Tuesday, 5 March 2024
Improved Area Monitoring with New Meraki Smart Cameras
Saturday, 2 March 2024
Showcasing Powerful Private 5G Use Cases at Cisco Live EMEA!
- Mobile broadcasting – wireless video crews roamed the exhibition halls with low latency and high bandwidth, delivering a streamlined multi-camera environment.
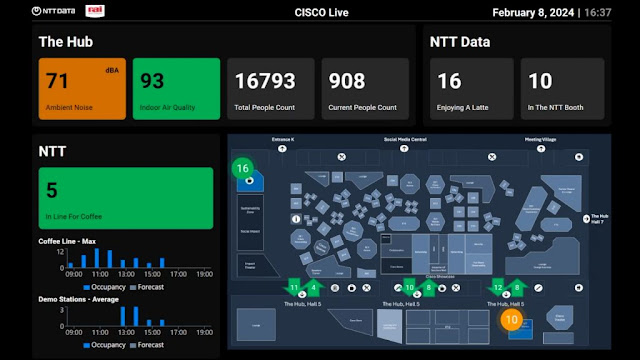
- Visitor traffic management – Cisco’s Meraki cameras and NTT DATA’s Smart Management Platform tracked visitor movements and congestion, enabling operations and security teams to communicate real-time, data-driven crowd control decisions.
- Emergency Response Vehicle (ERV) – Pre-packaged, flexible FWA Private 5G connectivity was setup and used to mimic rural cellular/satellite backhaul.
- Premium Booth Connectivity – When the booth is already built and the floor is laid, network cable cannot be raised. P5G provided booth broadband for the exhibitor.
- NTT Coffee Booth – Cisco’s Meraki cameras and the NTT DATA’s Smart Management Platform monitored and managed queues and seating to optimize the on-site experience.
- Enhanced exhibitor experiences – Cisco’s Meraki cameras embedded throughout the venue and in booths captured anonymized data including the number of visitors and time spent in the booth to use for planning and to create better customer experiences.
- Out of Band management – The Private 5G network, backhaul connectivity, and network operations center were integrated to provide the Cisco Live! events team with faster coordination and emergency response capabilities.
- Venue Safety – Machine vision detected whether individuals were wearing Personal Protection Equipment (PPE) through a real-time alert system, helping to ensure safety throughout the convention center’s facilities.
Thursday, 29 February 2024
Evolution to 5G-Advanced and Beyond: A Blueprint for Mobile Transport
Wireless trends and opportunities
Preparing your mobile transport for 5G Advanced and beyond
- Converged infrastructure: Cisco’s approach involves a unified infrastructure seamlessly integrating various network services across wireline and wireless domains. This convergence is essential for supporting diverse customer types and services, from consumer-focused mobile broadband to enterprise-level solutions. The infrastructure is designed to handle all kinds of access technologies on a single network platform, including 4G, 5G, FWA, and the emerging direct satellite-to-device connectivity outlined in 3GPP’s NTN standards.
- Programmable transport and network slicing services: At the heart of Cisco’s architecture are advanced transport technologies like Border Gateway Protocol (BGP)-based VPNs and segment routing (SR), crucial for a unified, packet-switched 5G transport. These technologies enable a flexible services layer and an efficient underlay infrastructure. This layering provides essential network services like quality of service (QoS), fast route convergence, and traffic-engineered forwarding. Network slicing is also a key feature, allowing operators to offer customized, intent-based services to different user segments. This capability is vital for monetizing 5G by enabling diverse and innovative use cases.
- Cloud-ready infrastructure: Recognizing the shift toward cloud-native applications and services, Cisco’s architecture is designed to support a variety of cloud deployments, including public, private, and hybrid models. This flexibility ensures that the transport network can adapt to different cloud environments, whether workloads are on-premises or colocated. Virtual routers in the public cloud play a significant role here, providing required IP networking functions (including BGP-VPN, SR, and QoS).
