Your network is increasingly targeted by cybercriminals. One of the most clever and damaging way they strike is through command and control attacks – a technique often executed over DNS. A command-and-control (also referred to as C&C or C2) server is an endpoint compromised and controlled by an attacker. Devices on your network can be commandeered by a cybercriminal to become a command center or a bonet (a term coined by a combination of the words “robot” and “network”) with the intention of obtaining full network control. Establishing C&C communications via a Trojan horse is an important step for them to move laterally inside your network, infecting machines with the intent to exfiltrate data.
What does your new investigation workflow look like? Today we take a closer look at how a C&C server attack can gain a foothold into your network, and how Cisco can identify, detect and block this type of threat using an integrated approach to security.
Imagine a security analyst whose enterprise has invested in network traffic analysis. Let’s call him Sam. He works for large financial services organization with over 10,000 employees and more than 80,000 user accounts. It’s 6:00 PM on a Friday evening and Sam is getting ready to catch the latest Zombie apocalypse movie with his buddies. A notification pops up on his Cisco Umbrella console telling him that Umbrella has blocked malware from communicating with a C&C channel.
Sam is tired. He spends copious amounts of time running down rabbit holes every time his SIEM registers an alert as suspicious. He is ready for a faster, more effective way to block threats and protect his environment. He is excited to see if Cisco Umbrella, a secure internet gateway, will make his life easier. Cisco Umbrella offers both real-time threat Intelligence, as well as the capabilities to mitigate attacks across an organization in a split second. It acts as the first line of defense against internet-borne threats like C&C communications attempting to exfiltrate data. Sam knows a DNS block on the Umbrella can simply be a symptom of persistent malware on your endpoints. He investigates further.
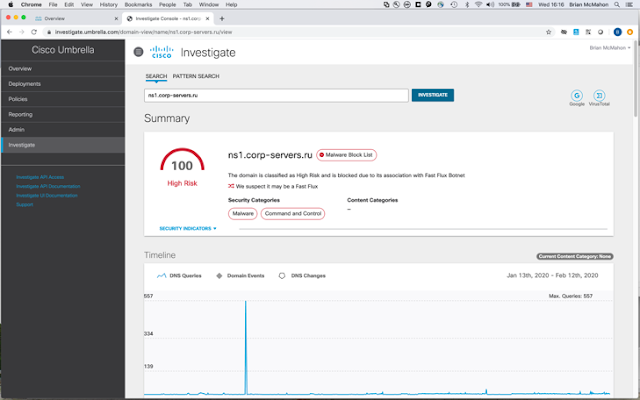
Sam identifies the malicious domain that is the epicenter of a C&C activity using Umbrella. Umbrella automatically proxies, decrypts, and inspects all subsequent requests with AMP for Endpoint to make a determination about the threat. Sam can also choose to block newly seen domains outright on the console. Now, while Sam knows that not all newly seen domains are bad, he knows this could be part of an emerging malware campaign or associated with another threat. In this case, Sam sees that Umbrella is working and has successfully blocked the threat.
Going After the Command-and-Control Servers
What does your new investigation workflow look like? Today we take a closer look at how a C&C server attack can gain a foothold into your network, and how Cisco can identify, detect and block this type of threat using an integrated approach to security.
Imagine a security analyst whose enterprise has invested in network traffic analysis. Let’s call him Sam. He works for large financial services organization with over 10,000 employees and more than 80,000 user accounts. It’s 6:00 PM on a Friday evening and Sam is getting ready to catch the latest Zombie apocalypse movie with his buddies. A notification pops up on his Cisco Umbrella console telling him that Umbrella has blocked malware from communicating with a C&C channel.
Sam investigates this threat using the Cisco Security
Sam is tired. He spends copious amounts of time running down rabbit holes every time his SIEM registers an alert as suspicious. He is ready for a faster, more effective way to block threats and protect his environment. He is excited to see if Cisco Umbrella, a secure internet gateway, will make his life easier. Cisco Umbrella offers both real-time threat Intelligence, as well as the capabilities to mitigate attacks across an organization in a split second. It acts as the first line of defense against internet-borne threats like C&C communications attempting to exfiltrate data. Sam knows a DNS block on the Umbrella can simply be a symptom of persistent malware on your endpoints. He investigates further.
