Mergers and acquisitions bring major challenges to nearly every aspect of a business, but integrating two different networks while maintaining enterprise security is perhaps one of the most demanding trials an organization can undergo.
Every organization has their own security policies, and applying new ones to hundreds or even thousands of new machines and users can be a logistical nightmare. On top of that, increasing the size of a network also increases its threat surface, potentially giving attackers new avenues to gain access and compromise sensitive data.
The pervasive network visibility that Cisco Stealthwatch Enterprise provides can give network and security administrators the information they need to facilitate a smooth and secure integration. Here are a few ways Stealthwatch Enterprise is useful in mergers and acquisitions.
Successfully integrating two networks requires extensive knowledge of what hosts, systems, and resources are present. To ensure you have the most accurate knowledge possible, use Stealthwatch Enterprise to discover the acquisition’s assets.
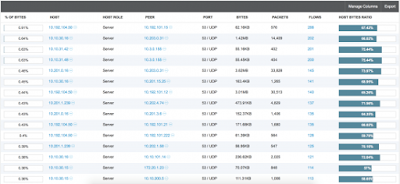
By using NetFlow and other sources of network traffic metadata, Stealthwatch Enterprise sees all activity on the network. This means that every host that produces traffic on the network is identified and logged automatically. In a few hours or days, engineers and architects will have records of every active host. These can then be inventoried by service to identify servers that need to be moved.
Here are example results of a query to identify active servers providing DNS:
Every organization has their own security policies, and applying new ones to hundreds or even thousands of new machines and users can be a logistical nightmare. On top of that, increasing the size of a network also increases its threat surface, potentially giving attackers new avenues to gain access and compromise sensitive data.
The pervasive network visibility that Cisco Stealthwatch Enterprise provides can give network and security administrators the information they need to facilitate a smooth and secure integration. Here are a few ways Stealthwatch Enterprise is useful in mergers and acquisitions.
Audits
Successfully integrating two networks requires extensive knowledge of what hosts, systems, and resources are present. To ensure you have the most accurate knowledge possible, use Stealthwatch Enterprise to discover the acquisition’s assets.
By using NetFlow and other sources of network traffic metadata, Stealthwatch Enterprise sees all activity on the network. This means that every host that produces traffic on the network is identified and logged automatically. In a few hours or days, engineers and architects will have records of every active host. These can then be inventoried by service to identify servers that need to be moved.
Here are example results of a query to identify active servers providing DNS:
Service and Application Identification
Different organizations use applications and services differently. Understanding what services and applications are used, how much they are used, and identifying the data flows in use by the services and applications is key to developing an integration strategy that minimizes impacts to normal business functions.
Stealthwatch Enterprise provides layer 7 visibility, which allows users to see application and service usage in a variety of formats. Here is an example summary of a network environment’s application traffic, visualized as a pie chart:
As a graph:
And as a table:
In addition, users can drill into the data to discover a variety of attributes with only a few clicks.
Policy Violations
Mergers and acquisitions often involve applying new policies to old networks. The comprehensive visibility provided by Stealthwatch Enterprise can be used to identify noncompliant traffic and policy violations in real time. Stealthwatch Enterprise users can define custom rules to trigger an alarm when traffic utilizes a prohibited service or violates a policy.
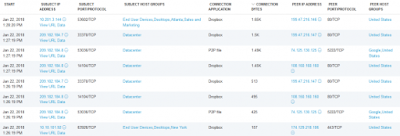
In the example below, traffic utilizing peer-to-peer (P2P) or Dropbox is identified:
Stealthwatch Enterprise can also be used to verify policy enforcement. For example, if P2P traffic is supposed to be blocked, any P2P activity could be indicative of a misconfigured policy.
Access Control and Segmentation
Stealthwatch Enterprise can also be used to develop network access control and firewall policies and verify their effectiveness. Utilizing the principle of least privilege, limiting hosts’ access to only network resources needed to perform their function can drastically reduce the reach of an attacker who manages to circumvent perimeter security. This is especially applicable to environments that must comply with industry regulations, such as PCI DSS, HIPAA, etc.
By understanding where sensitive assets reside and what network resources users interact with on a regular basis, architects can design access control policies that are effective and don’t impact normal business functions. Stealthwatch Enterprise uses network telemetry data to identify flows actually in use and takes out the guesswork, allowing for much smoother implementation and maintenance.
Additionally, administrators and architects often lack a way to verify if policies are working as intended. Using Stealthwatch Enterprise, custom rules can be defined to immediately highlight traffic that violates intended access controls, which can then be investigated and adjusted as necessary.
Link Monitoring
When integrating two networks, it is important to understand how different locations send data throughout the network to prevent erroneously disrupting network availability and to ensure data is transmitted efficiently. Stealthwatch Enterprise host group relationship maps can help with this.
Traffic profiles can also be built using Stealthwatch Enterprise to assist in capacity planning.
Maintaining Security
Last but most important, integrating separate networks bring a host of security implications, and attackers are aware of this and may keep track of major acquisitions to take advantage of the situation. No security measure is fool-proof, and you cannot simply assume your internal network is a safe area. This is even more important in an acquisition scenario where threats already present on the acquired network could be given free access to the larger network.
Stealthwatch Enterprise significantly reduces the time to identify a threat, giving security personnel a window of opportunity to mitigate the threat before sensitive data is stolen. By relying on NetFlow and other network traffic metadata, Stealthwatch Enterprise can identify a wide variety of security events including worm and botnet activity and advanced threats.
Identifying and mitigating these threats before they are integrated into the enterprise network with all of the legitimate systems can make the difference between a successful acquisition and a major data breach.
New opportunistic threats can also be detected during and after the integration process, ensuring that security is maintained throughout the organization from the beginning of the acquisition and after.









0 comments:
Post a Comment