Tuesday, 29 June 2021
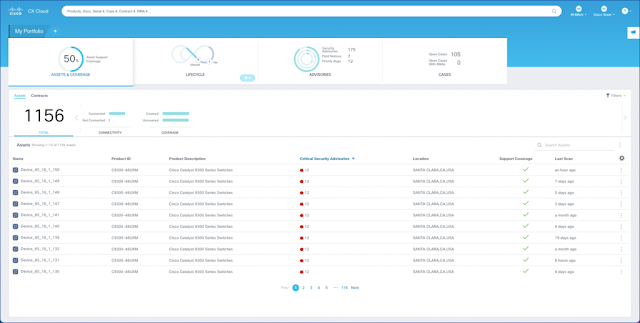
CX Cloud—expertise and insights at our fingertips
Monday, 28 June 2021
Enable Digital Transformation with Cisco SD-WAN
Cisco SD-WAN unlocks new possibilities with our network infrastructure, the new architecture is replacing the long-established role of the wide-area network (WAN), connecting our users at the branch office location to applications hosted on servers in the datacenters.
Often VPN (Virtual Private Network) tunnels or Multiprotocol Label Switching (MPLS) were implemented for segregation of data and security. This approached worked well for years, but as our customer moved into a mobile digital application world and their data move to the cloud, a new approached was required.
It’s a multi-cloud world
We live in a multi-cloud world, where using multiple clouds from multiple providers has become the new normal. Cisco SD-WAN has proven effective in helping Cisco partners accelerate their adoption of multi-cloud environments and drive business solutions for their customers. It helps them manage multiple network providers, ISP circuits, and connect branches to clouds. Cisco SD-WAN allows customers to deliver on-demand branch connectivity to their ISP and cloud providers directly from the SD-WAN controller.
Getting the details via developer experience
Are we doing this right though?
Saturday, 26 June 2021
Complete and continuous remote worker visibility with Network Visibility Module data as a primary telemetry source
Navigating the new normal
Organizations are currently facing new challenges related to monitoring and securing their remote workforces. Many users don’t always use their VPNs while working remotely – this creates gaps in visibility that increase organizational risks. In the past, many organizations viewed these occasional gaps in visibility as negligible risks due to low overall volumes of non-VPN-connected remote work. However, today, that’s no longer the case, as organizations and workers have been thrust into a new “work from home (WFH) era.”. This not only led to an explosion in the need for remote access from anywhere and on anything – effectively expanding threat surfaces and concurrently increasing opportunities for attackers – but – as if that weren’t enough – organizations were also hit with a wide-ranging and prolonged employee activity visibility blackout. This left security teams scrambling to adapt as this sudden “visibility blackout” further exacerbated overall organizational security risk levels.
Read More: 300-410: Implementing Cisco Enterprise Advanced Routing and Services (ENARSI)
Nostalgically remembering the good old days…
Back in olden times, circa late 2019 – back in the heydays of employee-activity visibility via on-premises network monitoring, and way, way back when people’s work-week routines involved commuting to the office, clocking in, logging onto the corporate network, and doing work in between water cooler breaks – organizations using Secure Network Analytics had absolute, total visibility into everything that their employees were doing. Back then, before the WFH era – security teams could instantly glean deep insights into practically everything that was being hosted within, interacting with, and connecting to their corporate networks. And despite these being simpler times, security teams still had to be incredibly agile, up to speed with rapidly changing and evolving technologies, and always ready to react to security incident-related fire drills at a moment’s notice.
Amidst the arms race that is network security, SecOps professionals must always be comfortable with high-pressure situations and fast-paced environments. It just comes with the territory. Plain and simple. It’s a job that requires a thick skin and continuous adaptation. I have always been impressed with security professionals’ ability to embrace such complexity and ambiguity, remain calm and collected, and just focus on the task at hand and execute. And I especially admire the ones that are naturally energized by their work and thrive on it. However, last year’s abrupt exodus away from corporate offices marked a paradigm shift that left even the best security teams in the dark and effectively lent a whole new meaning to the age-old adage, “the only constant is change”.
