By now, you may have heard about SecureX, Cisco’s new integrated platform that simplifies the security experience. SecureX is built into the Cisco security portfolio, and connects your entire security ecosystem for simplicity, better visibility, and greater operational efficiency. SecureX sign-on is one of the key features of SecureX – it’s giving users instant access to the platform and all of their applications and data, while keeping the identity provider (IdP) and multi-factor authentication (MFA) in sync.
Is your organization using an IdP and MFA provider? You can make life easier for your SecOps team, while strengthening your organization’s cybersecurity posture, improving compliance and increasing visibility without adding tasks to your team. This post will describe a new automated process that can do all these for you.
Background
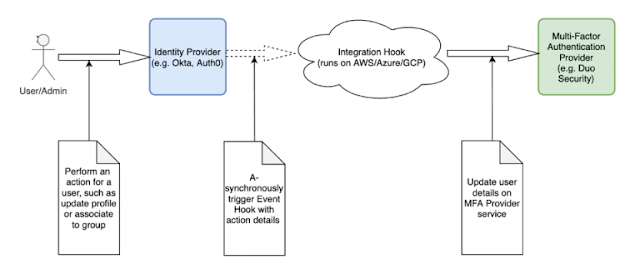
With SecureX sign-on, we are using several identity providers (like Okta, Auth0, Azure AD and Cisco security) as our applications need and see fit. We chose Duo to be our multi-factor authentication (MFA) provider as it gave us great visibility into our customers’ security posture and is a very flexible MFA. Now we needed to have our Identity and MFA Providers in sync.
An identity provider (abbreviated IdP or IDP) is a system entity that creates, maintains, and manages identity information for principals while providing authentication services to relying applications within a federation or distributed network.
Multi-factor authentication is an authentication method in which a computer user is granted access only after successfully presenting two or more pieces of evidence (or factors) to an authentication mechanism: knowledge (something only the user knows), possession (something the user and only the user has), and inherence (something the user and only the user is).
Multi-factor authentication reduces the incidence of online identity theft, because the victim’s password would no longer be enough to give a thief permanent access to their information.





0 comments:
Post a Comment