Sam identifies the malicious domain that is the epicenter of a C&C activity using Umbrella. Umbrella automatically proxies, decrypts, and inspects all subsequent requests with AMP for Endpoint to make a determination about the threat. Sam can also choose to block newly seen domains outright on the console. Now, while Sam knows that not all newly seen domains are bad, he knows this could be part of an emerging malware campaign or associated with another threat. In this case, Sam sees that Umbrella is working and has successfully blocked the threat.
Figure1: Identify the C&C Domain in Umbrella
But Sam is curious. He wants to know more. Sam decides to analyze the malicious code and try to identify samples in Threat Grid, Cisco’s dynamic file analysis solution that referenced this domain. Umbrella Investigate shows him samples in Threat Grid that referenced this domain. He drills down deeper.
Figure 2: Sightings in Threat Grid that referenced this domain
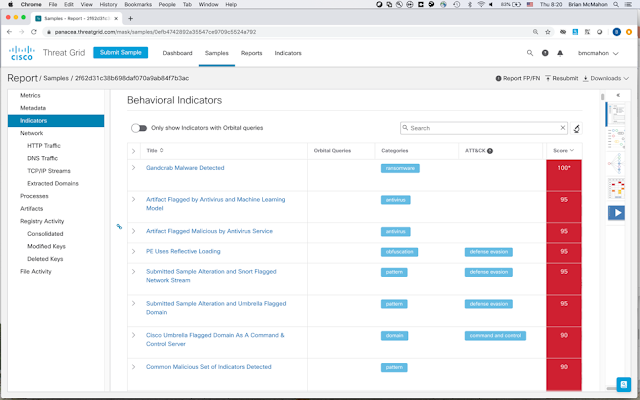
Using the Threat Grid console, Sam quickly realizes the file is malicious. He sees two internal targets that can be potentially compromised with this attack. If successful, this infected server could connect to another server, ready to receive commands and do the botnet owner’s bidding by compromising systems and exfiltrating your data.
Figure 3: The Aha! moment: The Malicious Verdict
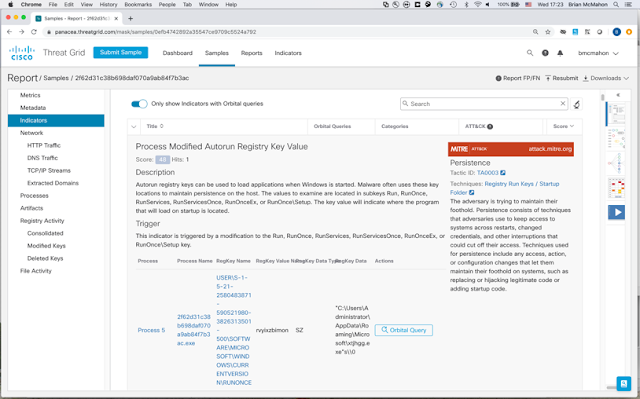
Sam is close to the Aha moment! He drills down to understand the behavioral indicators in Threat Grid. He gets every scrap of detail about this threat artifact. And sure enough, there’s our C&C connection. Victory!
Figure 4: Discovery: There’s our C&C connection.
But Sam wants more. Threat Grid also shows him the internal target that might need further analysis. It analyzes the files and suspicious behavior across his environment to deliver context-rich malware analytics and threat intelligence. Now that he is armed with insights into what the file is doing, he is ready to explore how this threat has impacted the network. Sam kick starts a threat investigation for observed internal targets in Cisco Threat Response using the Browser Plugin. The Plugin enables Sam to research any observable (e.g. Domain, IP-address, File-Hash, URL, etc.), on any HTML-based webpage, in Chrome. Interested in what Sam is doing?
Sam now knows which systems inside our network have seen the malicious file. This information is provided by AMP for Endpoint, our cloud-delivered endpoint protection, detection and response solution, that helps you simplify this investigations with a broader context from endpoint, web, email, and network data.
Figure 5: The Pivot to Threat Response
Figure 6: Getting the Full Picture – the Relations Graph in Threat Response
Upon investigation, Sam confirms that the malware is already correctly identified and blocked. With Cisco Threat Response, Sam can now achieve faster detections, simpler investigations, and immediate responses.
