this case, it’s arguably the worst-case scenario: Your company has been breached and information about the product was stolen.
It’s unfortunate, but such breaches are not an uncommon occurrence—it’s something security professionals are far too familiar with. They occur across sectors, yet the way the data is stolen often includes familiar patterns. There are plenty of possible suspects, and untangling their motives is difficult. But in this cybersecurity game of “Clue,” we’re less concerned if it were Mrs. Peacock or Professor Plum. We want to know what the weapon was and how to prevent future murders.
There are a variety of useful weapons in an attacker’s arsenal. Downloaders, administration tools, and infostealers all often play a part in such an attack. But the go-to tool in many scenarios like this today are remote access trojans, often referred to as a “RATs.”
A RAT is a swiss army knife of sorts. Distributed through familiar vectors, such as malicious downloads and email attachments, many RATs include all the weapons mention above, and more, making it easier for an attacker to leverage each component when carrying out an attack. In short, a RAT consolidates a number of tools into one package.
There is a lot of variation from RAT to RAT. Some are generalist tools, meant to be used across a variety of attack scenarios. Others are highly tailored to a specific attack. Some RATs use predetermined proxies to help mask an attacker’s ultimate location. Other RATs may leverage command-and-control (C2) infrastructure to do the same.
While the functionality and infrastructure used by a given RAT will differ, what follows are common features found within many RATs. To illustrate an attack, let’s take it back to our tech company breach, showing how an attacker can leverage a RAT to gain access to, and steal, sensitive files on your upcoming product.
Gather system information
The attacker managed to breach the defenses in your company using a phishing email that included a link to the RAT. However, that doesn’t mean that they will immediately know where they are on the network. They’ll naturally want to learn more about the computer they compromised. Is it an administrative assistant’s desktop, a laptop belonging to finance, or a web server? Performing reconnaissance on the system helps the attacker learn how deep into an organization they have penetrated, if they need to move laterally, or if they’re reached their intended target. Some reconnaissance tools even allow an attacker to scan other systems, gathering information about them.
Steal usernames and passwords
The attacker got onto one machine, but it wasn’t the intended target. They’d compromised a computer belonging to someone in the engineering group, but the materials they were after resided on a shared server. To move laterally, they may want to try searching for login credentials on the system they’ve already compromised. Many RATs include the ability to scrape saved and cached passwords, and once the usernames and passwords are in hand, the attacker can attempt to log into the shared server.
Log keystrokes
The attacker scanned the compromised computer looking for the login credentials, but no luck. Good news? Yes, but it’s only a minor setback. Many RATs include information-stealing components like keyloggers, meaning all the attacker has to do is enable it, and wait for the user of the compromised system to log into the shared server. When they enter login credentials, the attacker can capture them, and later attempt to log into the server themselves.
Download further malware
The attacker was able to obtain login credentials; however, their attempt to log in failed. (Perhaps your company uses multi-factor authentication?) To get to that shared engineering server, the attacker is going to have to call in reinforcements. They’ve identified a vulnerability on the shared server, and they need an attack toolkit to exploit it and gain access. Given how networks vary widely, many RATS include the ability to download further tools to assist them in gaining further access. In this case, the RAT operates like a downloader, pulling down an attack toolkit that allows the attacker to progress.
Accessing and uploading files
The attacker managed to gain access to the shared server, traversed its directory structure, and located documents that outline your new product’s features. The next step is to exfiltrate those files. Most RATs contain the ability to upload files to a predetermined location. This is often done with help of a proxy or through a C2 infrastructure, thus covering the attacker’s tracks as they steal the documents in question.
Recording audio, video, and taking screenshots
There may be times that an attacker isn’t satisfied with simply stealing design docs. Perhaps they obtained a slide deck, but it lacks context in certain slides. In order to learn more, they might want to return their attention to the initially compromised computer and have the RAT to record audio and/or video. The RAT might overhear the engineer speaking to a coworker or capture a video of a presentation meeting that discusses the product. RATs can often take screenshots as well, capturing critical documents on display.
This is just one scenario where a RAT could be used end-to-end in an attack. RATs can be used in other situations as well. For instance, what if an attacker is hoping to exfiltrate financial data? A RAT can be leveraged to scrape banking details from a compromised computer or collect credit card numbers using a keylogger.
