You have not seen or heard of Cisco DNA Center. While they have done an impressive job with Cisco DNA Center- the talk is often about the technical merits, intents and functions. As we talk of cross domain, I want to cross the domain from what Cisco DNA Center does to why you should move to the solution in terms of business outcomes and user experience.
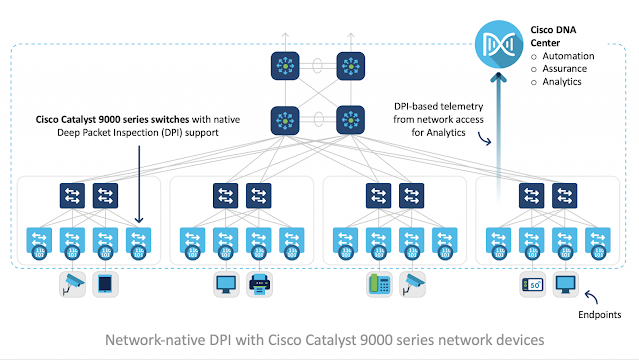
Recently there has been a lot of talk about Prime Infrastructure to Cisco DNA Center migration. It is important to call-out that while Prime Infrastructure is a network management/monitoring tool, Cisco DNA Center is a platform that does so much more — helping companies accelerate their digital transformation by providing insights, automation, and security across their networks in new and innovative ways.
So why should we move our IT organization to Cisco DNA Center? Part of my answer is that if you want to continue to run IT as we did 10 to 15 years ago – Prime Infrastructure will suit you just fine. However, if you are in a business that is growing, actively working on its digital transformation, grappling with hybrid work, wanting to leverage artificial intelligence and machine learning, or overall want to be more efficient, then you should read on.
Just as we see electric cars redefining transportation, Cisco DNA Center is redefining enterprise infrastructure software and network management. It is transforming infrastructure organizations across so many different use cases and personas including AIOPS, NETOPS, SECOPS, and DEVOPS which is no small endeavor.
In talking to various CIO’s and IT leaders, a common question comes up; “How do I turn IT into a competitive advantage for my organization?”. I interpret the question to be, “How do I use my IT infrastructure to drive business outcomes?” It is my belief that there are countless opportunities to differentiate depending on your industry sector.
My top 5 reasons why your organization would benefit from Cisco DNA Center:
Your Reputation
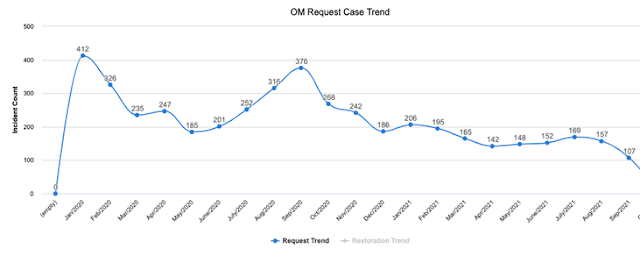
Reputation is critical. An IT organization’s reputation comes from delivery of services and uptime. As network infrastructure has reached the status of utility – everyone expects to have the infrastructure up and running 24/7, anything less than that can hurt the organizational reputation. The fact that Cisco DNA Center can help prevent outages and drastically shorten Mean Time to Resolution (MTTR) directly contributes to reputation. At the University, we are proud of the reputation our IT department has established and it is in large part due to the success we have had with Cisco DNA Center.
Visibility
Visibility; It is impossible to manage that which you can not see. As today’s infrastructure is everywhere, especially with the proliferation of wireless and IoT, visibility into the network with streaming telemetry enhances IT’s ability to monitor and manage the infrastructure. With AI/ML it enables visibility not possible before. As an innovative University IT, with Cisco DNA Center, we have gained tremendous new insights into the health of our entire network estate infrastructure previously not possible with Prime Infrastructure.