Figure 7: Malware Identified and Blocked
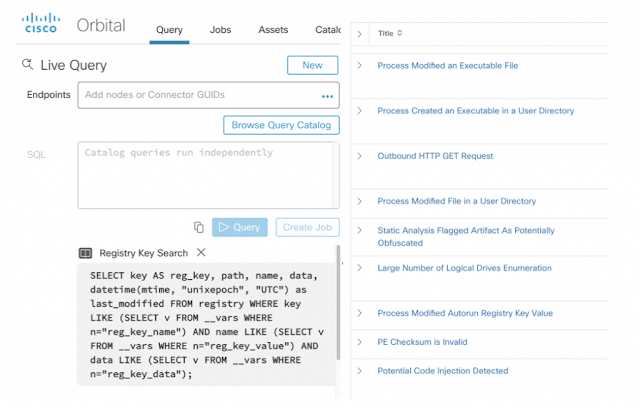
For all the Sam’s of the world, this analysis can be at your fingertips too. With Threat Grid, you can easily construct a query using the Orbital Advanced Search feature, a new advanced capability in Cisco AMP for Endpoints based on the behavior observed when the sample executed. This feature accelerates your hunt for threats and enables you to shrink the lifecycle of an incident– mitigating any or further damaging cost of the breach to your business.
Figure 8: Orbital Advanced Search Query in Threat Grid
This Orbital query enables you to gain deeper visibility so you may discern whether this is an isolated incident in your network, or there are other devices that may have seen this in your network. Additionally, Threat Grid can shine a light on other techniques like code injection that attackers might be using based on key behavioral indicators of malware. Security teams can save time by quickly prioritizing attacks with the biggest potential impact. In our investigation, we have discovered important details about this attack, as well as the malicious, forged documents that the attackers are using.
Figure 9: Orbital Query, Figure 10: Potential Code Injection Detected
Cisco Advanced Malware Protection (AMP) for Endpoints Prevents Fileless Attacks
AMP for Endpoints’ Exploit Prevention engine prevents all variants of fileless malware without needing any prior knowledge of the attacks. There are thousands of threats attempting to embed malicious code that can take over your workflows. Sam makes sure that the Exploit Prevention engine is enabled in AMP to catch any such activity.
Sounds too good to be true. No way?
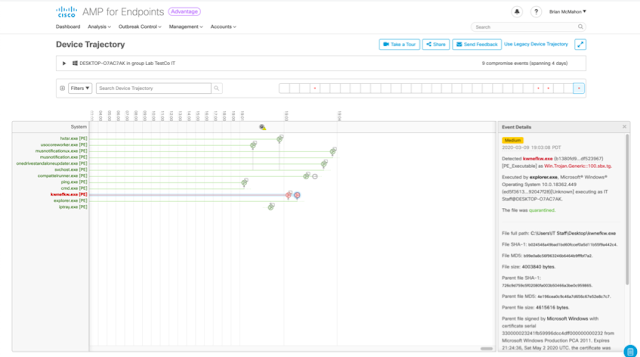
Figure 11: File is quarantined
AMP’s Exploit Prevention Engine remaps the runtime environment and its components (such as libraries and DLL entry and exit points) and places a decoy or a facade of these resources in their original locations. It then only let’s legitimate applications know their newly randomized address spaces. The end result is that legitimate processes continue to run seamlessly without experiencing any performance penalty, but anything else that attempts to execute in-memory can’t find its target, and therefore, cannot execute. Exploit Prevention’s remapping of the runtime environment effectively protects you against all variants of in-memory attacks, whether they are pre-existing or undiscovered zero-days deterministically. With that done, Sam is on his way to the movies.
Cisco’s Security Platform
Can you imagine flying an Airbus A380 without an air traffic controller? Cisco’s vision for a security platform is built from a simple idea that security solutions should act as a team, learning from each other, listening and responding as a coordinated unit. Our platform, Cisco SecureX,connects the breadth of Cisco’s integrated security portfolio and your entire security infrastructure for a consistent experience that unifies visibility, enables automation, and strengthens your security across your network, endpoints, cloud, and applications.
Try AMP for Endpoint
You could test out AMP for Endpoints and decide whether it’s right for you in under an hour. Don’t let C&C servers sit dormant in your environment and turn your computers become someone else’s malicious botnet!









0 comments:
Post a Comment