What’s important to highlight is that most RATs provide command line access to the systems that have been compromised. If adequate administrative rights are gained on these computers, an attacker can use a RAT to do just about anything that he or she desires.
RATs have been around for a long time, and many prominent RATs have come and gone. Some recent RATs that have been prevalent on the threat landscape include Orcus RAT and RevengeRAT, which have been used by a variety of threat actors. Another commonly seen RAT is ExileRAT, which has been used in attacks with possible espionage-related motives, and shares a C2 infrastructure with the LuckyCat family of threats.
Not all RATs are built from the ground up either. Some are semi-legitimate tools, repurposed or reconfigured for malicious use. Two such examples include Imminent RAT and Remcos.
There are a number of attack groups monitored by Talos Intelligence that use RATs in their malicious campaigns. The SWEED threat actor often used Agent Tesla, the Panda threat actor has been seen dropping Gh0st RAT, and the Tortoiseshell group, who was recently caught scamming veterans, uses a RAT called IvizTech.
So the attacker managed to get into your network and obtain your product plans this time. How do you prevent them from doing it next time?
Fortunately, there isn’t anything particularly special about the way a RAT gets onto a system. They’re distributed in much the same way as other types of malware: they’re sent by email, dropped by droppers, set up as the payloads for exploit kits, along with other common attack vectors. Consider the following:
Your goal is to keep the secrets under wraps until the public announcement. Unfortunately, your surprise is about to be spoiled. It happens sometimes, as much as we work to prevent it—from accidental embargo slips to insider leaks. But in this case, it’s arguably the worst-case scenario: Your company has been breached and information about the product was stolen.
It’s unfortunate, but such breaches are not an uncommon occurrence—it’s something security professionals are far too familiar with. They occur across sectors, yet the way the data is stolen often includes familiar patterns. There are plenty of possible suspects, and untangling their motives is difficult. But in this cybersecurity game of “Clue,” we’re less concerned if it were Mrs. Peacock or Professor Plum. We want to know what the weapon was and how to prevent future murders.
There are a variety of useful weapons in an attacker’s arsenal. Downloaders, administration tools, and infostealers all often play a part in such an attack. But the go-to tool in many scenarios like this today are remote access trojans, often referred to as a “RATs.”
The anatomy of a RAT
A RAT is a swiss army knife of sorts. Distributed through familiar vectors, such as malicious downloads and email attachments, many RATs include all the weapons mention above, and more, making it easier for an attacker to leverage each component when carrying out an attack. In short, a RAT consolidates a number of tools into one package.
There is a lot of variation from RAT to RAT. Some are generalist tools, meant to be used across a variety of attack scenarios. Others are highly tailored to a specific attack. Some RATs use predetermined proxies to help mask an attacker’s ultimate location. Other RATs may leverage command-and-control (C2) infrastructure to do the same.
Gather system information
The attacker managed to breach the defenses in your company using a phishing email that included a link to the RAT. However, that doesn’t mean that they will immediately know where they are on the network. They’ll naturally want to learn more about the computer they compromised. Is it an administrative assistant’s desktop, a laptop belonging to finance, or a web server? Performing reconnaissance on the system helps the attacker learn how deep into an organization they have penetrated, if they need to move laterally, or if they’re reached their intended target. Some reconnaissance tools even allow an attacker to scan other systems, gathering information about them.
Steal usernames and passwords
The attacker got onto one machine, but it wasn’t the intended target. They’d compromised a computer belonging to someone in the engineering group, but the materials they were after resided on a shared server. To move laterally, they may want to try searching for login credentials on the system they’ve already compromised. Many RATs include the ability to scrape saved and cached passwords, and once the usernames and passwords are in hand, the attacker can attempt to log into the shared server.
Log keystrokes
The attacker scanned the compromised computer looking for the login credentials, but no luck. Good news? Yes, but it’s only a minor setback. Many RATs include information-stealing components like keyloggers, meaning all the attacker has to do is enable it, and wait for the user of the compromised system to log into the shared server. When they enter login credentials, the attacker can capture them, and later attempt to log into the server themselves.