- Secure and simplified operations model: Security and operational simplicity with service assurance are essential components in Cisco’s architecture. The network is designed for easy programmability and automation, which is essential for operational efficiency and cost reductions. This includes extensive telemetry and open APIs for easy integration with orchestration tools and controllers. Additionally, AI and machine learning technologies can potentially be used for real-time network visibility and actionable insights for optimizing user experience across both wireline and wireless networks.
Tuesday, 27 February 2024
The Real Deal About ZTNA and Zero Trust Access
ZTNA hasn’t delivered on the full promise of zero trust
Classic ZTNA drawbacks
- Is there a method to keep multiple, individual user to app sessions from piggybacking onto one tunnel and thus increasing the potential of a significant security breach?
- Does the reverse proxy utilize next-generation protocols with the ability to support per-connection, per-application, and per-device tunnels to ensure no direct resource access?
- How do you completely obfuscate your internal resources so only those allowed to see them can do so?
- When do posture and authentication checks take place? Only at initial connection or continuously on a per session basis with credentials specific to a particular user without risk of sharing?
- Can you obtain awareness into user activity by fully auditing sessions from the user device to the applications without being hindered by proprietary infrastructure methods?
- If you use Certificate Authorities that issue certs and hardware-bound private keys with multi-year validity, what can be done to shrink this timescale and minimize risk exposure?
- The solution has a unified console enabling configuration, visibility and management from one central dashboard.
- Remote and hybrid workers can securely access every type of application, regardless of port or protocol, including those that are session-initiated, peer-to-peer or multichannel in design.
- A single agent enables all private and internet access functions including digital experience monitoring functions.
- The solution eliminates the need for on-premises VPN infrastructure and management while delivering secure access to all private applications.
- The login process is user friendly with a frictionless, transparent method across multiple application types.
- The ability to handle both traditional HTTP2 traffic and newer, faster, and more secure HTTP3 methods with MASQUE and QUIC
Cisco Secure Access: A modern approach to zero trust access
- To protect your hybrid workforce, our ZTA architectural design has what we call ‘proxy connections’ that connect one user to one application: no more. If the user has access to several apps as once, each app connection has its own ‘private tunnel’. The result is true network isolation as they are completely independent. This eliminates resource discovery and potential lateral movement by rogue users.
- We implement per session user ID verification, authentication and rich device compliance posture checks with contextual insights considered.
- Cisco Secure Access delivers a broad set of converged, cloud-based security services. Unlike alternatives, our approach overcomes IT complexity through a unified console with every function, including ZTA, managed from one interface. A single agent simplifies deployment with reduced device overhead. One policy engine further eases implementation as once a policy is written, it can be efficiently used across all appropriate security modules.
- Hybrid workers get a frictionless process: once authenticated, they go straight to any desired application-with just one click. This capability will transparently and automatically connect them with least privileged concepts, preconfigured security policies and adaptable enforcement measures that the administrator controls.
- Connections are quicker and provide high throughput. Highly repetitive authentication steps are significantly reduced.
Tuesday, 20 February 2024
Agniane Stealer: Information stealer targeting cryptocurrency users
Introduction
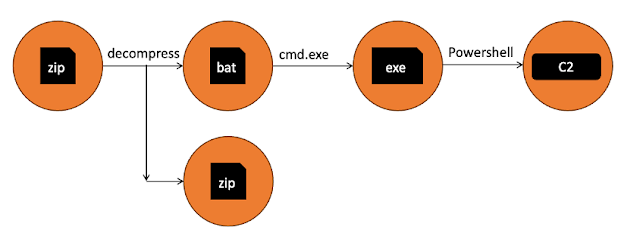
Execution Chain
- Reads the content of the previously extracted BAT file (passbook.bat).
- Through string matches and replacements, builds the payload dynamically and assigns it to a variable.
- Converted payload and static key from Base64 to a byte array.
- XOR’d the payload using a static key.
- Decompressed XOR’d payload using GZIP.
