“The more things change, the more they stay the same” can be true even with security.
Although our security tools and workflows have certainly become much stronger over the years, some challenges haven’t changed:
◉ Businesses still worry about their intellectual property being compromised and/or leveraged for nefarious use.
◉ Deploying a secure defense is still complex; many companies can find themselves deploying 50 to 100 different tools from 50+ vendors in an attempt to protect their businesses.
◉ There is still a lack of qualified security personnel, which becomes even more problematic given the large number of vendors and tools that must be managed.
◉ It is still difficult to explain the toolsets and processes required to secure a modern enterprise.
Expanding on that last point, a year ago, we began working with IBM to find a way to explain joint Cisco and IBM security value propositions in a way that is easier for our customers and partners to understand.
We’ve been told by customers that if we can reduce their vendor count from 50+ vendors to “something you can count on your fingers and toes,” it would improve not only technical efficiency for their response teams, but also offer operational efficiency to legal and finance teams through contract simplification. In response, over time and through a number of integrations, Cisco and IBM have jointly developed a comprehensive security story, greatly simplifying your vendor and tools landscape. Now, while I can’t say in good conscience that Cisco and IBM can address all your security concerns, integrated Cisco and IBM tools and services can meet a majority of your security needs and our technology ecosystems can fill in the gaps.
The result of our efforts to better explain these Cisco and IBM security value propositions is what I call “subway map” journeys.
Mapping a customer’s security journey with integrated solutions
Initially, we began by looking at the top three areas of concern for our customers:
◉ Insider threats: threats living inside the network
◉ Ransomware: malicious software that blocks system access
◉ Compliance: the need to meet and maintain compliance requirements
When customers explore how to protect their businesses against these three use cases, they typically deploy a number of tools, which can be viewed as subway stops along the security journey (Figure 1).
Although our security tools and workflows have certainly become much stronger over the years, some challenges haven’t changed:
◉ Businesses still worry about their intellectual property being compromised and/or leveraged for nefarious use.
◉ Deploying a secure defense is still complex; many companies can find themselves deploying 50 to 100 different tools from 50+ vendors in an attempt to protect their businesses.
◉ There is still a lack of qualified security personnel, which becomes even more problematic given the large number of vendors and tools that must be managed.
◉ It is still difficult to explain the toolsets and processes required to secure a modern enterprise.
Expanding on that last point, a year ago, we began working with IBM to find a way to explain joint Cisco and IBM security value propositions in a way that is easier for our customers and partners to understand.
We’ve been told by customers that if we can reduce their vendor count from 50+ vendors to “something you can count on your fingers and toes,” it would improve not only technical efficiency for their response teams, but also offer operational efficiency to legal and finance teams through contract simplification. In response, over time and through a number of integrations, Cisco and IBM have jointly developed a comprehensive security story, greatly simplifying your vendor and tools landscape. Now, while I can’t say in good conscience that Cisco and IBM can address all your security concerns, integrated Cisco and IBM tools and services can meet a majority of your security needs and our technology ecosystems can fill in the gaps.
The result of our efforts to better explain these Cisco and IBM security value propositions is what I call “subway map” journeys.
Mapping a customer’s security journey with integrated solutions
Initially, we began by looking at the top three areas of concern for our customers:
◉ Insider threats: threats living inside the network
◉ Ransomware: malicious software that blocks system access
◉ Compliance: the need to meet and maintain compliance requirements
When customers explore how to protect their businesses against these three use cases, they typically deploy a number of tools, which can be viewed as subway stops along the security journey (Figure 1).