Download further malware
The attacker was able to obtain login credentials; however, their attempt to log in failed. (Perhaps your company uses multi-factor authentication?) To get to that shared engineering server, the attacker is going to have to call in reinforcements. They’ve identified a vulnerability on the shared server, and they need an attack toolkit to exploit it and gain access. Given how networks vary widely, many RATS include the ability to download further tools to assist them in gaining further access. In this case, the RAT operates like a downloader, pulling down an attack toolkit that allows the attacker to progress.
Accessing and uploading files
The attacker managed to gain access to the shared server, traversed its directory structure, and located documents that outline your new product’s features. The next step is to exfiltrate those files. Most RATs contain the ability to upload files to a predetermined location. This is often done with help of a proxy or through a C2 infrastructure, thus covering the attacker’s tracks as they steal the documents in question.
Recording audio, video, and taking screenshots
There may be times that an attacker isn’t satisfied with simply stealing design docs. Perhaps they obtained a slide deck, but it lacks context in certain slides. In order to learn more, they might want to return their attention to the initially compromised computer and have the RAT to record audio and/or video. The RAT might overhear the engineer speaking to a coworker or capture a video of a presentation meeting that discusses the product. RATs can often take screenshots as well, capturing critical documents on display.
Other uses
This is just one scenario where a RAT could be used end-to-end in an attack. RATs can be used in other situations as well. For instance, what if an attacker is hoping to exfiltrate financial data? A RAT can be leveraged to scrape banking details from a compromised computer or collect credit card numbers using a keylogger.
What’s important to highlight is that most RATs provide command line access to the systems that have been compromised. If adequate administrative rights are gained on these computers, an attacker can use a RAT to do just about anything that he or she desires.
Notable RATs
RATs have been around for a long time, and many prominent RATs have come and gone. Some recent RATs that have been prevalent on the threat landscape include Orcus RAT and RevengeRAT, which have been used by a variety of threat actors. Another commonly seen RAT is ExileRAT, which has been used in attacks with possible espionage-related motives, and shares a C2 infrastructure with the LuckyCat family of threats.
Not all RATs are built from the ground up either. Some are semi-legitimate tools, repurposed or reconfigured for malicious use. Two such examples include Imminent RAT and Remcos.
There are a number of attack groups monitored by Talos Intelligence that use RATs in their malicious campaigns. The SWEED threat actor often used Agent Tesla, the Panda threat actor has been seen dropping Gh0st RAT, and the Tortoiseshell group, who was recently caught scamming veterans, uses a RAT called IvizTech.
To catch a RAT
So the attacker managed to get into your network and obtain your product plans this time. How do you prevent them from doing it next time?
Fortunately, there isn’t anything particularly special about the way a RAT gets onto a system. They’re distributed in much the same way as other types of malware: they’re sent by email, dropped by droppers, set up as the payloads for exploit kits, along with other common attack vectors. Consider the following:
- A good endpoint protection application is very useful in protecting against RATs. AMP for Endpoints blocks malware at point of entry, then detects, contains, and remediates advanced threats.
- Monitoring network traffic for unauthorized activity is also important. Cisco Stealthwatch is the most comprehensive visibility and network traffic security analytics solution that uses enterprise telemetry from the existing network infrastructure.
- Many RATs encrypt their traffic, as we discussed in last month’s Threat of the Month blog, so be sure you can monitor such traffic as well. Encrypted Traffic Analytics provides insight into threats in encrypted traffic, without the need for decryption, using network analytics and machine learning.
- Being able to connect to C2 domains is vital for many RATs to function. Blocking known malicious domains can go a long way in stopping a RAT in its tracks. Cisco Umbrella uses DNS to stop threats over all ports and protocols—even direct-to-IP connections—preventing connections to attacker’s servers.
- Multi-factor authentication products can prevent an attacker from logging into a system if they manage to obtain login credentials. Verify users’ identities with applications such as Cisco Duo.
- A good email security solution, as well as a strong network perimeter, will help to ensure that RATs are blocked outright. Cisco Email Security is your best defense against such attacks via email, while Cisco’s Next-Generation Firewall can stop attacks at the network boundaries.
- A web security appliance with data loss prevention (DLP) features will also assist in cases where a RAT gets in and is attempting to steal sensitive information through the network. The Cisco and Digital Guardian DLP solution is a high-performance, comprehensive security solution for data in motion.