IDC recently had the opportunity to talk to CISOs regarding the integration of Cisco Secure Workload and Secure Firewall. As analysts, we can articulate the technical benefits. The realized benefits can be different when real-life budget and time constraints are applied. Our conversations were quite illuminating. Below are 5 realities that may or may not surprise you when it comes to integrating perimeter and internal defenses:
1. Time is the currency of the day—Ransomware, cryptomining, and supply chain attacks are top of mind until we get into the office; business needs drive the fires to be fought during the day. The ever-present need to move quickly to stay ahead of cybercriminals require tools to “just work. ” According to the CISOs we spoke with, “if you’re limited on funds and don’t have a 20-person security team, you have to do a lot quickly…being able to get these overlapping protections…and they’re talking to each other really shines.”
2. Perimeter and internal defenses is not an “either-or” issue; it is an “and” issue—Firewalls have a prime vantage point, being able to observe all traffic traversing into and out of our infrastructure. But internal defenses are a bit more complicated. Digital transformation though does not wait for pristine security measures and policies to be put in place. Rather, digital transformation can force us to wrap devices or application like workloads and IoT devices in zero-trust policies elegantly or inelegantly; digital transformation does not care. According to the CISOs, “For organizations like hospitals that have IoT devices and new technologies, it’s going to be hard to wrap policies around all those devices. You’ve got some new scanner or a new handheld; how can you protect and lock them down? Maybe you can’t put an agent on some of them. So in a situation like that, with this [Secure Workload + Secure Firewall integration] you can wrap a zero trust policy around securing all those devices.”
3. Integration is real—Let’s acknowledge the elephant in the room; vaporware is a word for a reason. In this instance though, the integration of perimeter and internal defenses is actually happening already. The integration is going beyond a single pane of glass management console and being driven by a real need to solve real problems. According to the CISOs, “You can get that data from the firewall and then you can use that data to wrap a Tetration [Cisco Secure Workload] workload protection policy around those, even without an agent on there.”
4. Integration enables automation—Time poverty is omnipresent. The holy grail of security is automation, which isn’t possible without deep integration. According to the CISOs, “I can have one block list in SecureX. When I right click on an IP address or SHA-256, I’ve got some automation set up and block it at the AMP level, the firewall level, and a number of places, Stealthwatch…everywhere.”
5. “One throat to choke”—Budget, time and management constraint are real and painful. The CISO of a top 10 bank may not serve these masters, but the CISOs with whom we spoke do. Deeper discounting, simplified buying process, and a “one throat to choke” are intangible, but invaluable benefits of integration. According to the CISOs, “With one company, it makes it a lot easier to get people to work together.”
Integration is a key aspect of digital transformation, and in the security realm can mean the difference between an intrusion attempt and a data breach. However, integration has to mean more than simple co-existence. True integration will improve workflows, productivity, and security outcomes. The level of integration between perimeter and internal defenses may well be the difference maker, as CISOs continue to navigate new and emerging threats, technologies, and business requirements.
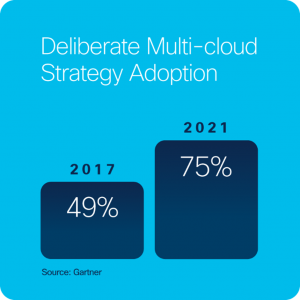
Source: cisco.com