Automation
Automation and orchestration is something a lot of IT organizations talk about, but largely speaking, it is more commonly seen managing cloud applications, not network infrastructure. Cisco DNA Center helps with automation workflows which saves time, effort, and creates consistency across the infrastructure and can help eliminate operator errors, the leading cause of outages. The IT staff is so much happier not having to worry about making errors when doing high volume or highly repetitive tasks.
User Experience
User Experience is king – if your IT team does not have a way to measure and track the user experience, it is hard to deliver what you can’t measure. That being said, there are a plethora of different ways to track and measure wired and wireless user experience with Cisco DNA Center. Measuring user experience with Cisco DNA Center is a topic unto itself and warrants its own blog, so stay tuned for that. But so far, our student, faculty, and guest user experience has been dramatically improved since using Cisco DNA Center.
Proactive Management/Actions
Proactive Actions – The fact is that “IT” is a service organization and as we strive to perform service improvement – we make every effort to become more and more proactive. Cisco DNA Center has been able to redefine proactive AI/ML and the ability to identify early stages of failures and allow notification and intervention before it becomes a user-impacting event.
The Machine Reasoning Engine (MRE) is another capability that leverages artificial intelligence (AI) to automate complex network operation workflows. It is like having a 30-year Cisco veteran standing behind your shoulder when you are trying to solve a difficult problem by automatically troubleshooting the issues, identifying the most probable root cause, and providing the recommended corrective action. The MRE is powered by a cloud-hosted knowledge base, built by Cisco, and will progressively give you more and more options to not only automatically troubleshoot issues, but to automatically resolve and remediate them as well.
Security
Information/Cyber security is one of the holy grails of IT. I am guessing many struggle with what is more important, user experience or information security. The good news is that they are complementary with Cisco DNA Center. Cisco DNA Center can help keep the network in compliance with software, best practices, and security advisories. It can also provide visibility to the InfoSec department about the security posture of the infrastructure. To top the icing on the cake, Cisco DNA Center is also able to install hot patches on equipment with IOX-SE without system reloads. This is huge from the aspect that we can react quickly to security remediation when we can do it without having to take downtime.
I know I said top five – but it worked itself into a Top 6 list. The reality is that I can go on and on as with each new release of Cisco DNA Center, there are tons of new features, workflows and innovations added to the platform. Deploying Cisco DNA Center into an organization and realizing its full potential can take some time and effort – but it is super easy to get started and start seeing value right away. There is also an abundance of resources to help your organization achieve its goals and progressively add capabilities at the pace that makes sense to your organization. But rest assured, it will improve how your organization operates and functions and can really add significant business value across your business.
To that end, I wanted to conclude with some tangible business value and benefits that organizations can yield from Cisco DNA Center. As always your mileage may vary (YMMV) depending on your organization.
Ticket Resolution Time (MTTR metric)
◉ Wireless Issue investigation time reduced to minutes; estimated time reduction is 75% from using Prime for the same task.
◉ Ability to use Cisco DNA Center to restore configuration to/from switching hardware failures, reduced hardware recovery time by 50%.
◉ MRE (Machine Reasoning Engine) empowers more Junior-level staff to troubleshoot issues further reducing support costs by 30%.
Reduction in Tickets
Within 90 days of activity using Cisco DNA Center assurance to optimize the network, we have seen:
◉ 50% reduction in wireless trouble tickets
◉ Failure detection (power supplies, SFPs) enabling more proactive repair and eliminating troubleshooting through proactive management. 100% reduction for preventable failures from component failures.
Cost Savings/Operational Efficiency improvements
◉ Switch Software upgrades (SWIM) processes resulting in 75% reduction in engineering time, which also translates to 75% savings in labor hours.
◉ Overall team efficiency – with the Cisco DNA Center tools and automation, more Junior-level staff are now able to perform tasks (MRE, visibility), yielding 20% reduction in operations support costs through annual salary savings.
Business Confidence
◉ Sensor data from the 1800s provides a comprehensive view of measured user experience not previously possible.
◉ Security Assessment due to software version not previously automated. This not only reduces the effort but more importantly helps ensure security related compliance previously not attainable with existing staffing levels.
Source: cisco.com