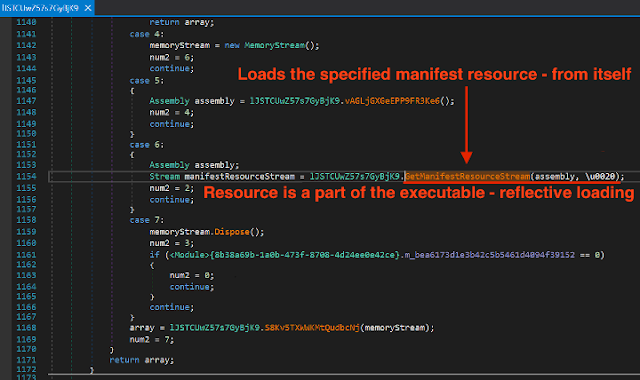
- Invokes payload after reflectively loading it into memory.
Binary Analysis
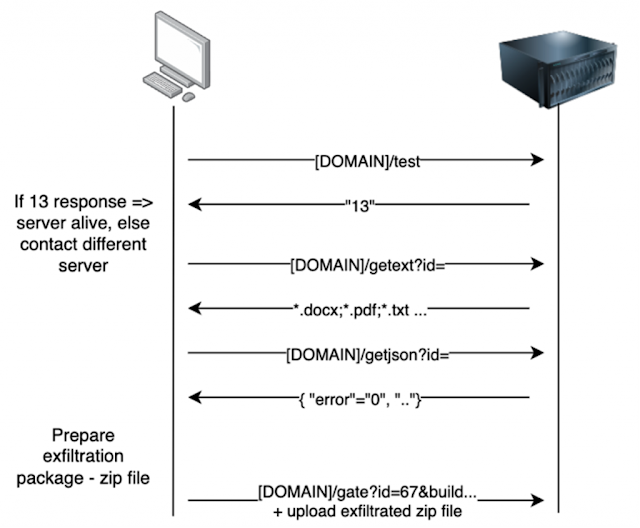
Command and Control
Other TTPs
- Enumerating registry key HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Uninstall for installed applications, it also collects this information.
- Checking for a public IP on a ip-api.com, i.e, https://ip-api.com/json/?fields=11827
- Dumping Bitcoin and other cryptocurrency wallets
- Performing (not well) checks to see if it’s running in a debugged or virtual env. etc.
- Collecting wallet.dat files.
- Enumerating Profile and User data.
- Collecting stored credit cards.
- Adding other malware like NGenTask.exe.log (the file with the SHA cf342712ac75824579780abdb0e12d7ba9e3de93f311e0f3dd5b35f73a6bbc3).
Monday, 19 February 2024
The Ultimate Study Tips to Prepare For Cisco 300-815 CLACCM Exam
Cisco 300-815 CLACCM Exam Details
Implementing Cisco Advanced Call Control and Mobility Services v1.0 (CLACCM 300-815) is a 90-minute exam with 55-65 questions. The core topics in the exam include:
Exam Preparation Tips: Navigating the 300-815 CLACCM Terrain
Preparing for the 300-815 CLACCM exam requires a strategic approach. Here are invaluable tips to guide you through the preparation process.
1. Understand the Cisco 300-815 CLACCM Exam Format
Before diving into your study sessions, take the time to familiarize yourself with the structure and format of the 300-815 CLACCM exam. Understanding the types of questions, exam duration, and scoring criteria will help you tailor your preparation effectively.
2. Create a Study Schedule
Efficient time management is vital to exam success. Draft a study schedule that allocates dedicated time slots for each exam topic. Breaking down your learning sessions into manageable chunks will impede overwhelm and assure complete coverage of all exam domains.
3. Utilize Reliable Resources
Equip yourself with high-quality study materials and resources tailored specifically for the 300-815 CLACCM exam. From official Cisco guides to reputable online courses and practice tests, leveraging reliable resources will enhance your understanding of exam concepts and boost confidence.
4. Hands-On Practice
Theory is essential, but practical application solidifies comprehension. Use lab environments or virtual simulations to reinforce your theoretical knowledge with hands-on practice. Experimenting with real-world scenarios will enhance retention and problem-solving skills.