New WFH blind spots
To illustrate, in today’s new WFH era, whenever remote workers don’t use their VPNs, organizations are 100% blind to what their employees are doing. This prevents security teams from successfully establishing baselines of normal worker behavior and continuously monitoring them, concomitantly preventing them from being able to alert on anomalous activity and hindering their ability to detect certain types of threats. As a result, SecOps teams have been left in the dark and have been finding themselves asking questions like, have any of our users visited malicious URLs? Is anyone exfiltrating sensitive proprietary data? Have any users’ devices been unintentionally compromised and are now demonstrating command and control (C&C) activity? Are we facing compliance-related and broader organizational risks due to employees running outdated and vulnerable operating systems that need to be patched?
Obtaining complete and continuous remote worker visibility with NVM data
To adapt to this modern conundrum, Secure Network Analytics recent release 7.3.1 began to address this whole “WFH visibility blackout conundrum” by making endpoint Network Visibility Module (NVM) data a primary telemetry source to provide organizations with continuity in remote worker monitoring and visibility without requiring NetFlow telemetry to be present. But that was just phase 1 – now, with release 7.3.2, we’ve further extended this capability with the Data Store now supporting all NVM telemetry record collection to offer 100%-complete and continuous remote worker visibility. So now, whenever a user either works on-network or remotely – be it at home or a local coffee shop – and thus off-network without tunneling through a VPN, or if they are optimizing their remote work experience through split tunneling, all their activity is stored locally. With Network Visibility Module data being a primary telemetry source, whenever workers do eventually turn their AnyConnect VPNs back on, the NVM module phones home and sends logs of all their user activities back to Secure Network Analytics.
This gives security practitioners the continuity in visibility that they need by allowing them to monitor remote worker activities through the collection and storage of NVM endpoint records. Security teams can now gain visibility into activities that they were previously blind to, such as:
◉ Downloading and hoarding of large amounts of sensitive company data
◉ Data exfiltration or the sharing of sensitive company data to an external source
◉ Visiting malicious IP addresses and/or inadvertently installing trojans or other malicious processes
◉ Running older operating system versions with vulnerabilities that need patching
Et cetera. The list of potentially suspicious activities goes on, regardless of whether they are unintentional or motivated by an insider that has gone rogue.
Additionally, with Release 7.3.2, customers that are using NVM data along with a Data Store deployment are also gaining the following benefits:
◉ NVM telemetry records can be collected, stored, and queried in the Data Store
◉ New NVM reports that are now available in the Report Builder application
◉ The ability to define customized security events based on NVM data-specific criteria
◉ All Endpoint Concentrator functions are now fully managed by the Flow Collector
Extend the zero-trust workplace to anywhere on any device
Drastically comprehensive and context-rich visibility is simply table stakes in our “new normal”
Thursday, 24 June 2021
Cisco Nexus Dashboard: Cloud Operational Platform for Observability
One of the things that used to keep me up at night is that troubleshooting a data center network typically involved multiple disparate teams, each having a different view of the network, user interface, and the applications it supports. Historically, it took probing the network manually with complex questions and use the answers derived from custom scripting, spreadsheets, and CLIs for troubleshooting and remediation.
Read More: 300-815: Implementing Cisco Advanced Call Control and Mobility Services (CLACCM)
And with scaling into the multi-cloud in modern data center fabrics, the size and scope of deployments are growing into hundreds or even thousands of devices. This results in operational complexity, and the cost of managing these devices has exponentially grown as it takes longer to troubleshoot issues using multiple tools and methods. These multiple tools result in disparate user experiences that result in a lot of time and manual processing spent on troubleshooting and tracking critical network events across global networks. It often requires time to hone into misbehaving devices or collect and analyze data across multiple devices. That can result in downtime which quickly becomes expensive.
Traditional data center network management tools and approaches assume a velocity and volume of change that is well below what is enabled by the cloud and is unable to meet the demands of cloud native applications and digital business.
Cisco Nexus Dashboard is designed to automate, monitor, and analyze your network infrastructure. Innovative architectural approaches were implemented to provide automation and visibility at scale. Nexus Dashboard Insights simplifies operations for our customers with a modern, stateless microservices architecture that can scale horizontally, leveraging open-source infrastructure code. Insights delivers dynamic correlation, impact analysis, proactive alerts, failure prediction, and remediation, along with operational data visualization. These capabilities help consolidate the number of operational tools needed and reduces application downtime, Mean Time to Identify (MTTI), Mean Time to Resolution (MTTR), and the operating costs.
Driving automation and visibility at scale
Here are the key architectural components of the Nexus Dashboard Insights architecture:
Collectors: Nexus Dashboard Insights incorporates universal telemetry collectors. These collectors support multiple input plugins for collecting software and hardware telemetry data streamed from networking infrastructure devices like routers, switches, firewalls, and load balancers.