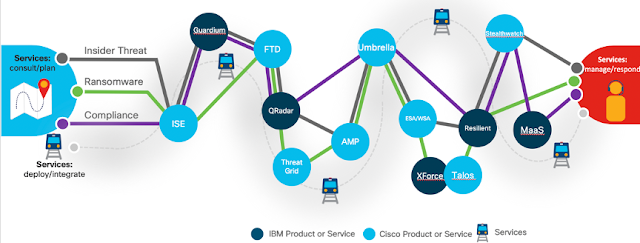
Figure 1: Security journey subway map
The three colored lines in this subway map are aligned with each use case. In each journey, the light blue and dark blue stops represent Cisco and IBM products, respectively. Also notice the subway car moving through the stops. The shortage of security personnel means many of our customers rely on services from Cisco and IBM to help transport them to their destination, whether through consulting before an engagement, integration services during deployment, or managed services afterward.
You can look at the briefs for Ransomware, Compliance, and Insider Threats workflows on the IBM and Cisco Security Solutions page, but let’s take a quick look now at Insider Threat and discuss how it’s been impacted by the ongoing pandemic.
Insider threats
In the case of insider threats, the primary concern is that an employee or other insider has gained privileged access to the network and can obtain company secrets or customer data. In response, a security solution must:
◉ Block causes of a potential compromise
◉ Restrict access to limit the scope of loss if the network is compromised
◉ Quickly identify and prioritize threats
◉ Detail the response plan so operators can move quickly to mitigate damage
As shown in Figure 2, the integrated Cisco and IBM defense against insider threats includes the following tools:
◉ Cisco Identity Services Engine (ISE) orchestrates who is using the network and creates policies for where they are allowed to go.
◉ Cisco Firepower Threat Defense (FTD) provides enforcement points and detection through NGFW/NGIPS functionality.
◉ Cisco Stealthwatch provides visibility into traffic on the network—so we know policies are being observed—while also providing insight into what policies could/should be.
◉ Cisco Advanced Malware Protection (AMP) enables file inspection across endpoints, the intrusion prevention system (IPS), email, and the web (ESA/WSA) to reduce points of compromise.
◉ IBM QRadar combines alerts from multiple sources and analyzes user activity to detect malicious insiders.
◉ IBM Resilient helps companies understand and orchestrate a response plan across people, process, and technology.
◉ IBM Guardium activates data loss prevention (DLP) to further the solution through classification of sensitive assets and data protection.
Figure 2. Insider threats subway journey
Going forward
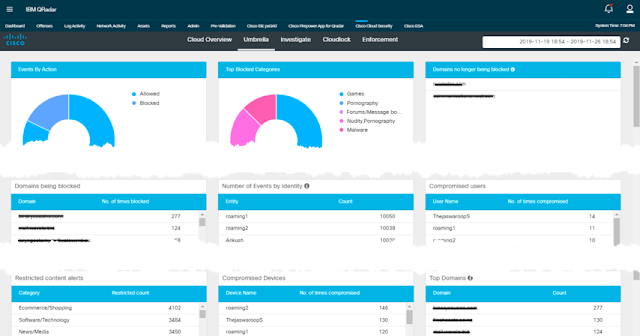
Stay-at-home orders have created a new set of challenges for many businesses during the pandemic. While the tools mentioned in the previous section remain relevant to combating insider threats, the relative importance of technologies such as Cisco Duo for MFA, Cisco AnyConnect for VPN access, Cisco AMP4EP, and Cisco Umbrella in protecting remote and mobile workers has increased. The changes in the way our customers leverage our tools also impacts the way we focus integration surface between our companies. As you may have guessed, consumption of AMP4EP logs in QRadar has is an area we’ve seen increase and we’ve received great feedback on the recently published Cloud Security app for QRadar (Figure 3) as well.
Figure 3. Cisco Cloud Security Dashboard in QRadar
In addition, as many of you have heard by now, Cisco has been focusing heavily on improving usability and workflow for customers leveraging our tools. That work has culminated in the recently launched Secure X tool. I’m happy to say that we have integrated Secure X into QRadar, so that customers can get hover-over information from Secure X directly in QRadar and also pivot into Secure X for additional drill-downs and investigation details.





0 comments:
Post a Comment