5. Stay Updated with Cisco 300-815 CLACCM Exam Topics
The networking field is constantly evolving, and exam content reflects these changes. Stay abreast of the latest developments, technologies, and industry trends related to the 300-815 CLACCM exam. Subscribe to relevant blogs, forums, and newsletters to remain informed.
6. Join Study Groups
Engage with fellow exam candidates by joining study groups or online forums dedicated to the 300-815 CLACCM exam. Collaborating with peers allows for knowledge sharing, peer support, and the opportunity to discuss difficult topics or practice questions.
7. Practice Time Management
Simulate exam conditions by taking practice test on nwexam to refine your time management skills. Set timers for practice exams or question sets to ensure you can complete tasks within the assigned timeframe. Practicing under time pressure will help minimize exam-day stress.
8. Review and Revise Regularly
Consistent revision is crucial for long-term retention and mastery of exam content. Schedule regular review sessions to boost learning and identify areas that require further attention. Utilize techniques such as flashcards or summarization to aid recall.
9. Focus on Weak Areas
Identify your weak areas through practice tests or self-assessment quizzes and prioritize them in your study plan. Allocate additional time and resources to topics where you feel less confident, ensuring a well-rounded understanding of all exam domains.
10. Maintain a Positive Mindset
Approach the 300-815 CLACCM exam with a positive mindset and confidence in your abilities. Visualize success, stay motivated, and maintain a healthy balance between study and relaxation. Remember, a positive attitude can significantly impact performance on exam day.
The CCNP Collaboration Certification: A Gateway to Excellence
The CCNP Collaboration certification isn't just a badge; it's a testament to your proficiency in deploying, configuring, and troubleshooting Cisco collaboration and unified communication solutions. Let's unravel the benefits that await those pursuing this prestigious certification.
Elevate Your Expertise in Collaboration Technologies
Becoming a CCNP Collaboration certified professional signifies a deep understanding of the latest collaboration technologies. This certification ensures you are well-versed in the tools that power modern workplaces, from voice and video communication to conferencing solutions.
Open Doors to Career Advancement
In the competitive realm of IT, a CCNP Collaboration certification is a key that unlocks doors to new career opportunities. Employers value the expertise and skills it represents, making you a sought-after professional in the job market.
Join the Elite League of Networking Professionals
With the CCNP Collaboration certification, you don't just earn a title; you join an elite league of networking professionals. The industry recognizes the rigor of the certification process, establishing you as a credible authority in collaboration technologies.
Conclusion: Your CCNP Collaboration Odyssey Begins
The CCNP Collaboration certification, with its pinnacle represented by the 300-815 CLACCM exam, opens doors to a world of possibilities. Elevate your expertise, advance your career, and join elite networking professionals. As you embark on this odyssey, remember that success is not just a destination; it's a continuous journey of learning, application, and growth. So, gear up, dive into the world of collaboration, and let your CCNP journey unfold!
Saturday, 17 February 2024
Award-Winning Centralized Platform Helps Unlock Value Through Simplicity
Platform design choices
New hybrid choice with centralized architecture
Use cases
Cisco innovations
- Consistent software experience across multiple network nodes.
- Simplified network operations through consistency with upgrades, qualification, deployment, and troubleshooting.
- Unified security and trust across the network.
- Programmable interfaces via consistent APIs.
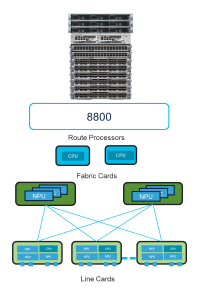
- Chassis: The router has an eight-slot 7RU chassis at 580 mm depth, which hosts fans, power supplies, RPs, SCs, and MPAs.
