Overview
Recently, about 50 users across 20 companies were alarmed by the Cisco Cognitive Threat Analytics (CTA) about a malware that exfiltrates gigabytes of data from their computers. An example of such CTA detection:
In addition to the usual malware command and control activities, the incident features an upload of 2.3 gigabytes of data to a highly suspicious destination. CTA has classified this incident as a malware with high severity and confidence.
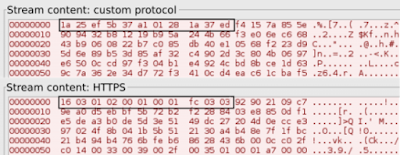
This particular malware is using a custom protocol over TCP port 443, which is assigned for HTTPS. Generally, less than 10% of organizations do any inspection of HTTPS traffic. In addition to relatively low probability of intercept, malware authors also use custom protocol that is not based on HTTPS. A comparison of the stream content of the custom protocol to a stream content of a HTTPS protocol is shown below.
Through state of the art anomaly detection, CTA has the ability to separate and highlight the exfiltration behavior, without the need to inspect the content. This naïve obfuscation method is therefore ineffective.
According to CTA statistics, nearly 100% of hosts infected by this malware family exhibit click-fraud behavior. There is a tendency to ignore click-fraud due to perception of low risk. As we can see, even a seemingly non-threatening malware activity can and will escalate into much more dangerous situation.
Exfiltration behavior details, IOCs, and references
Based on global CTA data, about 30% of incidents from this malware family exfiltrate data. CTA does identify the users exfiltrating the data using the information about traffic volume, frequency, destination and other characteristics. An example for 7 different infected hosts is shown below.
This communication is over a custom protocol on TCP port 443 assigned to HTTPS and to a dotted quad destination. Current publicly available investigations account neither for the custom protocol nor for the gigabytes of uploads. The list of identified destination IP addresses is as follows:
◉ 136.243.4.68
◉ 136.243.4.69
◉ 148.251.80.145
◉ 148.251.80.172
◉ 217.23.6.72
◉ 93.190.140.144
We have identified a sample [CYMRU] that has network traffic to the same destinations. These IP addresses have DNS associated entries to [1-3].jsservices[.]org, and [1-5].web-counter[.]info hostnames. Articles such as [MS-SEC-PORTAL] relate these hostnames to Miuref or Boaxxe malware families. Other resources [SOPHOS] also list Symmi as an alias for Miuref.
Miuref is a malware that can generate user traffic, and download unwanted applications and more malware to the infected endpoint. Its general monetization method is click-fraud. As observed, untreated infections can escalate into exfiltration of data.
This threat is a high risk to organizations. We advise to block traffic, to perform a full scan of the infected device, and then to reimage the device.
These concrete IOCs are currently being blocked for the CWS user base. In time, the IOCs are likely to be changed. CTA has the capability of detecting similar malware families that steal your information, irrespectively of the actual destination IP address.
About Cisco Cognitive Threat Analytics
Cisco Cognitive Threat Analytics (CTA) is a cloud-based breach detection and analytics technology focused on discovering novel and emerging threats by identifying C&C activity of malware. CTA processes web access logs from the Cisco Cloud Web Security (CWS), Cisco Web Security Appliance (WSA), or 3rd party web proxies such as Blue Coat ProxySG. CTA reduces time to discovery (TTD) of threats operating inside the network. It addresses gaps in perimeter-based defenses by identifying the symptoms of a malware infection or data breach using behavioral analysis and anomaly detection. The technology relies on advanced statistical modeling and machine learning to independently identify new threats, while constantly learning from what it sees and adapting over time. Through additional careful correlation, CTA presents 100% confirmed breaches to keep security teams focused on the particular devices that require a remediation. Focusing on C&C activity detection, CTA addresses a security visibility gap by discovering threats that may have entirely bypassed web as an infection vector (infections delivered through email, infected USB stick, BYOD).






0 comments:
Post a Comment