Securing today’s digital content has become more challenging, as there are more endpoints and wide area networks (WAN) to protect than ever before. There will be 27.1 billion networked devices/connections by 2021, up from 17.1 billion in 2016 globally (according to the latest Cisco Visual Networking Index). The majority (51%) of those endpoints will be machine-to-machine (M2M) modules by 2021. As the Internet of Things (IoT) landscape continues to expand, digital domains and demands for access to applications and data by people and things will continue to increase.
To accommodate new bandwidth requirements, we are seeing constant and significant network innovation across all access technologies. From high efficiency wireless upgrades (including new Wi-Fi standards and the coming 5G revolution) to enhanced fiber/optical deployments and fixed line advancements in cable and DSL networks. Each of these innovations are designed to enable a wide range of new connections and applications — dense IoT deployments with smart cities, smart cars, sensors on every seat in a stadium, every plant on a farm or every product in a grocery store.
Unfortunately, this new era of connectivity and network reliance will also create new volumes and complexities in cyberattacks. With the positive promise of global digital disruption (more data and more efficiency) also comes real security implications for network operators and their consumer and business users. Cyberattackers are relentless, whether casting a wide net or narrowly targeting an organization. Attackers go after everything—hacking firewalls, compromising credentials, and discovering both hardware and software vulnerabilities. They use multiple methods to compromise information and infrastructure resources, finding their way into data and networks wherever they can, with off-the-shelf malware, brute-force password attacks, or phishing, other forms of social engineering and distributed-denial-of-service (DDoS) attacks.
A DDoS attack occurs when multiple systems flood the bandwidth or resources of a targeted system, usually one or more web servers. Such an attack is often the result of multiple compromised online targets flooding the breached system with debilitating traffic. Peak DDoS attack volumes (measured in gigabits per second [Gbps]) have been increasing in size, with peak attacks reaching 400, 500, and 800 Gbps, respectively, in 2014, 2015, and 2016, according to the Arbor Networks 12th Annual Infrastructure Security report.
DDoS attacks can represent up to 18% of a country’s total Internet traffic, according to Cisco VNI, and they are occurring and increasing at roughly the same rate as internet traffic. In 2016, the top motivation behind DDoS attacks was criminals demonstrating their attack capabilities, with gaming and criminal extortion attempts.
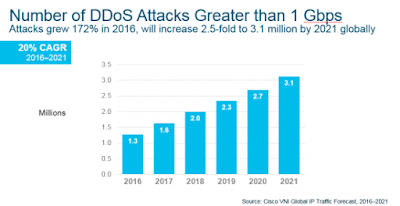
Today, the average DDoS attack size is roughly 1.2 Gbps, which is enough to take most organizations completely offline. Amplification attackers, who have tools for carrying out a DDoS attack, exploit vulnerabilities in the network and compute resources. Globally, the number of DDoS attacks greater than 1 Gbps grew 172% in 2016 and will increase 2.5-fold to 3.1 million by 2021.
To accommodate new bandwidth requirements, we are seeing constant and significant network innovation across all access technologies. From high efficiency wireless upgrades (including new Wi-Fi standards and the coming 5G revolution) to enhanced fiber/optical deployments and fixed line advancements in cable and DSL networks. Each of these innovations are designed to enable a wide range of new connections and applications — dense IoT deployments with smart cities, smart cars, sensors on every seat in a stadium, every plant on a farm or every product in a grocery store.
Unfortunately, this new era of connectivity and network reliance will also create new volumes and complexities in cyberattacks. With the positive promise of global digital disruption (more data and more efficiency) also comes real security implications for network operators and their consumer and business users. Cyberattackers are relentless, whether casting a wide net or narrowly targeting an organization. Attackers go after everything—hacking firewalls, compromising credentials, and discovering both hardware and software vulnerabilities. They use multiple methods to compromise information and infrastructure resources, finding their way into data and networks wherever they can, with off-the-shelf malware, brute-force password attacks, or phishing, other forms of social engineering and distributed-denial-of-service (DDoS) attacks.
A DDoS attack occurs when multiple systems flood the bandwidth or resources of a targeted system, usually one or more web servers. Such an attack is often the result of multiple compromised online targets flooding the breached system with debilitating traffic. Peak DDoS attack volumes (measured in gigabits per second [Gbps]) have been increasing in size, with peak attacks reaching 400, 500, and 800 Gbps, respectively, in 2014, 2015, and 2016, according to the Arbor Networks 12th Annual Infrastructure Security report.
DDoS attacks can represent up to 18% of a country’s total Internet traffic, according to Cisco VNI, and they are occurring and increasing at roughly the same rate as internet traffic. In 2016, the top motivation behind DDoS attacks was criminals demonstrating their attack capabilities, with gaming and criminal extortion attempts.
Today, the average DDoS attack size is roughly 1.2 Gbps, which is enough to take most organizations completely offline. Amplification attackers, who have tools for carrying out a DDoS attack, exploit vulnerabilities in the network and compute resources. Globally, the number of DDoS attacks greater than 1 Gbps grew 172% in 2016 and will increase 2.5-fold to 3.1 million by 2021.
The last few years have been particularly eventful period from a security threat perspective, with many serious data breaches that have been reported widely in the media (including the recent “Wanna Cry” ransomware attacks). When hackers breach cybersecurity defenses, the risks to consumers, small-to-medium business (SMBs) and enterprises are enormous, ranging from financial losses and damage to corporate reputations to exposure of intellectual property and the release of sensitive customer information. Ransomware has driven renewed interest in adoption of web security products designed to identify malicious websites and prevent web-borne threats from delivering malware onto employees and consumers PC’s, mobile devices and IoT connections.
The 2017 Midyear Cisco Security Report has been tracking the median time to detection (TTD). The overall trend has been downward, from over 39 hours in November 2016 to about 3.5 hours in May 2017.
There have been nearly 37 million records exposed according to the 2016 Identity Theft Resource Center report, and over 33 thousand records were exposed per breach. The highest number of breaches were in business, which includes retail, hospitality, trade, transportation, etc. The highest exposure of records during cyberattacks occurred in the healthcare industry.
From an infrastructure perspective, within the next year, a majority of US enterprises (>58%) will be deploying SD-WAN services, according to IDC. By 2020, at least 30 percent of international enterprise WAN service contracts will incorporate NFV based services, up from less than 1 percent in 2016, according to Gartner. Security is the leading use case, service, and a key business differentiator.
In the face of these persistent threats, network security—and ultimately data security—has become a paramount priority for most organizations. Simple endpoint solutions or an isolationist approach will not be sufficient barriers to dissuade today’s hackers. To effectively reduce or eliminate nefarious online activity in the age of hyperconnectivity, security needs to be embedded into a new digital culture that includes evolving hardware and software technologies as well as a heightened sense of awareness and diligence towards those who wish to profit from digital disruption through illegal practices.




0 comments:
Post a Comment