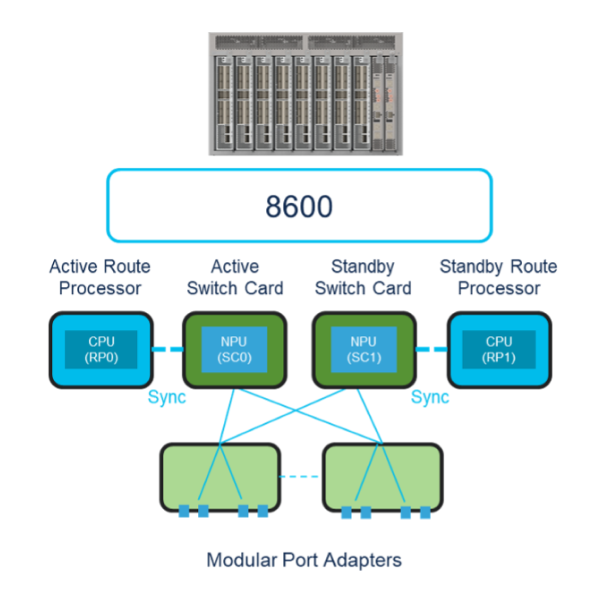
- Route processor: The RP hosts the CPU complex and the I/O ports. RPs fit vertically in the chassis from the front panel. Up to two RPs are supported in the system and the RPs operate in active-standby mode for a redundant system.
- Switch card: SCs sit orthogonally in the back of the MPAs with connections to all MPAs. SCs directly host the NPUs, with up to two SCs in the system that work in active-standby mode to deliver data plane redundancy.
- Power supplies: The router has four power supplies that can provide redundant power to the system. The power options include pluggable 3.2 KW AC and pluggable 3.2 KW DC.
- Fans: There are eight fans in the system, with each fan individually removable or replaceable to provide N+1 fan redundancy to the system.
- Modular port adapters: With a high degree of flexibility, the Cisco 8608 router supports a diverse range of interfaces, including 4×400 GbE, 24×10/25/50 GbE, and a combination of 16×100 GbE or 12×100 GbE+1×400 GbE or 8×100 GbE+2×400 GbE.
- Network operating system: Cisco IOS XR is the common NOS across access, aggregation, edge, and core platforms, including Cisco 8600 Series Routers. IOS XR provides network intelligence, programmability, and trustworthy solutions to help deliver operational efficiency.
- Manageability: Cisco Crosswork Network Automation is a comprehensive software platform that helps plan, provision, manage, optimize, and assure multi-vendor/multi-domain networks, including Cisco 8600 Series Routers, to help reduce operational costs.
Customer benefits
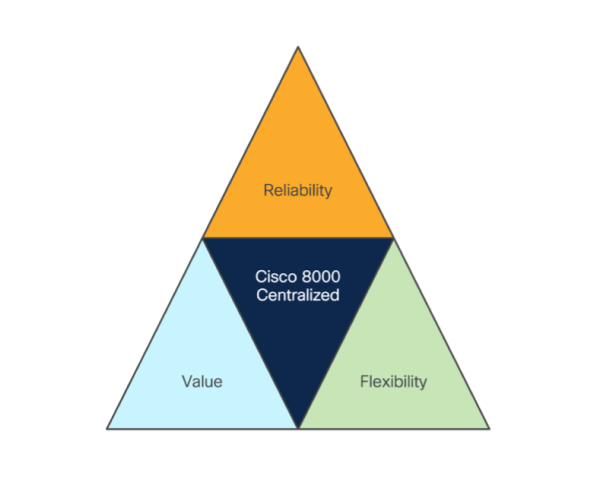
- Reliability: The unique hardware architecture provides industry-leading reliability with both control plane and data plane redundancy without loss of any front face plate.
- Flexibility: In-service upgradability and mix-and-match port support from 1G to 400G to help to efficiently meet both user and network traffic demands.
- Value: Customers can experience greater value with:
- Investment protection
- MPA backward compatibility
- Next-generation SC compatibility
- Optimized CapEx spending with right-sized platform to meet specific scale, space, power, and redundancy requirements
- Optimized OpEx spending with field-upgradeable and reusable components (similar to distributed systems) combined with using automated operations
- Sustainability that can help customers toward meeting their sustainability goals using a simplified centralized architecture.