Those of us who have been in security for more than 20 years are very familiar with the assertion that security is a process. For me, security has always been a process like a melody that ties in all other parts of the song. Staying on this musical analogy, if process is the melody, and you consider Cisco’s security portfolio as different instruments, then Cisco Threat Response is leading in this beautiful orchestration of investigation. Threat Response focuses on the process aspect of security. In this blog post, I want to introduce you to its value as an incident response tool and show you how to best utilize it with the integration of the Cisco Email Security product.
What is Cisco Threat Response?
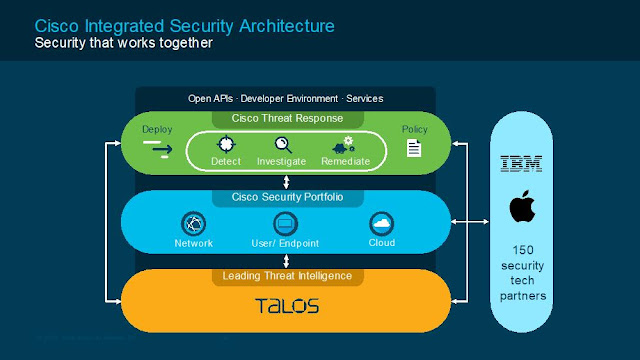
Just like how harmony is essential to a great piece of music, it’s equally a critical aspect of modern security architecture. Today’s Security Operations Centers (SOCs) are inundated with alerts to potential threats, all scattered across a discordant array of security products that don’t always like to play nice with each other. More often than not, this results in a lot of wasted labor and time. Think of Cisco Threat Response as a conductor that harmonizes the various components of your security infrastructure. And with Cisco’s open architecture, the Security portfolio of products works together like an orchestra.
Threat Response integrates threat intelligence from Cisco Talos and the various third party sources that make up your SOC to automatically research indicators of compromise (IOCs) and confirm threats quickly. By channeling threat data into a single user-friendly interface, your SOC team analysts can quickly aggregate alerts, investigate, and remediate threats lurking about your systems, network and cloud. No matter how big or small your organization may be, Threat Response is designed to scale, ensuring your cyber security programs run efficiently, effectively, and most of all harmoniously.
Cisco Email Security
Email is easily the most pervasive technology across businesses. It’s hard to imagine living without it. However, as integral as it is to day-to-day business functions, it’s also one of the most commonly exploited attack vectors. With over 90% of breaches starting via email, having an email security solution in place is no longer a luxury, but a necessity.
Cisco Email Security provides best in class efficacy and has been recognized for the third year in a row as the Top vendor in The Radicati Group’s 2018 Secure Email Gateway report. In addition, the integration of Email Security with Cisco Threat Response provides you with a more robust approach to email security. This layered defense provides industry-leading protection against malware, phishing, spoofing, ransomware and business email compromise (BEC).
Avoid Phishy Melodies
Most threat narratives have a very similar beginning. An attacker has phished their way into a network via an email and successfully socially engineered a user into disclosing their credentials. Unfortunately, this is usually followed by organizations discovering far too late that they’ve been compromised. Remember, however, that in order for the above scenario to play out, the attacker has to complete a series of phases of their attack without being detected. Luckily, as the defender, all you need to do is detect them in one phase! Even if something does get through, if you can detect that threat and respond with a countermeasure before the attacker completes that phase, you have won.
Cisco Threat Response brings your threat detection capabilities into simple focus with:
Simpler Integration: Let’s say you have a situation where AMP for Endpoints has detected a malicious file represented by a file hash (SHA) or Stealthwatch has alerted you of a user connecting to a suspicious URL. You can use Threat Response to pivot directly to Cisco’s Email Security and ask for the email messages associated with this SHA or URL and this information can be then used to stop that attack’s campaign dead in its tracks.
Simpler Data Tracking: Want to know where that malicious email or potential threat came from? Threat Response allows you to track and isolate which user received that SHA or URL and lets you block the domain of origin without needing to switch programs. Additionally, if said malicious link was shared amongst your network, you can also see when and where it was sent and prevent it from spreading further.
Simpler Workflow: Like I mentioned earlier, Cisco Threat Response is all about simplifying threat response through harmonizing the various tools you already have in place into a single resource. Furthermore, not only does this allow security analysts to reduce the number of interfaces they’re using, but Threat Response also provides them with context based graphs, telemetry charts, and even response suggestions.
Simpler Threat Hunting: As your analysts respond to threats, they can also log their threat response processes and observations into the integrated Casebook function. Since Casebooks are built on cloud API and data storage, they can also follow you from product to product, across your entire Cisco Security portfolio. In turn, this allows for faster and effective threat response and remediation efforts across your enterprise thanks to the ability for analysts to easily build and share Casebooks.





Find the best Self Defense Products, Personal Protection Equipment, Survival Gear and Security Devices for sale at Security Products Shop.
ReplyDeleteGreat post!! It was very informative and knowledgeable. Thank you for sharing this with us.
ReplyDeleteI know a website that provides the best email security tools, services and solutions. Visit https://thechecker.co today.