Today, knowing who is using your network is table stakes. What’s essential is knowing how the network is being accessed, what applications are being used, when they are used and most importantly, whether or not those applications are safe enough and compliant with your organization’s policies.
Independent testing company Miercom recently carried out a comprehensive set of tests to evaluate traffic analysis capabilities of Cisco’s Digital Network Architecture & Huawei’s Agile Solution along with a few other test areas.
Application types on the network today:
Independent testing company Miercom recently carried out a comprehensive set of tests to evaluate traffic analysis capabilities of Cisco’s Digital Network Architecture & Huawei’s Agile Solution along with a few other test areas.
Application types on the network today:
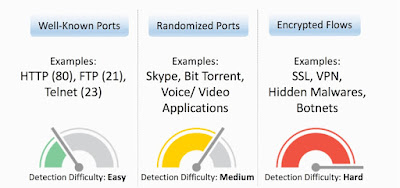
All major products in the networking business identify the basic flows of the packets based on IP, port number etc. to show information about traffic and determine whether the flow is based on http (port 80), https (port 443), ftp (port 21) etc. It’s very easy to identify and classify traffic based on these standard port numbers. However, nowadays, applications are evolving beyond this, using non-standard ports to using randomized ports. This makes it difficult to identify and classify flows based on HTTP and HTTPS. For example: A Skype call uses random higher order ports. Similarly, Bit Torrent uses randomized ports for every transaction. To identify such traffic, Cisco uses a deep packet inspection algorithm with its Application Visibility & Control (AVC) feature. Cisco AVC is based on NBAR2, which enables consistent visibility and control across its switching, wireless & routing platforms and offers granular and accurate application detection and control.
What about encrypted flows? More and more traffic is being encrypted. It’s difficult to have visibility into encrypted traffic because network devices cannot see inside because of technical issues or privacy concerns. Meanwhile, attackers are becoming more sophisticated and have started taking advantage of the opportunity by injecting malware or ransomware inside encrypted traffic. This leaves the network administrator completely blind to encrypted traffic that could potentially have malware or botnets hidden inside.
Cisco took an innovative approach to identify threats inside encrypted traffic with its latest network security innovation –Encrypted Traffic Analytics (ETA). ETA can be enabled with Cisco’s Catalyst 9000 switches and Cisco Stealthwatch.
ETA classifies & mitigates threats inside encrypted traffic without decrypting the packets, ensuring data privacy. Encrypted Traffic Analytics technology is enabled by the Catalyst 9000 switches and Cisco Stealthwatch, which uses the power of multi-layer machine learning to detect threats in encrypted traffic without any decryption.
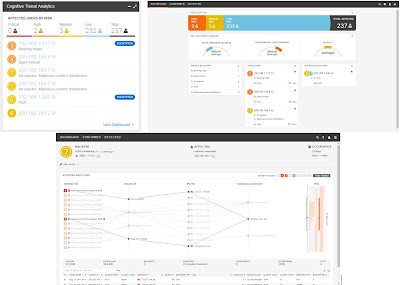
Cisco Stealthwatch with Cognitive Analytics allows an organization to see the number of malicious applications and activities on the network and provides a mechanism to quarantine such users from the network. ETA leverages innovative techniques such as sequence of packet length, timing, and initial data packets to detect malicious traffic using a cloud-based threat signature repository in order to keep up-to-date with the latest threats in the world.
Miercom found out that Huawei’s networking products and features are still living in the 19th century with limited visibility of IP address & port numbers versus true application recognition. Huawei’s NetStream technology (the company’s version of Cisco’s NetFlow) running on Huawei’s ENP (Ethernet Networking Processor) -based switches showcased a lack of recognition, resulting in poor visibility on an active network. Huawei also lacks the capability to detect any new or next-generation of threats which have begun to surface in the form of encrypted traffic.
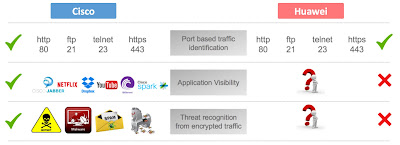
Miercom evaluated both Huawei and Cisco based on three stages of traffic analysis-
1. Basic port based identification
2. Application level visibility
3. Threat detection in encrypted traffic
In all three test cases Huawei was only able to showcased IP address and port number on its CLI output. No useful information could be seen on the web interface.
On contrary Cisco showed comprehensive output at every stage of the test, especially during stage 2 & 3.
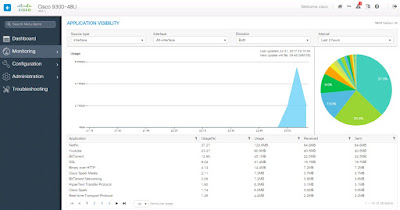
Cisco AVC accurately identified the applications running on the network, along with the amount of bandwidth they were consuming. Moreover, collaboration applications like Spark were even classified at the sub-flow level to monitor audio/video call, messaging etc. Such granularity empowers the administrator to apply granular policies based on application usage.
Miercom was impressed with Cisco Stealthwatch’s detection of a variety of malicious activities in the network that were completely missed by the Huawei infrastructure. Now, administrators using the Cisco solution can immediately respond to threats by taking corrective action to secure the network infrastructure and its users.
Summary
Huawei is trying to sell bare metal boxes which are not smart enough to offer the level of network visibility required to operate today’s and tomorrow’s networks. Cisco’s products and services not only offer a strong foundation for your enterprise infrastructure but also prepare organizations for hidden threats now and in the future to help prevent security breaches and save time and money.





0 comments:
Post a Comment