What is Threat Intelligence?
According to Wikipedia, “cyber threat intelligence is information about threats and threat actors that helps mitigate harmful events in cyberspace”. Wikipedia also points out that the “sources include open source intelligence, social media intelligence, human intelligence, technical intelligence, or intelligence from the deep and dark web”.
There are different forms of threat intelligence:
◉ Tactical: this type of intelligence can be used to identify the threat actor of a specific attack. Examples can be Indicators of Compromise (IoCs) like IP addresses, domains and file hashes.
◉ Operational: this type of intelligence focuses more on the Tools, Techniques and Procedures (TTPs) of the attacker.
◉ Strategic: this type of intelligence focuses more on high-level cyber risks and can be used to create a strategy for a company.
What is the SecureX Threat Response API?
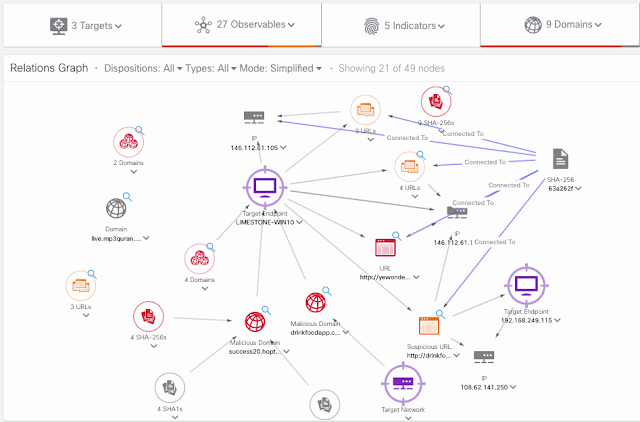
The SecureX Threat Response platform is a tool that aggregates and correlates the capabilities of many Cisco and third-party security products (called “modules”). This tool can be leveraged for “threat hunting” in a customer’s environment to help keep their environments secure. It does this by connecting to the API’s of the various products, and by doing so is able to retrieve information. This process is called “enrichment.” Enrichment focuses both on internal sightings and external threat intelligence. At the same time, Threat Response can take actions in a subset of the connected products. This process is called “response”.
Some products can only provide enrichment, while others can do both enrichment and response. Cisco Security customers can use Threat Response to quickly identify a root cause of a cyber-attack, by using any text (containing IoCs) as an input. This text can then be enriched both from internal monitoring modules (“Do I have any infected hosts?”), and from threat intelligence modules (“Are these IoCs bad?”). And it enables customers to quickly take response actions to remediate the threat.
If you’re a Cisco Security customer, guess what … You have access to Threat Response at no extra cost. The Threat Response APIs can be leveraged to automate a big chunk of the threat hunting process, and mainly the enrichment process.
How to harvest threat intelligence, and hunt the threats?
The internet contains many free sources of threat intelligence that can be used in addition to the Cisco Talos feeds. Using the SecureX Threat Response API, it is possible to harvest this and discover internal security events. This process is what was earlier described as “enrichment”, where both internal and external modules are checked for hits. There is a big community out there that shares new IoCs related to new cyber-attacks and malware campaigns.
So how can I harvest my threats?
Below are two examples that take a free source from the internet (blogs and Twitter) and parse them for IoCs. Both scripts then check for “target sightings” and automatically adds IoCs to SecureX Casebook. If there are any hits on internal targets, it will add a “HIGH PRIORITY” tag to the Case. The scripts will also send a Webex Teams alert to a configured Space (e.g. the Space used by a SOC). Check out the links below to find out more!
1. Searching threat intelligence blogs
The Cisco Talos blog is a perfect example of one of those free sources of threat intelligence that can be found on the internet. Their blog highlights threats and other information they find on a regular basis. However, who has the time to read all these blog posts, search through all their security tools for hits, and take action on them? Using the Threat Intelligence API, I was able to search the Talos blog (and others!) and pull out the exact information I needed to remediate my threat. Find out how on my DevNet Automation Exchange post:
2. Scouring Twitter Hashtags (e.g. #OPENDIR)
You can do a similar things with Twitter. The #opendir Twitter hashtag is used by many threat intelligence researchers to post their findings on new threats. This is a perfect example of one of those free sources of threat intelligence that can be found on the internet. Matching this information source with the connected Threat Response modules, gives you relevant hits to help protect your organization for unwanted threats.
These are just two examples of what you can do with these awesome API’s.






0 comments:
Post a Comment