Data lake: Insights pipeline supports data encoded in JSON or GPB, which gets transformed and stored in a data lake for further processing. Telemetry data from legacy devices that do not support streaming telemetry is retrieved using REST API or SSH and then put into the pipeline for transformation.
Analytics Engine: The analytics engine pipeline uses a serverless compute model. It handles tasks such as data enrichment, anomaly detection, data aggregation, and resource scoring by splitting them into modular tasks with associated task specifications. These tasks are processed independently, and the results are saved in the distributed data lake.
Architecture for deep visibility and operational simplicity
Tuesday, 22 June 2021
Power of Cloud Application Centric Infrastructure (Cloud ACI) in Service Chaining
It is a reality that most enterprise customers are moving from a private data center model to a hybrid multi-cloud model. They are either moving some of their existing applications or developing newer applications in a cloud native way to deploy in the public clouds. Customers are wary about sticking to just a single public cloud provider for fear of vendor lock-in. Hence, we are seeing a very high percentage of customers adopting a multi cloud strategy. According to Flexera 2021 State of the cloud report, this number stands at 92%. While a multi cloud model gives customers flexibility, better disaster recovery and helps with compliance, it also comes with a number of challenges. Customers have to learn not just one, but all of the different public cloud nuances and implementations.
More Info: 352-001: CCDE Design Written Exam (CCDE)
Navigating the different islands of public cloud
Load Balancers and More!
Unleash the power of service chaining
Monday, 21 June 2021
Top 10 CCNA 200-301 Exam Preparation Tips: Key to Success
When applying for any IT job position in comparison with numerous candidates, it is important to confirm extra qualifications for the role. Achieving a relevant certification is believed to be an amazing way to do so. This would be because recruitment manager view them as evidence of skills so signs for more reliable performance. If you are looking for some useful study methods concerning the CCNA 200-301 Exam, we have mentioned them below, but first, let’s explore the exam outline.
Essential Information of the CCNA 200-301 Exam
A vital step in preparing for any exam is to determine the list of the themes to be included. And the more comprehensive it is, the more consideration you should pay to this chapter. Regarding Cisco 200-301 exam, you can find a complete outline on Cisco’s official website. On the whole, the areas you’ll be evaluated on involve networking basics, IP connectivity and IP services, programmability, network access, and so on. At this step, it’s also essential to know what types of questions you will face, how much time you’ll be given, and how to ace the exam.
Sunday, 20 June 2021
Cisco Secure: Supporting NIST Cybersecurity Framework
Extending the alignment to include more Cisco products
Why should you care? With so many security frameworks, it can be difficult to know where to start from. While many organizations are challenged with managing and improving their cybersecurity programs against the dynamic threat landscape, it’s not easy to pick one framework over another. So where do they start from – ISACA COBIT 5? ISO27000 series? CIS CSC? NIST CSF? SABSA? Or something else? National Institute of Standards and Technology (NIST) developed the Cybersecurity Framework (CSF) exactly for this reason. It’s a simple, best-practices approach to Cybersecurity leveraging the specific standards that are widely used and already working well today.
Basics First
NIST CSF is a voluntary framework based on existing standards, guidelines and practices for reducing cyber risks. It enables organisations to discuss, address and manage cybersecurity risk.
More Info: 350-901: Developing Applications Using Cisco Core Platforms and APIs (DEVCOR)
◉ It is used to manage cybersecurity risks in a cost-effective way while protecting privacy
◉ It references the globally accepted standards (COBIT, ISO/IEC, ISA, NIST, CCS)
◉ It enables all organizations (large or small) to improve security and resilience
◉ 3 pillars – People, Process, and Technology – Each of these are important
◉ Only half of the CSF Categories are addressed by technology
◉ It emphasizes the importance of two other main pillars of Cybersecurity – People and Process
The Cybersecurity Framework consists of three main components: the Core, Implementation Tiers, and Profiles but for today’s discussion, we will focus only on Core which is a ‘set of activities and outcomes using a language that is easy to understand.
How CSF Core makes lives easier?
The CSF Core consists of four components as shown in the table below. The CSF Core provides a set of activities to achieve specific cybersecurity outcomes. It also gives guidance on how to achieve those outcomes. The table below lists each of these components with a short description and example: